reducebluestacks
bluestacks 时间:2021-02-19 阅读:()
EvadingAndroidRuntimeAnalysisThroughDetectingProgrammedInteractionsWenruiDiaoTheChineseUniversityofHongKongdw013@ie.
cuhk.
edu.
hkXiangyuLiuTheChineseUniversityofHongKonglx012@ie.
cuhk.
edu.
hkZhouLiACMMemberlzcarl@gmail.
comKehuanZhangTheChineseUniversityofHongKongkhzhang@ie.
cuhk.
edu.
hkABSTRACTDynamicanalysistechniquehasbeenwidelyusedinAndroidmalwaredetection.
Previousworksonevadingdynamicanalysisfocusondiscoveringthengerprintsofemulators.
However,suchmethodhasbeenchallengedsincetheintroductionofrealdevicesinrecentworks.
Inthispaper,weproposeanewapproachtoevadeautomatedruntimeanalysisthroughdetectingprogrammedinteractions.
Thisapproach,inessence,triestotelltheidentityofthecurrentappcontroller(humanuserorautomatedexplorationtool),byndingintrinsicdifferencesbetweenhumanuserandmachinetesterininteractionpatterns.
Theeffectivenessofourapproachhasbeendemonstratedthroughevaluationagainst11real-worldonlinedynamicanalysisservices.
KeywordsAndroidmalware;dynamicanalysis;programmedinteraction1.
INTRODUCTIONWiththeevolutionofmobilecomputingtechnology,smartphonehasexperiencedenormousgrowthinconsumermarket,amongwhichAndroiddeviceshavetakenthelion'sshare.
Unfortunately,Android'sopenecosystemalsoturnsitselfintoaplaygroundformalware.
Accordingtoarecentreport[9],onaverage,8,240newAndroidmalwaresampleswerediscoveredinasingleday.
TocombatthemassivevolumeofAndroidmalwarenewlyemerged,automateddetectiontechniques(staticanddynamic)wereproposedandhavebecomethemainstreamsolutions.
Dy-namicanalysisframeworksmonitorthebehaviorsoftheappsam-plesexecutedinacontrolledenvironmentunderdifferentstimuli.
Comparedwithstaticanalysis,dynamicanalysisdoesnothavetounderstandthecomplicatedlogicinmaliciouscodeandisimmunetocodeobfuscationandpacking.
Moreover,lessnoticeablerun-timemaliciousbehaviorscouldbediscovered.
Thetraditionaldynamicanalysisplatformswerelargelybuiltuponemulatorstoenablefastandeconomicmalwareanalysis.
Permissiontomakedigitalorhardcopiesofallorpartofthisworkforpersonalorclassroomuseisgrantedwithoutfeeprovidedthatcopiesarenotmadeordistributedforprotorcommercialadvantageandthatcopiesbearthisnoticeandthefullcitationontherstpage.
Copyrightsforcomponentsofthisworkownedbyothersthantheauthor(s)mustbehonored.
Abstractingwithcreditispermitted.
Tocopyotherwise,orrepublish,topostonserversortoredistributetolists,requirespriorspecicpermissionand/orafee.
Requestpermissionsfrompermissions@acm.
org.
WiSec'16,July18–20,2016,Darmstadt,Germany.
2016Copyrightheldbytheowner/author(s).
PublicationrightslicensedtoACM.
ISBN978-1-4503-4270-4/16/07.
.
.
$15.
00DOI:http://dx.
doi.
org/10.
1145/2939918.
2939926Toevadedynamicanalysis,abroadspectrumofanti-emulationtechniqueshavebeenproposed[21,28,14,17]andadoptedbymalwareauthors.
Ingeneral,thesetechniquesweredesignedtongerprinttheruntimeenvironmentandlookforartifactsthatcantellphysicaldeviceandemulatorapart.
Thougheffectiveatrst,countermeasureshavebeendevelopedbythesecuritycommunitytodiminishtheefcacyofanti-emulation.
Recently,researchersproposedtousephysicaldevices[19]andmorphartifactsuniquetoemulators[12,11,13].
Thesemethodswreckedthebaseofanti-emulationtechniques,butwebelievethearmsracebetweendynamicanalysisandevasionhasnotyetended.
AutomatedExploration.
Differentfromthetraditionaldesktopmalware,Androidmalwareareevent-driven,meaningthatmali-ciousbehaviorsareusuallytriggeredaftercertaincombinationsofuseractionsorsystemevents.
Therefore,thesimpleinstall-then-executeanalysismodelisnoteffectivetotriggermalware'sruntimebehaviors.
