authenticatezhonguancun
zhonguancun 时间:2021-04-02 阅读:()
CNNICDNSSECPolicyandPracticeStatementforICANNEmergencyBack-EndRegistryOperatorChinaInternetNetworkInformationCenter(CNNIC)Submittedon2018-09-011DocumentControlSECURITYCALSSIFICATIONFileNamePublicDNSSECPolicyandPracticeStatementforICANNEmergencyBack-EndRegistryOperatorAuditsDateVersionUpdateDescription2013-07-18Version-1.
0CNNICEBEROTeamFirstVersion2014-10-15Version-1.
2CNNICEBEROTeamAdjustthestructureofthedocument2017-08-07Version-1.
3CNNICEBEROTeamUpdateManagement,OperationalandPhysicalControl2017-08-28Version-1.
4CNNICEBEROTeamAdjustthestructureofthedocument2017-10-23Version-1.
5GuangTaiXieQuartlyReview2017-12-1Version-1.
5GuangTaiXieQuartlyReview2018-01-16Version-1.
6GuangTaiXieQuartlyReview,FixsomeURLandstatement.
2018-05-08Version-1.
6GuangTaiXieQuartlyReview.
2019-09-03Version-1.
7CNNICEBEROTeamQuartlyReview.
Contents1Introduction31.
1Overview31.
2DocumentNameandIdentification.
31.
3CommunityandApplicability.
41.
4SpecificationAdministration.
52PublicationandRepositories.
52.
1Repositories.
52.
2PublicationofKeySigningKeys(KSK)62.
3AccessControlsonRepositories63OperationalRequirements.
63.
1MeaningofDomainNames.
63.
2ActivationofDNSSECforChildZone.
63.
3IdentificationandAuthenticationofChildZoneManager63.
4RegistrationofDelegationSigner(DS)ResourceRecords63.
5MethodtoProvePossessionofPrivateKey.
73.
6RemovalofDSResourceRecords.
74Facility,Management,andOperationalControl.
74.
1PhysicalControls74.
2ProceduralControls.
94.
3PersonnelControls.
104.
4AuditLoggingProcedures114.
5CompromiseandDisasterRecovery134.
6EntityTermination155TechnicalSecurityControls.
155.
1KeyPairGenerationandInstallation155.
2PrivateKeyProtectionandCryptographicModuleEngineeringControls.
.
.
.
.
.
165.
3OtherAspectsofKeyPairManagement.
185.
4ActivationData.
185.
5ComputerSecurityControls.
195.
6NetworkSecurityControls195.
7Timestamping.
195.
8LifeCycleTechnicalControls.
196ZoneSigning.
206.
1KeyLengths,KeyTypesandAlgorithms.
206.
2AuthenticatedDenialofExistence.
206.
3SignatureFormat.
206.
4ZoneSigningKeyRoll-over.
206.
5KeySigningKeyRoll-over.
216.
6SignatureLife-timeandRe-signingFrequency.
216.
7VerificationofZoneSigningKeySet.
226.
8VerificationofResourceRecords.
226.
9ResourceRecordsTime-to-Live.
227ComplianceAudit.
237.
1FrequencyofEntityComplianceAudit.
237.
2Identity/QualificationsofAuditor.
237.
3Auditor'sRelationshiptoAuditedParty.
237.
4TopicsCoveredbyAudit.
237.
5ActionsTakenasaresultofDeficiency.
237.
6CommunicationofResults248LegalMatters248.
1Fees248.
2FinancialResponsibility.
248.
3ConfidentialityofBusinessInformation.
248.
4PrivacyofPersonalInformation.
258.
5LimitationsofLiability268.
6TermandTermination261Introduction1.
1OverviewDomainNameSystemSecurityExtensions(DNSSEC)areasetofspecificationsfromIETFtoaddsecuritytotheDNS.
DNSSECprovidesamechanismtovalidateDNSdatatoprovethatithasnotbeenmodifiedduringtransitovertheInternet.
ThisisachievedbyincorporatingpublickeycryptographyintotheDNShierarchy,formingachainoftrustoriginatingfromtherootzone.
DNSwasnotoriginallydesignedwithstrongsecuritymechanismstoprovideintegrityandauthenticityofDNSdata.
Overtheyears,anumberofvulnerabilitieshavebeendiscoveredthatthreatenthereliabilityandtrustworthinessofthesystem.
DNSSECaddressesthesevulnerabilitiesbyaddingdataoriginauthentication,dataintegrityverificationandauthenticateddenialofexistencecapabilitiestotheDNS.
Thisdocumentwillprovidethegoverningpoliciesandprovisionsrelatedtothemanagement,securityandtechnicalspecificationsofthe".
TLD"(EBEROeventTLD)KeySigningKey(KSK)andZoneSigningKey(ZSK).
ThisdocumentwillbeunderthecontrolandmanagementofCNNIC.
Informationinthisdocumentandsubsequentdocumentswillbemadepublicasrequired.
1.
2DocumentNameandIdentificationDNSSECPolicyandPracticeStatement.
1.
3CommunityandApplicabilityInthissection,associatedentitiesandtheirrolesaredescribed.
1.
3.
1RegistryWheninanEBEROevent,CNNICwillbetheRegistryfortheTLDtop-leveldomain.
TheRegistryadministratesregistrationsoftheTLDdomainnamesandoperatesDNSserversfortheTLDzone,etc.
AsforDNSSECService,theRegistrygeneratessigningkeys(KSKandZSK)oftheTLDzoneandcompleteszonesigningfortheTLDzone.
Further,throughregisteringdelegationsigner(DS)recordsoftheRegistryintotherootzone,theRegistryenablesoriginauthenticationanddataintegrityverificationofrecordsintheTLDzonebyusingKSKoftherootzoneasatrustanchor.
1.
3.
2RegistrarTheRegistraroftheEBEROeventTLDisanentitywhohasconcludedanagreementwiththeRegistryforagencyoperationsontop-leveldomainnameregistrations.
TheRegistrarisresponsiblefortheadministrationandmanagementofdomainnamesonbehalfoftheRegistrant.
TheRegistrarhandlestheregistration,maintenanceandmanagementofaRegistrant'sdomainnameandisanaccreditedEBEROeventTLD'spartner.
TheRegistrarisresponsibleforsecurelyauthenticationoftheRegistrantofadomain.
TheRegistrarisresponsibleforadding,removingorupdatingspecifiedDSrecordsforeachdomainattherequestoftheRegistrant.
1.
3.
3RegistrantARegistrantisanentitythatcontrolsadomainname.
Registrantsareresponsibleforgeneratingandprotectingtheirownkeys,andregisteringandmaintainingtheDSrecordsthroughtheRegistrar.
TheRegistrantisresponsibleforissuinganemergencykeyrolloverifkeysaresuspectedofbeingcompromisedorhavebeenlost.
TheRegistrantmaydoalltheabovethingsitself.
Butinsomecases,Registrantrequests"DNSProvider"(maybeRegistrarorotherentity),whoprovidesoperationservicesforauthoritativeDNSservers,togeneratesigningkeys,composedigitalsignaturesonRegistrantZoneandgenerateDSrecord(s).
1.
3.
4RelyingPartyRelyingpartyisalltheentityrelatedtotheTLDDNSSECService,includingDNSProviders,cachingDNSserveroperatorsanduserswhoutilizetheirservices.
HerewerefertotheDNSProviderwhomanagesRegistrantZoneas"RegistrantZoneManager".
Insomecases,Registranthim/her-selfmaybeRegistrantZoneManager.
1.
4SpecificationAdministrationThisDPSwillbeperiodicallyreviewedandupdated,asappropriatebytheCNNICEBEROTeam.
CNNICEBEROTeamisresponsibleformanagingtheDPSandshouldbeconsideredthepointofcontactforallmattersrelatedtotheDPS.
1.
4.
1SpecificationAdministrationOrganizationChinaInternetNetworkInformationCenter(CNNIC)4South4thstreet,zhonguancunHaidianqu,BeijingP.
R.
China1.
4.
2ContactInformationCNNICEBEROTeam:ChinaInternetNetworkInformationCenter.
(CNNIC)4South4thstreet,zhonguancunHaidianqu,BeijingP.
R.
ChinaTelephone:+86-10-58813200Fax:+86-10-58812666-123Email:ebero@cnnic.
cnhttps://www.
cnnic.
cn2PublicationandRepositories2.
1RepositoriesCNNICpublishestheDPSinthedocssectionofCNNIC'swebsite,at:http://www.
cnnic.
cn/jscx/dnssec/dnssecdps/2.
2PublicationofKeySigningKeys(KSK)OnceanewgenerationtopleveldomainnamehavingbeenoperatedbyEBERO,thepublickeyoftheKSK(DSrecord)willbepublishedintherootzone2.
3AccessControlsonRepositoriesInformationpublishedinthedocsportionoftheCNNICwebsiteispubliclyaccessibleinformation.
Read-onlyaccesstosuchinformationisunrestricted.
CNNIChasimplementedlogicalandphysicalsecuritymeasurestopreventunauthorizedpersonsfromadding,deleting,ormodifyingrepositoryentries.
3OperationalRequirements3.
1MeaningofDomainNamesTheDNSSECdeploymentpolicyofEBEROeventTLDprovidesDNSSECsupportfordomainnamesofandbelowthesecondlevelthatareendedwith".
TLD".
Butthisrequiresthatallapplicantsandregistrarsfordomainnamesendedwith".
TLD"shouldsubmittoCNNICbothlegaldomainnameswhichconformtotherulesfordomainnamenomenclatureandlegallyauthoritativeresourcerecords.
3.
2ActivationofDNSSECforChildZoneBasedonthefactthatachildzonehasbeendulydelegatedbyCNNIC,theEBEROeventTLDcanprovideDNSSECsupportforthechildzoneafterreceivingitsdelegationsinger(DS).
CNNICwillwritetheDSsubmittedbythechildzoneintothezonefileof".
TLD".
Userscanquerytherecordviatherecursiveserver.
3.
3IdentificationandAuthenticationofChildZoneManagerItistheresponsibilityoftheRegistrartosecurelyidentifyandauthenticatetheRegistrantthroughasuitablemechanism,andincompliancewiththestipulationsinthecontractbetweenCNNICandtheRegistrar.
3.
4RegistrationofDelegationSigner(DS)ResourceRecordsTheEBEROeventTLDregistrydoesnotrequiresecondaryorlowerdomainnamesof".
TLD"tosupportDNSSEC.
Whetheritshouldbesupportedbythesedomainnamestotallydependsontheregistrant.
TofacilitatethesubmissionofDSof".
TLD"childzonesandrealizethebindingofDSrecordswithdomainnameinformation,CNNICneedstoopenDSregistrationchannelstodomainnameregistrars.
CNNICprovidesthefollowingmethodfordomainnameregistrars:1)TheycansubmitDSrecordsviaEPP(RFC5910).
3.
5MethodtoProvePossessionofPrivateKeyTheRegistrydoesnotconductanycontrolswiththeaimofvalidatingtheRegistrantasthemanagerofaprivatekey.
TheRegistrarisresponsibleforconductingthecontrolsthatarerequiredandthosedeemednecessary.
3.
6RemovalofDSResourceRecordsTokeepzonefilesclean,preventuselessDSstoragefromcausingexpansionofzonefilesandpreventzonefilesigningfromtakingtoomuchtime,theadministratorof".
TLD"zonefilesmayremoveaDSresourcerecordinthefollowingtwocases:1)Whena".
TLD"childzoneasksforDSupdating,theoldDSrecordisremoved;2)Whena".
TLD"childzonecancelsitsDNSSECdeploymentandgoesintothenon-DNSSEC-servicestate.
TheoldDSrecordisremoved10dayslaterinsteadofbeingremovedimmediately.
