中国tianyaclub
tianyaclub 时间:2021-01-30 阅读:()
DynamicMonitoringModelforBBSContentSecurity*JingYu,YanpingZhaoSchoolofManagement&EconomicsBeijingInstituteofTechnologyBeijingP.
R.
Chinapaopaofish@bit.
edu.
cn,zhaoyp@bit.
edu.
cnAbstract:-BulletinBoardService(BBS)communityshouldbeaharmoniouspublicspeakinglocationfullofharmlessopinions.
ThispaperanalyzesthecharacteristicsofarticlecontentinBBS,especiallyforChineseLanguage,andproposesanoveldynamicmonitoringmodelforBBScontentsecurity.
Themodelisbasedonafastmulti-patternmatchingalgorithm,andusesacombinedapproachofTextFiltering,SocialNetworkAnalysis(SNA)andspotinvestigatingmethod.
Thesystemcandiscoverillegalarticleefficiently,andidentifydangerpersonsandthebehaviorpatterndynamically.
Key-Words:-BBS;Contentsecurity;Multi-patternmatch;SNA*ThisresearchissupportedbytheNationalNaturalScienceFoundationofChina(70471064),andResearchFoundationofBeijingInstituteofTechnology(BIT-UBF-200308G10).
1IntroductionTheoryresearchesandpracticeapplicationsaboutcontentsecurityfilteringmainlyaimatordinaryWWWtextsorEmail.
However,theexistingmethodsandtechnologiesarenotverysatisfactoryinviewofBBStexts.
Thereasonsasfollows:Firstly,thearticlecontentofBBSisdisplayedincisivelyandvividly,anduselargenumbersofshorteningsymbols,fabricatingtermswhichmakethetraditionalfilteringsystemscannotdistinguish.
Secondly,BBShasextremelyquickpublicrespondandspreadspeed,sothatithasdifficultyinmonitoringBBStimelyanddynamically.
Finally,sinceBBSiscomparativelyeasyforusersregisternewaccountsatanymoment,theanalystsareoverwhelmedwiththeincompleteormisleadinginformationfrommanysources,andhavedifficultyindiscoveringtheirrelations.
Thereisaneedtohelptheanalyststoidentifykeydangerpersonswhomaybehaveseveralvirtualaccounts,andtrackandanalyzerelationdataofthem.
ThispaperproposesaninnovativedynamicmonitoringmodelforBBScontentsecurity,whichusesacombinedapproachofTextFiltering,SocialNetworkAnalysis(SNA)andspotinvestigatingmethod,especiallyefficientforChinesenaturallanguage.
Thispaperisorganizedasfollows,insection2,somerelatedworks;section3proposestheframeworkofdynamicmonitoringmodelforBBScontentsecurity;section4,mainlydesignstwocoremodules,onesupportsContentFilterbasedonanovelfastMulti-Patternmatchingalgorithm,theothersupportsLinkAnalyzer;section5,someinitialtestresults;section6,conclusionsandfuturework.
2RelatedWorkRoughlytherearethreekindsofcontentsecurityfilteringtechnologies.
Thefirstiskeyword(s)matchingalgorithms.
ThesecondisstatisticalmethodbasedonVectorSpaceModel(VSM).
Thelastoneisbasedonknowledgebase.
Themostpopularoneissimplepattern(keyword)matchingbasedonSingle-PatternorMulti-Pattern.
Thespeedofpatternmatchingalgorithmisemphasizedinordertomeettheneedofbroadbandinformationfilteringonnetwork.
However,inthepracticalapplicationoffilteringsystem,twoexistingproblemsneedtobesolved.
TheyarehowtomaketherulesforfilteringcontentandwhichkindofpatternmatchingalgorithmismoreefficienttoChineselanguagetexts.
ThesecondfilteringtechnologyisstatisticalmethodbasedonVSM,whichiscomparativelyusedmoreintextclassificationresearchthaninothers.
Theaccuracyisenhancedgreatlythroughtrainingalargeamountofclearlyclassifiedcorpusandconstructingfeaturevector(keywords)torepresenteachclass.
Butthismethodconsumesmoretimeincomputingsimilaritybetweenfeaturevectorsandthatofunknowndocuments[1].
Thetwotechnologiesabove-mentionedhaveacommondisadvantageofnon-semantic.
Thecontentfilteringtechnologybasedonknowledgebaseisbecomingaresearchhotspotallovertheworld.
ThisresearchismoremeaningfultoChinesetextfilteringsinceitisbasedoncharactersetsnotwords.
JinYao-hongusesHierarchicalNetworkofConceptstheory(HNC)[2]andmatchingmethodbasedoncomplicatedChinesesemanticknowledgerules.
Itsaccuracyismorethan90%,butitsefficiencyiscomparativelyratherlow.
Wecanseespeedandaccuracyarebothimportanttothebroadbandnetworkcontentfiltering.
SoitisnecessarytoimprovetheexistingfilteringalgorithmtoadapttoChinesetextefficiently.
Someexpertsworkedonmixturedfilteringmethodresearch[3][4].
OthersapplySNAtechnologytoBBSresearch.
Forexample,VilleH.
Tuulosandetalcombinetopicmodelwithsocialnetworksforchatdatatopicmining[5].
KouZhong-baoandetaldiscoverthe"smallworld"phenomenonofBBS[6].
Buttherehasn'tbeenresearchaboutSNAappliedtoBBScontentsecuritymonitoring.
3FrameworkofDynamicMonitoringforBBSContentSecurity3.
1BBSDataSourceThedatausedinthispaperwascapturedfromTianyaClubBBS,whichisverypopularinP.
R.
China(www.
tianyaclub.
com).
ThetotalnumberofregisteredIDsisabout3,000,000andthenumberofliveusersisoftenover30,000.
SoTianyaClubprovidesaverygooddataresourceforourresearch.
Ingeneral,everyBBSismoreorlesscomposedofsomediscussiongroups(community).
Eachgrouphasaseriesofarticlesorganizedaccordingtodifferenttopics.
Thefirstarticleisinitialarticle.
Othersarereplyarticlesthatcommentsontheinitialone.
EacharticlecontainsaccountID,title,groupinformation,dateandtime,contents.
TheaccountIDofinitialarticleistheusernameofannouncer,whilethatofreplyarticleistheusernameofreplier.
SocialnetworkGemergesbecauseofthereplyrelationamongtheseaccountIDs.
EachaccountIDwhohastakenpartintopicdiscussionisanodevinG.
ThesetofvisV.
AlinkisestablishedbetweentwonodeswhenoneaccountIDrepliestotheother.
EachlinkeisanarcfromreplyIDtoinitialID.
ThesetofeisE.
AsocialnetworkinBBSisasmallworld[6].
3.
2DynamicMonitoringModelforBBSContentSecurityFig.
1presentstheframeworkofdynamicmonitoringmodelforBBScontentsecurity.
Fig.