Tosolvethisissue,automatedexplorationtechniquesareintegratedintodynamicanalysisframeworks,includingeventinjection,UIelementidentication,etc.
Theultimategoalofthemistoachievegoodcoverageofapp'sexecutionpathsinalimitedperiod.
NewEvadingTechniques.
Inthispaper,weproposeanewapproachtoevadeAndroidautomatedruntimeanalysisthroughdetectingprogrammedinteractions.
Thecoreideaofthisapproachistodeterminetheidentityofthepartyoperatingtheapp(ahumanuseroranautomatedexplorationtool)bymonitoringtheinteractionpatterns.
Tomalwareanalysis,thegoalofinteractionisdifferentfromthatofarealuser.
Forefciency,explorationtoolinjectssimulatedusereventsandavoidsaccessingtheunderlyingdevices.
Suchsimulatedeventsandhardwaregeneratedonesareinconsistentinmostcases.
Also,toachievehighcoverageofexecutionpaths,explorationtooltendstotriggerallvalidcontrols,amongwhichsomearenotsupposedtobetriggeredbyhuman.
WeleveragetheseinsightsandbuiltanevasivecomponentPIDetector,whichmonitorstheeventstreamandidentiestheeventsunlikelycomingfromarealuser.
Themaliciouspayloadwillbeheldfromexecutionifadynamicanalyzerisidentied.
Comparedwiththepreviousanti-emulationtechniques,ourapproachexploitsthegapbetweenhumanandmachineinrun-timebehaviors,insteadofrelyingonfeaturesregardingexecutionenvironment.
Oneprominentadvantageofourapproachisitsrobustnessagainstanytestingplatform,evenonecomposedofphysicaldevices.
Weimplementedaproof-of-conceptappandsubmitteditto11onlinedynamicanalysisservicesscreeningsamplessubmittedfromallsortsofsources.
Thepreliminaryresultshavealreadydemonstratedtheeffectivenessofourapproach:nearlyall(avail-able)surveyedservicesexhibitatleastonepre-denedpatternofprogrammedinteractions.
Asarecommendation,thedesignofthecurrentdynamicanalysisplatformsshouldberevisitedtodefendagainstsuchnewtypeofevasion.
Contributions.
Wesummarizethispaper'scontributionsasbelow:NewTechniqueandAttackSurface.
Weproposeanewap-proachtoevadeAndroidruntimeanalysis:programmedin-teractiondetection,whichprovidesanewvenueforevadingdynamicanalysisotherthanexistinganti-emulationworks.
ImplementationandEvaluation.
Weimplementedaproof-of-conceptappandtesteditonseveralreal-worldAndroiddynamicanalysisplatforms.
Theexperimentalresultsdemon-strateourapproachishighlyeffective.
2.
RELATEDWORKMostAndroiddynamicanalysisframeworksarebuiltuponem-ulators[20],whichiseasiertobedeployedandmoreeconomical,asthecostofpurchasingmobiledevicesisexempted.
Besides,theappbehaviorsonemulatorsareeasiertobemonitoredandcontrolled.
Suchframeworks,however,arenotrobustagainstevasivemalware,andanti-emulationtechniqueshavebeenwidelydiscussed.
Inthissection,wereviewthesetechniquesanddescribethecountermeasuresproposedbysecuritycommunity.
2.
1Anti-EmulationNearlyallpreviousanti-emulationtechniques[21,28,14,17]exploittheuniquefeaturesofthevirtualizedenvironmentandrefrainfromexecutingthecoremaliciouspayload(e.
g.
,sendingSMStopremiumnumber)whenthehostisfoundasanemulator.
Thefeaturesthatdifferentiateemulatorsfromrealmobiledevicesandareleveragedforanti-emulationarelistedbelow:FirmwareFeatures.
Themobiledevicesmanufacturedbyvendorsareassembledfromdistinctivermware,whichembedsuniqueIDorinformationreectingthehardwarespecication.
Onthecontrary,emulatorstendtousexeddummyvaluestollrmwarefeatures.
Forexample,nullandandroid-testarefedtormware-queryAPIslikeBuild.
SERIALandBuild.
HOSTbyemulators.
DeviceFeatures.
Alotofperipheraldevices,especiallysensors,havebeenintegratedintomobiledevices,likeaccelerometerandgyroscope.
Notallthesensorsaresupportedbyemulators,whichcanbeexploitedforemulatoridentication.
Forthesensorssimulatedbyemulators,thedatastreamproduceddifferssigni-cantly(usuallyconstant)fromwhatisgeneratedfromrealdevices(randomlydistributed)[28].
