pointpcanywhere
pcanywhere 时间:2021-04-03 阅读:()
LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHacked1LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPER2LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERTableofContents3ExecutiveSummary31.
WeakDatabaseCredentials4Easeofattackandimpact6Defense62.
LMHashandBroadcastRequests7Easeofattackandimpact10Defense103.
OpenShares10Easeofattackandimpact12Defense124.
Default/WeakCredentialsonSensitiveResources12Easeofattackandimpact13MisconfiguredApacheTomcatwithdefaultcredentials15VNC16DRAC16Defense175.
VulnerabilitieswithPublicExploits17Easeofattackandimpact18Defense18Summary18Acknowledgements19AboutTheAuthor19AboutMcAfeeFoundstoneProfessionalServicesThiswhitepaperwaswrittenby:AmitBagreePrincipalSecurityConsultantMcAfeeFoundstoneProfessionalServicesExecutiveSummaryTheintentofthispaperistopresentacompilationoftheeasiestandmostprevalentnetwork-basedtechniquesanattackercanusetogainaccesstosystemsanddata,alsopopularlyknownas"low-hangingfruit"intheinformationsecuritycommunity.
Moreoftenthannot,theseleadtocompletecompromiseofaMicrosoftWindowsdomain.
Thefocusofthispaperisongainingthefirstfootholdonthenetwork.
Thesemethodsarebasedonmypersonalexperienceandhencearesubjective,andmostpenetrationtesterswouldconcurwithmany,ifnotall,ofthem.
Thispaperdoesnotdiscussnewattacks,butratherpresentscommonlyknownmethodsoffindinglow-hangingfruit,theeasewithwhichtheycanbeexploited,theimpactofthisexploitation,and,finally,remediationsuggestionstoaddressthem.
Afteryearsofpenetrationtestingandahighsuccessrateofcompromisingdomains,myprimemotivationforwritingthispaperistohelporganizationsperformthesesothatweallupthegameofhackinganddefendingdata.
Thiswillbeofinteresttonetworkanddatabaseadministrators,aswellasapplicationowners,sothattheybecomebetterinformedaboutprotectingtheirassetsanddata.
Securityprofessionalswillalsofindthisinformationuseful,asitwillhelpthembecomemoreawareoftheseexploitswhiletheyperformpenetrationtesting.
Thisshouldalsohelpmanagementpersonnelunderstandthegravityoffindingonesuchfruitontheirnetwork.
Belowisacompilationoffiveofthelowest-hangingfruits.
1.
WeakDatabaseCredentialsDataisanorganization'smostpreciousasset,soitcomesasnosurprisethatdatabasesareaprimetargetforattackers.
Whatmakesitmorelucrativeforanattackerishoweasilymanydatabasescanbecompromised.
OneofthemostvaluedtargetsistheMicrosoftSQLserver,givenitsprevalenceandsneakyinstancesofMSDEs/SQLServerExpressgettinginstalledwithoutusers'awareness.
ItisstillnotuncommontofindMSSQLserversusingweakorblankpasswords.
Surprisinglythe"Enforcepasswordpolicy"(includingaccountlockoutfromtheOS),whichhasbeenavailablesinceMicrosoftSQLserver2005(9.
xx),isoftennotused.
Thismakesitextremelyeasyforanattackertoconductabrute-forceattackontheseSQLservers.
WHITEPAPERLowHangingFruits:TheTopFiveEasiestWaystoHackorGetHacked3LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedConnectWithUs4LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPEREaseofattackandimpactTherearemanywaystodiscoverMSSQLserversonanetworkandperformabrute-forceattack.
OneofmyfavoritetoolsisSQLPing3.
0,whichcanbeusedforbothMSSQLserverdiscoveryandbrute-forcing.
Theinterfaceisintuitive,andallyouhavetoprovideistheIPsandlistofusernamesandpasswordstotry.
Ensurethat"DisableICMPcheck"under"Options"isselectedtoperformathoroughdiscoveryandtoggle"Brute-ForcePasswords"accordingtoyourneed.
Figure1.
ThemanyinstancesofMSSQLserversdiscoveredonanetworkwithsomeofthemusingweakorblankpasswords.
BelowaresomeofthemostcommonMSSQLusernamesonwhichtoattemptabrute-forceattack:sasqladminprobedistributor_admindboguestsysAlthoughthe"sa"(securityadministrator)accountisthemostprivilegedaccount,ifanattackergainsaccesstoalesserprivilegedaccountlike"admin,"theycanstillattempttoescalatetheirprivileges.
Thefigurebelowshowsonesuchinstance,wherealesserprivileged"admin"accountwascompromised,andthenaSQLqueryisusedtorecoverthe"sa"useraccounthashwithasimpleSQLclient"issqlw.
"Figure2.
The"sa"hashretrievedfromtheSQLserver.
Forpre-2005versionsofMSSQL,youcanqueryadifferenttable:SELECTpasswordFROMmaster.
dbo.
sysxloginsWHEREname='sa';5LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERThiscanthenbecrackedusingadictionaryattackwithvariouspasswordcrackingtools.
ThefigurebelowshowsJohntheRippersuccessfullyretrievingthepasswordfromthehashabove.
Figure3.
Asuccessfuldictionarycrackingofan"sa"password.
Thislow-hangingfruitisveryenticing,as,inmostcases,notonlydoesthecompromiseofaMicrosoftSQLserverprovidecompleteaccesstothedatabasesthemselves,butalsototheunderlyingoperatingsystem(OS)—typicallyMicrosoftWindows.
Microsoftprovidespowerfulextendedstoredprocedureslike"xp_cmdshell,"whichcandirectlyinteractwiththeOSsoanattackercansimplyusethenetcommandstoaddhimselfasalocaladministrator:xp_cmdshell'netuserfstonePassPhrase!
0/add'xp_cmdshell'netlocalgroupadministratorsfstone/add'OrevenasadomainuserifSQLserviceaccounthasprivileges:xp_cmdshell'netuser/addfstonePassPhrase!
0/add/domain'Notethatjustdisablingextendedstoredproceduresprovidesnoprotectionsinceitcanbeeasilyre-enabled:sp_configure'showadvancedoptions',1reconfiguresp_configure'xp_cmdshell',1reconfigureOtherdatabases,suchasOracle,PostgreSQL,MySQL,andothers,arealsovulnerabletosimilarbrute-forceattacks.
YoucanfindvariouscredentiallistsspecifictotargetingthosedatabasesontheInternet.
HoweverthemethodstoescalateprivilegesforgainingaccesstotheunderlyingOSisnotalwaysstraightforward.
CompromisingaSybasedatabaseandescalatingprivilegesisverysimilartodoingsoinMicrosoftSQL,althoughitisnotascommonlyusedasMicrosoftSQL.
TodiscoverSybaseonanetwork,youcanuseNmapwiththe–sVflag,whichtypicallylistensonports5000-5004.
YoucanidentifySybaseinstancesviaotheropenportslistedhere,oryoucanalsousethefollowingNmapscript:nmap--scriptbroadcast-sybase-asa-discoverSybasealsousescommoncredentialslikeentldbdbo/dbopswd,mon_user/mon_user,sa/blank.
McAfeeVulnerabilityManagerforDatabasesisapowerfultoolthatcanperformdiscoveryandbrute-forcingofSybasedatabases,alongwithallotherpopulardatabasesaswell.
SybaseusespowerfulstoredprocedurescapableofinteractingdirectlywiththeOSjustlikeMicrosoftSQL.
Thereisaspecificxp_cmdshellconfigurationsettingthatdeterminesthesecuritycontextunderwhichxp_cmdshellexecutesinSybase.
SettingittozerowillexecutethecommandshellunderthesecuritycontextofSybaseitself.
Withthedefaultsetting,(1)xp_cmdshellwillexecuteunderthecontextoftheuserwhoisexecutingthequery.
6LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure4.
