2011ArubaNetworksInc.
comodo 时间:2021-01-12 阅读:()
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
SupportAdvisory:ArubaOSDefaultCertificateExpirationIssuedFebruary14,2011UpdatedApril8,2011Thisdocument,includingtheinformationitcontainsandtheprogramsmadeavailablethroughthelinksthatitincludes,isprovidedtoyouonan"asis"basis.
ARUBAANDITSSUPPLIERSDONOTWARRANTTHATSUCHINFORMATIONORTHEFUNCTIONSCONTAINEDINSUCHPROGRAMSWILLMEETYOURREQUIREMENTSORTHATTHEOPERATIONOFTHEPROGRAMSWILLBEUNINTERRUPTEDORERROR-FREE.
THEINFORMATIONANDPROGRAMSAREPROVIDEDTOYOUWITHNOWARRANTYOFANYKIND,EXPRESSORIMPLIED,INCLUDINGWITHOUTLIMITATION,ANYIMPLIEDWARRANTIESOFMERCHANTABILITY,FITNESSFORAPARTICULARPURPOSEANDNONINFRINGEMENT.
INNOEVENTWILLARUBA,ITSSUPPLIERS,ORANYONEELSEWHOHASBEENINVOLVEDINTHECREATION,PRODUCTION,ORDELIVERYOFTHEINFORMATIONORPROGRAMSBELIABLEFORANYDIRECT,INDIRECT,INCIDENTALORCONSEQUENTIALDAMAGES,INCLUDINGWITHOUTLIMITATION,LOSTPROFITSORLOSTDATA,THATMAYARISEOUTOFYOURUSEOFORFAILURETOUSETHEINFORMATIONORPROGRAMS,EVENIFARUBAORSUCHOTHERENTITIESHAVEBEENADVISEDOFTHEPOSSIBILITYOFSUCHDAMAGES.
THEFOREGOINGSHALLNOTBEDEEMEDTOPRECLUDEANYLIABILITYWHICH,UNDERAPPLICABLEPRODUCTSLIABILITYLAW,CANNOTBEPRECLUDEDBYCONTRACT.
ThisdocumentisbeingprovidedtoyoupursuanttotheprovisionsofyourapplicablesoftwarelicenseagreementwithAruba,andtheinformationandprogramsmaybeusedonlypursuanttothetermsandconditionsofsuchagreement.
ThisArubaSecurityAdvisorconstitutesArubaProprietaryInformationandshouldnotbedisseminated,forwardedordisclosed.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
SummaryOnJune29,2011thedefaultSSL/TLScertificate"securelogin.
arubanetworks.
com"thatisinstalledonallArubacontrollerswillexpire.
Whilethisdefaultcertificatewasneverintendedforproductionuse,Arubaisawarethatanumberofcustomersareusingthiscertificateinproductionnetworks.
Thesecustomerswillneedtoreplacethecertificate.
Affectedcustomershavetwooptions:1.
Replacethedefaultcertificatewithacertificateissuedbyaninternalcertificateauthorityorapubliccertificateauthority.
Thisoptionisrecommendedandprovidesthegreatestsecurity.
2.
UpgradetheArubaOSimagetoaversionnumberequaltoorgreaterthan3.
3.
3.
10,3.
4.
4.
2,5.
0.
3.
2,6.
0.
1.
1,or6.
1.
0.
0.
Thesesoftwareimagescontainanewdefaultcertificatethatwillreplacetheexpiringcertificate.
Thisoptiondoesnotprovidegoodsecurity,sinceallArubacustomershaveaccesstothesamecertificateandimpersonationattacksarepossible.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
BackgroundTheArubaOSoperatingsystemloadedonallArubaMobilityControllerscontainsapre-loadeddigitalcertificatewiththename"securelogin.
arubanetworks.
com".
Thiscertificatewasissuedbyapubliccertificateauthority(CA)thatistrustedbymostbrowsersandoperatingsystems.
Bydefaultthecertificateisusedforthecontroller'smanagementinterface(WebUI),captiveportal,andEAPtermination.
Thiscertificateisintendedforquicklysettinguplabnetworks,demonstrations,andproof-of-conceptdeployments.
Asstatedintheuserguide,thedefaultcertificateisnotintendedforproductiondeployment,sinceeveryArubacontrollercontainsthesamecertificateandthisenablesimpersonationattacks.
Thefollowingtextsummarizestherisks:CaptivePortal:Anattackerimpersonatingacaptiveportalloginscreenmaybeabletoobtaintheusernameandpasswordofauthorizedusersonthesystem.