PerformanceFeatures.
Performance,particularlyprocessingspeed,isadisadvantageforemulators.
ThoughmoderndesktopPChasmoreprocessingpower,suchimprovementisoverwhelmedbypenaltyfrominstructiontranslation.
Asshownin[28],adversarycouldmeasureCPUandgraphicalperformance,andthendeterminetheexistenceofemulator.
Italsoturnsoutthatthereexistsahugenumberofheuristicscanbeemployedforemulatordetection.
Jingetal.
[14]proposedaframeworkwhichcanautomaticallydetectthediscrepanciesbetweenAndroidemulatorsandrealdevices,andmorethan10,000heuristicshavebeendiscovered.
Fixingthesediscrepanciesonemulatorsneedstremendouseffortsbyallmeans.
2.
2CountermeasuresTheanti-emulationtechniquessurveyedabovearequiteeffectivebutnotimpeccable.
Theyalllookforobservableartifactsproducedfromvirtualization,whichturnsouttobetheAchilles'heel.
Wedescribetwotypesofcountermeasuresforobscuringrunningplatformbelow:UsingPhysicalDevices.
Buildinganalysisplatformonphysicaldevicescouldthwartanti-emulationbehaviorsnaturally.
Vidasetal.
[29]proposedahybridsystemnamedA5,whichcombinesbothvirtualandphysicalpoolsofAndroiddevices.
Morerecently,Muttietal.
[19]proposedBareDroid,whichrunsbare-metalanalysisonAndroidapps.
Thesystemisbuiltsolelyuponoff-the-shelfAndroiddevicesandappliesseveralnoveltechniqueslikefastrestorationtoreducetheperformancecost.
Theevaluationresultsoftheseworksprovethatmalwarearenotabletodiscerntheanalysisplatformwithusers'devices.
ChangingArtifacts.
Anotherdirectionistochangetheobservableartifactstomasqueradetheemulatorsasrealdevices.
Huetal.
[13],Dietzel[11]andGajranietal.
[12]followedthistrail.
TheycustomizedtheemulatorframeworkandhookedruntimeAPIs(inbothJavaandLinuxlayer)tofeedfakevaluestotheprobingfunctionsofmalware.
Themaliciousbehaviorscouldberevealedwhenthechecksforrealdevicesareallpassed.
3.
BACKGROUNDANDMOTIVATIONFromtheperspectiveoftheadversary,pursuingthedirectionofngerprintingexecutionenvironmentwouldleadtoadead-endinthetrendthatmoreandmoreanalysisplatformsaredrivenbyrealdevicesortailoredemulators.
Inthiswork,weexploreanewdirection:insteadofsensingwhatenvironmentrunstheapp,weinspectthebehaviorsofdynamicanalyzerandfocusonhowitinteractswiththeapp.
Werstbrieyoverviewthecurrentdynamicanalysistechniquesandthenintroducetheconceptofprogrammedinteractiontomotivateourresearch.
3.
1DynamicAnalysisDifferentfromstaticanalysistools,whichscrutinizethesourcecodeorbinarycodeoftheprogramtoidentifythemaliciouspayload,dynamicanalysisframeworksexecutetheprogramtocapturethemaliciousbehaviorsintheruntime.
Inparticular,theexecutionenvironmentfordynamicanalysisisinstrumented,andvarioussystemoruserinputs(e.
g.
,clickingUIbuttons)areinjectedtotriggerallsortsofapp'sbehaviors.
IfcertainmaliciousI/Opatternsorbehaviorsareidentied(e.
g.
,sendingSMStopremiumnumbers),theappisconsideredasmalware.
Thoughstaticanalysisavoidsthecostofrunningappandisusuallymoreefcient,itcouldbethwartedwhenobfuscationorpackingtechniquesareemployed.
AsshownintheworkbyRastogietal.
[23],commonmalwaretransformationtechniquescouldmakemaliciousappsevadepop-ularstaticanalysistoolsathighsuccessrate.
Ontheotherhand,dynamicanalysisisrobustagainstcode-levelevadingtechniquesandissuitableforprocessingappswithcomplicatedprogramlogics.
Acorpusofframeworkshavebeendevelopedandprovedtobeeffective,includingDroidScope[31],AppsPlayground[22],CopperDroid[26],etc.
Googlealsodevelopeditsdynamicanalysisframework,Bouncer[16],tocheckeveryappsubmittedtoGooglePlay.
3.
1.