4Facility,Management,andOperationalControl4.
1PhysicalControls4.
1.
1SiteLocationandConstructionToavoidunauthorizedoperationsandleakageofsensitiveinformation,DNSSECoperationandmaintenanceofthe".
TLD"iscarriedoutinastrictlyprotectedphysicalenvironment.
CNNIChasestablishedasoundbackupsystemforallDNSSEC-relatedservicesintheIDCofeachsecondaryoperationcenter,wherethelevelofphysicalprotectionisthesameasthatoftheprimaryoperationcenter.
4.
1.
2PhysicalAccessImportantequipmenthardwaresecuritymodules(HSM)usedfor".
TLD"DNSSECdeploymentmustbeplacedinalockedelectro-magneticshieldingcabinettopreventoutsideelectromagneticsignalsfrominterferingwiththegenerationofkeys.
4.
1.
3PowerandAirConditioningCNNICfacilitiesareequippedwithtwoseparatepowersupplysystems(oneworkingandtheotherstandby)andheating/ventilation/airconditioningsystemtocontroltemperatureandrelativehumiditysothatuninterruptedoperationcanbeensured.
4.
1.
4WaterExposuresCNNIChastakenreasonablemeasurestopreventtheEBEROeventTLDservicesystemfrombeingexposedtowater.
4.
1.
5FirePreventionandProtectionCNNIChastakenreasonablefirepreventionandprotectionmeasures.
Incaseoffire,smokeandflamescansoonbebroughtundercontrol.
Allthesemeasuresmeettherequirementsoflocallawsandregulationsforfirecontrolandprevention.
4.
1.
6MediaStorageAllsoftware,data-containingmedia,auditinginformation,archivesandthecorrespondingbackupinformationarestoredinasecurelocalorremotedeviceforappropriatephysicalandlogicalaccesstopreventthemfromaccidentaldamage(water,fire,electromagneticfields,etc.
)orfrombeingexposedtounauthorizedpersonnel.
4.
1.
7WasteDisposalBeforebeingdiscardedordumped,sensitivepaperdocumentsandmaterialsshallbeshreddedinapapershredder;CD-ROMs,magneticdisks,etc.
,shallbedemagnetizedinademagnetizer;HSMsandotherequipmentshallbephysicallydestroyedorzeroedasperthemanufacturer'sinstruction.
OtheruselessarticlesorgoodsshallbedisposedofinaccordancewiththegeneralproceduresofCNNIC.
4.
1.
8Off-siteBackupKeysystemdata,auditinglogdataandotherimportantinformationrelatedto".
TLD"DNSSECservicewillbestoredintheoff-sitebackupmediaoftheprimaryoperationcenterandthesecondaryoperationcentersinaphysicallyisolatedmanner.
4.
2ProceduralControlsCNNICwillformulatestrictprocedurestocontroltheconstructionanddeploymentofhardwarefacilities.
CNNICwillalsoworkoutrelevantspecificationsandprocedurestocontrolthedeploymentofsoftwareandtostandardizealloperations.
4.
2.
1TrustedRolesTrustedrolesrefertothepersonswho,duringEBEROeventTLDDNSSECoperation,arepermittedtooperateHSMs,generatekeysandparticipateingeneratingandsigningzonefiles.
Tobespecific,theserolesincludethefollowingtwotypes:1)Systemadministrators;2)Systemoperators.
Eachtypeoftheaboverolesisnotauthorizedtodothejoboftheother.
CNNICwillselectandtrainthetrustedrolesinbasicDNSSECskillssothattheywillbecompetentfortheirlaterwork.
Excellentpersonnelfromthesetrustedroleswillbeselectedtobethekeyadministrators(definedin5.
1.
1).
4.
2.
2NumberofPersonsRequiredPerTaskInactualoperation,thenumberofpersonstoplayeachofthetrustedrolesdescribedinSection4.
2.
1isasfollows:1)DuringconstructionofDNSSEChardwareequipmentandenvironment,atleastonepersonperroleshallbepresentatthesite,andoneofthemshallbeinvolvedintheentireprocessofconstructionanddeployment.
2)DuringDNSSECsoftwareserviceanddeployment,atleastonepersonperroleshallbepresentatthesite,andonesystemadministratorshallbeinvolvedintheentireprocessofsoftwaredeployment.
TheSystemoperator(s)shallcheckthecorrectnessofsoftwaredeployment.
3)Eachtimekeysaregeneratedorbackedup,atleastthreepersonsshallbepresentatthesite(theyareallthecurrentkeyadministrators,pleasesee5.
1.
1).
Atleast,twoofthemshallbesystemadministratorsandoneshallbeSystemoperator.
4.
2.
3IdentificationandAuthenticationforEachRoleCNNICwillselecttrustedpersonsfortheimplementationofEBEROeventTLDDNSSECdeploymentaccordingtotheirworkexperience,qualificationsandjobduties.
TheselectedpersonsshallsignaconfidentialityagreementwithCNNICtoundertakeallthemanagementdutiesauthorizedbytheagreement.
TheyshallpromisetokeepconfidentialtheinformationrelatedtoEBEROeventTLDDNSSECdeploymentstrategies.
Theyshallundertakenottodisclosetheinformationtoanythirdparty,orelsetheyshallassumecorrespondinglegalliabilities.
4.
2.
4TasksRequiringSeparationofDuties1)ConstructionofDNSSEChardwareequipmentandenvironment2)DeploymentofDNSSECsoftwareservice3)operationofkeys4.
3PersonnelControls4.
3.
1Qualifications,Experience,andClearanceRequirementsCNNICwillselectanumberoftrustedrolesfortheimplementationofEBEROeventTLDDNSSECdeploymentaccordingtotheirworkexperience,qualificationsandjobduties.
ThesepersonsshallpromisetokeepconfidentialthedetailsrelatedtoEBEROeventTLDDNSSECdeploymentandnottodisclosetheinformationtoanythirdparty.
4.
3.
2BackgroundCheckProceduresAllcandidatesfor".
TLD"trustedrolesshallbesubjecttoaninvestigationintoandassessmentoftheirbackgroundsofatleastthemostrecentthreeyears.
Beforebeingappointedasatrustedrole,acandidateshallbesubjecttoanassessmentofthefollowing:1)Certificationofpriorworkexperience2)Certificationofhighesteducationallevel3)Investigationofanycriminalrecord4)Investigationofpersonalcredit4.
3.
3TrainingRequirementsToimproveemployees'competenceforandsatisfactionwiththeirwork,CNNICwillprovidebasictechnicaltrainingforthemandadjustorupdatethetrainingcourseswhennecessary.
CustomizedtomeettherealneedsofCNNICemployees,thetrainingcoursescoverthefollowingcontents:1)BasicconceptsofDNS/DNSSEC;2)Anintroductionofjobduties;3)Useandmaintenanceofsoftwareandhardwarethathavebeendeployed;4)Proceduresfordisasterrecoveryandbusinesscontinuitymanagement.
4.
3.
4RetrainingFrequencyandRequirementsEverytwoyearsorwhenmajoradjustmentsaremadetothesystemframeworkCNNICwillprovideadditionaltrainingortestingforitsemployeestoimprovetheircompetenceforandsatisfactionwiththework.
4.
3.
5JobRotationFrequencyandSequenceCNNICemployeeswillmutuallyexchangetheirfunctionalrolesonarotatingbasiswhennecessary.
4.
3.
6SanctionsforUnauthorizedActionsSanctionswillbemetedoutforunauthorizedactionsinaccordancewiththeemploymentagreement.
Seriousnegligencemayleadtoterminationoftheemployment.
4.
3.
7ContractingPersonnelRequirementsInsomecasestemporaryemployeesareneededfortheDNSSECoperationandmaintenanceofEBEROeventTLD.
Tobeselectedastrustedroles,theseemployeesmustbesubjecttobackgroundinvestigationandthensignaconfidentialityagreementwhichisthesameaspermanentemployeessign.
Theirworkmustbeundertheguidanceandsupervisionofothertrustedroles.
4.
3.
8DocumentationSuppliedtoPersonnelCNNICprovidesnecessarytraininganddocumentsforitsemployeestoenhancetheircompetenceforandsatisfactionwiththework.
4.
4AuditLoggingProcedures4.
4.
1TypesofEventsRecordedAuditingisperformedmanuallyorautomatically.
CNNICwillrecordthefollowingmajorevents:1)Eventsrelatedto".
TLD"KSK&ZSKlifecyclemanagement,including:Generation,backup,storage,archivedanddeletionofkeys;Exportingofthepublickeys;EventsrelatedtoHSMlifecyclemanagement;2)EventsrelatedtomanagementofKSK&ZSKsigning,including:Activationofkeys;Acceptanceandconfirmationofpublickeysigninginformation;Successorfailureofthesigningprocess;Eventsofkeyrotation;3)Security-relatedevents,including:Successfulorunsuccessfulsystemaccessattempts;Alloperationsperformedbytrustedroles;Writing,readinganddeletingsecurity-sensitivefiles;Systembreakdownsandemergentfailures;IDCentries;Systemchangesorupdates;Handlingoffailures.
Theserecordsshouldincludethedateandtimewhentherecordismade,thetypeandnumberoftherecord,etc.
CNNICwillperiodicallyaudittheserecordsforsecuritysakeandrecordandsolveanyproblemfoundintheauditingprocess.
4.
4.
2FrequencyofProcessingLogCNNICanalyzessomeoftheaboverecordsinareal-timemannerthroughaloganalysissystem.
WhereverthereisanyproblemconcerningDNSSECservice,CNNICwillimmediatelycheckthecorrespondingrecords.
4.
4.
3RetentionPeriodforAuditLogAuditlogsareelectronicallystoredinthelogsystemforatleastonemonth.
Afterthat,thelogswillbearchivedandkeptinthetapelibraryforatleast10years.
4.
4.
4ProtectionofAuditLogThelogsystemandtapelibrarywillrejectunauthorizedaccess,modificationanddeletion.
4.
4.
5AuditLogBackupProceduresLogskeptinthetapelibrarywillbesenttothesecondaryoperationcentersonamonthlybasisforbackup.
4.
4.
6AuditCollectionSystemAuditinformationwillbeautomaticallygeneratedandrecordedattheapplication,networkandoperationsystemlevels.
AuditdatawillbemanuallygeneratedandrecordedbyCNNICemployees.
Electronicinformationwillbeincrementallybackedupintheoperationcenter;paperrecordswillbearchivedbytypeandentryandproperlykept.
4.
4.
7NotificationtoEvent-causingSubjectWhentheauditcollectionsystemrecordsacertainevent,itisunnecessarytonotifytheindividual,organization,equipmentorapplicationprogramthatcausestheevent.
4.
4.
8VulnerabilityAssessmentsRecordsoftheaboveeventmayserveasthenecessarymaterialandbasisforassessingthevulnerabilityofEBEROeventTLDDNSSECserviceoperation.
4.
5CompromiseandDisasterRecovery4.
5.
1IncidentandCompromiseHandlingProceduresDatabasedataisbackedupinthesecondaryoperationcenterssothatoriginalzonefilescanbedirectlygeneratedincaseofanycompromiseordisaster.
KeysarealsobackedupintheHSMofthesecondaryoperationcenterssothattheyareavailablewhenadisasteroccurstotheprimaryoperationcenter.
SeeSection5.
2.
4formoredetail.
4.
5.
2CorruptedComputingResources,Software,and/orDataIncaseofcorruptedcomputingresources,softwareand/ordata,CNNICwillhandletheprobleminaccordancewiththeproceduresspecifiedinthe".
TLD"RegistryEmergencyResponseProgram.
Ifservicecannotberesumedorfailurecannotberemovedinashorttime,CNNICwillconsiderswitchingservicestothesecondaryoperationcenterbyadoptingthedisasterrecoverymechanism.