Togglingtheextendedstoredprocedurexp_cmdshell'ssecuritycontext.
LikewithMicrosoftSQL,youcanthenusethe"net"commandstointeractwiththeOS.
Figure5.
Thexp_cmdshellbeingusedtoqueryWindowsuseraccounts.
DefenseBeginbysettingstrongpasswordsforallSQLserveraccounts.
Wikipedia'sarticlePasswordStrength:Guidelinesforstrongpasswordsisagoodstartingpoint.
Considerrenamingcommonaccountslistedabovetopreventsuchbruteforcingandassign"sysadmin"privilegestotherenamed"sa"account.
Mostimportantly,ensurethatyouuseSQLserver2005andaboveonWindowsserver2003andabovesoyoucanutilizetheOSloginpoliciesofpasswordcomplexityandaccountlockout,asrecommendedherebyMicrosoft.
ForSybase,utilizethe"UserLoginLockout"policytocontrolaccountlockout.
2.
LMHashandBroadcastRequestsIfyouhaveevenremotelydealtwithsecurityinaWindowsenvironment,chancesareyouhaveheardoftheLANManager(LM)hash.
TheideaofahashistopreventreversingofthehashedvaluebacktoitsplaintextandOSsusethismethodtoavoiddisclosureofaccountpasswords.
However,withtoday'scomputingpower,LMhashhasbecomeaveryweakformofhashandlikelyarootcauseofmanydatatheftsandcompromise.
7LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPEREaseofattackandimpactThefigurebelowdescribestheprocessofgeneratinganLMhashfromapassword—"Passphrase321.
"Figure6.
HowanLMhashisgeneratedfromapassword.
Notonlydoesthismethodsignificantlyreducethekeyspacethatyouneedtoguess,italsodoesnotusea"salt"—arandomvaluetopreventgenerationofthesamehashforthesamepassword.
Thismakesithighlysusceptibletopre-computeddictionaryattacks,suchasrainbowtables,whichrevealcleartextpasswordsinamatterofseconds.
FigurebelowshowssixLMhashesthatwerecrackedusinga4ATIRadeon6950GPUcardssetup.
Figure7.
HowquicklyLMhashescanbecracked.
AllMicrosoftOSs,includingandpriortoWindowsXPandWindowsServer2003,usedLMhashesbydefault,and,althoughorganizationsareslowlyupgradingtolatestsystems,itonlytakesasingleoldsystemonanetworktogetcompromised.
Inaddition,MicrosoftstillstorestheLMhashesfornewerOSsinmemoryforuserswithcurrentlylogged-oninteractivesessions,asdescribedindetailhere.
NotethatNTLMv1(thefirstupgradetoLM)isalsoaffectedbyseriouscryptographicvulnerabilitiesandcanbeeasilyreversedbutwillnotbedealtwithspecificallyinthispaper.
TherealinsidiousfactofexploitinguseofLMhashesonanetworkisthatyoudonotnecessarilyneedanyauthenticatedaccesstohostsonyourLAN.
Andyoudonotneedtouseanyhighlydisruptiveman-in-the-8LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERmiddle(MITM)techniques,likeARPspoofingeither.
AllanattackerhastodoisexploitthelackoftrustverificationinhownameresolutionworksonWindowsdomains.
MicrosoftdescribestheprocessofhostnameresolutionhereandNetBIOSnameresolutionhere.
Ifaresourceresolutionisrequestedforsayabcxyz.
com,thefigurebelowdescribeshowaWindowsOSwouldlookforananswer(IPaddress)fromsourcesinroughlythefollowingorder.
Figure8.
TheorderofresourcenameresolutionforMicrosoftsystems.
Ifanon-existentresourceisrequested,WindowssystemswouldsendoutaLLMNR(Link-LocalMulticastNameResolution)orNBNS(NetBIOSNameService)broadcastdependingontheOS.
OnlyWindowsVista/WindowsServer2008andabovesendLLMNRbroadcastmessagebeforesendingaNBNSbroadcast.
Thesebroadcastmessagesblindlytrusttheresponses,andallanattackerneedstodoisrespondback,tellingthevictimtoconnecttothem.
Then,dependingonthetypeofrequestandtheOSconfiguration,thevictimmayactuallysendLMorNTLMv1hasheswithitsfollow-upquery.
AndthatisallanattackerneedstodotogetaLMhash:listenforNBNSandLLMNRbroadcastrequestsontheLANandrespondbackwiththeirIPaddresstoconnectbackto.
Youwouldbeamazedathowmanysuchqueriesflybyonanetwork.
Givenenoughtimeorabusynetwork,anattackerwouldseelotofmistypedURLs,resourcerequestsfornon-existentprinters,drives,andmore.
9LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERThefiguresbelowshowtwoofmyfavoritetoolstoexploitLMhashesasdescribedabove.
Figure9.
Metasploit'sNBNSspoofingmodule.
BysettingtheirownsystemasSPOOFIPinMetasploit'sNBNSspoofingmodule(auxiliary/spoof/nbns/nbns_response),anattackertricksthevictimstoconnectbacktothemwhenrequestingforanon-existentresource.
WhenusedalongwithcoupleofotherMetasploitmodulesforcapturingthehashessuchasSMB(auxiliary/server/capture/smb)andHTTP_NTLM(auxiliary/server/capture/http_ntlm),thiscanleadtopasswordswithoutmucheffort.
Figure10.
CapturedandcrackedNTLMv1passwords.
Responder.
pyisapythonscriptwrittentotakeadvantageofthisbroadcastbehaviorandotherWindowsdefaultnetworkconfigurations.
YoucanuseittospoofNBNS,aswellasLLMNRrequestsandactiveman-in-the-middleWPADrequests.
Thefigurebelowshowsanexampleconfiguration.
Figure11.
ActivespoofingforNBNS,LLMNR,andWPADrequestsalongwithforcedNTLMandLMauthentication.
YoucanfindmoredetailsontheResponderscripthere.
10LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERDefenseThebestdefenseagainstexploitationofLM/NTLMv1hashesistocompletelyeliminateusingthemonthehostsandnetworks.
Ideally,youcoulduseagrouppolicyforthefollowingtwosettingsforallhostsonanetwork:Networksecurity:DonotstoreLANManagerhashvalueonnextpasswordchange–EnabledNetworksecurity:LANManagerauthenticationlevel–SendNTLMv2responseonly.
RefuseLM&NTLM.
Thesecanalsobesetforindividualhostsviathe"LocalSecurityPolicy,"whichmisstheglobalsettingforvariousreasons.
Ensurethatpasswordsforallaccounts,includingserviceaccounts,arechangedwhenthepolicyisbeenapplied.
Inaddition,considerenforcingpasswordlengthsof15charactersormoreforHLA(HighLevelAccess)accountstoautomaticallyensurethatLMhashesarenotstoredeveninmemory,asdiscussedearlier.
Finally,considerimplementingamonitoringtooltodetectspoofingattacksasdiscussedhere.
3.
OpenSharesSometimesyoudon'thavetobreakadoortoenterin—it'ssimplyleftopen.
Anditisimportanttorememberthatcompromisingsystems,applications,andpasswordsisultimatelyjustameanstotherealend—data.
Likeweakcredentialsondatabases,opensharesareanothergoldmineforanattacker,anditisnotuncommontoseethempoppinguponnetworkseverynowandthen.
Opensharesaresharesaccessibleoverthenetworkwithoutanycredentials.
Thisistypicallyaresultofmisconfigurationandhasledmetodiscoverallsortsofsensitiveinformation,includingSocialSecuritynumbers(SSNs),creditcarddata,passwords,payrollinformation,andmore.
Andwhat'sworsethanstoringsensitivedataonanon-encryptedfileKeepingthatfileinaworldreadableshare.
EaseofattackandimpactFindingopensharesandsensitivedatainsidethemisextremelyeasywiththeuseofrighttools.
MyfavoritetoolisSoftperfect'sNetworkScanner(Netscan).