Ifcaptiveportalisusedonlyforguestaccess,thismaynotbedeemedaserioussecurityrisk.
Ifcaptiveportalisusedtoauthenticateinternalusers,thisattackcouldcausemoreseriousdamage.
AdministrativeWebUI:Tocarryoutanimpersonationattackagainstthecontroller'sadministrativeWebUI,theattackerwouldneedtointercepttrafficbetweenasystemadministrator'scomputerandthecontroller.
Thiswouldtypicallyrequireaninsiderattack,assumingadministrativeaccessisblockedfrompublicnetworks.
Theriskisseriousinthiscase,sinceasuccessfulattackwouldallowanunauthorizedpersontoobtainadministrativecredentialsfortheArubacontroller.
TheWebUIcertificateshouldalwaysbereplaced,evenifwithaself-signedcertificatethateachsystemadministratormustexplicitlytrust.
802.
1XEAPTermination:Thisistheriskiestuseofthedefaultcertificate,becauseanimpersonationattackmaybecarriedoutoverawirelessnetwork,andasuccessfulattackmayrevealusernamesandpasswordhashes(providingmaterialforanofflinepasswordcrackingattempt)orallowtheattackertogetauserconnectedtoahostilenetworkwhiletheuserthinksheorsheisconnectedtoatrustednetwork.
Thedefaultcertificateshouldneverbeusedfor802.
1X.
Arubaisawarethatsomecustomersdousethedefaultcertificateinproduction,typicallyforsecuringthecaptiveportalloginscreeninguestnetworkswhereensuringtheidentityofthecontrollerisnotanimportantsecurityconsideration.
Thedefaultcertificatewasvalidforfiveyears,andwillexpireonJune29,2011.
Ifthenetworkadministratordoesnotreplacethecertificate,thefollowingwilloccur:1.
UsersconnectingtocaptiveportalorWebUIpageswillreceiveabrowserwarningshowingthattheservercertificatehasexpired.
Usersmaybypassthewarning(withvaryingdegreesofdifficultydependingonthebrowser)andcontinueontousethesystemnormally.
2.
IfEAPterminationhasbeenenabledfor802.
1X,andthedefaultcertificateisbeingusedastheservercertificate,manyclientoperatingsystemswillrefusetocontinuetheauthenticationprocess.
Thiswillresultinanapparentnetworkoutagefortheseusers.
Clientoperatingsystemsmayormaynotdisplayawarningmessagetotheuser.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
Thisdocumentoutlinestheproceduresneededtoupdatethedefaultcertificate,inorderofpreference:Option1:InstallauniqueservercertificateOption2:UpgradeArubaOS2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
Option1:InstallaUniqueServerCertificateThisistherecommendedapproachsinceitprovidesthebestsecurity.
Inthisapproach,thedefaultcertificatewillremainonthecontroller,butyouwillloadoneormorenewcertificatesandthenconfigurethesystemtousethenewcertificate(s).
Ifyourorganizationoperatesaninternalcertificateauthority(CA)andallclientsthatwillusethesystemalreadytrusttheinternalCA,youmayusetheinternalCAtoissueanewcertificatetothecontroller.
Thisoptionisrecommendedfor802.
1XEAPterminationandWebUIadministrativeaccesstothecontroller.
Itcanalsobeusedforcaptiveportalaslongasthegeneralpublicwillnotbeaccessingthesystem(sincetheinternalCAwillnotbetrusted,thegeneralpublicwouldreceivebrowserwarnings.
)Ifpresentingacaptiveportalpagetocomputersownedbythegeneralpublic,acertificateissuedbyapublicCA(VeriSign,GeoTrust,Comodo,etc.
)shouldbeusedsothatbrowserwarningsarenotgenerated.
YoumaychoosetouseacertificateissuedbyapublicCAforWebUIadministrativeaccesstothecontrollerandfor802.
1XEAPterminationaswell,butuseofapublicCAinsteadofaninternalCAprovidesnobenefitinthosecases.
Beforerequestingacertificate,decidewhetheryouneeda1024-bitkey,2048-bitkey,or4096-bitkey.
NotethatmanypublicCAsnolongerissuecertificateswith1024-bitkeys.
IfyouarerunningArubaOS6.
1orgreater,youmayuseacertificatewitha2048-bitkeyforanypurpose.
Youmayuseacertificatewitha4096-bitkeyonlyforcaptiveportalandWebUI.