4.
5.
3EntityPrivateKeyCompromiseProcedures4.
5.
3.
1ZSKCompromiseIncasetheZSKiscrackedorleakedoutanewZSKshallbegeneratedandsigningshallbeperformedusingthenewkey.
TheoldZSKwillbekeptfor10daysandthendeleted.
4.
5.
3.
2KSKCompromiseIncasetheKSKiscrackedorleakedout,itmustbeupdatedimmediately.
Insuchacase,CNNICwillgenerateandannounceanewKSKasquicklyaspossibleandsubmittotherootzoneforaDSrecordcorrespondingtothenewly-generatedKSK.
TherootzonewillsendthenewDSrecordtoallauthoritativeserversanddeletetheoldDSrecord.
Finally,CNNICwilldeletetheoldKSKandusethenewoneforZSKre-signing.
TheinformationofemergentKSKupdatewillbeannouncedthroughCNNICofficialwebsitehttp://www.
cnnic.
cn/gywm/xwzx/xwzxtzgg/andtheCNNICDNSSECmaillist.
InformationoftheleakedKSKanditssignaturewillbekeptbyCNNICfor30daysandthendeleted.
4.
5.
4BusinessContinuityandITDisasterRecoveryCapabilitiesCNNIChasformulateda".
TLD"registrybusinesscontinuityplaninaccordancewiththeContinuityManagementProcedures,asecond-leveldocumentofCNNICinformationsecuritymanagementsystem(ISMS).
FormulatedwithreferencetotherequirementsofISO27001oncontinuity,theContinuityManagementProceduresclarifiesthattheaimofcontinuitymanagementistocombinepreventionwithresumptionofcontrol;proactivelyguardagainstanddealwithIT-relatedemergentevents;avoidinterruptionofoperationalactivities;confinetheimpactofIT-relatedemergenteventsonCNNICtowithinabearablelimit;andensurethecontinuityofcoreservices,byestablishingacontinuitymanagementsystemfeaturedby"soundmechanism,centralizedleadership,clearaccountability,proactiveprevention,quickresponseandefficientdisposal".
TheOperationContinuityManagementProceduresalsoclarifiesthemethodsforandcontentsoftheimplementationoftheregistrycontinuityplan.
The".
TLD"RegistryEmergencyResponseProgramhasdesignedspecificproceduresforvariouspre-setscenariosandclarifiedtheoperationsofpersonnelondifferentworkpostsinhandlingemergentevents.
Thepre-setscenariosaredesignedbasedonthethreatsidentifiedthroughriskanalysesandCNNIC'sexperienceinoperatingthe".
TLD"domainnamesystem.
Thesescenariosmainlyincludethosewheresecurityeventsareverylikelytooccurorwhereeventsthatonceoccurredmayleadto"significant"ormoreserioussecurityevents.
Theyalsoincludethescenarioswheresecurityeventsarenotlikelytooccurbutoncetheyoccur,theywillconstituteanextremelygreatsecuritythreat.
Meanwhile,pre-setemergentscenarioswillbeenrichedaccordingtorealsituationssothattheEmergencyResponseProgramcanbecontinuouslyimproved.
4.
6EntityTerminationIfCNNICdecidestoterminatetheEBERPeventTLDregistryservice,itshallnotifyICANNofitsdecisioninadvanceandthetransitionprocesscanbestartedafterICANNhasselectedanewRegistry.
Toensuretheavailabilityandcontinuityofregistryserviceduringthetransitionprocess,CNNICshallhaveconsultationswiththenewRegistryaboutkeyrotation.
5TechnicalSecurityControls5.
1KeyPairGenerationandInstallation5.
1.
1KeyPairGenerationAllpairsofkeys(ZSKandKSK)inusearegeneratedintheHSMinasecureway.
ThecryptographicmodulemeetsthestandardofChineseauthoritiesandrelevantinternationalstandards.
FivekeyadministratorsaccountaregeneratedduringtheHSMinitializationprocess,andonlymorethanhalfofthemhavepassedidentityauthenticationcantheHSMbeaccessed.
Generationofkeysisperformedbywell-trainedkeyadministrators.
Atleastthreekeyadministrators(AppointingatleasttwosystemadministratorsandatleastoneSystemoperatorisallowedinanemergencysituation)willbeinvolvedintheentireprocessofkeygenerationanddesignatedauditingpersonnelwillbepresenttosuperviseandrecordtheprocess.
5.
1.
2PublicKeyDeliveryEachpublickeyofKSKgeneratedwillbeexportedfromtheHSManditsvaliditywillbeverifiedbySystemoperators.
ThenitwillbesenttoICANNandatthesametimetheinformationwillbepublishedontheofficialwebsiteofCNNIC.
5.
1.
3PublicKeyParametersGenerationandQualityCheckingBasicparametersforgenerationofkeysusedfortheDNSSECdeploymentofEBEROeventTLDareasfollows:1)KSKgenerationalgorithmandkeylength:RSA-SHA2562048bits2)ZSKgenerationalgorithmandkeylength:RSA-SHA2561024bitsInadditionCNNICwilladjusttheaboveparameterswhennecessaryaccordingtorealsituationstoensurethatthekeysaresufficientlysafeandprotectthemfrombeingcracked.
5.
1.
4KeyUsagePurposesAllkeysgeneratedwillbeusedonlyforthepurposeoftheEBEROeventTLDdeploymentratherthananyotherpurposes.
ZSKisusedforsigningeachDNSresourcerecordsset(RRset)oftheEBEROeventTLDzonefiles.
KSKisusedforsigningDNSKEYRRsetof".
TLD"zonefiles.
5.
2PrivateKeyProtectionandCryptographicModuleEngineeringControlsAfterbeinggenerated,keys(ZSKandKSK)aredirectlystoredintheHSM.
5.
2.
1CryptographicModuleStandardsandControlsThecryptographicmodulemeetsthestandardofChineseauthoritiesandrelevantinternationalstandards.
FivekeyadministratorsaccountaregeneratedduringtheHSMinitializationprocess,andonlymorethanhalfofthemhavepassedidentityauthenticationcantheHSMbeaccessed.
5.
2.
2PrivateKey(m-of-n)Multi-personControlTheHSMprovideskeybackupfunctions.
Itdividesanencryptedkeyinto5segmentsandstorestheminfivedifferentsmartcards,eachkeptbyankeyadministrator.
Inemergentcases,thekeyintheHSMcanberestoredusingany3ofthesegments.
5.
2.
3PrivateKeyEscrowCNNIC(theRegistry)doesnotescrowprivatekeys.
5.
2.
4PrivateKeyBackupAfterbeinggenerated,privatekeysarebackedupinanotherHSMwithidenticalconfigurationusingaspecialkey-backupcard.
InadditionCNNICwillsendatleastthreekeyadministrator(Appointingatleastonesystemadministratorsisallowedinanemergencysituation)carryingspecialkey-backupcardtothesecondaryoperationcentersonaregularbasistobackthemupintheHSMofthesecondaryoperationcenter.
5.
2.
5PrivateKeyStorageonCryptographicModuleItisforbiddentoaccessorreadprivatekeysinanyplaintextformbutitispermittedtobackuptheirinformationinspecialkey-backupcardinancryptographicmanner.
5.
2.
6PrivateKeyArchivalPrivatekeysareusedforbackuponlyandshallnotbeusedinanyotherform.
Meanwhile,informationofprivatekeybackupwillberecordedandacorrespondingarchivewillbecreatedforthispurpose.
5.
2.
7PrivateKeyTransferintoorfromaCryptographicModuleTheHSMthatgeneratesprivatekeyssupportszonesigning(encryption)functions.
Afteraprivatekeyisgenerated,theHSMwilldirectlyexportittothecryptographicmoduleforuseviaaninternalphysicalprocessunit.
5.
2.
8MethodofActivatingPrivateKeyPrivatekeysareautomaticallyactivatedbytheHSMbasedonpre-settimingparameterswithoutanyneedforhumanintervention.
5.
2.
9MethodofDeactivatingPrivateKeyPrivatekeysareautomaticallydeactivatedbytheHSMbasedonpre-settimingparameterswhentheyexpire,withoutanyneedforartificialintervention.
5.
2.
10MethodofDestroyingPrivateKeyPrivatekeysstoredintheHSMareautomaticallydestroyedwhentheyexpire,withoutanyneedforhumanintervention.
Privatekeysstoredinthekey-backupcardandbackupHSMaredeletedinastandardmannerasspecified,andsuchaprocessissupervisedandrecordedbydesignatedpersonnel.
5.
3OtherAspectsofKeyPairManagement5.
3.
1PublicKeyArchivalPublickeyswillbearchivedtogetherwithothertypesoftraceableinformationsuchaslogdata.
5.
3.
2KeyUsagePeriodsWhenkeysexpiretheywillbedeletedfromthesigningsystemandwillnotbeusedanymore.
TheusageperiodofZSKis3monthsandthatofKSKis12months.
Therecordofsigningisvalidfor30days.
5.
4ActivationDataTheactivationdataisthepersonalpassphraseforthecardofeachkeyadministratorthatisusedtoactivatetheHSM.
5.
4.
1ActivationDataGenerationandInstallationEachkeyisresponsibleforcreatingtheirownactivationdatapursuanttotheapplicablerequirementsofatleastninecharactersofvaryingnature.
5.
4.
2ActivationDataProtectionKeyadministratorsarerequiredtosafeguardtheircardandsignanagreementacknowledgingtheirresponsibilities.
EachKeyadministratorisresponsibleforprotectingtheiractivationdatainthebestpossibleway.
Onthesuspicionofcompromisedactivationdata,theKeyadministratormustimmediatelychangeit.
5.
5ComputerSecurityControlsInDNSSECdeploying".
TLD",specificservers(forzonefilegeneration)areallowedtoaccessHSM.
Theauthorityofaccesstosuchserversshouldberestrictedandcontrolledsothatonlytrustedrolescangetaccesstothem.
Accesscontrolpoliciesshouldalsobemadeforotherserversthatcommunicatewiththeaboveserverstoensuretheirsecurity.
5.
6NetworkSecurityControlsAllpairsofkeysaregeneratedinHSM.
Toensureitssecurityandpreventotherserversorequipmentinthenetworkfromaccessingit,aseparatesubnetwillbebuiltfordeployingthekeygenerationsystem.
Thesecurityofthesubnetwillbeensuredbyafirewallandothersecuritymeans.
5.
7TimestampingUTCisadoptedfortimingthevalidityofalllogs,signingrecords,etc.
,relatedtothesigningsystem.
5.
8LifeCycleTechnicalControls5.
8.
1SystemDevelopmentControlsAllsourcecodesarestoredincontrolsystemsofthesameversionandthesecodesarebackedupandarchivedperiodically.
5.
8.
2SecurityManagementControlsCNNICcreatesahashofallsoftwarepackagesinstalledonproductionsystems.
Thishashmaybeusedtoverifytheintegrityofsuchsoftware.
Themonitoringsystemwillalertwhencriticalsoftwarepackagesaremodified.
5.
8.
3LifeCycleSecurityControlsThesignersystemisdesignedtorequireaminimumofmaintenance.
Updatescriticaltothesecurityandoperationsofthesignersystemwillbeappliedafterformaltestingandapproval.
Theoriginofallsoftwareandfirmwarewillbesecurelyauthenticatedbyavailablemeans.
CriticalhardwarecomponentsoftheHSMwillbeprocureddirectlyfromthemanufacturerandtransportedintamper-evidentbagstotheirdestinationinthesecurefacility.
Anyhardwarewillbedecommissionedwellbeforethespecifiedlifetimeexpectancy.
6ZoneSigningThispartdealswithtechnicalparametersofkeys,authenticateddenialofexistence,thelifecycleofkeysandrotationpoliciesforDNSSECdeployment.