YoucanimportalistofIPsyouwouldliketotestorevenprovidearange,asseeninthescreenshotbelow.
Figure12.
FigureshowsIPrangeinputfieldsforNetScan.
Underthe"Options:->"Shares"menu,youcanselectthe"Enablesecurityanduserpermissionscan"tocheckread/writeprivilegesontheshares.
Uponpressingthe"StartScanning"button,itwouldlookforsharesonalldiscoveredIPaddresses.
Youcanthenapplythesharesfilter()toonlylookatsystemswithavailablesharedfolders.
Theredmarkedfoldersaresharesaccessiblewithoutauthentication.
Belowareacoupleofexamplesofhowfindingsuchopensharesonanetworkarenotthatrare.
11LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure13.
Systemsdiscoveredwithopennetworkshares.
Figure14.
Systemsdiscoveredwithopennetworkshares.
Onceyoufindanysuchshares,thenextlogicalstepforanattackerwouldbetolookforsensitivedata.
AndmyfavoritetoolforthisjobisAstroGrep—aWindowsbased"grep"utility.
Apartfromkeywords,italsosupportsregexsoyoucanlookforSSNs,creditcardnumbers,andotherformatteddata.
Figure15.
AfileonanetworkaccessiblesharewithcredentialspossiblyforaMicrosoftaccount.
12LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure16.
Sensitivedataofauser'sdesktopbackeduponanetworkaccessibleshare.
DefenseAsthesayinggoes"thereisnopatchformisconfiguration.
"Thebestdefensetopreventsuchinadvertentexposureofdataiseducationanddetection.
Networksecurityteamsinorganizationsneedtocontinuouslylearntherisksofmisconfigurednetworksharesandroutinelyusemethodssuchastheonesdescribedabovetodetectopensharesontheirnetwork.
Thisshouldbecomepartofthesecuritylifecycle.
4.
Default/WeakCredentialsonSensitiveResourcesThismethodofattackisessentiallyawaytolookforanyresourceswhichcanbeeasilycompromised.
Typically,themostlucrativewayistolookforweak/defaultcredentials.
Plus,iftheseresourcesaresensitive,anattackerhitsthejackpot.
EaseofattackandimpactTolookfordefaultorweakcredentialsdoesnotrequirerunningacomprehensiveautomatedvulnerabilityscan.
Therearemultipletoolsthatcanusedtoaccomplishthisgoal.
Followingarefiveofthemostfruitfulones:RapidAssessmentofWebResources(RAWR):Aquickandcomprehensivewaytolookatallwebresourcesonanetwork.
ItisapythonscriptandusesphantomJStotakescreenshotsoflandingpagesofallwebresourcesdiscoveredandpresentsitinasearchableHTMLreport.
ItisavailableonBacktrack6andtakesinvariousfileformats,suchasNmap,Nessus,andMetasploit,forinput.
Mostimportantly,itprovidesdefaultpasswordsuggestionsusingseveralonlinesources.
Eyewitness:Anotherpythonscript(thereisaRubyversionaswell)thatusesGhost.
pyforwebpagescreenshots;ittakesinvariousfileformats,includingNmap,Nessus,andAmap;anditisdesignedtorunonKali.
Itgroupstogethersimilarwebpages,likedefaultserverpagesandprovidespasswordsuggestionsaswell.
13LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERNmaphttp-screenshotscript:FinallythereisanNSEscriptthatallowsyoutoscananetworkwithNmapandtakeascreenshotofeverywebpageatthesametime.
Itusesthe"wkhtmltoimage"librarytotaketheimages.
NessusDefaultCommonCredentialsScanPolicy:Whiletheabovethreetoolsfocusonwebresources,thisNessuspolicyismuchbroaderandlooksfordefaultandeasilyguessablecredentialsforallkindsofresources,suchasnetworkingdevices,OSs,databases,andothers.
Ihaveexcludedsomeoftheplug-insfromthispolicythatperformuserenumerationandbrute-forcetypeofattackstopreventdisruptionofservices.
Soensurethatyoureadthroughtheselectedplug-insbeforelaunchingthisscan.
NBTEnum3.
3:AnothercommonblindspotformanyITteamsisuseraccountsonOSs,especiallyserviceaccounts.
NBTEnum3.
3isoneofthemanytoolsanattackercanusetotakeadvantageofweakcredentialsonsuchaccounts.
Thistoolprovidesanicefeaturetoperformpasswordcheckingonlywhenthe"accountlockoutthreshold"issettozero.
Itisveryeffectiveinfindingaccountswithhavepasswordsthatarethesameastheusername.
Believeitornot,entiredomainshavebeencompromisedusingthismethod.
Figure17.
Twouseraccountsdiscoveredusingpasswordsthatarethesameastheusername.
Toofferapeekintowhatkindofdamagethesedefault/weakcredentialscanleadto,takealookatthefollowingexamples.
MisconfiguredApacheTomcatwithdefaultcredentialsSinceit'sthemostpopularwebserver,itisnotuncommontocomeacrossinstancesofApacheTomcatmisconfigurationstoenablemanageraccessandusedefaultcredentials(admin/admin,tomcat/tomcat).
Manytimes,thesemisconfigurationstendtobetestinstances.
However,theycanbevaluabletargetsforanattackeriftheyarepartofaWindowsdomain,asthiswouldpresentopportunitiesforprivilegeescalation.
14LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERSinceTomcattypicallyrunswith"SYSTEM"privilegesonaWindowssystem,anattackercaneasilycompromisethehostOS,asseenbelow.
Figure18.
TomcatManagerapplicationaccessedwithdefaultcredentials.
Usingaweb-basedshell,suchasLaudanum,allowseasyshellaccesstothehostOS.
Figure19.
TheJSPcommandshellexecuting"whoami.
"Figure20.
"Localadministrators"ontheserver.
15LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPEROryoucanusetheMetasploit"ApacheTomcatManagerApplicationDeployerAuthenticatedCodeExecution"module.
Figure21.
ApacheTomcatManagerusingdefaultcredentials.
Powerfulremotecontrolandadministrativeapplications,likeVNC,DRAC(DellRemoteAccessControl),Radmin,andPCAnywhere,cansometimesuseno/default/weakpasswords,and,oncediscovered,theynotonlyprovideaccess,butalsoawealthofinformationaboutanorganization'sbusiness.
Screenshotsbelowprovideaninsidelookatsomesuchdiscoveries.
VNCFigure22.
AnactiveSSHsessionviewedoveracompromisedVNCconnection.
Figure23.
SensitivetradingapplicationdataoveracompromisedVNCconnection.
16LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure24.
Auser'semailsoveracompromisedVNCconnection.
DRACFigure25.
DRACusingroot/calvinpasswordcombination.
Figure26.
"ConsoleRedirectionConnection"screenprovidesfullremotecontrolofthesystem.
DefenseTherootcauseofthislow-hangingfruitislackofstrongpasswords—allstepstakentoaddressthatwouldhelppreventitsexploitation.
Useadefense-in-depthapproach,startingwithdocumentingastrongpasswordpolicythatclearlydefinesinclusionofthird-partyandsensitiveapplications.
Theproceduredocumentationshouldlistthelength,complexity,andlockoutrequirements,pertheacceptablerisklevel.
Enforcingsuchpolicyisnotsimplyamatterofsoftwareimplementation,butalsoeducationandawareness.
Makesuretoalsoincluderoutinetestingwiththetoolsandmethodsdiscussedaboveforstrongenforcement.
17LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPER5.
VulnerabilitieswithPublicExploitsAsadefender,ifyouhavenotbeencompromisedthusfarusinganyofthemethodsabove,youhavedoneagoodjob.
Inmypersonalexperience,amajorityoforganizationsfailtoprotectthemselvesagainsttheabovetechniques.