ForWebUIorcaptiveportal,performanceisthegreatestwithsmallerkeysizes,butsecurityisslightlyreduced.
Tomaximizecompatibility,alwaysuseRSAunlessyouhaveaspecificreasontouseECC.
Ifyouarerunninganyreleasepriorto6.
1,youmayuseacertificatewitha2048-bitor4096-bitkeyonlyforcaptiveportalandWebUI.
802.
1XEAPterminationsupportsonly1024-bitkeys.
ForWebUIorcaptiveportal,performanceisthegreatestwithsmallerkeysizes,butsecurityisslightlyreduced.
Thefollowinginstructionsshouldbefollowedtoobtainandinstallaservercertificate.
1.
GenerateaCertificateSigningRequest(CSR)fromthecontrollerbynavigatingtoConfigurationManagementCertificatesCSR.
Filloutthenecessaryfields.
Afterclicking"GenerateNew",thecontrollerwillgenerateaprivatekey,whichremainslockedinsidethecontroller,andabase64-encodedCSR.
TheCSRcontainsallthedetailsneededforyourCAtoissuethecertificate.
TheCommonName(CN)fieldshouldcontainthefullURLthatwebbrowserswillnavigatetoinordertoreachthecontroller'sembeddedwebserver.
TakecaretofillouttheCommonNamefieldcorrectlyaccordingtothepurposeofthecertificate:a.
Forcaptiveportal,thesystemwillautomaticallyissueHTTPredirectsandspoofDNSresponsestothecaptiveportalclientsothatthebrowserappearstobeconnectingtothecorrectDNSnamethatmatchesthecertificatecommonname.
Thisistoensurethatbrowserwarningsarenotgenerated.
Ifthecertificateisonlybeingusedforcaptiveportal,thenameintheCNfieldisunimportant–butmakesureitfallswithin2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
yourdomainnamesothatapublicCAwillcorrectlyauthorizeownershipofthecertificate.
b.
ForWebUI,theCNfieldshouldmatchtheaddressyouusetomanagethecontroller.
ThiscanbeanIPaddressoraFullyQualifiedDomainName(FQDN).
c.
For802.
1XEAPTermination,theCNfieldisnotmatchedbytheclientagainstanyotherparameter.
ItissuggestedthatyouchooseaFQDNthatisownedbyyourorganization.
2.
Clickon"ViewCurrent".
Copythebase64textshown,andpastethisintothecertificaterequestwindowprovidedbyyourcertificateauthority.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
3.
Onceyouhaveobtainedthecertificate,navigatetoConfigurationManagementCertificatesUploadanduploadthecertificatetothecontroller.
ThecertificatewillmostlikelybeprovidedtoyouinPEMorDERformat–ifyouarenotsurewhichformatitisin,tryPEMfirstandifanerrormessageresults,tryDER.
APEMformatcertificatewillbebase64-encodedandwillbeginwiththetext"-----BEGINCERTIFICATE-----".
4.
Ifyouwanttousethenewcertificateforcaptiveportal,navigatetoConfigurationManagementGeneralandchangetheCaptivePortalServerCertificate.
IfyouwanttousethenewcertificateforWebUI,configurationisfoundonthesamescreenunder"WebUIManagementAuthenticationMethod".
5.
IfyouwanttousethenewcertificateforEAPTermination,navigatetoConfigurationSecurityAuthenticationL2Authentication802.
1XAuthentication2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
ProfileAdvancedandchangetheservercertificateforallactive802.
1XauthenticationprofilesthatuseEAPTermination.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
Option2:UpgradeArubaOSArubahasobtainedanewcertificatelabeled"securelogin.
arubanetworks.
com"fromapublicCAthatreplacestheolddefaultcertificate.
ThenewcertificatehasanexpirationdateofNovember21,2013.
ThiscertificateisincludedaspartofthefollowingArubaOSsoftwarereleases:6.
1beginningwithrelease6.
1.
0.
06.
0beginningwithrelease6.
0.
1.
15.
0beginningwithrelease5.
0.
3.
23.
4beginningwithrelease3.
4.
4.
23.
3beginningwithrelease3.
3.
3.
10AllotherArubaOSreleasesdatedlaterthanJune1,2011Afterupgradingtooneoftheabovelistedreleases,nofurtheractionisrequiredtoenablethecertificate.
Ifthesystemwaspreviouslyconfiguredtousethedefaultcertificate,itwillautomaticallyusethenewlyupdatedcertificate.