6.
1KeyLengths,KeyTypesandAlgorithmsFortheEBEROeventTLDDNSSECdeployment,thealgorithmsforkeygenerationandthecorrespondingkeylengthsareasfollows:1)KSKgenerationalgorithmandkeylength:RSA-SHA2562048bits2)ZSKgenerationalgorithmandkeylength:RSA-SHA2561024bits6.
2AuthenticatedDenialofExistenceTopreventunauthorizedpeoplefromviciouslyscanning".
TLD"zonefilesandprotect".
TLD"zonedata,NSEC3(RFC5155)isadoptedforDNSSECdeployment.
6.
3SignatureFormatThesignatureformatin".
TLD"zonefilesconformstothestandardformatdefinedinRFC4034.
6.
4ZoneSigningKeyRoll-overTopreventthekeysfrombeingcrackedorleakedout,ZSKshouldbereplacedandrotatedonaregularbasis.
TheZSKroll-overpolicyistoadoptapre-publishmechanism(RFC4641).
ThevalidityperiodofeachZSKgeneratedis100daysandtheroll-overcycleis90days.
Figure1ZSKRoll-overCycle6.
5KeySigningKeyRoll-overAsthefoundationofthechainoftrustofDNSSEC,theKSKshouldalsoberotatedonaregularbasistopreventitfrombeingcrackedorleakedout.
TheKSKroll-overpolicyistoadoptadouble-signaturemechanism(RFC4641).
ThevalidityperiodofeachKSKgeneratedis13monthsandtheroll-overcycleis12months.
DuringtheKSKroll-overperiod,the".
TLD"zoneadministratorshallsubmittheDSrecordrelatedtothenewKSKtotherootzoneadministratorsoastomaintaintheintegrityofthechainoftrust.
Figure2KSKRoll-overCycle6.
6SignatureLife-timeandRe-signingFrequencyThesignaturevalidityperiod,withoutexception,is30daysforallresourcerecords(RRSIG,RFC4034)of".
TLD"zonesignatures,allofwhichshallbere-signedwhentheyexpire.
Sothere-signingfrequencyisonceevery30days.
Inaddition,re-signingisalsonecessaryeachtimeZSKorKSKisrotated.
ZonesigningwillbeexecutedintheHSM,forwhichthebasicproceduresareasfollows:1)ThehiddenprimarymasterobtainsresourcerecordsfromtheEBEROeventTLDregistrationdatabaseandgeneratestheoriginalzonefile;2)ThehiddenprimarymastersecurelysendstheoriginalzonefiletoHSM;3)HSMreadstheconfigurationfilesforzonesigningandgeneratesthekeysneeded,includingKSKandZSK;4)HSMexecuteszonesigningusingZSKandKSK;5)Whenzonesigningiscompleted,HSMsendsthefilesthathavebeensignedbacktothehiddenprimarymaster;6)Thezonefilesthathavebeensignedareloadedontothehiddenprimarymaster,whichwillthenupdatedatatothesecondarymasterservers.
Figure3".
TLD"ZoneFileSigning6.
7VerificationofZoneSigningKeySetToensuresignaturesandthevalidityperiodofkeys,securitycontrolsareconductedagainsttheDNSKEYpriortopublishingzoneinformationontheInternet.
ThisisdonebyverifyingthechainfromDSintherootzonetoKSK,ZSKandthesignatureoverthe".
TLD"SOA.
6.
8VerificationofResourceRecordsTheRegistryverifiesthatallresourcerecordsarevalidinaccordancewiththecurrentstandardspriortodistribution.
6.
9ResourceRecordsTime-to-LiveTheTTLofDNSSEC-relatedresourcerecordsin".
TLD"zonefilesissettobeoneday,whichisconsistentwiththeTTLofotherDNSresourcerecordsinthezonefiles.
7ComplianceAudit7.
1FrequencyofEntityComplianceAuditComplianceauditsareconductedatleastannuallyatthesoleexpenseoftheauditedentity.
7.
2Identity/QualificationsofAuditorCNNIC'scomplianceauditsareperformedbyapublicaccountingfirmthatdemonstratesproficiencyinDNSSECpublickeyinfrastructuretechnology,informationsecuritytoolsandtechniques,securityauditing,andthethird-partyattestationfunction,whichrequiresthepossessionofcertainskillsets,qualityassurancemeasuressuchaspeerreview,competencytesting,standardswithrespecttoproperassignmentofstafftoengagements,andrequirementsforcontinuingprofessionaleducation.
7.
3Auditor'sRelationshiptoAuditedPartyComplianceauditsofCNNIC'soperationsareperformedbyapublicaccountingfirmthatisindependentofCNNIC.
Thirdpartyauditorsdonotparticipateinthemulti-personcontrolforthe".
TLD"ZSKandKSK.
7.
4TopicsCoveredbyAuditThescopeofCNNIC'sannualcomplianceauditincludesallDNSSECoperationssuchaskeyenvironmentalcontrols,keymanagementoperations,infrastructure/administrativecontrols,KSKandZSKandsignaturelifecyclemanagementandpracticesdisclosure.
7.
5ActionsTakenasaresultofDeficiencyWithrespecttocomplianceauditsofCNNIC'soperations,significantexceptionsordeficienciesidentifiedduringthecomplianceauditwillresultinadeterminationofactionstobetaken.
ThisdeterminationismadebyCNNICmanagementwithinputfromtheauditor.
CNNICmanagementisresponsiblefordevelopingandimplementingacorrectiveactionplan.
IfCNNICdeterminesthatsuchexceptionsordeficienciesposeanimmediatethreattothesecurityorintegrityofthe".
TLD"KSKand/orZSK,acorrectiveactionplanwillbedevelopedwithin30daysandimplementedwithinacommerciallyreasonableperiodoftime.
Forlessseriousexceptionsordeficiencies,CNNICmanagementwillevaluatethesignificanceofsuchissuesanddeterminetheappropriatecourseofaction.
7.
6CommunicationofResultsTheauditingmanagershallsubmitawrittenreportoftheauditresultstoCNNICnotlaterthan30calendardaysaftertheaudit.
8LegalMatters8.
1FeesTheEBEROeventTLDRegsitrydoesnotchargeRegistrarsanyfeesforDNSSEC.
8.
2FinancialResponsibilityNotapplicable.
8.
3ConfidentialityofBusinessInformation8.
3.
1ScopeofConfidentialInformationThefollowingrecordsshallbekeptconfidentialandprivate(Confidential/PrivateInformation):1)PrivatekeysandinformationneededtorecoversuchPrivateKeys2)Transactionalrecords(bothfullrecordsandtheaudittrailoftransactions)3)AudittrailrecordscreatedorretainedbyCNNIC4)AuditreportscreatedbyCNNIC(totheextentsuchreportsaremaintained),andtheirrespectiveauditors(whetherinternalorpublic)5)Contingencyplanninganddisasterrecoveryplans6)SecuritymeasurescontrollingtheoperationsofCNNIChardwareandsoftwareandtheadministrationofDNSKeys8.
3.
2TypesofInformationnotConsideredConfidentialAllinformationpertainingtothedatabaseoftopleveldomainsispublicinformation.
PublicKeys,KeyRevocation,andotherstatusinformation,aswellasCNNICpublicationandinformationcontainedwithinthemarenotconsideredConfidential/PrivateInformation.
8.
3.
3ResponsibilitytoProtectConfidentialInformationCNNICsecuresconfidentialinformationagainstcompromiseanddisclosuretothirdparties.
8.
4PrivacyofPersonalInformation8.
4.
1InformationTreatedasPrivateTotheextentCNNICreceivesorprocesses,onbehalfofacustomer,personallyidentifiableinformation(PII)inthecourseofproviding".
TLD"Zoneservices,suchPIIistreatedasprivateinaccordancewiththetermsofCNNIC'sagreementswithRegistrarsandCNNIC'sPrivacyPolicy.
8.
4.
2InformationnotDeemedPrivateSubjecttoapplicablelaws,allinformationrequiredtobepublishedaspartofawhoisdatabaseisnotdeemedprivate.
8.
4.
3ResponsibilitytoProtectPrivateInformationInproviding".
TLD"Zoneservices,CNNICactsasadatacontroller,andanyobligationsthatCNNICmayhavewithrespecttoanypersonallyidentifiableinformationisgoverned,subjecttoapplicablelaw,bythetermsofCNNIC'sagreementswithregistrarsandtotheextentnotgovernedbyanyapplicableRegistryRegistraragreement.
8.
4.
4DisclosurePursuanttoJudicialorAdministrativeProcessCNNICshallbeentitledtodiscloseConfidential/PrivateInformationif,ingoodfaith,CNNICbelievesthatsuchdisclosureisnecessaryinresponsetojudicial,administrative,orotherlegalprocessduringthediscoveryprocessinaciviloradministrativeaction,suchassubpoenas,interrogatories,requestsforadmission,andrequestsforproductionofdocuments.
8.
5LimitationsofLiabilityCNNICshallnotbeliableforanyfinanciallossorlossesarisingfromincidentaldamageorimpairmentresultingfromitsperformanceofitsobligationshereunderorthe".
TLD"ZoneManager'sorthe".
TLD"ZoneKSKandZSKOperator'sperformanceoftheirrespectiveobligationsunderDNSSECPracticeStatementforthe".
TLD"ZoneKSKandZSKOperator.
Nootherliability,implicitorexplicit,isaccepted.
8.
6TermandTermination8.
6.
1TermTheDPSbecomeseffectiveuponpublicationontheCNNICwebsite.
AmendmentstothisDPSbecomeeffectiveuponpublicationontheCNNICwebsite.
8.
6.
2TerminationThisDPSisamendedfromtimetotimeandwillremaininforceuntilitisreplacedbyanewversion.
8.
6.
3DisputeResolutionProvisionsDisputesamongDNSSECparticipantsshallberesolvedpursuanttoprovisionsintheapplicableagreementsamongtheparties.
DisputesinvolvingCNNICrequireaninitialnegotiationperiodofsixty(60)daysfollowedbylitigationintheBeijingHaidianDistrictintermediatepeople'scourt,PRC.
8.
6.
4GoverningLawThisDPSshallbegovernedbythelawsofthePeople'sRepublicofChina.
0CNNICEBEROTeamFirstVersion2014-10-15Version-1.
2CNNICEBEROTeamAdjustthestructureofthedocument2017-08-07Version-1.
3CNNICEBEROTeamUpdateManagement,OperationalandPhysicalControl2017-08-28Version-1.
4CNNICEBEROTeamAdjustthestructureofthedocument2017-10-23Version-1.
5GuangTaiXieQuartlyReview2017-12-1Version-1.
5GuangTaiXieQuartlyReview2018-01-16Version-1.
6GuangTaiXieQuartlyReview,FixsomeURLandstatement.
2018-05-08Version-1.
6GuangTaiXieQuartlyReview.
2019-09-03Version-1.
7CNNICEBEROTeamQuartlyReview.
Contents1Introduction31.
1Overview31.
2DocumentNameandIdentification.
31.
3CommunityandApplicability.
41.
4SpecificationAdministration.
52PublicationandRepositories.
52.
1Repositories.
52.
2PublicationofKeySigningKeys(KSK)62.
3AccessControlsonRepositories63OperationalRequirements.
63.
1MeaningofDomainNames.
63.
2ActivationofDNSSECforChildZone.
63.
3IdentificationandAuthenticationofChildZoneManager63.
4RegistrationofDelegationSigner(DS)ResourceRecords63.
5MethodtoProvePossessionofPrivateKey.
73.
6RemovalofDSResourceRecords.
74Facility,Management,andOperationalControl.
74.
1PhysicalControls74.
2ProceduralControls.
94.