1FrameworkofdynamicmonitoringmodelforBBScontentsecurity.
Thesystemisaimedatmonitoringterroristsordangerpersons'speechamongallLANuserswhoaccesstheBBSserver,suchasTianyaClub.
Thewholeframeworkincludesfourmodules.
(1)"CaptureandConvertData"moduleThismoduleisinchargeofcapturing,processingandconvertingBBSnetworkdataonthegatewayofLANwithfastdatapacketcaptureandprotocolanalysistechnology.
BasedonthecharacteristicofChineselanguage,the"plasmodium","synonym","meaningless"phenomenonexistsintheBBScontent.
Wegivedefinition1andexplanationhereandtheothersinthefollowingsections.
Definition1:"plasmodium"isaChineselanguagephenomenoninBBS.
Thereareafewofdeliberateinterferentialcharacters,suchas"*",writtenamongChinesecharactersbydangerpersonstoescapethefilteringsystem.
ItisbasedonnoticeablecharacterofChineselanguagedifferentfromEnglishlanguageisthatoneEnglishwordisusuallyequivalenttotwoorthreeChinesecharacters.
Forexample,thecombinationofcharacter"中"and"国"produces"中国"whichmeans"China".
Thiskindofphenomenondoesnotinfluencereaders'understanding,suchas"中*国"("中国"actually).
Butthenegativeinfluenceof"*"isthat"中*国"cannotbematchedbythepatternof"中国".
Sothedataneedtobecleanedoutthesedeliberateinterferentialcharactersafterconverting.
ThecleanedBBSdataisstoredas.
txtfilesintheappointedsitedirectories.
(2)"ExtractInformation"moduleUsefulinformationcontainedin.
txtfilesabove-mentionedisextractedandstoredintodatabase.
Thedataisdividedintotwokindsofinformationwewilldealwith.
Onekindis"title"and"content"thatarethedealingobjectsofContentFiltermodule.
Theotherischaracterinformation,suchas"accountID","data","time"etc.
thatarethedealingobjectsofLinkAnalysismodule.
(3)"ContentFilter"and"LinkAnalyzer"modules"ContentFilter"canmonitorarticlecontentandidentifywhetheranyfilteringruleismatched.
IfthereisaBBSarticlecontainingillegalcontent,therecordofthisspeakerismarkedwithdifferentlevel.
Then"LinkAnalyzer"makesajudgmentthatwhoistheauthoroftheillegalarticle(dangerpersons)andrecordshischaracters.
Alongwiththeexpansionofdangercommunitiesmatchedwithfilteringrules,"LinkAnalyzer"canhelptoanalyzethestatusoftheseaccountIDscharactersaccordingtosomeSNAparametervalues.
Moreover,VisualizationSoftwarecanhelpsimulatecommunitystructureanddiscoverpersons'relations,communitydistribution,informationspreadchannels,behaviorpatternsandinfluencepatterns.
Thefollowingsectionintroducesthesetwocoremodulesindetails.
4TwoCoreModules4.
1Thenovelfastmulti-patternmatchingalgorithmSpeedisveryimportantinsecurityfilteringapplication.
Asystemwithlowefficiencycannotperformwellinmonitoring.
MostpopularfastmatchingalgorithmsarebasedonMulti-pattern.
ThemostnotablealgorithmsincludeAho-Corasick(shortasAC)[12]andCommentz-Walter(shortasCW)[11]algorithms.
Astringisdefinedasapattern.
TheadvantageofMulti-patternmatchingalgorithmisthatalltheoccurrencesofanygivenstringscanbefoundonlyinoneprocessofscanningtext.
Thiskindofalgorithmshastwosteps.
Firstly,foragivensetofstrings,afinitestateautomaton(orwecallitpatterntree)isconstructed.
Andthen,thetextsteamisscannedfromendtoendwiththispatterntree.
Actually,patternmatchingisaprocessofstatetransition.
Eachstateisrepresentedbyanumber.
"0"representsstartstate.
Thereisanotherspecialstate,outputstate.
Whenanoutputstateisreceived,thecorrespondingstringisemitted.
WedenoteasetofstringsbyS,andintendtodetectalltheoccurrencesofanystringsinSinatextstreamT.
Patternmatchingisthatgivenacurrentstateandthenextinputcharacter,themachinecheckstoseeifthecharactercausesafailuretransition.
Ifnot,thenitmakesatransitiontothecorrespondingstateaccordingtothecharacter.
Incaseofafailuretransitionthemachinemustreconsiderthecharactercausingthefailureforthenexttransitionandthesameprocessisrepeatedrecursivelyuntilthegivencharacterleadstoanon-failureoutputstate.
Mostmulti-patternalgorithmsusetheshiftmethodofSingle-patternmatchingalgorithmBM[13],forexample,CW.
Whenapatterncharacterisnotmatchedbythenextinputcharacter,severaltextcharacterswouldbeskippedaccordingtoashiftvalue.
Inthisway,thematchingprocessbecomesmoreefficient.
WemadecomparisontosomearticlecontentsinChineselanguageandinEnglishlanguagewithCWalgorithm.
WediscoveredthatthetraditionalkeywordsmatchingalgorithmisnotsuitableforChineselanguage.
Thereasonsasfollows:(1)Fromfig.
2(b),eachEnglishwordiscomposedof26lettersfrom'a'to'z'.
Andthelengthofeachwordisabout5letters.
Butfromfig.
2(a)ordinaryChinesecharactersaremorethan3,000atleasttomakethebasicunitsofaword,andeachwordismadeofabouttwocharacters.
TheresultofthisdifferenceisthatChinesepatterntree(fig.
2(a))isfarwiderthanEnglishpatterntree(fig.
2(b)).
MuchmatchingtimeisconsumedinmatchingthefirstcharacterinChinesepatterntree.
Fig.
2(a)Chinesepatterntree.
Whereweuses1torepresentstring1:空军(airman)intheleftbranch,s2:飞机(airplane),s3:军队(army),s4:战争(battle),s5:前线(battlefront),s6:战场(battleground).
States:2,4,6,7,9,11representtheiroutputstates.
Fig.
2(b)Englishpatterntree.
Whereweuses1torepresentstring1:airman,intheleftbranch,s2:airplane,s3:army,s4:battle,s5:battlefront,s6:battleground.
States:6,11,14,20,26,32representtheiroutputstates.
(2)SinceanEnglishword(about5letters)islongerthanaChineseword(about2characters).
ItresultsthatChinesepatterntree(fig.
2(a))hasfewerdepths,notasmuchdeepasEnglishpatterntree(fig.
2(b)).
Andsincetheshiftvalueisdeterminedbyminimumpatternlength,Chinesewordsaretooshortandthesystemcannotsaverunningtimeinshiftstage.
OursolutionisthatallChinesecharacterscontainedinstringpatternsareorganizedaccordingtoeachcomputeduniquevalue,readintoaHashtable.