Whilethisoptionprovidesthesamelevelofsecuritygivenbythepreviousdefaultcertificate,itisnotagoodoptionwhereanysecurityrequirementsexist.
SSL/TLSsecurityisprovidedbythecertificate'sprivatekeybeingkeptsecret.
Ifthecertificate'sprivatekeybecomesknown,itispossibleforanattackertoimpersonateanyserverorwebsiteusingthatcertificatewithouttheknowledgeoftheenduser.
BecausethesamecertificateandprivatekeyareinstalledonallArubacontrollers,anattackerneedonlyreverseengineerasinglesoftwareimagetoobtaintheprivatekey.
Whilethisprocessisnon-trivial,itiscertainlynotbeyondthemeansofaskilledanddeterminedattacker.
ItisalsopossibleforanattackertosimplypurchaseanduseanArubacontrollerforthepurposeofconductinganimpersonationattack.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
FAQQ:WhathappensifIhaveconfigured802.
1Xdevicesinmynetworktoonlytrustthe"securelogin.
arubanetworks.
com"certificate,ortoonlytrusttheEquifaxSecureCertificateAuthorityA:Thesedeviceswillneedtobereconfiguredafterinstallationofanewcertificate.
IftheseareWindowsdevices,UNCHECK"Connecttotheseservers"andUNCHECK"EquifaxSecureCertificateAuthority"intheTrustedRootCertificationAuthorities.
Afterconnectingtothecontrollerwiththenewcertificateinstalled,Windowswillupdatethesesettingsbypromptingtheuser.
Q:IsthecertificatebuiltintotheTPMchipaffectedbythisadvisoryA:No.
AllArubacontrollersthatcontainaTrustedPlatformModule(TPM),includingtheM3,3000series,and600series,containacertificateuniquetothecontrollerthathasbeenprogrammedatthefactory.
Thiscertificateisnotexpiringandisnotaffectedbythisadvisory.
ThiscertificateisusedforMaster-Localauthentication,ControlPlaneSecurity(CPsec),andRAPauthentication.
ItisnotsuitableforuseasanSSLcertificatesinceitwasissuedbyAruba'smanufacturingCA,whichisnottrustedbybrowsers.
Q:WhatcertificateauthoritywasusedtogeneratethenewcertificateWhatchainsdoesitcontain2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
A:ThenewcertificatewasissuedbyPositiveSSL,andultimatelychainsbackuptoUSERTrust,whichisissuedbyAddTrustExternalCARoot.
DevicesconnectingtothenetworkmusthaveUSERTrustinstalledasatrustedrootCAinorderfortheArubafactorydefaultcertificatetobetrusted.
UnderaWindowssystem,thecertificatechainappearsas
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
SupportAdvisory:ArubaOSDefaultCertificateExpirationIssuedFebruary14,2011UpdatedApril8,2011Thisdocument,includingtheinformationitcontainsandtheprogramsmadeavailablethroughthelinksthatitincludes,isprovidedtoyouonan"asis"basis.
ARUBAANDITSSUPPLIERSDONOTWARRANTTHATSUCHINFORMATIONORTHEFUNCTIONSCONTAINEDINSUCHPROGRAMSWILLMEETYOURREQUIREMENTSORTHATTHEOPERATIONOFTHEPROGRAMSWILLBEUNINTERRUPTEDORERROR-FREE.
THEINFORMATIONANDPROGRAMSAREPROVIDEDTOYOUWITHNOWARRANTYOFANYKIND,EXPRESSORIMPLIED,INCLUDINGWITHOUTLIMITATION,ANYIMPLIEDWARRANTIESOFMERCHANTABILITY,FITNESSFORAPARTICULARPURPOSEANDNONINFRINGEMENT.
INNOEVENTWILLARUBA,ITSSUPPLIERS,ORANYONEELSEWHOHASBEENINVOLVEDINTHECREATION,PRODUCTION,ORDELIVERYOFTHEINFORMATIONORPROGRAMSBELIABLEFORANYDIRECT,INDIRECT,INCIDENTALORCONSEQUENTIALDAMAGES,INCLUDINGWITHOUTLIMITATION,LOSTPROFITSORLOSTDATA,THATMAYARISEOUTOFYOURUSEOFORFAILURETOUSETHEINFORMATIONORPROGRAMS,EVENIFARUBAORSUCHOTHERENTITIESHAVEBEENADVISEDOFTHEPOSSIBILITYOFSUCHDAMAGES.