3PersonnelControls.
104.
4AuditLoggingProcedures114.
5CompromiseandDisasterRecovery134.
6EntityTermination155TechnicalSecurityControls.
155.
1KeyPairGenerationandInstallation155.
2PrivateKeyProtectionandCryptographicModuleEngineeringControls.
.
.
.
.
.
165.
3OtherAspectsofKeyPairManagement.
185.
4ActivationData.
185.
5ComputerSecurityControls.
195.
6NetworkSecurityControls195.
7Timestamping.
195.
8LifeCycleTechnicalControls.
196ZoneSigning.
206.
1KeyLengths,KeyTypesandAlgorithms.
206.
2AuthenticatedDenialofExistence.
206.
3SignatureFormat.
206.
4ZoneSigningKeyRoll-over.
206.
5KeySigningKeyRoll-over.
216.
6SignatureLife-timeandRe-signingFrequency.
216.
7VerificationofZoneSigningKeySet.
226.
8VerificationofResourceRecords.
226.
9ResourceRecordsTime-to-Live.
227ComplianceAudit.
237.
1FrequencyofEntityComplianceAudit.
237.
2Identity/QualificationsofAuditor.
237.
3Auditor'sRelationshiptoAuditedParty.
237.
4TopicsCoveredbyAudit.
237.
5ActionsTakenasaresultofDeficiency.
237.
6CommunicationofResults248LegalMatters248.
1Fees248.
2FinancialResponsibility.
248.
3ConfidentialityofBusinessInformation.
248.
4PrivacyofPersonalInformation.
258.
5LimitationsofLiability268.
6TermandTermination261Introduction1.
1OverviewDomainNameSystemSecurityExtensions(DNSSEC)areasetofspecificationsfromIETFtoaddsecuritytotheDNS.
DNSSECprovidesamechanismtovalidateDNSdatatoprovethatithasnotbeenmodifiedduringtransitovertheInternet.
ThisisachievedbyincorporatingpublickeycryptographyintotheDNShierarchy,formingachainoftrustoriginatingfromtherootzone.
DNSwasnotoriginallydesignedwithstrongsecuritymechanismstoprovideintegrityandauthenticityofDNSdata.
Overtheyears,anumberofvulnerabilitieshavebeendiscoveredthatthreatenthereliabilityandtrustworthinessofthesystem.
DNSSECaddressesthesevulnerabilitiesbyaddingdataoriginauthentication,dataintegrityverificationandauthenticateddenialofexistencecapabilitiestotheDNS.
Thisdocumentwillprovidethegoverningpoliciesandprovisionsrelatedtothemanagement,securityandtechnicalspecificationsofthe".
TLD"(EBEROeventTLD)KeySigningKey(KSK)andZoneSigningKey(ZSK).
ThisdocumentwillbeunderthecontrolandmanagementofCNNIC.
Informationinthisdocumentandsubsequentdocumentswillbemadepublicasrequired.
1.
2DocumentNameandIdentificationDNSSECPolicyandPracticeStatement.
1.
3CommunityandApplicabilityInthissection,associatedentitiesandtheirrolesaredescribed.
1.
3.
1RegistryWheninanEBEROevent,CNNICwillbetheRegistryfortheTLDtop-leveldomain.
TheRegistryadministratesregistrationsoftheTLDdomainnamesandoperatesDNSserversfortheTLDzone,etc.
AsforDNSSECService,theRegistrygeneratessigningkeys(KSKandZSK)oftheTLDzoneandcompleteszonesigningfortheTLDzone.
Further,throughregisteringdelegationsigner(DS)recordsoftheRegistryintotherootzone,theRegistryenablesoriginauthenticationanddataintegrityverificationofrecordsintheTLDzonebyusingKSKoftherootzoneasatrustanchor.
1.
3.
2RegistrarTheRegistraroftheEBEROeventTLDisanentitywhohasconcludedanagreementwiththeRegistryforagencyoperationsontop-leveldomainnameregistrations.
TheRegistrarisresponsiblefortheadministrationandmanagementofdomainnamesonbehalfoftheRegistrant.
TheRegistrarhandlestheregistration,maintenanceandmanagementofaRegistrant'sdomainnameandisanaccreditedEBEROeventTLD'spartner.
TheRegistrarisresponsibleforsecurelyauthenticationoftheRegistrantofadomain.
TheRegistrarisresponsibleforadding,removingorupdatingspecifiedDSrecordsforeachdomainattherequestoftheRegistrant.
1.
3.
3RegistrantARegistrantisanentitythatcontrolsadomainname.
Registrantsareresponsibleforgeneratingandprotectingtheirownkeys,andregisteringandmaintainingtheDSrecordsthroughtheRegistrar.
TheRegistrantisresponsibleforissuinganemergencykeyrolloverifkeysaresuspectedofbeingcompromisedorhavebeenlost.
TheRegistrantmaydoalltheabovethingsitself.
Butinsomecases,Registrantrequests"DNSProvider"(maybeRegistrarorotherentity),whoprovidesoperationservicesforauthoritativeDNSservers,togeneratesigningkeys,composedigitalsignaturesonRegistrantZoneandgenerateDSrecord(s).
1.
3.
4RelyingPartyRelyingpartyisalltheentityrelatedtotheTLDDNSSECService,includingDNSProviders,cachingDNSserveroperatorsanduserswhoutilizetheirservices.
HerewerefertotheDNSProviderwhomanagesRegistrantZoneas"RegistrantZoneManager".
Insomecases,Registranthim/her-selfmaybeRegistrantZoneManager.
1.
4SpecificationAdministrationThisDPSwillbeperiodicallyreviewedandupdated,asappropriatebytheCNNICEBEROTeam.
CNNICEBEROTeamisresponsibleformanagingtheDPSandshouldbeconsideredthepointofcontactforallmattersrelatedtotheDPS.
1.
4.
1SpecificationAdministrationOrganizationChinaInternetNetworkInformationCenter(CNNIC)4South4thstreet,zhonguancunHaidianqu,BeijingP.
R.
China1.
4.
2ContactInformationCNNICEBEROTeam:ChinaInternetNetworkInformationCenter.
(CNNIC)4South4thstreet,zhonguancunHaidianqu,BeijingP.
R.
ChinaTelephone:+86-10-58813200Fax:+86-10-58812666-123Email:ebero@cnnic.
cnhttps://www.
cnnic.
cn2PublicationandRepositories2.
1RepositoriesCNNICpublishestheDPSinthedocssectionofCNNIC'swebsite,at:http://www.
cnnic.
cn/jscx/dnssec/dnssecdps/2.
2PublicationofKeySigningKeys(KSK)OnceanewgenerationtopleveldomainnamehavingbeenoperatedbyEBERO,thepublickeyoftheKSK(DSrecord)willbepublishedintherootzone2.
3AccessControlsonRepositoriesInformationpublishedinthedocsportionoftheCNNICwebsiteispubliclyaccessibleinformation.
Read-onlyaccesstosuchinformationisunrestricted.
CNNIChasimplementedlogicalandphysicalsecuritymeasurestopreventunauthorizedpersonsfromadding,deleting,ormodifyingrepositoryentries.
3OperationalRequirements3.
1MeaningofDomainNamesTheDNSSECdeploymentpolicyofEBEROeventTLDprovidesDNSSECsupportfordomainnamesofandbelowthesecondlevelthatareendedwith".
TLD".
Butthisrequiresthatallapplicantsandregistrarsfordomainnamesendedwith".
TLD"shouldsubmittoCNNICbothlegaldomainnameswhichconformtotherulesfordomainnamenomenclatureandlegallyauthoritativeresourcerecords.
3.
2ActivationofDNSSECforChildZoneBasedonthefactthatachildzonehasbeendulydelegatedbyCNNIC,theEBEROeventTLDcanprovideDNSSECsupportforthechildzoneafterreceivingitsdelegationsinger(DS).
CNNICwillwritetheDSsubmittedbythechildzoneintothezonefileof".
TLD".
Userscanquerytherecordviatherecursiveserver.
3.
3IdentificationandAuthenticationofChildZoneManagerItistheresponsibilityoftheRegistrartosecurelyidentifyandauthenticatetheRegistrantthroughasuitablemechanism,andincompliancewiththestipulationsinthecontractbetweenCNNICandtheRegistrar.
3.
4RegistrationofDelegationSigner(DS)ResourceRecordsTheEBEROeventTLDregistrydoesnotrequiresecondaryorlowerdomainnamesof".
TLD"tosupportDNSSEC.
Whetheritshouldbesupportedbythesedomainnamestotallydependsontheregistrant.
TofacilitatethesubmissionofDSof".
TLD"childzonesandrealizethebindingofDSrecordswithdomainnameinformation,CNNICneedstoopenDSregistrationchannelstodomainnameregistrars.
CNNICprovidesthefollowingmethodfordomainnameregistrars:1)TheycansubmitDSrecordsviaEPP(RFC5910).
3.
5MethodtoProvePossessionofPrivateKeyTheRegistrydoesnotconductanycontrolswiththeaimofvalidatingtheRegistrantasthemanagerofaprivatekey.
TheRegistrarisresponsibleforconductingthecontrolsthatarerequiredandthosedeemednecessary.
3.
6RemovalofDSResourceRecordsTokeepzonefilesclean,preventuselessDSstoragefromcausingexpansionofzonefilesandpreventzonefilesigningfromtakingtoomuchtime,theadministratorof".
TLD"zonefilesmayremoveaDSresourcerecordinthefollowingtwocases:1)Whena".
TLD"childzoneasksforDSupdating,theoldDSrecordisremoved;2)Whena".
TLD"childzonecancelsitsDNSSECdeploymentandgoesintothenon-DNSSEC-servicestate.
TheoldDSrecordisremoved10dayslaterinsteadofbeingremovedimmediately.
4Facility,Management,andOperationalControl4.
1PhysicalControls4.
1.
1SiteLocationandConstructionToavoidunauthorizedoperationsandleakageofsensitiveinformation,DNSSECoperationandmaintenanceofthe".
TLD"iscarriedoutinastrictlyprotectedphysicalenvironment.
CNNIChasestablishedasoundbackupsystemforallDNSSEC-relatedservicesintheIDCofeachsecondaryoperationcenter,wherethelevelofphysicalprotectionisthesameasthatoftheprimaryoperationcenter.
4.
1.
2PhysicalAccessImportantequipmenthardwaresecuritymodules(HSM)usedfor".
TLD"DNSSECdeploymentmustbeplacedinalockedelectro-magneticshieldingcabinettopreventoutsideelectromagneticsignalsfrominterferingwiththegenerationofkeys.
4.
1.
3PowerandAirConditioningCNNICfacilitiesareequippedwithtwoseparatepowersupplysystems(oneworkingandtheotherstandby)andheating/ventilation/airconditioningsystemtocontroltemperatureandrelativehumiditysothatuninterruptedoperationcanbeensured.
4.
1.
4WaterExposuresCNNIChastakenreasonablemeasurestopreventtheEBEROeventTLDservicesystemfrombeingexposedtowater.
4.
1.
5FirePreventionandProtectionCNNIChastakenreasonablefirepreventionandprotectionmeasures.
Incaseoffire,smokeandflamescansoonbebroughtundercontrol.
Allthesemeasuresmeettherequirementsoflocallawsandregulationsforfirecontrolandprevention.
4.
1.
6MediaStorageAllsoftware,data-containingmedia,auditinginformation,archivesandthecorrespondingbackupinformationarestoredinasecurelocalorremotedeviceforappropriatephysicalandlogicalaccesstopreventthemfromaccidentaldamage(water,fire,electromagneticfields,etc.
)orfrombeingexposedtounauthorizedpersonnel.
4.
1.