AteachnodeofHashtable,childHashtableissetdynamicallythroughcomputingthelattercharacterofthisnodeinonestring.
ThiskindoffiniteautomatonisbasedonHash.
(Seefig.
3)Fig.
3Newstringpatterntreebasedonfastmulti-patternmatchingalgorithm.
Ifastringiscomposedofthreecharacters,depth3childhashtablecanbesetdynamically.
4.
2FilteringrulesbasedonpatternThenextproblemishowtomakefilteringrules.
WeusestatisticalmethodbasedonVSM.
Themodelmapseachdocumenttoasetofnormalizedtermsasavector,whichisexpressedas(T1,W1;T2,W2;…,Tn,Wn),whereTiisafeatureterm,WiistheweightforTi.
ThetraditionalTF-IDF[14]weights:∑=++*=niikiikiikNNttfNNttft122)05.
0(log)()05.
0log()()(ω(1)Thefilteringruleswemadeshouldhaverepresentationanddiscrimination.
Thatisfeaturetermsmustrepresentthecontentofthetargetandcandiscriminateaclassofdocumentsfromothers.
ThetraditionalTF-IDFonlycancomputetheweightofaterminoneclass,butcannotdiscriminatethedifferenceofitsweightinseveralclasses.
Therefore,themodifiedTF-IDFweightsaredefinedasfollows:)1()05.
0(log)()05.
0log()()(122DCDAniikiikiikDIDINNttfNNttft**++*=∑=ω(2)DIDA(DistributionInformationamongClasses)andDIDC(DistributionInformationinsideaClass)aretwoimpactfactors.
DIDArepresentsthedistributiondifferenceoffeaturetermsamongkindsofclasses.
DIDCrepresentsthedistributiondifferenceoffeaturetermsinthesameclass.
DIDAandDIDCaredefinedasfollows:)()1())()((12kmikkiDAttfmttfttfDI=∑=(3)∑==mikikttfmttf1)(1)(Wheretfi(tk)representsthefrequencyoffeaturetermtkinclassi,mrepresentsthenumberofclasses.
Whenafeaturetermtkonlyappearsinaclass,DIDA=1anditdiscriminatesclassstrongly.
Whenthefrequencyoftkineachclassisequal,DIDA=0anditcanhardlydiscriminatesclass.
)()1())()(('12'knjkkjDCttfnttfttfDI=∑=(4)∑==njkjkttfnttf1')(1)(Wheretfj(tk)representsthefrequencyoffeaturetermtkindocumentj,nrepresentsthenumberofdocumentsinoneclass.
Whenafeaturetermtkonlyappearsinadocumentofaclass,DIDA=1anditcanhardlydiscriminatesclass.
Thisdocumentislikelytobeanexceptionofthisclass.
Whenthefrequencyoftkineachdocumentofaclassisequal,DIDA=0,itdiscriminatesclassstrongly.
ThesystemcomputestheweightsoffeaturetermsaccordingtothemodifiedTF-IDFandselectsthosetermswiththeirweightsbiggerthanathreshold.
Andmaketheselectedtermsaspatternsinthepatterntree.
Thiskindofpatternalsocanbeaddedandmodifiedmanually.
Besides,wehavespecialtreatmentforsynonymandmeaninglesswords.
Theirdefinitionsareasfollows:Definition2,synonymmeansthemeaningofonewordissimilartoanother,oradialect,oranirregularwordtorepresentameaningfulword.
Wesetonedelegatewordforasynonymlist.
Thesystemevaluatestheweightofeachwordinthislistequaltothatofdelegate.
Forexample,adelegate"弟弟妹妹"(brothersandsisters)alwaysreplacesitsshorteningsymbolsandfabricatingterms"ddmm"inthelist.
Definition3,meaninglesswords,themeaningofthesewordshasnotenoughdiscriminationamongclasses.
Someofthemneedtobeidentifiedandpickedout.
Administratorcanaddormodifythemintoastopwordlist.
4.
3LinkAnalyzerSocialnetworkanalysistheoryhasmanymeaningfulparameters[7][8],whichcanexplainsomesocialproblemsincommunityenvironment.
WeusetheseparameterstodiscoverimportantinformationfromBBScharacterrelationdata.
TheparametersasDegree,Closeness,BetweennesscandisclosethestatusofdangerpersonsinBBS,andparametersasCharacteristicpathlength,Clustercoefficientdisclosethedensedegreeofcommunityandinformationspreadspeedwithincommunity.
Degreerepresentsthenumberofedgesconnectedwithnodev.
Indegreerepresentsthenumberofreplyfromothernodestonodev.
Outdegreerepresentsthenumberofreplyfromnodevtoothernode.
ThethreeparametersevaluatethedifferenceofcorestatusamongdangeraccountIDs.
Theyaredefined:maxdeg)deg()(vvd=(5)maxdeg)deg()(invinvdin=(6)maxdeg)deg()(outvoutvdout=(7)Itholds0≤d(v),din(v),dout(v)≤1,degmax,indegmaxandoutdegmaxarethemaximumvalueofDegree,IndegreeandOutdegreerespectively.
ClosenessweighstheadjacencydegreebetweennodevandothernodesuV.
Itisdefined:∈),(1)(uvdnvclVu∈Σ=(8)Wherenrepresentsthenumberofnodes,d(v,u)representstheshortestpathlengthfromnodevtonodeuV.
Itholds0≤∈cl(v)≤1.
Betweennessrepresentsthedependingdegreeonnodevfromnodeu∈VtoothernodeszV.
Itis∈defined:∑≠≠≠≠∈=zvuvzuzunVzuzunvzunnnvbw,,0),(;,),();,()2)(1(1)((9)Wheren(u,z)isthenumberofgeodesicsfromutozandn(u,z;v)isthenumberofgeodesicsfromutozpassingthroughv.
Itholds0≤bw(v)≤1.
Characteristicpathlengthrepresentstheaverageshortestpathlengthofn(n-1)/2pairofnodes.
Itisdefined:2/)1(),(,=∑nnuvdLuv(10)ClustercoefficientistheaverageofallnodesCv.
Cvisdefined:2/)1()(ΓΕ=vvvvkkC(11)Where)deg(vkv=,)(vΓΕrepresentstheedgesthattheneighborsofnodevconnecteachother.
Wecanobtainthedynamiccharacteristicsofdangeroussocialnetwork,anddiscovernewbehaviourpatternsthroughobservingandcomparingthechangeofparametervaluesindifferenttime.
Weusetheequationsumexpressionasfollows:2112))()((tptppmiii∑==(12)Wheremrepresentsthenumberofparameters,t1andt2representtwodifferenttimes,pi(t)representsthevalueofparameteriattimet.
Ifthevalueofpisbiggerthanthreshold,thereisanotablepatternvariance.
Thesystemneedtomonitorandanalyzeagain.