Andifyoucanprotectagainstthisfifthlow-hangingfruit—vulnerabilitieswithpublicexploits—anattackerwouldknowtheyareupagainstafairlysecurity-matureorganization.
Youwouldalsonotethatthismethodofgainingafootholdonthenetworkistypicallynoisierthantheonesdiscussedearlier.
EaseofattackandimpactHavingavulnerabilityisonething,andhavingavulnerabilitywithapublicallyavailableexploitisanother.
Metasploitexploitationframeworkandexploit-db.
comaretwoofthelargestsourcesoffreepublicallyavailableexploits.
Twoofmyfavoritewaystomakeuseoftheseexploitsareexplainedbelow:ByusingaNessusscanpolicyselectingonlyvulnerabilitychecksfilteredby"ExploitAvailable=True.
"Thiscanquicklyprovidealistoflucrativetargetsthatareexploitableandcanalsopossiblyprovideremoteaccess.
Figure27.
AscreenshotofNessus'sfiltertoonlyselectvulnerabilitychecksthathaveanexploitavailable.
ByimportingNmapscanresultsintoMetasploit.
AftertyingaPostgreSQLdatabasetoMetasploitandimportingalllivehosts,openportsandservicesdata,Metasploitprovidesveryusefulmodulestotargetspecificsystemsorservices.
Basedonexperienceandknowledgeoftheenvironment,anattackercanselectivelygoaftertargetsthatcanbevulnerable.
AgoodprimerforusingthisMetasploitfunctionalitycanbefoundhere.
Thescreenshotsbelowshowasmallsampleofeasyexploitationofsuchvulnerabilitiesandthelevelofaccesstheycanprovidetoanattacker.
Figure28.
ExploitationofMS08_067,whichprovidesremoteaccessandhashesforuseraccountsfromthelocalSAMdatabase.
18LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure29.
ExploitationofMS09_050allowingremoteadministrativeaccesstothesystem.
Figure30.
FigureshowsexploitationofCVE-2009-1429allowinganattackertoaddusertothesystem.
DefenseUseadefense-in-depthapproachtoprotectagainstsuchexploitationwiththebestlineofdefensebeingup-to-datepatchingforallsystemsandsoftwareallthetime.
Organizationsshouldlookintodevisingacomprehensivepatchmanagementstrategyfortimelyupdatesofallsystems.
Usesoftwareforpatchmanagementaswellasvulnerabilityscanning.
Useascanpolicy,asdiscussedabove,tolookexclusivelyforvulnerabilitieswithpubliclyavailableexploits.
Thiswouldprovidehighvalueforthetimeandmoneyinvested.
Alsoincludestrongblocking,monitoring,andloggingcapabilitiesforalltrustzoneswithinyournetwork.
SummaryThereyouhaveit—acollectionofthetopfivelow-hangingfruit.
AtMcAfeeFoundstoneProfessionalServices,wearepassionateabouthackingandsecuringorganizations,andIhopethiswhitepaperhelpsyouhackordefendbetter.
Iencourageyoutoshareyourthoughtsandfeedbackwithme.
AcknowledgementsAnoteofthankstoPalanAnnamalaiandCarricDooleyforprovidingareviewofthiswhitepaperandtoBradAntoniewiczforhissupport.
19LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERAboutTheAuthorAmitBagreeisaprincipalsecurityconsultantatMcAfeeFoundstoneProfessionalServices,basedoutofOrlando,Florida.
Heisthetechnicalleadfornetworksecurityservicesandanexpertatperformingpenetrationtests.
Hehasfocusedallhisenergiesonbreakingthingsapartsincechildhoodandenjoyssharingthosefailuresandsuccesseswithothers.
Hehelpsclientswithavarietyofsecurityneeds,developsnewservicelinemethodologies,andimprovesexistingmethodologieswithnewattacks,testingmethods,andremediationsuggestions.
Amitholdsamaster'sdegreeininformationsecuritytechnologyandmanagementfromCarnegieMellonUniversity.
AboutMcAfeeFoundstoneProfessionalServicesMcAfeeFoundstoneProfessionalServices,adivisionofMcAfee,offersexpertservicesandeducationtohelporganizationscontinuouslyandmeasurablyprotecttheirmostimportantassetsfromthemostcriticalthreats.
Throughastrategicapproachtosecurity,McAfeeFoundstoneidentifiesandimplementstherightbalanceoftechnology,people,andprocesstomanagedigitalriskandleveragesecurityinvestmentsmoreeffectively.
Thecompany'sprofessionalservicesteamconsistsofrecognizedsecurityexpertsandauthorswithbroadsecurityexperiencewithmultinationalcorporations,thepublicsector,andtheUSmilitary.
http://www.
mcafee.
com/us/services/mcafeefoundstone-practice.
aspxAboutMcAfeeMcAfeeisoneoftheworld'sleadingindependentcybersecuritycompanies.
Inspiredbythepowerofworkingtogether,McAfeecreatesbusinessandconsumersolutionsthatmaketheworldasaferplace.
Bybuildingsolutionsthatworkwithothercompanies'products,McAfeehelpsbusinessesorchestratecyberenvironmentsthataretrulyintegrated,whereprotection,detectionandcorrectionofthreatshappensimultaneouslyandcollaboratively.
Byprotectingconsumersacrossalltheirdevices,McAfeesecurestheirdigitallifestyleathomeandaway.
Byworkingwithothersecurityplayers,McAfeeisleadingtheefforttouniteagainstcybercriminalsforthebenefitofall.
www.
mcafee.
com.
McAfeeandtheMcAfeelogoandFoundstonearetrademarksorregisteredtrademarksofMcAfee,LLCoritssubsidiariesintheUSandothercountries.
Othermarksandbrandsmaybeclaimedasthepropertyofothers.
Copyright2017McAfee,LLC.
61429wp_low-hanging-fruit_0115JANUARY2015LicenseThescreenshotimagesandcontentofthiswhitepaper,"LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHacked"byAmitBagree,arelicensedundertheCreativeCommonsAttribution-ShareAlike4.
0InternationalLicense.
Toviewacopyofthislicense,visithttp://creativecommons.
org/licenses/by-sa/4.
0/.
2821MissionCollegeBlvd.
SantaClara,CA95054888.
847.
8766www.
mcafee.
com20LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHacked
WeakDatabaseCredentials4Easeofattackandimpact6Defense62.
LMHashandBroadcastRequests7Easeofattackandimpact10Defense103.
OpenShares10Easeofattackandimpact12Defense124.
Default/WeakCredentialsonSensitiveResources12Easeofattackandimpact13MisconfiguredApacheTomcatwithdefaultcredentials15VNC16DRAC16Defense175.
VulnerabilitieswithPublicExploits17Easeofattackandimpact18Defense18Summary18Acknowledgements19AboutTheAuthor19AboutMcAfeeFoundstoneProfessionalServicesThiswhitepaperwaswrittenby:AmitBagreePrincipalSecurityConsultantMcAfeeFoundstoneProfessionalServicesExecutiveSummaryTheintentofthispaperistopresentacompilationoftheeasiestandmostprevalentnetwork-basedtechniquesanattackercanusetogainaccesstosystemsanddata,alsopopularlyknownas"low-hangingfruit"intheinformationsecuritycommunity.
Moreoftenthannot,theseleadtocompletecompromiseofaMicrosoftWindowsdomain.
Thefocusofthispaperisongainingthefirstfootholdonthenetwork.
Thesemethodsarebasedonmypersonalexperienceandhencearesubjective,andmostpenetrationtesterswouldconcurwithmany,ifnotall,ofthem.
Thispaperdoesnotdiscussnewattacks,butratherpresentscommonlyknownmethodsoffindinglow-hangingfruit,theeasewithwhichtheycanbeexploited,theimpactofthisexploitation,and,finally,remediationsuggestionstoaddressthem.
Afteryearsofpenetrationtestingandahighsuccessrateofcompromisingdomains,myprimemotivationforwritingthispaperistohelporganizationsperformthesesothatweallupthegameofhackinganddefendingdata.