7WasteDisposalBeforebeingdiscardedordumped,sensitivepaperdocumentsandmaterialsshallbeshreddedinapapershredder;CD-ROMs,magneticdisks,etc.
,shallbedemagnetizedinademagnetizer;HSMsandotherequipmentshallbephysicallydestroyedorzeroedasperthemanufacturer'sinstruction.
OtheruselessarticlesorgoodsshallbedisposedofinaccordancewiththegeneralproceduresofCNNIC.
4.
1.
8Off-siteBackupKeysystemdata,auditinglogdataandotherimportantinformationrelatedto".
TLD"DNSSECservicewillbestoredintheoff-sitebackupmediaoftheprimaryoperationcenterandthesecondaryoperationcentersinaphysicallyisolatedmanner.
4.
2ProceduralControlsCNNICwillformulatestrictprocedurestocontroltheconstructionanddeploymentofhardwarefacilities.
CNNICwillalsoworkoutrelevantspecificationsandprocedurestocontrolthedeploymentofsoftwareandtostandardizealloperations.
4.
2.
1TrustedRolesTrustedrolesrefertothepersonswho,duringEBEROeventTLDDNSSECoperation,arepermittedtooperateHSMs,generatekeysandparticipateingeneratingandsigningzonefiles.
Tobespecific,theserolesincludethefollowingtwotypes:1)Systemadministrators;2)Systemoperators.
Eachtypeoftheaboverolesisnotauthorizedtodothejoboftheother.
CNNICwillselectandtrainthetrustedrolesinbasicDNSSECskillssothattheywillbecompetentfortheirlaterwork.
Excellentpersonnelfromthesetrustedroleswillbeselectedtobethekeyadministrators(definedin5.
1.
1).
4.
2.
2NumberofPersonsRequiredPerTaskInactualoperation,thenumberofpersonstoplayeachofthetrustedrolesdescribedinSection4.
2.
1isasfollows:1)DuringconstructionofDNSSEChardwareequipmentandenvironment,atleastonepersonperroleshallbepresentatthesite,andoneofthemshallbeinvolvedintheentireprocessofconstructionanddeployment.
2)DuringDNSSECsoftwareserviceanddeployment,atleastonepersonperroleshallbepresentatthesite,andonesystemadministratorshallbeinvolvedintheentireprocessofsoftwaredeployment.
TheSystemoperator(s)shallcheckthecorrectnessofsoftwaredeployment.
3)Eachtimekeysaregeneratedorbackedup,atleastthreepersonsshallbepresentatthesite(theyareallthecurrentkeyadministrators,pleasesee5.
1.
1).
Atleast,twoofthemshallbesystemadministratorsandoneshallbeSystemoperator.
4.
2.
3IdentificationandAuthenticationforEachRoleCNNICwillselecttrustedpersonsfortheimplementationofEBEROeventTLDDNSSECdeploymentaccordingtotheirworkexperience,qualificationsandjobduties.
TheselectedpersonsshallsignaconfidentialityagreementwithCNNICtoundertakeallthemanagementdutiesauthorizedbytheagreement.
TheyshallpromisetokeepconfidentialtheinformationrelatedtoEBEROeventTLDDNSSECdeploymentstrategies.
Theyshallundertakenottodisclosetheinformationtoanythirdparty,orelsetheyshallassumecorrespondinglegalliabilities.
4.
2.
4TasksRequiringSeparationofDuties1)ConstructionofDNSSEChardwareequipmentandenvironment2)DeploymentofDNSSECsoftwareservice3)operationofkeys4.
3PersonnelControls4.
3.
1Qualifications,Experience,andClearanceRequirementsCNNICwillselectanumberoftrustedrolesfortheimplementationofEBEROeventTLDDNSSECdeploymentaccordingtotheirworkexperience,qualificationsandjobduties.
ThesepersonsshallpromisetokeepconfidentialthedetailsrelatedtoEBEROeventTLDDNSSECdeploymentandnottodisclosetheinformationtoanythirdparty.
4.
3.
2BackgroundCheckProceduresAllcandidatesfor".
TLD"trustedrolesshallbesubjecttoaninvestigationintoandassessmentoftheirbackgroundsofatleastthemostrecentthreeyears.
Beforebeingappointedasatrustedrole,acandidateshallbesubjecttoanassessmentofthefollowing:1)Certificationofpriorworkexperience2)Certificationofhighesteducationallevel3)Investigationofanycriminalrecord4)Investigationofpersonalcredit4.
3.
3TrainingRequirementsToimproveemployees'competenceforandsatisfactionwiththeirwork,CNNICwillprovidebasictechnicaltrainingforthemandadjustorupdatethetrainingcourseswhennecessary.
CustomizedtomeettherealneedsofCNNICemployees,thetrainingcoursescoverthefollowingcontents:1)BasicconceptsofDNS/DNSSEC;2)Anintroductionofjobduties;3)Useandmaintenanceofsoftwareandhardwarethathavebeendeployed;4)Proceduresfordisasterrecoveryandbusinesscontinuitymanagement.
4.
3.
4RetrainingFrequencyandRequirementsEverytwoyearsorwhenmajoradjustmentsaremadetothesystemframeworkCNNICwillprovideadditionaltrainingortestingforitsemployeestoimprovetheircompetenceforandsatisfactionwiththework.
4.
3.
5JobRotationFrequencyandSequenceCNNICemployeeswillmutuallyexchangetheirfunctionalrolesonarotatingbasiswhennecessary.
4.
3.
6SanctionsforUnauthorizedActionsSanctionswillbemetedoutforunauthorizedactionsinaccordancewiththeemploymentagreement.
Seriousnegligencemayleadtoterminationoftheemployment.
4.
3.
7ContractingPersonnelRequirementsInsomecasestemporaryemployeesareneededfortheDNSSECoperationandmaintenanceofEBEROeventTLD.
Tobeselectedastrustedroles,theseemployeesmustbesubjecttobackgroundinvestigationandthensignaconfidentialityagreementwhichisthesameaspermanentemployeessign.
Theirworkmustbeundertheguidanceandsupervisionofothertrustedroles.
4.
3.
8DocumentationSuppliedtoPersonnelCNNICprovidesnecessarytraininganddocumentsforitsemployeestoenhancetheircompetenceforandsatisfactionwiththework.
4.
4AuditLoggingProcedures4.
4.
1TypesofEventsRecordedAuditingisperformedmanuallyorautomatically.
CNNICwillrecordthefollowingmajorevents:1)Eventsrelatedto".
TLD"KSK&ZSKlifecyclemanagement,including:Generation,backup,storage,archivedanddeletionofkeys;Exportingofthepublickeys;EventsrelatedtoHSMlifecyclemanagement;2)EventsrelatedtomanagementofKSK&ZSKsigning,including:Activationofkeys;Acceptanceandconfirmationofpublickeysigninginformation;Successorfailureofthesigningprocess;Eventsofkeyrotation;3)Security-relatedevents,including:Successfulorunsuccessfulsystemaccessattempts;Alloperationsperformedbytrustedroles;Writing,readinganddeletingsecurity-sensitivefiles;Systembreakdownsandemergentfailures;IDCentries;Systemchangesorupdates;Handlingoffailures.
Theserecordsshouldincludethedateandtimewhentherecordismade,thetypeandnumberoftherecord,etc.
CNNICwillperiodicallyaudittheserecordsforsecuritysakeandrecordandsolveanyproblemfoundintheauditingprocess.
4.
4.
2FrequencyofProcessingLogCNNICanalyzessomeoftheaboverecordsinareal-timemannerthroughaloganalysissystem.
WhereverthereisanyproblemconcerningDNSSECservice,CNNICwillimmediatelycheckthecorrespondingrecords.
4.
4.
3RetentionPeriodforAuditLogAuditlogsareelectronicallystoredinthelogsystemforatleastonemonth.
Afterthat,thelogswillbearchivedandkeptinthetapelibraryforatleast10years.
4.
4.
4ProtectionofAuditLogThelogsystemandtapelibrarywillrejectunauthorizedaccess,modificationanddeletion.
4.
4.
5AuditLogBackupProceduresLogskeptinthetapelibrarywillbesenttothesecondaryoperationcentersonamonthlybasisforbackup.
4.
4.
6AuditCollectionSystemAuditinformationwillbeautomaticallygeneratedandrecordedattheapplication,networkandoperationsystemlevels.
AuditdatawillbemanuallygeneratedandrecordedbyCNNICemployees.
Electronicinformationwillbeincrementallybackedupintheoperationcenter;paperrecordswillbearchivedbytypeandentryandproperlykept.
4.
4.
7NotificationtoEvent-causingSubjectWhentheauditcollectionsystemrecordsacertainevent,itisunnecessarytonotifytheindividual,organization,equipmentorapplicationprogramthatcausestheevent.
4.
4.
8VulnerabilityAssessmentsRecordsoftheaboveeventmayserveasthenecessarymaterialandbasisforassessingthevulnerabilityofEBEROeventTLDDNSSECserviceoperation.
4.
5CompromiseandDisasterRecovery4.
5.
1IncidentandCompromiseHandlingProceduresDatabasedataisbackedupinthesecondaryoperationcenterssothatoriginalzonefilescanbedirectlygeneratedincaseofanycompromiseordisaster.
KeysarealsobackedupintheHSMofthesecondaryoperationcenterssothattheyareavailablewhenadisasteroccurstotheprimaryoperationcenter.
SeeSection5.
2.
4formoredetail.
4.
5.
2CorruptedComputingResources,Software,and/orDataIncaseofcorruptedcomputingresources,softwareand/ordata,CNNICwillhandletheprobleminaccordancewiththeproceduresspecifiedinthe".
TLD"RegistryEmergencyResponseProgram.
Ifservicecannotberesumedorfailurecannotberemovedinashorttime,CNNICwillconsiderswitchingservicestothesecondaryoperationcenterbyadoptingthedisasterrecoverymechanism.
4.
5.
3EntityPrivateKeyCompromiseProcedures4.
5.
3.
1ZSKCompromiseIncasetheZSKiscrackedorleakedoutanewZSKshallbegeneratedandsigningshallbeperformedusingthenewkey.
TheoldZSKwillbekeptfor10daysandthendeleted.
4.
5.
3.
2KSKCompromiseIncasetheKSKiscrackedorleakedout,itmustbeupdatedimmediately.
Insuchacase,CNNICwillgenerateandannounceanewKSKasquicklyaspossibleandsubmittotherootzoneforaDSrecordcorrespondingtothenewly-generatedKSK.
TherootzonewillsendthenewDSrecordtoallauthoritativeserversanddeletetheoldDSrecord.
Finally,CNNICwilldeletetheoldKSKandusethenewoneforZSKre-signing.
TheinformationofemergentKSKupdatewillbeannouncedthroughCNNICofficialwebsitehttp://www.
cnnic.
cn/gywm/xwzx/xwzxtzgg/andtheCNNICDNSSECmaillist.
InformationoftheleakedKSKanditssignaturewillbekeptbyCNNICfor30daysandthendeleted.
4.
5.
4BusinessContinuityandITDisasterRecoveryCapabilitiesCNNIChasformulateda".
TLD"registrybusinesscontinuityplaninaccordancewiththeContinuityManagementProcedures,asecond-leveldocumentofCNNICinformationsecuritymanagementsystem(ISMS).
FormulatedwithreferencetotherequirementsofISO27001oncontinuity,theContinuityManagementProceduresclarifiesthattheaimofcontinuitymanagementistocombinepreventionwithresumptionofcontrol;proactivelyguardagainstanddealwithIT-relatedemergentevents;avoidinterruptionofoperationalactivities;confinetheimpactofIT-relatedemergenteventsonCNNICtowithinabearablelimit;andensurethecontinuityofcoreservices,byestablishingacontinuitymanagementsystemfeaturedby"soundmechanism,centralizedleadership,clearaccountability,proactiveprevention,quickresponseandefficientdisposal".