5InitialTestingResultsThefollowfiguresandtablesaresometestresults.
Inthefigures,The33accountIDsarefilteredoutbecausethecontentoftheirarticlesismatchedbythefilteringrulesofmilitaryaffairsclass.
Theydiscussedaroundthistopic.
Weusespotinvestigatingmethodstotracksomevitallinkclues.
Thismethodcontainsthreestepsasfollows:StepOne:GeneralInvestigationWeconsiderallaccountIDsasawhole.
Infig.
4thereareseveralcliquesinthiscommunity.
Thecentralkeypersonsofcliquesareobvious.
ID1andID7havebiggernodesanddeepercolor.
AndthearticlesfromID18,ID19,ID20andID21cannotarouseotherpersons'interest.
WecanidentifyeachIDcharacter'sstatusthroughcomputingSNAparametervalues.
(Seetab.
1)Fig.
4Generalinvestigation.
Tab.
1TopthreeaccountIDswithmaximumparametervalues.
ThistablerepresentsthetopthreekeyaccountIDsaccordingtothemaximumparametervalues.
WefindID1andID7havehighercentralityandareconsideredasleaders.
StepTwo:PartitionInvestigationWeneedtopaymoreattentiontothetwoleadersID1andID7.
ThepartitiongroupwecaredalsoincludestheaccountIDswhichhaverelationtoeitherID1orID7.
(Seefig.
5)Fig.
5.
Partitioninvestigation.
Wecanfindanimportantrolethatmaybeignoredinstep1.
HeisID10.
HenotonlyrepliedID1,butalsorepliedID7.
AlthoughhehasnothighcentralityasID1andID7,hemaybetheinformationsource.
StepThree:IndividualInvestigationWeshouldemphasisoninvestigatingthekeypersonsandtheirrepliers.
Wecanfindmoreneighborhoodinformationandclues.
Fig.
6.
Individualinvestigation.
Infig.
6,nineaccountIDsrepliedID1exceptID4.
ID1repliedID4unexpectedly.
WesupposethatanothercliquewillcomeuparoundID4.
6ConclusionsandFutureWorkThispaperintroducestheBBScontentsecurityframeworkroughly.
ThedynamicmonitoringmodelusesacombinedapproachofTextFiltering,SocialNetworkAnalysis(SNA)andspotinvestigatingmethod.
Inthecontentfiltering,anovelfastmulti-patternmatchingalgorithmisproposedandmoreefficientforChineselanguageespecially.
Inordertoimprovetheeffectofcontentfiltering,wedesigntoaddasemanticfunctioninthecontentfiltermodulebasedonknowledgerules.
Besides,moreBBSdataminingworkneedtodowithSNAtheory.
References:[1]HeJing,LiuHai-yan,Real-timeContentFilteringBasedonVectorSpaceModel,ComputerEngineering,Vol.
30,No.
15,2004,8,pp.
26-27.
[2]JinYao-hong,DesignandImplementationofSemantic-basedTextFilteringSystem,ComputerEngineeringandApplication,No.
17,2003,pp.
22-25.
[3]SUGui-yang,LIJian-hua,MAYing-hua,etal,Improvingtheprecisionofthekeyword-matchingpornographictextfilteringmethodusingahybridmodel,JournalofZhejiangUniversitySCIENCE,Vol.
5,No.
9,2004,pp.
1106-1113.
[4]LiuChang-yu,TangChang-jie,YuZhong-hua,BayesDiscriminatorforBBSDocumentBasedonLatentSemanticAnalysis,ChineseJournalofComputers,Vol.
27,No.
4,2004,pp.
566-572.
[5]VilleH.
Tuulos,HenryTirri,Combiningtopicmodelsandsocialnetworksforchatdatamining,Proceedings-IEEE/WIC/ACMInternationalConferenceonWebIntelligence,WI2004,2004,pp.
206-213.
[6]KouZhong-bao,ZhangChang-shui,Replynetworksonabulletinboardsystem,PhysicalReviewE(Statistical,Nonlinear,andSoftMatterPhysics),Vol.
67,No.
3,March,2003,pp.
36117-1-6.
[7]PetterHolme,CharacteristicsofSmallWorldNetworks,http://www.
tp.
umu.
se/_kim/Network/holme1.
pdf,20th,April,2001.
[8]D.
J.
Watts,S.
H.
Strogatz,CollectiveDynamicsof`Small-World'Networks,Nature,1998,pp.
393-440.
[9]Commentz-WalterB,Astring-matchingalgorithmfastontheaverage,Proc6thInternationalColloquiumonAutomataLanguagesandProgramming,1979,pp.
118-132.
[10]AhoAV,CorasickMJ,Efficientstringmatching:anaidtobibliographicsearch,CommunicationsoftheACM,No.
18,1975,pp.
333-340.
[11]BoyerRS,MooreJS,Afaststring-searchingalgorithm,CommunicationsoftheACM,No.
20,1977,pp.
762-772.
[12]Salton,G.
(Ed.
),AutomaticTextProcessing.
AddisonWesley,Massachusetts,1989.
R.
Chinapaopaofish@bit.
edu.
cn,zhaoyp@bit.
edu.
cnAbstract:-BulletinBoardService(BBS)communityshouldbeaharmoniouspublicspeakinglocationfullofharmlessopinions.
ThispaperanalyzesthecharacteristicsofarticlecontentinBBS,especiallyforChineseLanguage,andproposesanoveldynamicmonitoringmodelforBBScontentsecurity.
Themodelisbasedonafastmulti-patternmatchingalgorithm,andusesacombinedapproachofTextFiltering,SocialNetworkAnalysis(SNA)andspotinvestigatingmethod.
Thesystemcandiscoverillegalarticleefficiently,andidentifydangerpersonsandthebehaviorpatterndynamically.
Key-Words:-BBS;Contentsecurity;Multi-patternmatch;SNA*ThisresearchissupportedbytheNationalNaturalScienceFoundationofChina(70471064),andResearchFoundationofBeijingInstituteofTechnology(BIT-UBF-200308G10).
1IntroductionTheoryresearchesandpracticeapplicationsaboutcontentsecurityfilteringmainlyaimatordinaryWWWtextsorEmail.
However,theexistingmethodsandtechnologiesarenotverysatisfactoryinviewofBBStexts.
Thereasonsasfollows:Firstly,thearticlecontentofBBSisdisplayedincisivelyandvividly,anduselargenumbersofshorteningsymbols,fabricatingtermswhichmakethetraditionalfilteringsystemscannotdistinguish.
Secondly,BBShasextremelyquickpublicrespondandspreadspeed,sothatithasdifficultyinmonitoringBBStimelyanddynamically.
Finally,sinceBBSiscomparativelyeasyforusersregisternewaccountsatanymoment,theanalystsareoverwhelmedwiththeincompleteormisleadinginformationfrommanysources,andhavedifficultyindiscoveringtheirrelations.