THEFOREGOINGSHALLNOTBEDEEMEDTOPRECLUDEANYLIABILITYWHICH,UNDERAPPLICABLEPRODUCTSLIABILITYLAW,CANNOTBEPRECLUDEDBYCONTRACT.
ThisdocumentisbeingprovidedtoyoupursuanttotheprovisionsofyourapplicablesoftwarelicenseagreementwithAruba,andtheinformationandprogramsmaybeusedonlypursuanttothetermsandconditionsofsuchagreement.
ThisArubaSecurityAdvisorconstitutesArubaProprietaryInformationandshouldnotbedisseminated,forwardedordisclosed.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
SummaryOnJune29,2011thedefaultSSL/TLScertificate"securelogin.
arubanetworks.
com"thatisinstalledonallArubacontrollerswillexpire.
Whilethisdefaultcertificatewasneverintendedforproductionuse,Arubaisawarethatanumberofcustomersareusingthiscertificateinproductionnetworks.
Thesecustomerswillneedtoreplacethecertificate.
Affectedcustomershavetwooptions:1.
Replacethedefaultcertificatewithacertificateissuedbyaninternalcertificateauthorityorapubliccertificateauthority.
Thisoptionisrecommendedandprovidesthegreatestsecurity.
2.
UpgradetheArubaOSimagetoaversionnumberequaltoorgreaterthan3.
3.
3.
10,3.
4.
4.
2,5.
0.
3.
2,6.
0.
1.
1,or6.
1.
0.
0.
Thesesoftwareimagescontainanewdefaultcertificatethatwillreplacetheexpiringcertificate.
Thisoptiondoesnotprovidegoodsecurity,sinceallArubacustomershaveaccesstothesamecertificateandimpersonationattacksarepossible.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
BackgroundTheArubaOSoperatingsystemloadedonallArubaMobilityControllerscontainsapre-loadeddigitalcertificatewiththename"securelogin.
arubanetworks.
com".
Thiscertificatewasissuedbyapubliccertificateauthority(CA)thatistrustedbymostbrowsersandoperatingsystems.
Bydefaultthecertificateisusedforthecontroller'smanagementinterface(WebUI),captiveportal,andEAPtermination.
Thiscertificateisintendedforquicklysettinguplabnetworks,demonstrations,andproof-of-conceptdeployments.
Asstatedintheuserguide,thedefaultcertificateisnotintendedforproductiondeployment,sinceeveryArubacontrollercontainsthesamecertificateandthisenablesimpersonationattacks.
Thefollowingtextsummarizestherisks:CaptivePortal:Anattackerimpersonatingacaptiveportalloginscreenmaybeabletoobtaintheusernameandpasswordofauthorizedusersonthesystem.
Ifcaptiveportalisusedonlyforguestaccess,thismaynotbedeemedaserioussecurityrisk.
Ifcaptiveportalisusedtoauthenticateinternalusers,thisattackcouldcausemoreseriousdamage.
AdministrativeWebUI:Tocarryoutanimpersonationattackagainstthecontroller'sadministrativeWebUI,theattackerwouldneedtointercepttrafficbetweenasystemadministrator'scomputerandthecontroller.
Thiswouldtypicallyrequireaninsiderattack,assumingadministrativeaccessisblockedfrompublicnetworks.
Theriskisseriousinthiscase,sinceasuccessfulattackwouldallowanunauthorizedpersontoobtainadministrativecredentialsfortheArubacontroller.
TheWebUIcertificateshouldalwaysbereplaced,evenifwithaself-signedcertificatethateachsystemadministratormustexplicitlytrust.
802.
1XEAPTermination:Thisistheriskiestuseofthedefaultcertificate,becauseanimpersonationattackmaybecarriedoutoverawirelessnetwork,andasuccessfulattackmayrevealusernamesandpasswordhashes(providingmaterialforanofflinepasswordcrackingattempt)orallowtheattackertogetauserconnectedtoahostilenetworkwhiletheuserthinksheorsheisconnectedtoatrustednetwork.
Thedefaultcertificateshouldneverbeusedfor802.
1X.
Arubaisawarethatsomecustomersdousethedefaultcertificateinproduction,typicallyforsecuringthecaptiveportalloginscreeninguestnetworkswhereensuringtheidentityofthecontrollerisnotanimportantsecurityconsideration.
Thedefaultcertificatewasvalidforfiveyears,andwillexpireonJune29,2011.