TheOperationContinuityManagementProceduresalsoclarifiesthemethodsforandcontentsoftheimplementationoftheregistrycontinuityplan.
The".
TLD"RegistryEmergencyResponseProgramhasdesignedspecificproceduresforvariouspre-setscenariosandclarifiedtheoperationsofpersonnelondifferentworkpostsinhandlingemergentevents.
Thepre-setscenariosaredesignedbasedonthethreatsidentifiedthroughriskanalysesandCNNIC'sexperienceinoperatingthe".
TLD"domainnamesystem.
Thesescenariosmainlyincludethosewheresecurityeventsareverylikelytooccurorwhereeventsthatonceoccurredmayleadto"significant"ormoreserioussecurityevents.
Theyalsoincludethescenarioswheresecurityeventsarenotlikelytooccurbutoncetheyoccur,theywillconstituteanextremelygreatsecuritythreat.
Meanwhile,pre-setemergentscenarioswillbeenrichedaccordingtorealsituationssothattheEmergencyResponseProgramcanbecontinuouslyimproved.
4.
6EntityTerminationIfCNNICdecidestoterminatetheEBERPeventTLDregistryservice,itshallnotifyICANNofitsdecisioninadvanceandthetransitionprocesscanbestartedafterICANNhasselectedanewRegistry.
Toensuretheavailabilityandcontinuityofregistryserviceduringthetransitionprocess,CNNICshallhaveconsultationswiththenewRegistryaboutkeyrotation.
5TechnicalSecurityControls5.
1KeyPairGenerationandInstallation5.
1.
1KeyPairGenerationAllpairsofkeys(ZSKandKSK)inusearegeneratedintheHSMinasecureway.
ThecryptographicmodulemeetsthestandardofChineseauthoritiesandrelevantinternationalstandards.
FivekeyadministratorsaccountaregeneratedduringtheHSMinitializationprocess,andonlymorethanhalfofthemhavepassedidentityauthenticationcantheHSMbeaccessed.
Generationofkeysisperformedbywell-trainedkeyadministrators.
Atleastthreekeyadministrators(AppointingatleasttwosystemadministratorsandatleastoneSystemoperatorisallowedinanemergencysituation)willbeinvolvedintheentireprocessofkeygenerationanddesignatedauditingpersonnelwillbepresenttosuperviseandrecordtheprocess.
5.
1.
2PublicKeyDeliveryEachpublickeyofKSKgeneratedwillbeexportedfromtheHSManditsvaliditywillbeverifiedbySystemoperators.
ThenitwillbesenttoICANNandatthesametimetheinformationwillbepublishedontheofficialwebsiteofCNNIC.
5.
1.
3PublicKeyParametersGenerationandQualityCheckingBasicparametersforgenerationofkeysusedfortheDNSSECdeploymentofEBEROeventTLDareasfollows:1)KSKgenerationalgorithmandkeylength:RSA-SHA2562048bits2)ZSKgenerationalgorithmandkeylength:RSA-SHA2561024bitsInadditionCNNICwilladjusttheaboveparameterswhennecessaryaccordingtorealsituationstoensurethatthekeysaresufficientlysafeandprotectthemfrombeingcracked.
5.
1.
4KeyUsagePurposesAllkeysgeneratedwillbeusedonlyforthepurposeoftheEBEROeventTLDdeploymentratherthananyotherpurposes.
ZSKisusedforsigningeachDNSresourcerecordsset(RRset)oftheEBEROeventTLDzonefiles.
KSKisusedforsigningDNSKEYRRsetof".
TLD"zonefiles.
5.
2PrivateKeyProtectionandCryptographicModuleEngineeringControlsAfterbeinggenerated,keys(ZSKandKSK)aredirectlystoredintheHSM.
5.
2.
1CryptographicModuleStandardsandControlsThecryptographicmodulemeetsthestandardofChineseauthoritiesandrelevantinternationalstandards.
FivekeyadministratorsaccountaregeneratedduringtheHSMinitializationprocess,andonlymorethanhalfofthemhavepassedidentityauthenticationcantheHSMbeaccessed.
5.
2.
2PrivateKey(m-of-n)Multi-personControlTheHSMprovideskeybackupfunctions.
Itdividesanencryptedkeyinto5segmentsandstorestheminfivedifferentsmartcards,eachkeptbyankeyadministrator.
Inemergentcases,thekeyintheHSMcanberestoredusingany3ofthesegments.
5.
2.
3PrivateKeyEscrowCNNIC(theRegistry)doesnotescrowprivatekeys.
5.
2.
4PrivateKeyBackupAfterbeinggenerated,privatekeysarebackedupinanotherHSMwithidenticalconfigurationusingaspecialkey-backupcard.
InadditionCNNICwillsendatleastthreekeyadministrator(Appointingatleastonesystemadministratorsisallowedinanemergencysituation)carryingspecialkey-backupcardtothesecondaryoperationcentersonaregularbasistobackthemupintheHSMofthesecondaryoperationcenter.
5.
2.
5PrivateKeyStorageonCryptographicModuleItisforbiddentoaccessorreadprivatekeysinanyplaintextformbutitispermittedtobackuptheirinformationinspecialkey-backupcardinancryptographicmanner.
5.
2.
6PrivateKeyArchivalPrivatekeysareusedforbackuponlyandshallnotbeusedinanyotherform.
Meanwhile,informationofprivatekeybackupwillberecordedandacorrespondingarchivewillbecreatedforthispurpose.
5.
2.
7PrivateKeyTransferintoorfromaCryptographicModuleTheHSMthatgeneratesprivatekeyssupportszonesigning(encryption)functions.
Afteraprivatekeyisgenerated,theHSMwilldirectlyexportittothecryptographicmoduleforuseviaaninternalphysicalprocessunit.
5.
2.
8MethodofActivatingPrivateKeyPrivatekeysareautomaticallyactivatedbytheHSMbasedonpre-settimingparameterswithoutanyneedforhumanintervention.
5.
2.
9MethodofDeactivatingPrivateKeyPrivatekeysareautomaticallydeactivatedbytheHSMbasedonpre-settimingparameterswhentheyexpire,withoutanyneedforartificialintervention.
5.
2.
10MethodofDestroyingPrivateKeyPrivatekeysstoredintheHSMareautomaticallydestroyedwhentheyexpire,withoutanyneedforhumanintervention.
Privatekeysstoredinthekey-backupcardandbackupHSMaredeletedinastandardmannerasspecified,andsuchaprocessissupervisedandrecordedbydesignatedpersonnel.
5.
3OtherAspectsofKeyPairManagement5.
3.
1PublicKeyArchivalPublickeyswillbearchivedtogetherwithothertypesoftraceableinformationsuchaslogdata.
5.
3.
2KeyUsagePeriodsWhenkeysexpiretheywillbedeletedfromthesigningsystemandwillnotbeusedanymore.
TheusageperiodofZSKis3monthsandthatofKSKis12months.
Therecordofsigningisvalidfor30days.
5.
4ActivationDataTheactivationdataisthepersonalpassphraseforthecardofeachkeyadministratorthatisusedtoactivatetheHSM.
5.
4.
1ActivationDataGenerationandInstallationEachkeyisresponsibleforcreatingtheirownactivationdatapursuanttotheapplicablerequirementsofatleastninecharactersofvaryingnature.
5.
4.
2ActivationDataProtectionKeyadministratorsarerequiredtosafeguardtheircardandsignanagreementacknowledgingtheirresponsibilities.
EachKeyadministratorisresponsibleforprotectingtheiractivationdatainthebestpossibleway.
Onthesuspicionofcompromisedactivationdata,theKeyadministratormustimmediatelychangeit.
5.
5ComputerSecurityControlsInDNSSECdeploying".
TLD",specificservers(forzonefilegeneration)areallowedtoaccessHSM.
Theauthorityofaccesstosuchserversshouldberestrictedandcontrolledsothatonlytrustedrolescangetaccesstothem.
Accesscontrolpoliciesshouldalsobemadeforotherserversthatcommunicatewiththeaboveserverstoensuretheirsecurity.
5.
6NetworkSecurityControlsAllpairsofkeysaregeneratedinHSM.
Toensureitssecurityandpreventotherserversorequipmentinthenetworkfromaccessingit,aseparatesubnetwillbebuiltfordeployingthekeygenerationsystem.
Thesecurityofthesubnetwillbeensuredbyafirewallandothersecuritymeans.
5.
7TimestampingUTCisadoptedfortimingthevalidityofalllogs,signingrecords,etc.
,relatedtothesigningsystem.
5.
8LifeCycleTechnicalControls5.
8.
1SystemDevelopmentControlsAllsourcecodesarestoredincontrolsystemsofthesameversionandthesecodesarebackedupandarchivedperiodically.
5.
8.
2SecurityManagementControlsCNNICcreatesahashofallsoftwarepackagesinstalledonproductionsystems.
Thishashmaybeusedtoverifytheintegrityofsuchsoftware.
Themonitoringsystemwillalertwhencriticalsoftwarepackagesaremodified.
5.
8.
3LifeCycleSecurityControlsThesignersystemisdesignedtorequireaminimumofmaintenance.
Updatescriticaltothesecurityandoperationsofthesignersystemwillbeappliedafterformaltestingandapproval.
Theoriginofallsoftwareandfirmwarewillbesecurelyauthenticatedbyavailablemeans.
CriticalhardwarecomponentsoftheHSMwillbeprocureddirectlyfromthemanufacturerandtransportedintamper-evidentbagstotheirdestinationinthesecurefacility.
Anyhardwarewillbedecommissionedwellbeforethespecifiedlifetimeexpectancy.
6ZoneSigningThispartdealswithtechnicalparametersofkeys,authenticateddenialofexistence,thelifecycleofkeysandrotationpoliciesforDNSSECdeployment.
6.
1KeyLengths,KeyTypesandAlgorithmsFortheEBEROeventTLDDNSSECdeployment,thealgorithmsforkeygenerationandthecorrespondingkeylengthsareasfollows:1)KSKgenerationalgorithmandkeylength:RSA-SHA2562048bits2)ZSKgenerationalgorithmandkeylength:RSA-SHA2561024bits6.
2AuthenticatedDenialofExistenceTopreventunauthorizedpeoplefromviciouslyscanning".
TLD"zonefilesandprotect".
TLD"zonedata,NSEC3(RFC5155)isadoptedforDNSSECdeployment.
6.
3SignatureFormatThesignatureformatin".
TLD"zonefilesconformstothestandardformatdefinedinRFC4034.
6.
4ZoneSigningKeyRoll-overTopreventthekeysfrombeingcrackedorleakedout,ZSKshouldbereplacedandrotatedonaregularbasis.
TheZSKroll-overpolicyistoadoptapre-publishmechanism(RFC4641).
ThevalidityperiodofeachZSKgeneratedis100daysandtheroll-overcycleis90days.
Figure1ZSKRoll-overCycle6.
5KeySigningKeyRoll-overAsthefoundationofthechainoftrustofDNSSEC,theKSKshouldalsoberotatedonaregularbasistopreventitfrombeingcrackedorleakedout.
TheKSKroll-overpolicyistoadoptadouble-signaturemechanism(RFC4641).
ThevalidityperiodofeachKSKgeneratedis13monthsandtheroll-overcycleis12months.
DuringtheKSKroll-overperiod,the".
TLD"zoneadministratorshallsubmittheDSrecordrelatedtothenewKSKtotherootzoneadministratorsoastomaintaintheintegrityofthechainoftrust.
Figure2KSKRoll-overCycle6.
6SignatureLife-timeandRe-signingFrequencyThesignaturevalidityperiod,withoutexception,is30daysforallresourcerecords(RRSIG,RFC4034)of".