Thereisaneedtohelptheanalyststoidentifykeydangerpersonswhomaybehaveseveralvirtualaccounts,andtrackandanalyzerelationdataofthem.
ThispaperproposesaninnovativedynamicmonitoringmodelforBBScontentsecurity,whichusesacombinedapproachofTextFiltering,SocialNetworkAnalysis(SNA)andspotinvestigatingmethod,especiallyefficientforChinesenaturallanguage.
Thispaperisorganizedasfollows,insection2,somerelatedworks;section3proposestheframeworkofdynamicmonitoringmodelforBBScontentsecurity;section4,mainlydesignstwocoremodules,onesupportsContentFilterbasedonanovelfastMulti-Patternmatchingalgorithm,theothersupportsLinkAnalyzer;section5,someinitialtestresults;section6,conclusionsandfuturework.
2RelatedWorkRoughlytherearethreekindsofcontentsecurityfilteringtechnologies.
Thefirstiskeyword(s)matchingalgorithms.
ThesecondisstatisticalmethodbasedonVectorSpaceModel(VSM).
Thelastoneisbasedonknowledgebase.
Themostpopularoneissimplepattern(keyword)matchingbasedonSingle-PatternorMulti-Pattern.
Thespeedofpatternmatchingalgorithmisemphasizedinordertomeettheneedofbroadbandinformationfilteringonnetwork.
However,inthepracticalapplicationoffilteringsystem,twoexistingproblemsneedtobesolved.
TheyarehowtomaketherulesforfilteringcontentandwhichkindofpatternmatchingalgorithmismoreefficienttoChineselanguagetexts.
ThesecondfilteringtechnologyisstatisticalmethodbasedonVSM,whichiscomparativelyusedmoreintextclassificationresearchthaninothers.
Theaccuracyisenhancedgreatlythroughtrainingalargeamountofclearlyclassifiedcorpusandconstructingfeaturevector(keywords)torepresenteachclass.
Butthismethodconsumesmoretimeincomputingsimilaritybetweenfeaturevectorsandthatofunknowndocuments[1].
Thetwotechnologiesabove-mentionedhaveacommondisadvantageofnon-semantic.
Thecontentfilteringtechnologybasedonknowledgebaseisbecomingaresearchhotspotallovertheworld.
ThisresearchismoremeaningfultoChinesetextfilteringsinceitisbasedoncharactersetsnotwords.
JinYao-hongusesHierarchicalNetworkofConceptstheory(HNC)[2]andmatchingmethodbasedoncomplicatedChinesesemanticknowledgerules.
Itsaccuracyismorethan90%,butitsefficiencyiscomparativelyratherlow.
Wecanseespeedandaccuracyarebothimportanttothebroadbandnetworkcontentfiltering.
SoitisnecessarytoimprovetheexistingfilteringalgorithmtoadapttoChinesetextefficiently.
Someexpertsworkedonmixturedfilteringmethodresearch[3][4].
OthersapplySNAtechnologytoBBSresearch.
Forexample,VilleH.
Tuulosandetalcombinetopicmodelwithsocialnetworksforchatdatatopicmining[5].
KouZhong-baoandetaldiscoverthe"smallworld"phenomenonofBBS[6].
Buttherehasn'tbeenresearchaboutSNAappliedtoBBScontentsecuritymonitoring.
3FrameworkofDynamicMonitoringforBBSContentSecurity3.
1BBSDataSourceThedatausedinthispaperwascapturedfromTianyaClubBBS,whichisverypopularinP.
R.
China(www.
tianyaclub.
com).
ThetotalnumberofregisteredIDsisabout3,000,000andthenumberofliveusersisoftenover30,000.
SoTianyaClubprovidesaverygooddataresourceforourresearch.
Ingeneral,everyBBSismoreorlesscomposedofsomediscussiongroups(community).
Eachgrouphasaseriesofarticlesorganizedaccordingtodifferenttopics.
Thefirstarticleisinitialarticle.
Othersarereplyarticlesthatcommentsontheinitialone.
EacharticlecontainsaccountID,title,groupinformation,dateandtime,contents.
TheaccountIDofinitialarticleistheusernameofannouncer,whilethatofreplyarticleistheusernameofreplier.
SocialnetworkGemergesbecauseofthereplyrelationamongtheseaccountIDs.
EachaccountIDwhohastakenpartintopicdiscussionisanodevinG.
ThesetofvisV.
AlinkisestablishedbetweentwonodeswhenoneaccountIDrepliestotheother.
EachlinkeisanarcfromreplyIDtoinitialID.
ThesetofeisE.
AsocialnetworkinBBSisasmallworld[6].
3.
2DynamicMonitoringModelforBBSContentSecurityFig.
1presentstheframeworkofdynamicmonitoringmodelforBBScontentsecurity.
Fig.
1FrameworkofdynamicmonitoringmodelforBBScontentsecurity.
Thesystemisaimedatmonitoringterroristsordangerpersons'speechamongallLANuserswhoaccesstheBBSserver,suchasTianyaClub.
Thewholeframeworkincludesfourmodules.
(1)"CaptureandConvertData"moduleThismoduleisinchargeofcapturing,processingandconvertingBBSnetworkdataonthegatewayofLANwithfastdatapacketcaptureandprotocolanalysistechnology.
BasedonthecharacteristicofChineselanguage,the"plasmodium","synonym","meaningless"phenomenonexistsintheBBScontent.
Wegivedefinition1andexplanationhereandtheothersinthefollowingsections.
Definition1:"plasmodium"isaChineselanguagephenomenoninBBS.
Thereareafewofdeliberateinterferentialcharacters,suchas"*",writtenamongChinesecharactersbydangerpersonstoescapethefilteringsystem.
ItisbasedonnoticeablecharacterofChineselanguagedifferentfromEnglishlanguageisthatoneEnglishwordisusuallyequivalenttotwoorthreeChinesecharacters.
Forexample,thecombinationofcharacter"中"and"国"produces"中国"whichmeans"China".
Thiskindofphenomenondoesnotinfluencereaders'understanding,suchas"中*国"("中国"actually).
Butthenegativeinfluenceof"*"isthat"中*国"cannotbematchedbythepatternof"中国".
Sothedataneedtobecleanedoutthesedeliberateinterferentialcharactersafterconverting.
ThecleanedBBSdataisstoredas.
txtfilesintheappointedsitedirectories.
(2)"ExtractInformation"moduleUsefulinformationcontainedin.
txtfilesabove-mentionedisextractedandstoredintodatabase.
Thedataisdividedintotwokindsofinformationwewilldealwith.
Onekindis"title"and"content"thatarethedealingobjectsofContentFiltermodule.
Theotherischaracterinformation,suchas"accountID","data","time"etc.
thatarethedealingobjectsofLinkAnalysismodule.
(3)"ContentFilter"and"LinkAnalyzer"modules"ContentFilter"canmonitorarticlecontentandidentifywhetheranyfilteringruleismatched.