Thiswillbeofinteresttonetworkanddatabaseadministrators,aswellasapplicationowners,sothattheybecomebetterinformedaboutprotectingtheirassetsanddata.
Securityprofessionalswillalsofindthisinformationuseful,asitwillhelpthembecomemoreawareoftheseexploitswhiletheyperformpenetrationtesting.
Thisshouldalsohelpmanagementpersonnelunderstandthegravityoffindingonesuchfruitontheirnetwork.
Belowisacompilationoffiveofthelowest-hangingfruits.
1.
WeakDatabaseCredentialsDataisanorganization'smostpreciousasset,soitcomesasnosurprisethatdatabasesareaprimetargetforattackers.
Whatmakesitmorelucrativeforanattackerishoweasilymanydatabasescanbecompromised.
OneofthemostvaluedtargetsistheMicrosoftSQLserver,givenitsprevalenceandsneakyinstancesofMSDEs/SQLServerExpressgettinginstalledwithoutusers'awareness.
ItisstillnotuncommontofindMSSQLserversusingweakorblankpasswords.
Surprisinglythe"Enforcepasswordpolicy"(includingaccountlockoutfromtheOS),whichhasbeenavailablesinceMicrosoftSQLserver2005(9.
xx),isoftennotused.
Thismakesitextremelyeasyforanattackertoconductabrute-forceattackontheseSQLservers.
WHITEPAPERLowHangingFruits:TheTopFiveEasiestWaystoHackorGetHacked3LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedConnectWithUs4LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPEREaseofattackandimpactTherearemanywaystodiscoverMSSQLserversonanetworkandperformabrute-forceattack.
OneofmyfavoritetoolsisSQLPing3.
0,whichcanbeusedforbothMSSQLserverdiscoveryandbrute-forcing.
Theinterfaceisintuitive,andallyouhavetoprovideistheIPsandlistofusernamesandpasswordstotry.
Ensurethat"DisableICMPcheck"under"Options"isselectedtoperformathoroughdiscoveryandtoggle"Brute-ForcePasswords"accordingtoyourneed.
Figure1.
ThemanyinstancesofMSSQLserversdiscoveredonanetworkwithsomeofthemusingweakorblankpasswords.
BelowaresomeofthemostcommonMSSQLusernamesonwhichtoattemptabrute-forceattack:sasqladminprobedistributor_admindboguestsysAlthoughthe"sa"(securityadministrator)accountisthemostprivilegedaccount,ifanattackergainsaccesstoalesserprivilegedaccountlike"admin,"theycanstillattempttoescalatetheirprivileges.
Thefigurebelowshowsonesuchinstance,wherealesserprivileged"admin"accountwascompromised,andthenaSQLqueryisusedtorecoverthe"sa"useraccounthashwithasimpleSQLclient"issqlw.
"Figure2.
The"sa"hashretrievedfromtheSQLserver.
Forpre-2005versionsofMSSQL,youcanqueryadifferenttable:SELECTpasswordFROMmaster.
dbo.
sysxloginsWHEREname='sa';5LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERThiscanthenbecrackedusingadictionaryattackwithvariouspasswordcrackingtools.
ThefigurebelowshowsJohntheRippersuccessfullyretrievingthepasswordfromthehashabove.
Figure3.
Asuccessfuldictionarycrackingofan"sa"password.
Thislow-hangingfruitisveryenticing,as,inmostcases,notonlydoesthecompromiseofaMicrosoftSQLserverprovidecompleteaccesstothedatabasesthemselves,butalsototheunderlyingoperatingsystem(OS)—typicallyMicrosoftWindows.
Microsoftprovidespowerfulextendedstoredprocedureslike"xp_cmdshell,"whichcandirectlyinteractwiththeOSsoanattackercansimplyusethenetcommandstoaddhimselfasalocaladministrator:xp_cmdshell'netuserfstonePassPhrase!
0/add'xp_cmdshell'netlocalgroupadministratorsfstone/add'OrevenasadomainuserifSQLserviceaccounthasprivileges:xp_cmdshell'netuser/addfstonePassPhrase!
0/add/domain'Notethatjustdisablingextendedstoredproceduresprovidesnoprotectionsinceitcanbeeasilyre-enabled:sp_configure'showadvancedoptions',1reconfiguresp_configure'xp_cmdshell',1reconfigureOtherdatabases,suchasOracle,PostgreSQL,MySQL,andothers,arealsovulnerabletosimilarbrute-forceattacks.
YoucanfindvariouscredentiallistsspecifictotargetingthosedatabasesontheInternet.
HoweverthemethodstoescalateprivilegesforgainingaccesstotheunderlyingOSisnotalwaysstraightforward.
CompromisingaSybasedatabaseandescalatingprivilegesisverysimilartodoingsoinMicrosoftSQL,althoughitisnotascommonlyusedasMicrosoftSQL.
TodiscoverSybaseonanetwork,youcanuseNmapwiththe–sVflag,whichtypicallylistensonports5000-5004.
YoucanidentifySybaseinstancesviaotheropenportslistedhere,oryoucanalsousethefollowingNmapscript:nmap--scriptbroadcast-sybase-asa-discoverSybasealsousescommoncredentialslikeentldbdbo/dbopswd,mon_user/mon_user,sa/blank.
McAfeeVulnerabilityManagerforDatabasesisapowerfultoolthatcanperformdiscoveryandbrute-forcingofSybasedatabases,alongwithallotherpopulardatabasesaswell.
SybaseusespowerfulstoredprocedurescapableofinteractingdirectlywiththeOSjustlikeMicrosoftSQL.
Thereisaspecificxp_cmdshellconfigurationsettingthatdeterminesthesecuritycontextunderwhichxp_cmdshellexecutesinSybase.
SettingittozerowillexecutethecommandshellunderthesecuritycontextofSybaseitself.
Withthedefaultsetting,(1)xp_cmdshellwillexecuteunderthecontextoftheuserwhoisexecutingthequery.
6LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure4.
Togglingtheextendedstoredprocedurexp_cmdshell'ssecuritycontext.
LikewithMicrosoftSQL,youcanthenusethe"net"commandstointeractwiththeOS.
Figure5.
Thexp_cmdshellbeingusedtoqueryWindowsuseraccounts.
DefenseBeginbysettingstrongpasswordsforallSQLserveraccounts.
Wikipedia'sarticlePasswordStrength:Guidelinesforstrongpasswordsisagoodstartingpoint.
Considerrenamingcommonaccountslistedabovetopreventsuchbruteforcingandassign"sysadmin"privilegestotherenamed"sa"account.
Mostimportantly,ensurethatyouuseSQLserver2005andaboveonWindowsserver2003andabovesoyoucanutilizetheOSloginpoliciesofpasswordcomplexityandaccountlockout,asrecommendedherebyMicrosoft.
ForSybase,utilizethe"UserLoginLockout"policytocontrolaccountlockout.
2.
LMHashandBroadcastRequestsIfyouhaveevenremotelydealtwithsecurityinaWindowsenvironment,chancesareyouhaveheardoftheLANManager(LM)hash.
TheideaofahashistopreventreversingofthehashedvaluebacktoitsplaintextandOSsusethismethodtoavoiddisclosureofaccountpasswords.
However,withtoday'scomputingpower,LMhashhasbecomeaveryweakformofhashandlikelyarootcauseofmanydatatheftsandcompromise.
7LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPEREaseofattackandimpactThefigurebelowdescribestheprocessofgeneratinganLMhashfromapassword—"Passphrase321.
"Figure6.
HowanLMhashisgeneratedfromapassword.
Notonlydoesthismethodsignificantlyreducethekeyspacethatyouneedtoguess,italsodoesnotusea"salt"—arandomvaluetopreventgenerationofthesamehashforthesamepassword.