Ifthenetworkadministratordoesnotreplacethecertificate,thefollowingwilloccur:1.
UsersconnectingtocaptiveportalorWebUIpageswillreceiveabrowserwarningshowingthattheservercertificatehasexpired.
Usersmaybypassthewarning(withvaryingdegreesofdifficultydependingonthebrowser)andcontinueontousethesystemnormally.
2.
IfEAPterminationhasbeenenabledfor802.
1X,andthedefaultcertificateisbeingusedastheservercertificate,manyclientoperatingsystemswillrefusetocontinuetheauthenticationprocess.
Thiswillresultinanapparentnetworkoutagefortheseusers.
Clientoperatingsystemsmayormaynotdisplayawarningmessagetotheuser.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
Thisdocumentoutlinestheproceduresneededtoupdatethedefaultcertificate,inorderofpreference:Option1:InstallauniqueservercertificateOption2:UpgradeArubaOS2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
Option1:InstallaUniqueServerCertificateThisistherecommendedapproachsinceitprovidesthebestsecurity.
Inthisapproach,thedefaultcertificatewillremainonthecontroller,butyouwillloadoneormorenewcertificatesandthenconfigurethesystemtousethenewcertificate(s).
Ifyourorganizationoperatesaninternalcertificateauthority(CA)andallclientsthatwillusethesystemalreadytrusttheinternalCA,youmayusetheinternalCAtoissueanewcertificatetothecontroller.
Thisoptionisrecommendedfor802.
1XEAPterminationandWebUIadministrativeaccesstothecontroller.
Itcanalsobeusedforcaptiveportalaslongasthegeneralpublicwillnotbeaccessingthesystem(sincetheinternalCAwillnotbetrusted,thegeneralpublicwouldreceivebrowserwarnings.
)Ifpresentingacaptiveportalpagetocomputersownedbythegeneralpublic,acertificateissuedbyapublicCA(VeriSign,GeoTrust,Comodo,etc.
)shouldbeusedsothatbrowserwarningsarenotgenerated.
YoumaychoosetouseacertificateissuedbyapublicCAforWebUIadministrativeaccesstothecontrollerandfor802.
1XEAPterminationaswell,butuseofapublicCAinsteadofaninternalCAprovidesnobenefitinthosecases.
Beforerequestingacertificate,decidewhetheryouneeda1024-bitkey,2048-bitkey,or4096-bitkey.
NotethatmanypublicCAsnolongerissuecertificateswith1024-bitkeys.
IfyouarerunningArubaOS6.
1orgreater,youmayuseacertificatewitha2048-bitkeyforanypurpose.
Youmayuseacertificatewitha4096-bitkeyonlyforcaptiveportalandWebUI.
ForWebUIorcaptiveportal,performanceisthegreatestwithsmallerkeysizes,butsecurityisslightlyreduced.
Tomaximizecompatibility,alwaysuseRSAunlessyouhaveaspecificreasontouseECC.
Ifyouarerunninganyreleasepriorto6.
1,youmayuseacertificatewitha2048-bitor4096-bitkeyonlyforcaptiveportalandWebUI.
802.
1XEAPterminationsupportsonly1024-bitkeys.
ForWebUIorcaptiveportal,performanceisthegreatestwithsmallerkeysizes,butsecurityisslightlyreduced.
Thefollowinginstructionsshouldbefollowedtoobtainandinstallaservercertificate.
1.
GenerateaCertificateSigningRequest(CSR)fromthecontrollerbynavigatingtoConfigurationManagementCertificatesCSR.
Filloutthenecessaryfields.
Afterclicking"GenerateNew",thecontrollerwillgenerateaprivatekey,whichremainslockedinsidethecontroller,andabase64-encodedCSR.
TheCSRcontainsallthedetailsneededforyourCAtoissuethecertificate.
TheCommonName(CN)fieldshouldcontainthefullURLthatwebbrowserswillnavigatetoinordertoreachthecontroller'sembeddedwebserver.
TakecaretofillouttheCommonNamefieldcorrectlyaccordingtothepurposeofthecertificate:a.
Forcaptiveportal,thesystemwillautomaticallyissueHTTPredirectsandspoofDNSresponsestothecaptiveportalclientsothatthebrowserappearstobeconnectingtothecorrectDNSnamethatmatchesthecertificatecommonname.
Thisistoensurethatbrowserwarningsarenotgenerated.