IfthereisaBBSarticlecontainingillegalcontent,therecordofthisspeakerismarkedwithdifferentlevel.
Then"LinkAnalyzer"makesajudgmentthatwhoistheauthoroftheillegalarticle(dangerpersons)andrecordshischaracters.
Alongwiththeexpansionofdangercommunitiesmatchedwithfilteringrules,"LinkAnalyzer"canhelptoanalyzethestatusoftheseaccountIDscharactersaccordingtosomeSNAparametervalues.
Moreover,VisualizationSoftwarecanhelpsimulatecommunitystructureanddiscoverpersons'relations,communitydistribution,informationspreadchannels,behaviorpatternsandinfluencepatterns.
Thefollowingsectionintroducesthesetwocoremodulesindetails.
4TwoCoreModules4.
1Thenovelfastmulti-patternmatchingalgorithmSpeedisveryimportantinsecurityfilteringapplication.
Asystemwithlowefficiencycannotperformwellinmonitoring.
MostpopularfastmatchingalgorithmsarebasedonMulti-pattern.
ThemostnotablealgorithmsincludeAho-Corasick(shortasAC)[12]andCommentz-Walter(shortasCW)[11]algorithms.
Astringisdefinedasapattern.
TheadvantageofMulti-patternmatchingalgorithmisthatalltheoccurrencesofanygivenstringscanbefoundonlyinoneprocessofscanningtext.
Thiskindofalgorithmshastwosteps.
Firstly,foragivensetofstrings,afinitestateautomaton(orwecallitpatterntree)isconstructed.
Andthen,thetextsteamisscannedfromendtoendwiththispatterntree.
Actually,patternmatchingisaprocessofstatetransition.
Eachstateisrepresentedbyanumber.
"0"representsstartstate.
Thereisanotherspecialstate,outputstate.
Whenanoutputstateisreceived,thecorrespondingstringisemitted.
WedenoteasetofstringsbyS,andintendtodetectalltheoccurrencesofanystringsinSinatextstreamT.
Patternmatchingisthatgivenacurrentstateandthenextinputcharacter,themachinecheckstoseeifthecharactercausesafailuretransition.
Ifnot,thenitmakesatransitiontothecorrespondingstateaccordingtothecharacter.
Incaseofafailuretransitionthemachinemustreconsiderthecharactercausingthefailureforthenexttransitionandthesameprocessisrepeatedrecursivelyuntilthegivencharacterleadstoanon-failureoutputstate.
Mostmulti-patternalgorithmsusetheshiftmethodofSingle-patternmatchingalgorithmBM[13],forexample,CW.
Whenapatterncharacterisnotmatchedbythenextinputcharacter,severaltextcharacterswouldbeskippedaccordingtoashiftvalue.
Inthisway,thematchingprocessbecomesmoreefficient.
WemadecomparisontosomearticlecontentsinChineselanguageandinEnglishlanguagewithCWalgorithm.
WediscoveredthatthetraditionalkeywordsmatchingalgorithmisnotsuitableforChineselanguage.
Thereasonsasfollows:(1)Fromfig.
2(b),eachEnglishwordiscomposedof26lettersfrom'a'to'z'.
Andthelengthofeachwordisabout5letters.
Butfromfig.
2(a)ordinaryChinesecharactersaremorethan3,000atleasttomakethebasicunitsofaword,andeachwordismadeofabouttwocharacters.
TheresultofthisdifferenceisthatChinesepatterntree(fig.
2(a))isfarwiderthanEnglishpatterntree(fig.
2(b)).
MuchmatchingtimeisconsumedinmatchingthefirstcharacterinChinesepatterntree.
Fig.
2(a)Chinesepatterntree.
Whereweuses1torepresentstring1:空军(airman)intheleftbranch,s2:飞机(airplane),s3:军队(army),s4:战争(battle),s5:前线(battlefront),s6:战场(battleground).
States:2,4,6,7,9,11representtheiroutputstates.
Fig.
2(b)Englishpatterntree.
Whereweuses1torepresentstring1:airman,intheleftbranch,s2:airplane,s3:army,s4:battle,s5:battlefront,s6:battleground.
States:6,11,14,20,26,32representtheiroutputstates.
(2)SinceanEnglishword(about5letters)islongerthanaChineseword(about2characters).
ItresultsthatChinesepatterntree(fig.
2(a))hasfewerdepths,notasmuchdeepasEnglishpatterntree(fig.
2(b)).
Andsincetheshiftvalueisdeterminedbyminimumpatternlength,Chinesewordsaretooshortandthesystemcannotsaverunningtimeinshiftstage.
OursolutionisthatallChinesecharacterscontainedinstringpatternsareorganizedaccordingtoeachcomputeduniquevalue,readintoaHashtable.
AteachnodeofHashtable,childHashtableissetdynamicallythroughcomputingthelattercharacterofthisnodeinonestring.
ThiskindoffiniteautomatonisbasedonHash.
(Seefig.
3)Fig.
3Newstringpatterntreebasedonfastmulti-patternmatchingalgorithm.
Ifastringiscomposedofthreecharacters,depth3childhashtablecanbesetdynamically.
4.
2FilteringrulesbasedonpatternThenextproblemishowtomakefilteringrules.
WeusestatisticalmethodbasedonVSM.
Themodelmapseachdocumenttoasetofnormalizedtermsasavector,whichisexpressedas(T1,W1;T2,W2;…,Tn,Wn),whereTiisafeatureterm,WiistheweightforTi.
ThetraditionalTF-IDF[14]weights:∑=++*=niikiikiikNNttfNNttft122)05.
0(log)()05.
0log()()(ω(1)Thefilteringruleswemadeshouldhaverepresentationanddiscrimination.
Thatisfeaturetermsmustrepresentthecontentofthetargetandcandiscriminateaclassofdocumentsfromothers.
ThetraditionalTF-IDFonlycancomputetheweightofaterminoneclass,butcannotdiscriminatethedifferenceofitsweightinseveralclasses.
Therefore,themodifiedTF-IDFweightsaredefinedasfollows:)1()05.
0(log)()05.
0log()()(122DCDAniikiikiikDIDINNttfNNttft**++*=∑=ω(2)DIDA(DistributionInformationamongClasses)andDIDC(DistributionInformationinsideaClass)aretwoimpactfactors.
DIDArepresentsthedistributiondifferenceoffeaturetermsamongkindsofclasses.
DIDCrepresentsthedistributiondifferenceoffeaturetermsinthesameclass.
DIDAandDIDCaredefinedasfollows:)()1())()((12kmikkiDAttfmttfttfDI=∑=(3)∑==mikikttfmttf1)(1)(Wheretfi(tk)representsthefrequencyoffeaturetermtkinclassi,mrepresentsthenumberofclasses.
Whenafeaturetermtkonlyappearsinaclass,DIDA=1anditdiscriminatesclassstrongly.