Thismakesithighlysusceptibletopre-computeddictionaryattacks,suchasrainbowtables,whichrevealcleartextpasswordsinamatterofseconds.
FigurebelowshowssixLMhashesthatwerecrackedusinga4ATIRadeon6950GPUcardssetup.
Figure7.
HowquicklyLMhashescanbecracked.
AllMicrosoftOSs,includingandpriortoWindowsXPandWindowsServer2003,usedLMhashesbydefault,and,althoughorganizationsareslowlyupgradingtolatestsystems,itonlytakesasingleoldsystemonanetworktogetcompromised.
Inaddition,MicrosoftstillstorestheLMhashesfornewerOSsinmemoryforuserswithcurrentlylogged-oninteractivesessions,asdescribedindetailhere.
NotethatNTLMv1(thefirstupgradetoLM)isalsoaffectedbyseriouscryptographicvulnerabilitiesandcanbeeasilyreversedbutwillnotbedealtwithspecificallyinthispaper.
TherealinsidiousfactofexploitinguseofLMhashesonanetworkisthatyoudonotnecessarilyneedanyauthenticatedaccesstohostsonyourLAN.
Andyoudonotneedtouseanyhighlydisruptiveman-in-the-8LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERmiddle(MITM)techniques,likeARPspoofingeither.
AllanattackerhastodoisexploitthelackoftrustverificationinhownameresolutionworksonWindowsdomains.
MicrosoftdescribestheprocessofhostnameresolutionhereandNetBIOSnameresolutionhere.
Ifaresourceresolutionisrequestedforsayabcxyz.
com,thefigurebelowdescribeshowaWindowsOSwouldlookforananswer(IPaddress)fromsourcesinroughlythefollowingorder.
Figure8.
TheorderofresourcenameresolutionforMicrosoftsystems.
Ifanon-existentresourceisrequested,WindowssystemswouldsendoutaLLMNR(Link-LocalMulticastNameResolution)orNBNS(NetBIOSNameService)broadcastdependingontheOS.
OnlyWindowsVista/WindowsServer2008andabovesendLLMNRbroadcastmessagebeforesendingaNBNSbroadcast.
Thesebroadcastmessagesblindlytrusttheresponses,andallanattackerneedstodoisrespondback,tellingthevictimtoconnecttothem.
Then,dependingonthetypeofrequestandtheOSconfiguration,thevictimmayactuallysendLMorNTLMv1hasheswithitsfollow-upquery.
AndthatisallanattackerneedstodotogetaLMhash:listenforNBNSandLLMNRbroadcastrequestsontheLANandrespondbackwiththeirIPaddresstoconnectbackto.
Youwouldbeamazedathowmanysuchqueriesflybyonanetwork.
Givenenoughtimeorabusynetwork,anattackerwouldseelotofmistypedURLs,resourcerequestsfornon-existentprinters,drives,andmore.
9LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERThefiguresbelowshowtwoofmyfavoritetoolstoexploitLMhashesasdescribedabove.
Figure9.
Metasploit'sNBNSspoofingmodule.
BysettingtheirownsystemasSPOOFIPinMetasploit'sNBNSspoofingmodule(auxiliary/spoof/nbns/nbns_response),anattackertricksthevictimstoconnectbacktothemwhenrequestingforanon-existentresource.
WhenusedalongwithcoupleofotherMetasploitmodulesforcapturingthehashessuchasSMB(auxiliary/server/capture/smb)andHTTP_NTLM(auxiliary/server/capture/http_ntlm),thiscanleadtopasswordswithoutmucheffort.
Figure10.
CapturedandcrackedNTLMv1passwords.
Responder.
pyisapythonscriptwrittentotakeadvantageofthisbroadcastbehaviorandotherWindowsdefaultnetworkconfigurations.
YoucanuseittospoofNBNS,aswellasLLMNRrequestsandactiveman-in-the-middleWPADrequests.
Thefigurebelowshowsanexampleconfiguration.
Figure11.
ActivespoofingforNBNS,LLMNR,andWPADrequestsalongwithforcedNTLMandLMauthentication.
YoucanfindmoredetailsontheResponderscripthere.
10LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERDefenseThebestdefenseagainstexploitationofLM/NTLMv1hashesistocompletelyeliminateusingthemonthehostsandnetworks.
Ideally,youcoulduseagrouppolicyforthefollowingtwosettingsforallhostsonanetwork:Networksecurity:DonotstoreLANManagerhashvalueonnextpasswordchange–EnabledNetworksecurity:LANManagerauthenticationlevel–SendNTLMv2responseonly.
RefuseLM&NTLM.
Thesecanalsobesetforindividualhostsviathe"LocalSecurityPolicy,"whichmisstheglobalsettingforvariousreasons.
Ensurethatpasswordsforallaccounts,includingserviceaccounts,arechangedwhenthepolicyisbeenapplied.
Inaddition,considerenforcingpasswordlengthsof15charactersormoreforHLA(HighLevelAccess)accountstoautomaticallyensurethatLMhashesarenotstoredeveninmemory,asdiscussedearlier.
Finally,considerimplementingamonitoringtooltodetectspoofingattacksasdiscussedhere.
3.
OpenSharesSometimesyoudon'thavetobreakadoortoenterin—it'ssimplyleftopen.
Anditisimportanttorememberthatcompromisingsystems,applications,andpasswordsisultimatelyjustameanstotherealend—data.
Likeweakcredentialsondatabases,opensharesareanothergoldmineforanattacker,anditisnotuncommontoseethempoppinguponnetworkseverynowandthen.
Opensharesaresharesaccessibleoverthenetworkwithoutanycredentials.
Thisistypicallyaresultofmisconfigurationandhasledmetodiscoverallsortsofsensitiveinformation,includingSocialSecuritynumbers(SSNs),creditcarddata,passwords,payrollinformation,andmore.
Andwhat'sworsethanstoringsensitivedataonanon-encryptedfileKeepingthatfileinaworldreadableshare.
EaseofattackandimpactFindingopensharesandsensitivedatainsidethemisextremelyeasywiththeuseofrighttools.
MyfavoritetoolisSoftperfect'sNetworkScanner(Netscan).
YoucanimportalistofIPsyouwouldliketotestorevenprovidearange,asseeninthescreenshotbelow.
Figure12.
FigureshowsIPrangeinputfieldsforNetScan.
Underthe"Options:->"Shares"menu,youcanselectthe"Enablesecurityanduserpermissionscan"tocheckread/writeprivilegesontheshares.
Uponpressingthe"StartScanning"button,itwouldlookforsharesonalldiscoveredIPaddresses.
Youcanthenapplythesharesfilter()toonlylookatsystemswithavailablesharedfolders.
Theredmarkedfoldersaresharesaccessiblewithoutauthentication.
Belowareacoupleofexamplesofhowfindingsuchopensharesonanetworkarenotthatrare.
11LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure13.
Systemsdiscoveredwithopennetworkshares.
Figure14.
Systemsdiscoveredwithopennetworkshares.
Onceyoufindanysuchshares,thenextlogicalstepforanattackerwouldbetolookforsensitivedata.
AndmyfavoritetoolforthisjobisAstroGrep—aWindowsbased"grep"utility.
Apartfromkeywords,italsosupportsregexsoyoucanlookforSSNs,creditcardnumbers,andotherformatteddata.
Figure15.
AfileonanetworkaccessiblesharewithcredentialspossiblyforaMicrosoftaccount.
12LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure16.
Sensitivedataofauser'sdesktopbackeduponanetworkaccessibleshare.
DefenseAsthesayinggoes"thereisnopatchformisconfiguration.
"Thebestdefensetopreventsuchinadvertentexposureofdataiseducationanddetection.
Networksecurityteamsinorganizationsneedtocontinuouslylearntherisksofmisconfigurednetworksharesandroutinelyusemethodssuchastheonesdescribedabovetodetectopensharesontheirnetwork.
Thisshouldbecomepartofthesecuritylifecycle.