TLD"zonesignatures,allofwhichshallbere-signedwhentheyexpire.
Sothere-signingfrequencyisonceevery30days.
Inaddition,re-signingisalsonecessaryeachtimeZSKorKSKisrotated.
ZonesigningwillbeexecutedintheHSM,forwhichthebasicproceduresareasfollows:1)ThehiddenprimarymasterobtainsresourcerecordsfromtheEBEROeventTLDregistrationdatabaseandgeneratestheoriginalzonefile;2)ThehiddenprimarymastersecurelysendstheoriginalzonefiletoHSM;3)HSMreadstheconfigurationfilesforzonesigningandgeneratesthekeysneeded,includingKSKandZSK;4)HSMexecuteszonesigningusingZSKandKSK;5)Whenzonesigningiscompleted,HSMsendsthefilesthathavebeensignedbacktothehiddenprimarymaster;6)Thezonefilesthathavebeensignedareloadedontothehiddenprimarymaster,whichwillthenupdatedatatothesecondarymasterservers.
Figure3".
TLD"ZoneFileSigning6.
7VerificationofZoneSigningKeySetToensuresignaturesandthevalidityperiodofkeys,securitycontrolsareconductedagainsttheDNSKEYpriortopublishingzoneinformationontheInternet.
ThisisdonebyverifyingthechainfromDSintherootzonetoKSK,ZSKandthesignatureoverthe".
TLD"SOA.
6.
8VerificationofResourceRecordsTheRegistryverifiesthatallresourcerecordsarevalidinaccordancewiththecurrentstandardspriortodistribution.
6.
9ResourceRecordsTime-to-LiveTheTTLofDNSSEC-relatedresourcerecordsin".
TLD"zonefilesissettobeoneday,whichisconsistentwiththeTTLofotherDNSresourcerecordsinthezonefiles.
7ComplianceAudit7.
1FrequencyofEntityComplianceAuditComplianceauditsareconductedatleastannuallyatthesoleexpenseoftheauditedentity.
7.
2Identity/QualificationsofAuditorCNNIC'scomplianceauditsareperformedbyapublicaccountingfirmthatdemonstratesproficiencyinDNSSECpublickeyinfrastructuretechnology,informationsecuritytoolsandtechniques,securityauditing,andthethird-partyattestationfunction,whichrequiresthepossessionofcertainskillsets,qualityassurancemeasuressuchaspeerreview,competencytesting,standardswithrespecttoproperassignmentofstafftoengagements,andrequirementsforcontinuingprofessionaleducation.
7.
3Auditor'sRelationshiptoAuditedPartyComplianceauditsofCNNIC'soperationsareperformedbyapublicaccountingfirmthatisindependentofCNNIC.
Thirdpartyauditorsdonotparticipateinthemulti-personcontrolforthe".
TLD"ZSKandKSK.
7.
4TopicsCoveredbyAuditThescopeofCNNIC'sannualcomplianceauditincludesallDNSSECoperationssuchaskeyenvironmentalcontrols,keymanagementoperations,infrastructure/administrativecontrols,KSKandZSKandsignaturelifecyclemanagementandpracticesdisclosure.
7.
5ActionsTakenasaresultofDeficiencyWithrespecttocomplianceauditsofCNNIC'soperations,significantexceptionsordeficienciesidentifiedduringthecomplianceauditwillresultinadeterminationofactionstobetaken.
ThisdeterminationismadebyCNNICmanagementwithinputfromtheauditor.
CNNICmanagementisresponsiblefordevelopingandimplementingacorrectiveactionplan.
IfCNNICdeterminesthatsuchexceptionsordeficienciesposeanimmediatethreattothesecurityorintegrityofthe".
TLD"KSKand/orZSK,acorrectiveactionplanwillbedevelopedwithin30daysandimplementedwithinacommerciallyreasonableperiodoftime.
Forlessseriousexceptionsordeficiencies,CNNICmanagementwillevaluatethesignificanceofsuchissuesanddeterminetheappropriatecourseofaction.
7.
6CommunicationofResultsTheauditingmanagershallsubmitawrittenreportoftheauditresultstoCNNICnotlaterthan30calendardaysaftertheaudit.
8LegalMatters8.
1FeesTheEBEROeventTLDRegsitrydoesnotchargeRegistrarsanyfeesforDNSSEC.
8.
2FinancialResponsibilityNotapplicable.
8.
3ConfidentialityofBusinessInformation8.
3.
1ScopeofConfidentialInformationThefollowingrecordsshallbekeptconfidentialandprivate(Confidential/PrivateInformation):1)PrivatekeysandinformationneededtorecoversuchPrivateKeys2)Transactionalrecords(bothfullrecordsandtheaudittrailoftransactions)3)AudittrailrecordscreatedorretainedbyCNNIC4)AuditreportscreatedbyCNNIC(totheextentsuchreportsaremaintained),andtheirrespectiveauditors(whetherinternalorpublic)5)Contingencyplanninganddisasterrecoveryplans6)SecuritymeasurescontrollingtheoperationsofCNNIChardwareandsoftwareandtheadministrationofDNSKeys8.
3.
2TypesofInformationnotConsideredConfidentialAllinformationpertainingtothedatabaseoftopleveldomainsispublicinformation.
PublicKeys,KeyRevocation,andotherstatusinformation,aswellasCNNICpublicationandinformationcontainedwithinthemarenotconsideredConfidential/PrivateInformation.
8.
3.
3ResponsibilitytoProtectConfidentialInformationCNNICsecuresconfidentialinformationagainstcompromiseanddisclosuretothirdparties.
8.
4PrivacyofPersonalInformation8.
4.
1InformationTreatedasPrivateTotheextentCNNICreceivesorprocesses,onbehalfofacustomer,personallyidentifiableinformation(PII)inthecourseofproviding".
TLD"Zoneservices,suchPIIistreatedasprivateinaccordancewiththetermsofCNNIC'sagreementswithRegistrarsandCNNIC'sPrivacyPolicy.
8.
4.
2InformationnotDeemedPrivateSubjecttoapplicablelaws,allinformationrequiredtobepublishedaspartofawhoisdatabaseisnotdeemedprivate.
8.
4.
3ResponsibilitytoProtectPrivateInformationInproviding".
TLD"Zoneservices,CNNICactsasadatacontroller,andanyobligationsthatCNNICmayhavewithrespecttoanypersonallyidentifiableinformationisgoverned,subjecttoapplicablelaw,bythetermsofCNNIC'sagreementswithregistrarsandtotheextentnotgovernedbyanyapplicableRegistryRegistraragreement.
8.
4.
4DisclosurePursuanttoJudicialorAdministrativeProcessCNNICshallbeentitledtodiscloseConfidential/PrivateInformationif,ingoodfaith,CNNICbelievesthatsuchdisclosureisnecessaryinresponsetojudicial,administrative,orotherlegalprocessduringthediscoveryprocessinaciviloradministrativeaction,suchassubpoenas,interrogatories,requestsforadmission,andrequestsforproductionofdocuments.
8.
5LimitationsofLiabilityCNNICshallnotbeliableforanyfinanciallossorlossesarisingfromincidentaldamageorimpairmentresultingfromitsperformanceofitsobligationshereunderorthe".
TLD"ZoneManager'sorthe".
TLD"ZoneKSKandZSKOperator'sperformanceoftheirrespectiveobligationsunderDNSSECPracticeStatementforthe".
TLD"ZoneKSKandZSKOperator.
Nootherliability,implicitorexplicit,isaccepted.
8.
6TermandTermination8.
6.
1TermTheDPSbecomeseffectiveuponpublicationontheCNNICwebsite.
AmendmentstothisDPSbecomeeffectiveuponpublicationontheCNNICwebsite.
8.
6.
2TerminationThisDPSisamendedfromtimetotimeandwillremaininforceuntilitisreplacedbyanewversion.
8.
6.
3DisputeResolutionProvisionsDisputesamongDNSSECparticipantsshallberesolvedpursuanttoprovisionsintheapplicableagreementsamongtheparties.
DisputesinvolvingCNNICrequireaninitialnegotiationperiodofsixty(60)daysfollowedbylitigationintheBeijingHaidianDistrictintermediatepeople'scourt,PRC.
8.
6.
4GoverningLawThisDPSshallbegovernedbythelawsofthePeople'sRepublicofChina.
- authenticatezhonguancun相关文档
- proceedingszhonguancun
- Chinesezhonguancun
- 中关村zhonguancun
- Zhongzhonguancun
- 中国zh
- 工件a
GeorgeDatacenter:洛杉矶/达拉斯/芝加哥/纽约vps云服务器;2核/8GB/250GB/2TB流量/1Gbps端口,$84/年
georgedatacenter怎么样?GeorgeDatacenter是一家2017年成立的美国商家,正规注册公司(REG: 10327625611),其实是oneman。现在有优惠,有几款特价VPS,基于Vmware。支持Paypal付款。GeorgeDatacenter目前推出的一款美国vps,2核/8GB内存/250GB NVMe空间/2TB流量/1Gbps端口/Vmware/洛杉矶/达拉...
UCloud云服务器低至年59元
最近我们是不是在讨论较多的是关于K12教育的问题,培训机构由于资本的介入确实让家长更为焦虑,对于这样的整改我们还是很支持的。实际上,在云服务器市场中,我们也看到内卷和资本的力量,各大云服务商竞争也是相当激烈,更不用说个人和小公司服务商日子确实不好过。今天有看到UCloud发布的夏季促销活动,直接提前和双十一保价挂钩。这就是说,人家直接在暑假的时候就上线双十一的活动。早年的双十一活动会提前一周到十天...

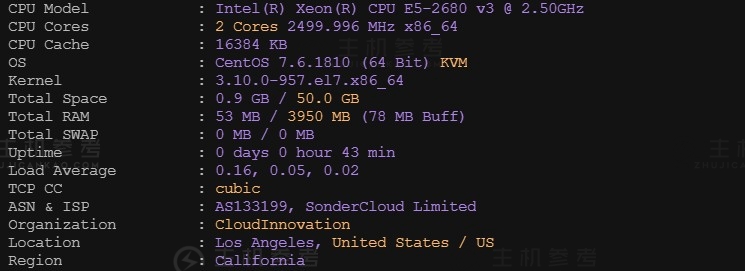
恒创科技SonderCloud,美国VPS综合性能测评报告,美国洛杉矶机房,CN2+BGP优质线路,2核4G内存10Mbps带宽,适用于稳定建站业务需求
最近主机参考拿到了一台恒创科技的美国VPS云服务器测试机器,那具体恒创科技美国云服务器性能到底怎么样呢?主机参考进行了一番VPS测评,大家可以参考一下,总体来说还是非常不错的,是值得购买的。非常适用于稳定建站业务需求。恒创科技服务器怎么样?恒创科技服务器好不好?henghost怎么样?henghost值不值得购买?SonderCloud服务器好不好?恒创科技henghost值不值得购买?恒创科技是...
zhonguancun为你推荐
-
硬盘的工作原理硬盘的工作原理?是怎样存取数据的?xyq.163.cbg.com梦幻西游里,CBG是什么?在那里,能帮忙详细说一下吗seo优化工具想找一个效果好的SEO优化软件使用,在网上找了几款不知道哪款好,想请大家帮忙出主意,用浙江哪款软件效果好haole16.com玛丽外宿中16全集在线观看 玛丽外宿中16qvod快播高清下载m.2828dy.combabady为啥打不开了,大家帮我提供几个看电影的网址www.5any.com重庆哪里有不是全日制的大学?www.03ggg.comwww.tvb33.com这里好像有中国性戏观看吧??www.bbb551.com100bbb网站怎样上不去了www.22zizi.com乐乐电影天堂 http://www.leleooo.com 这个网站怎么样?www.175qq.com这表情是什么?