Whenthefrequencyoftkineachclassisequal,DIDA=0anditcanhardlydiscriminatesclass.
)()1())()(('12'knjkkjDCttfnttfttfDI=∑=(4)∑==njkjkttfnttf1')(1)(Wheretfj(tk)representsthefrequencyoffeaturetermtkindocumentj,nrepresentsthenumberofdocumentsinoneclass.
Whenafeaturetermtkonlyappearsinadocumentofaclass,DIDA=1anditcanhardlydiscriminatesclass.
Thisdocumentislikelytobeanexceptionofthisclass.
Whenthefrequencyoftkineachdocumentofaclassisequal,DIDA=0,itdiscriminatesclassstrongly.
ThesystemcomputestheweightsoffeaturetermsaccordingtothemodifiedTF-IDFandselectsthosetermswiththeirweightsbiggerthanathreshold.
Andmaketheselectedtermsaspatternsinthepatterntree.
Thiskindofpatternalsocanbeaddedandmodifiedmanually.
Besides,wehavespecialtreatmentforsynonymandmeaninglesswords.
Theirdefinitionsareasfollows:Definition2,synonymmeansthemeaningofonewordissimilartoanother,oradialect,oranirregularwordtorepresentameaningfulword.
Wesetonedelegatewordforasynonymlist.
Thesystemevaluatestheweightofeachwordinthislistequaltothatofdelegate.
Forexample,adelegate"弟弟妹妹"(brothersandsisters)alwaysreplacesitsshorteningsymbolsandfabricatingterms"ddmm"inthelist.
Definition3,meaninglesswords,themeaningofthesewordshasnotenoughdiscriminationamongclasses.
Someofthemneedtobeidentifiedandpickedout.
Administratorcanaddormodifythemintoastopwordlist.
4.
3LinkAnalyzerSocialnetworkanalysistheoryhasmanymeaningfulparameters[7][8],whichcanexplainsomesocialproblemsincommunityenvironment.
WeusetheseparameterstodiscoverimportantinformationfromBBScharacterrelationdata.
TheparametersasDegree,Closeness,BetweennesscandisclosethestatusofdangerpersonsinBBS,andparametersasCharacteristicpathlength,Clustercoefficientdisclosethedensedegreeofcommunityandinformationspreadspeedwithincommunity.
Degreerepresentsthenumberofedgesconnectedwithnodev.
Indegreerepresentsthenumberofreplyfromothernodestonodev.
Outdegreerepresentsthenumberofreplyfromnodevtoothernode.
ThethreeparametersevaluatethedifferenceofcorestatusamongdangeraccountIDs.
Theyaredefined:maxdeg)deg()(vvd=(5)maxdeg)deg()(invinvdin=(6)maxdeg)deg()(outvoutvdout=(7)Itholds0≤d(v),din(v),dout(v)≤1,degmax,indegmaxandoutdegmaxarethemaximumvalueofDegree,IndegreeandOutdegreerespectively.
ClosenessweighstheadjacencydegreebetweennodevandothernodesuV.
Itisdefined:∈),(1)(uvdnvclVu∈Σ=(8)Wherenrepresentsthenumberofnodes,d(v,u)representstheshortestpathlengthfromnodevtonodeuV.
Itholds0≤∈cl(v)≤1.
Betweennessrepresentsthedependingdegreeonnodevfromnodeu∈VtoothernodeszV.
Itis∈defined:∑≠≠≠≠∈=zvuvzuzunVzuzunvzunnnvbw,,0),(;,),();,()2)(1(1)((9)Wheren(u,z)isthenumberofgeodesicsfromutozandn(u,z;v)isthenumberofgeodesicsfromutozpassingthroughv.
Itholds0≤bw(v)≤1.
Characteristicpathlengthrepresentstheaverageshortestpathlengthofn(n-1)/2pairofnodes.
Itisdefined:2/)1(),(,=∑nnuvdLuv(10)ClustercoefficientistheaverageofallnodesCv.
Cvisdefined:2/)1()(ΓΕ=vvvvkkC(11)Where)deg(vkv=,)(vΓΕrepresentstheedgesthattheneighborsofnodevconnecteachother.
Wecanobtainthedynamiccharacteristicsofdangeroussocialnetwork,anddiscovernewbehaviourpatternsthroughobservingandcomparingthechangeofparametervaluesindifferenttime.
Weusetheequationsumexpressionasfollows:2112))()((tptppmiii∑==(12)Wheremrepresentsthenumberofparameters,t1andt2representtwodifferenttimes,pi(t)representsthevalueofparameteriattimet.
Ifthevalueofpisbiggerthanthreshold,thereisanotablepatternvariance.
Thesystemneedtomonitorandanalyzeagain.
5InitialTestingResultsThefollowfiguresandtablesaresometestresults.
Inthefigures,The33accountIDsarefilteredoutbecausethecontentoftheirarticlesismatchedbythefilteringrulesofmilitaryaffairsclass.
Theydiscussedaroundthistopic.
Weusespotinvestigatingmethodstotracksomevitallinkclues.
Thismethodcontainsthreestepsasfollows:StepOne:GeneralInvestigationWeconsiderallaccountIDsasawhole.
Infig.
4thereareseveralcliquesinthiscommunity.
Thecentralkeypersonsofcliquesareobvious.
ID1andID7havebiggernodesanddeepercolor.
AndthearticlesfromID18,ID19,ID20andID21cannotarouseotherpersons'interest.
WecanidentifyeachIDcharacter'sstatusthroughcomputingSNAparametervalues.
(Seetab.
1)Fig.
4Generalinvestigation.
Tab.
1TopthreeaccountIDswithmaximumparametervalues.
ThistablerepresentsthetopthreekeyaccountIDsaccordingtothemaximumparametervalues.
WefindID1andID7havehighercentralityandareconsideredasleaders.
StepTwo:PartitionInvestigationWeneedtopaymoreattentiontothetwoleadersID1andID7.
ThepartitiongroupwecaredalsoincludestheaccountIDswhichhaverelationtoeitherID1orID7.
(Seefig.
5)Fig.
5.
Partitioninvestigation.
Wecanfindanimportantrolethatmaybeignoredinstep1.
HeisID10.
HenotonlyrepliedID1,butalsorepliedID7.
AlthoughhehasnothighcentralityasID1andID7,hemaybetheinformationsource.
StepThree:IndividualInvestigationWeshouldemphasisoninvestigatingthekeypersonsandtheirrepliers.
Wecanfindmoreneighborhoodinformationandclues.
Fig.
6.
Individualinvestigation.
Infig.
6,nineaccountIDsrepliedID1exceptID4.
ID1repliedID4unexpectedly.
WesupposethatanothercliquewillcomeuparoundID4.
6ConclusionsandFutureWorkThispaperintroducestheBBScontentsecurityframeworkroughly.