Ifthecertificateisonlybeingusedforcaptiveportal,thenameintheCNfieldisunimportant–butmakesureitfallswithin2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
yourdomainnamesothatapublicCAwillcorrectlyauthorizeownershipofthecertificate.
b.
ForWebUI,theCNfieldshouldmatchtheaddressyouusetomanagethecontroller.
ThiscanbeanIPaddressoraFullyQualifiedDomainName(FQDN).
c.
For802.
1XEAPTermination,theCNfieldisnotmatchedbytheclientagainstanyotherparameter.
ItissuggestedthatyouchooseaFQDNthatisownedbyyourorganization.
2.
Clickon"ViewCurrent".
Copythebase64textshown,andpastethisintothecertificaterequestwindowprovidedbyyourcertificateauthority.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
3.
Onceyouhaveobtainedthecertificate,navigatetoConfigurationManagementCertificatesUploadanduploadthecertificatetothecontroller.
ThecertificatewillmostlikelybeprovidedtoyouinPEMorDERformat–ifyouarenotsurewhichformatitisin,tryPEMfirstandifanerrormessageresults,tryDER.
APEMformatcertificatewillbebase64-encodedandwillbeginwiththetext"-----BEGINCERTIFICATE-----".
4.
Ifyouwanttousethenewcertificateforcaptiveportal,navigatetoConfigurationManagementGeneralandchangetheCaptivePortalServerCertificate.
IfyouwanttousethenewcertificateforWebUI,configurationisfoundonthesamescreenunder"WebUIManagementAuthenticationMethod".
5.
IfyouwanttousethenewcertificateforEAPTermination,navigatetoConfigurationSecurityAuthenticationL2Authentication802.
1XAuthentication2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
ProfileAdvancedandchangetheservercertificateforallactive802.
1XauthenticationprofilesthatuseEAPTermination.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
Option2:UpgradeArubaOSArubahasobtainedanewcertificatelabeled"securelogin.
arubanetworks.
com"fromapublicCAthatreplacestheolddefaultcertificate.
ThenewcertificatehasanexpirationdateofNovember21,2013.
ThiscertificateisincludedaspartofthefollowingArubaOSsoftwarereleases:6.
1beginningwithrelease6.
1.
0.
06.
0beginningwithrelease6.
0.
1.
15.
0beginningwithrelease5.
0.
3.
23.
4beginningwithrelease3.
4.
4.
23.
3beginningwithrelease3.
3.
3.
10AllotherArubaOSreleasesdatedlaterthanJune1,2011Afterupgradingtooneoftheabovelistedreleases,nofurtheractionisrequiredtoenablethecertificate.
Ifthesystemwaspreviouslyconfiguredtousethedefaultcertificate,itwillautomaticallyusethenewlyupdatedcertificate.
Whilethisoptionprovidesthesamelevelofsecuritygivenbythepreviousdefaultcertificate,itisnotagoodoptionwhereanysecurityrequirementsexist.
SSL/TLSsecurityisprovidedbythecertificate'sprivatekeybeingkeptsecret.
Ifthecertificate'sprivatekeybecomesknown,itispossibleforanattackertoimpersonateanyserverorwebsiteusingthatcertificatewithouttheknowledgeoftheenduser.
BecausethesamecertificateandprivatekeyareinstalledonallArubacontrollers,anattackerneedonlyreverseengineerasinglesoftwareimagetoobtaintheprivatekey.
Whilethisprocessisnon-trivial,itiscertainlynotbeyondthemeansofaskilledanddeterminedattacker.
ItisalsopossibleforanattackertosimplypurchaseanduseanArubacontrollerforthepurposeofconductinganimpersonationattack.
2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
FAQQ:WhathappensifIhaveconfigured802.
1Xdevicesinmynetworktoonlytrustthe"securelogin.
arubanetworks.
com"certificate,ortoonlytrusttheEquifaxSecureCertificateAuthorityA:Thesedeviceswillneedtobereconfiguredafterinstallationofanewcertificate.
IftheseareWindowsdevices,UNCHECK"Connecttotheseservers"andUNCHECK"EquifaxSecureCertificateAuthority"intheTrustedRootCertificationAuthorities.
Afterconnectingtothecontrollerwiththenewcertificateinstalled,Windowswillupdatethesesettingsbypromptingtheuser.
Q:IsthecertificatebuiltintotheTPMchipaffectedbythisadvisoryA:No.
AllArubacontrollersthatcontainaTrustedPlatformModule(TPM),includingtheM3,3000series,and600series,containacertificateuniquetothecontrollerthathasbeenprogrammedatthefactory.