4.
Default/WeakCredentialsonSensitiveResourcesThismethodofattackisessentiallyawaytolookforanyresourceswhichcanbeeasilycompromised.
Typically,themostlucrativewayistolookforweak/defaultcredentials.
Plus,iftheseresourcesaresensitive,anattackerhitsthejackpot.
EaseofattackandimpactTolookfordefaultorweakcredentialsdoesnotrequirerunningacomprehensiveautomatedvulnerabilityscan.
Therearemultipletoolsthatcanusedtoaccomplishthisgoal.
Followingarefiveofthemostfruitfulones:RapidAssessmentofWebResources(RAWR):Aquickandcomprehensivewaytolookatallwebresourcesonanetwork.
ItisapythonscriptandusesphantomJStotakescreenshotsoflandingpagesofallwebresourcesdiscoveredandpresentsitinasearchableHTMLreport.
ItisavailableonBacktrack6andtakesinvariousfileformats,suchasNmap,Nessus,andMetasploit,forinput.
Mostimportantly,itprovidesdefaultpasswordsuggestionsusingseveralonlinesources.
Eyewitness:Anotherpythonscript(thereisaRubyversionaswell)thatusesGhost.
pyforwebpagescreenshots;ittakesinvariousfileformats,includingNmap,Nessus,andAmap;anditisdesignedtorunonKali.
Itgroupstogethersimilarwebpages,likedefaultserverpagesandprovidespasswordsuggestionsaswell.
13LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERNmaphttp-screenshotscript:FinallythereisanNSEscriptthatallowsyoutoscananetworkwithNmapandtakeascreenshotofeverywebpageatthesametime.
Itusesthe"wkhtmltoimage"librarytotaketheimages.
NessusDefaultCommonCredentialsScanPolicy:Whiletheabovethreetoolsfocusonwebresources,thisNessuspolicyismuchbroaderandlooksfordefaultandeasilyguessablecredentialsforallkindsofresources,suchasnetworkingdevices,OSs,databases,andothers.
Ihaveexcludedsomeoftheplug-insfromthispolicythatperformuserenumerationandbrute-forcetypeofattackstopreventdisruptionofservices.
Soensurethatyoureadthroughtheselectedplug-insbeforelaunchingthisscan.
NBTEnum3.
3:AnothercommonblindspotformanyITteamsisuseraccountsonOSs,especiallyserviceaccounts.
NBTEnum3.
3isoneofthemanytoolsanattackercanusetotakeadvantageofweakcredentialsonsuchaccounts.
Thistoolprovidesanicefeaturetoperformpasswordcheckingonlywhenthe"accountlockoutthreshold"issettozero.
Itisveryeffectiveinfindingaccountswithhavepasswordsthatarethesameastheusername.
Believeitornot,entiredomainshavebeencompromisedusingthismethod.
Figure17.
Twouseraccountsdiscoveredusingpasswordsthatarethesameastheusername.
Toofferapeekintowhatkindofdamagethesedefault/weakcredentialscanleadto,takealookatthefollowingexamples.
MisconfiguredApacheTomcatwithdefaultcredentialsSinceit'sthemostpopularwebserver,itisnotuncommontocomeacrossinstancesofApacheTomcatmisconfigurationstoenablemanageraccessandusedefaultcredentials(admin/admin,tomcat/tomcat).
Manytimes,thesemisconfigurationstendtobetestinstances.
However,theycanbevaluabletargetsforanattackeriftheyarepartofaWindowsdomain,asthiswouldpresentopportunitiesforprivilegeescalation.
14LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERSinceTomcattypicallyrunswith"SYSTEM"privilegesonaWindowssystem,anattackercaneasilycompromisethehostOS,asseenbelow.
Figure18.
TomcatManagerapplicationaccessedwithdefaultcredentials.
Usingaweb-basedshell,suchasLaudanum,allowseasyshellaccesstothehostOS.
Figure19.
TheJSPcommandshellexecuting"whoami.
"Figure20.
"Localadministrators"ontheserver.
15LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPEROryoucanusetheMetasploit"ApacheTomcatManagerApplicationDeployerAuthenticatedCodeExecution"module.
Figure21.
ApacheTomcatManagerusingdefaultcredentials.
Powerfulremotecontrolandadministrativeapplications,likeVNC,DRAC(DellRemoteAccessControl),Radmin,andPCAnywhere,cansometimesuseno/default/weakpasswords,and,oncediscovered,theynotonlyprovideaccess,butalsoawealthofinformationaboutanorganization'sbusiness.
Screenshotsbelowprovideaninsidelookatsomesuchdiscoveries.
VNCFigure22.
AnactiveSSHsessionviewedoveracompromisedVNCconnection.
Figure23.
SensitivetradingapplicationdataoveracompromisedVNCconnection.
16LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure24.
Auser'semailsoveracompromisedVNCconnection.
DRACFigure25.
DRACusingroot/calvinpasswordcombination.
Figure26.
"ConsoleRedirectionConnection"screenprovidesfullremotecontrolofthesystem.
DefenseTherootcauseofthislow-hangingfruitislackofstrongpasswords—allstepstakentoaddressthatwouldhelppreventitsexploitation.
Useadefense-in-depthapproach,startingwithdocumentingastrongpasswordpolicythatclearlydefinesinclusionofthird-partyandsensitiveapplications.
Theproceduredocumentationshouldlistthelength,complexity,andlockoutrequirements,pertheacceptablerisklevel.
Enforcingsuchpolicyisnotsimplyamatterofsoftwareimplementation,butalsoeducationandawareness.
Makesuretoalsoincluderoutinetestingwiththetoolsandmethodsdiscussedaboveforstrongenforcement.
17LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPER5.
VulnerabilitieswithPublicExploitsAsadefender,ifyouhavenotbeencompromisedthusfarusinganyofthemethodsabove,youhavedoneagoodjob.
Inmypersonalexperience,amajorityoforganizationsfailtoprotectthemselvesagainsttheabovetechniques.
Andifyoucanprotectagainstthisfifthlow-hangingfruit—vulnerabilitieswithpublicexploits—anattackerwouldknowtheyareupagainstafairlysecurity-matureorganization.
Youwouldalsonotethatthismethodofgainingafootholdonthenetworkistypicallynoisierthantheonesdiscussedearlier.
EaseofattackandimpactHavingavulnerabilityisonething,andhavingavulnerabilitywithapublicallyavailableexploitisanother.
Metasploitexploitationframeworkandexploit-db.
comaretwoofthelargestsourcesoffreepublicallyavailableexploits.
Twoofmyfavoritewaystomakeuseoftheseexploitsareexplainedbelow:ByusingaNessusscanpolicyselectingonlyvulnerabilitychecksfilteredby"ExploitAvailable=True.
"Thiscanquicklyprovidealistoflucrativetargetsthatareexploitableandcanalsopossiblyprovideremoteaccess.
Figure27.
AscreenshotofNessus'sfiltertoonlyselectvulnerabilitychecksthathaveanexploitavailable.
ByimportingNmapscanresultsintoMetasploit.
AftertyingaPostgreSQLdatabasetoMetasploitandimportingalllivehosts,openportsandservicesdata,Metasploitprovidesveryusefulmodulestotargetspecificsystemsorservices.
Basedonexperienceandknowledgeoftheenvironment,anattackercanselectivelygoaftertargetsthatcanbevulnerable.
AgoodprimerforusingthisMetasploitfunctionalitycanbefoundhere.
Thescreenshotsbelowshowasmallsampleofeasyexploitationofsuchvulnerabilitiesandthelevelofaccesstheycanprovidetoanattacker.
Figure28.
ExploitationofMS08_067,whichprovidesremoteaccessandhashesforuseraccountsfromthelocalSAMdatabase.
18LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERFigure29.
ExploitationofMS09_050allowingremoteadministrativeaccesstothesystem.
Figure30.