ThedynamicmonitoringmodelusesacombinedapproachofTextFiltering,SocialNetworkAnalysis(SNA)andspotinvestigatingmethod.
Inthecontentfiltering,anovelfastmulti-patternmatchingalgorithmisproposedandmoreefficientforChineselanguageespecially.
Inordertoimprovetheeffectofcontentfiltering,wedesigntoaddasemanticfunctioninthecontentfiltermodulebasedonknowledgerules.
Besides,moreBBSdataminingworkneedtodowithSNAtheory.
References:[1]HeJing,LiuHai-yan,Real-timeContentFilteringBasedonVectorSpaceModel,ComputerEngineering,Vol.
30,No.
15,2004,8,pp.
26-27.
[2]JinYao-hong,DesignandImplementationofSemantic-basedTextFilteringSystem,ComputerEngineeringandApplication,No.
17,2003,pp.
22-25.
[3]SUGui-yang,LIJian-hua,MAYing-hua,etal,Improvingtheprecisionofthekeyword-matchingpornographictextfilteringmethodusingahybridmodel,JournalofZhejiangUniversitySCIENCE,Vol.
5,No.
9,2004,pp.
1106-1113.
[4]LiuChang-yu,TangChang-jie,YuZhong-hua,BayesDiscriminatorforBBSDocumentBasedonLatentSemanticAnalysis,ChineseJournalofComputers,Vol.
27,No.
4,2004,pp.
566-572.
[5]VilleH.
Tuulos,HenryTirri,Combiningtopicmodelsandsocialnetworksforchatdatamining,Proceedings-IEEE/WIC/ACMInternationalConferenceonWebIntelligence,WI2004,2004,pp.
206-213.
[6]KouZhong-bao,ZhangChang-shui,Replynetworksonabulletinboardsystem,PhysicalReviewE(Statistical,Nonlinear,andSoftMatterPhysics),Vol.
67,No.
3,March,2003,pp.
36117-1-6.
[7]PetterHolme,CharacteristicsofSmallWorldNetworks,http://www.
tp.
umu.
se/_kim/Network/holme1.
pdf,20th,April,2001.
[8]D.
J.
Watts,S.
H.
Strogatz,CollectiveDynamicsof`Small-World'Networks,Nature,1998,pp.
393-440.
[9]Commentz-WalterB,Astring-matchingalgorithmfastontheaverage,Proc6thInternationalColloquiumonAutomataLanguagesandProgramming,1979,pp.
118-132.
[10]AhoAV,CorasickMJ,Efficientstringmatching:anaidtobibliographicsearch,CommunicationsoftheACM,No.
18,1975,pp.
333-340.
[11]BoyerRS,MooreJS,Afaststring-searchingalgorithm,CommunicationsoftheACM,No.
20,1977,pp.
762-772.
[12]Salton,G.
(Ed.
),AutomaticTextProcessing.
AddisonWesley,Massachusetts,1989.
- 中国tianyaclub相关文档
- 题目:危机管理与新媒体传播——论政府危机管理中的互联
- Tiananmentianyaclub
- 美国对华贸易决策中的利益集团因素
- 域名田英解读天涯公司声明 关于域名tianyaclub
- tianyaclub邦联制和联邦制分别是什么?
- tianyaclub薏仁粉怎么吃?
香港2GB内存DIYVM2核(¥50月)香港沙田CN2云服务器
DiyVM 香港沙田机房,也是采用的CN2优化线路,目前也有入手且在使用中,我个人感觉如果中文业务需要用到的话虽然日本机房也是CN2,但是线路的稳定性不如香港机房,所以我们在这篇文章中亲测看看香港机房,然后对比之前看到的日本机房。香港机房的配置信息。CPU内存 硬盘带宽IP价格购买地址2核2G50G2M1¥50/月选择方案4核4G60G3M1¥100/月选择方案4核8G70G3M4¥200/月选择...
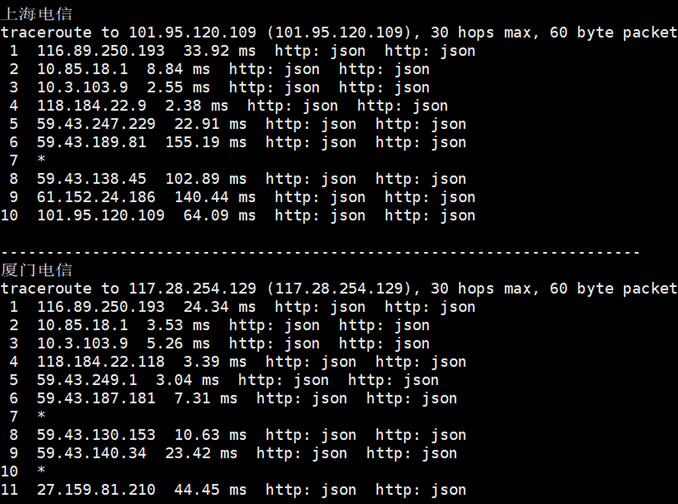
RackNerd美国大硬盘服务器促销:120G SSD+192TB HDD,1Gbps大带宽,月付$599,促销美国月付$服务器促销带宽
racknerd怎么样?racknerd最近发布了一些便宜美国服务器促销,包括大硬盘服务器,提供120G SSD+192TB HDD,有AMD和Intel两个选择,默认32G内存,1Gbps带宽,每个月100TB流量,5个IP地址,月付$599。价格非常便宜,需要存储服务器的朋友可以关注一下。RackNerd主要经营美国圣何塞、洛杉矶、达拉斯、芝加哥、亚特兰大、新泽西机房基于KVM虚拟化的VPS、...
野草云提供适合入门建站香港云服务器 年付138元起 3M带宽 2GB内存
野草云服务商在前面的文章中也有多次提到,算是一个国内的小众服务商。促销活动也不是很多,比较专注个人云服务用户业务,之前和站长聊到不少网友选择他们家是用来做网站的。这不看到商家有提供香港云服务器的优惠促销,可选CN2、BGP线路、支持Linux与windows系统,支持故障自动迁移,使用NVMe优化的Ceph集群存储,比较适合建站用户选择使用,最低年付138元 。野草云(原野草主机),公司成立于20...
tianyaclub为你推荐
-
笔记本1g内存条价格1G笔记本的内存条多少钱?麒麟990和骁龙865哪个好5G手机芯片高通865对比麒麟990 5G SOC哪个好?音乐播放器哪个好哪个音乐播放器最好炒股软件哪个好最好的炒股软件是哪个?苹果手机助手哪个好最新版iphone助手 PP助手好用吗?电陶炉和电磁炉哪个好电磁炉与电陶炉有啥区别,哪个更好些?yy空间登录yy空间怎么上传照片?如何增加百度收录如何提高百度收录率?360云盘360云盘和微云那个好用?360云盘同步版360云盘和360云盘同步版有什么区别?哪个更好用?