Thiscertificateisnotexpiringandisnotaffectedbythisadvisory.
ThiscertificateisusedforMaster-Localauthentication,ControlPlaneSecurity(CPsec),andRAPauthentication.
ItisnotsuitableforuseasanSSLcertificatesinceitwasissuedbyAruba'smanufacturingCA,whichisnottrustedbybrowsers.
Q:WhatcertificateauthoritywasusedtogeneratethenewcertificateWhatchainsdoesitcontain2011ArubaNetworksInc.
FurtherdistributionprohibitedwithoutpriorwrittenconsentfromArubaNetworksInc.
ForArubaCustomers,EmployeesandAuthorizedChannelPartnersOnly.
A:ThenewcertificatewasissuedbyPositiveSSL,andultimatelychainsbackuptoUSERTrust,whichisissuedbyAddTrustExternalCARoot.
DevicesconnectingtothenetworkmusthaveUSERTrustinstalledasatrustedrootCAinorderfortheArubafactorydefaultcertificatetobetrusted.
UnderaWindowssystem,thecertificatechainappearsas
- 2011ArubaNetworksInc.相关文档
- cmdmcomodo
- WayBillcomodo
- impactcomodo
- VarParseNumFromStrcomodo
- 丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂丂comodo
- Europeacomodo
DMIT(季度$28.88)调整洛杉矶CN2 GIA优化端口
对于DMIT商家已经关注有一些时候,看到不少的隔壁朋友们都有分享到,但是这篇还是我第一次分享这个服务商。根据看介绍,DMIT是一家成立于2017年的美国商家,据说是由几位留美学生创立的,数据中心位于香港、伯力G-Core和洛杉矶,主打香港CN2直连云服务器、美国CN2直连云服务器产品。最近看到DMIT商家有对洛杉矶CN2 GIA VPS端口进行了升级,不过价格没有变化,依然是季付28.88美元起。...

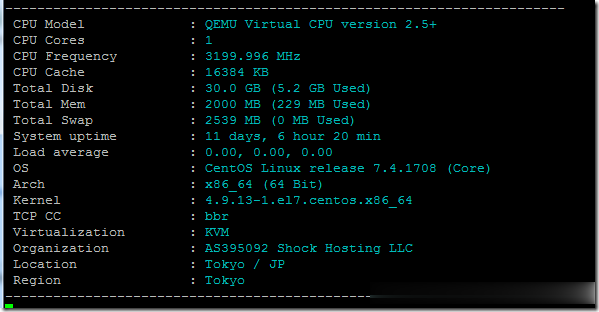
ShockHosting日本机房VPS测试点评
这个月11号ShockHosting发了个新上日本东京机房的邮件,并且表示其他机房可以申请转移到日本,刚好赵容手里有个美国的也没数据就发工单申请新开了一个,这里做个简单的测试,方便大家参考。ShockHosting成立于2013年,目前提供的VPS主机可以选择11个数据中心,包括美国洛杉矶、芝加哥、达拉斯、杰克逊维尔、新泽西、澳大利亚、新加坡、日本、荷兰和英国等。官方网站:https://shoc...
Hostodo:$19.99/年KVM-1GB/12GB/4TB/拉斯维加斯
Hostodo发布了几款采用NVMe磁盘的促销套餐,从512MB内存起,最低年付14.99美元,基于KVM架构,开设在拉斯维加斯机房。这是一家成立于2014年的国外VPS主机商,主打低价VPS套餐且年付为主,基于OpenVZ和KVM架构,产品性能一般,数据中心目前在拉斯维加斯和迈阿密,支持使用PayPal或者支付宝等付款方式。下面列出几款NVMe硬盘套餐配置信息。CPU:1core内存:512MB...

comodo为你推荐
-
独立ip主机独立ip虚拟主机怎么样?是不是真的很好用,和vps有什么区别吗?vps主机vps主机是什么?英文域名中文域名与英文域名区别域名服务商域名服务商所属区域怎么填写便宜的虚拟主机低价虚拟主机那种类型的好呢?100m网站空间100M网站空间可以存多少张图片和多少文字?网站空间申请网站空间申请香港虚拟主机推荐一下香港的虚拟主机公司!万网虚拟主机万网,云服务器和与虚拟主机有什么区别?我是完全不知到的那种,谢谢。用前者还是后者合适。怎么做网页。万网虚拟主机万网云虚拟主机怎么用,如何配置