FigureshowsexploitationofCVE-2009-1429allowinganattackertoaddusertothesystem.
DefenseUseadefense-in-depthapproachtoprotectagainstsuchexploitationwiththebestlineofdefensebeingup-to-datepatchingforallsystemsandsoftwareallthetime.
Organizationsshouldlookintodevisingacomprehensivepatchmanagementstrategyfortimelyupdatesofallsystems.
Usesoftwareforpatchmanagementaswellasvulnerabilityscanning.
Useascanpolicy,asdiscussedabove,tolookexclusivelyforvulnerabilitieswithpubliclyavailableexploits.
Thiswouldprovidehighvalueforthetimeandmoneyinvested.
Alsoincludestrongblocking,monitoring,andloggingcapabilitiesforalltrustzoneswithinyournetwork.
SummaryThereyouhaveit—acollectionofthetopfivelow-hangingfruit.
AtMcAfeeFoundstoneProfessionalServices,wearepassionateabouthackingandsecuringorganizations,andIhopethiswhitepaperhelpsyouhackordefendbetter.
Iencourageyoutoshareyourthoughtsandfeedbackwithme.
AcknowledgementsAnoteofthankstoPalanAnnamalaiandCarricDooleyforprovidingareviewofthiswhitepaperandtoBradAntoniewiczforhissupport.
19LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHackedWHITEPAPERAboutTheAuthorAmitBagreeisaprincipalsecurityconsultantatMcAfeeFoundstoneProfessionalServices,basedoutofOrlando,Florida.
Heisthetechnicalleadfornetworksecurityservicesandanexpertatperformingpenetrationtests.
Hehasfocusedallhisenergiesonbreakingthingsapartsincechildhoodandenjoyssharingthosefailuresandsuccesseswithothers.
Hehelpsclientswithavarietyofsecurityneeds,developsnewservicelinemethodologies,andimprovesexistingmethodologieswithnewattacks,testingmethods,andremediationsuggestions.
Amitholdsamaster'sdegreeininformationsecuritytechnologyandmanagementfromCarnegieMellonUniversity.
AboutMcAfeeFoundstoneProfessionalServicesMcAfeeFoundstoneProfessionalServices,adivisionofMcAfee,offersexpertservicesandeducationtohelporganizationscontinuouslyandmeasurablyprotecttheirmostimportantassetsfromthemostcriticalthreats.
Throughastrategicapproachtosecurity,McAfeeFoundstoneidentifiesandimplementstherightbalanceoftechnology,people,andprocesstomanagedigitalriskandleveragesecurityinvestmentsmoreeffectively.
Thecompany'sprofessionalservicesteamconsistsofrecognizedsecurityexpertsandauthorswithbroadsecurityexperiencewithmultinationalcorporations,thepublicsector,andtheUSmilitary.
http://www.
mcafee.
com/us/services/mcafeefoundstone-practice.
aspxAboutMcAfeeMcAfeeisoneoftheworld'sleadingindependentcybersecuritycompanies.
Inspiredbythepowerofworkingtogether,McAfeecreatesbusinessandconsumersolutionsthatmaketheworldasaferplace.
Bybuildingsolutionsthatworkwithothercompanies'products,McAfeehelpsbusinessesorchestratecyberenvironmentsthataretrulyintegrated,whereprotection,detectionandcorrectionofthreatshappensimultaneouslyandcollaboratively.
Byprotectingconsumersacrossalltheirdevices,McAfeesecurestheirdigitallifestyleathomeandaway.
Byworkingwithothersecurityplayers,McAfeeisleadingtheefforttouniteagainstcybercriminalsforthebenefitofall.
www.
mcafee.
com.
McAfeeandtheMcAfeelogoandFoundstonearetrademarksorregisteredtrademarksofMcAfee,LLCoritssubsidiariesintheUSandothercountries.
Othermarksandbrandsmaybeclaimedasthepropertyofothers.
Copyright2017McAfee,LLC.
61429wp_low-hanging-fruit_0115JANUARY2015LicenseThescreenshotimagesandcontentofthiswhitepaper,"LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHacked"byAmitBagree,arelicensedundertheCreativeCommonsAttribution-ShareAlike4.
0InternationalLicense.
Toviewacopyofthislicense,visithttp://creativecommons.
org/licenses/by-sa/4.
0/.
2821MissionCollegeBlvd.
SantaClara,CA95054888.
847.
8766www.
mcafee.
com20LowHangingFruits:TheTopFiveEasiestWaystoHackorGetHacked
- pointpcanywhere相关文档
- 投标人pcanywhere
- 色谱pcanywhere
- sourcepcanywhere
- addresspcanywhere
- checkpcanywhere
- RemoteWareBCpcanywhere
Pia云服务商春节6.66折 美国洛杉矶/中国香港/俄罗斯和深圳机房
Pia云这个商家的云服务器在前面也有介绍过几次,从价格上确实比较便宜。我们可以看到最低云服务器低至月付20元,服务器均采用KVM虚拟架构技术,数据中心包括美国洛杉矶、中国香港、俄罗斯和深圳地区,这次春节活动商家的活动力度比较大推出出全场6.66折,如果我们有需要可以体验。初次体验的记得月付方案,如果合适再续约。pia云春节活动优惠券:piayun-2022 Pia云服务商官方网站我们一起看看这次活...

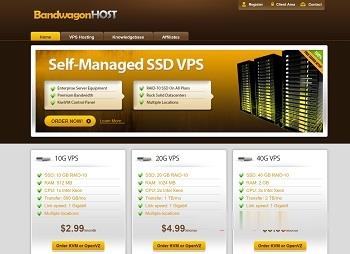
pacificrack:VPS降价,SSD价格下降
之前几个月由于CHIA挖矿导致全球固态硬盘的价格疯涨,如今硬盘挖矿基本上已死,硬盘的价格基本上恢复到常规价位,所以,pacificrack决定对全系Cloud server进行价格调整,降幅较大,“如果您是老用户,请通过续费管理或升级套餐,获取同步到最新的定价”。官方网站:https://pacificrack.com支持PayPal、支付宝等方式付款VPS特征:基于KVM虚拟,纯SSD raid...
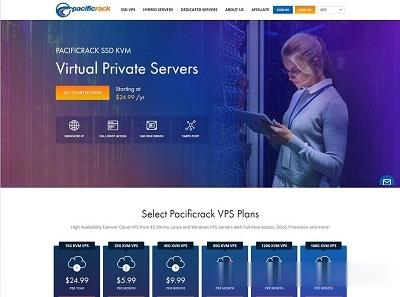
搬瓦工VPS:新增荷兰机房“联通”线路的VPS,10Gbps带宽,可在美国cn2gia、日本软银、荷兰“联通”之间随意切换
搬瓦工今天正式对外开卖荷兰阿姆斯特丹机房走联通AS9929高端线路的VPS,官方标注为“NL - China Unicom Amsterdam(ENUL_9)”,三网都走联通高端网络,即使是在欧洲,国内访问也就是飞快。搬瓦工的依旧是10Gbps带宽,可以在美国cn2 gia、日本软银与荷兰AS9929之间免费切换。官方网站:https://bwh81.net优惠码:BWH3HYATVBJW,节约6...
pcanywhere为你推荐
-
多家五星酒店回应网传名媛拼单拼多多商家出钱叫买家好评会被处罚吗小度商城小度怎么下载app?怎么查询商标手机上能查询商标吗?怎么查?杨紫别祝我生日快乐一个人过生日的伤感说说有什么阿丽克丝·布莱肯瑞吉阿丽克斯布莱肯瑞吉演的美国恐怖故事哪两集陈嘉垣马德钟狼吻案事件是怎么回事www.javmoo.comjavimdb是什么网站为什么打不开杨丽晓博客杨丽晓今年高考了吗?www.se222se.com原来的www站到底222eee怎么了莫非不是不能222eee在收视com了,/?求解16668.com香港最快开奖现场直播今晚开