1InputGenerationandAutomatedExplorationSinceapp'sruntimebehaviorsoftendependontheinputsfromtheuserorsystem,theeffectivenessofthedynamicanalysisframeworkhighlydependsonthestrategyofinputgeneration.
ComparingtothetraditionalPCmalware,whichtendtotakemaliciousactions(e.
g.
,controllingthesystem)onceexecuted,mobilemalwaretendtodelaythemaliciousactionstillasequenceofeventsareobserved(e.
g.
,hijackingthelegitimateappandstealingthereceivedmessages).
Therefore,thetestingplatformshouldbeabletogeneratetheinputinacontext-awaremannerandexploretheexecutionpathsautomatically.
Below,wedescribetwowidelyadoptedstrategiesinautomatedpathexploration:Fuzzing-basedExploration.
Fuzzingisablack-boxtestingtechniqueinwhichthesystemundertestisstressedwithinvalid,unexpectedorrandominputstransmittedfromexternalinterfacestoidentifythebugsinprograms[25].
OntheAndroidplatform,GoogleprovidesanofcialfuzzerMonkey[8],whichgeneratespseudo-randomstreamsofusereventssuchasclicks,touches,orgestures,aswellasanumberofsystem-leveleventsandinjectsthemintotheframeworkthroughAndroidDebugBridge(ADB).
SeveraldynamicanalysisframeworkshaveincorporatedMonkeyastheexplorationengine,suchasVetDroid[32]andAndrubis[15].
Model-basedExploration.
Onthecontrary,model-basedtestingaimsatinjectingeventsaligningwithaspecicpatternormodelwhichcouldbederivedbyanalyzingtheapp'scodeorUI.
Thetestcasesgeneratedareusuallymoreeffectiveandefcientindis-coveringmaliciousactivities.
Tosupportthistestingmode,GooglehasdevelopedanexplorationtoolnamedMonkeyRunner[5]whichallowstestingplatformtointeractwithanappinpre-denedeventsequences.
MonkeyRunnerhasbeenadoptedbyseveraltestingplatformsincludingMobile-Sandbox[24],CopperDroid[26],etc.
InthecourseofautomatedUIinteractions,alargenumberofinvalidactionscouldbetriggeredifthepropertiesofUIstructureisdisregarded.
Asasolution,GoogledevelopedUIAutomator[7],whichinspectsthelayouthierarchyanddevicestatustodecidethemeaningfulUIactions.
Besides,AppsPlayground[22]leveragedanumberofheuristicstocustomizeinputsforcertainUIcontrols(e.
g.
,loginbox).
CuriousDroid[10]decomposestheon-screenlay-outandcreatescontext-basedmodelon-the-y.
SmartDroid[33]usesahybridmodelwhichextractscallgraphsthroughstaticanalysisandinitiatesactionsleadingtosensitiveAPIs.
3.
2Motivation:ProgrammedInteractionThemaindesigngoaloftheaboveframeworksistoexploreallpotentialpathsleadingtomaliciousbehaviorsefciently.
Assuch,theinputeventstheygeneratedareusuallypredictable,redatregularandshortinterval,andmassiveforgoodcoverage,whichsignicantlydifferfromwhatareproducedbyhumanusers.
Hence,leveragingthisinsight,wedesignanewmechanismtocapturesuchprogrammedinteractionsanddistinguishhumanusersfromtestingplatforms.
Weenvisionourapproachcouldbeimplementedasacomponent(wecallitPIDetector),embeddedwithinAndroidmalwareandmonitoringthesystemeventsofitsinterests.
Beforetheexecutionofmaliciouspayload,thecollectedeventsequencewillbeanalyzedbyPIDetector,andtheexecutiononlypro-ceedswhentheeventsequenceisdeterminedtobeproducedbyhumanuser.
Comparedwithanti-emulationtechniques,ourapproachoffersanotherlayerofprotectiontomalwareevenanalyzedonbare-metalplatforms.
Itisalsorobustagainsttheupgradeswhichaltertheobservableartifactsbyanalysisframeworks.
Atthehighlevel,ourapproachcanbeconsideredasavariantofCAPTCHA[30]–humanscanpass,butcomputerprogramscan'tpass.
Infact,thestate-of-arttextorimagebasedCAPTCHAschemesmayachievethesameorevenbetteraccuracyindistinguishinghumanandcomputer.
However,askingusertosolveCAPTCHAbeforeusingtheappwoulddriveawaymanyusersandreducetheinfectionrate.
Incontrast,suchissuesarenotembodiedinourapproach.
3.
3AssumptionsOurapproachintendstoevadethedetectionbydynamicanal-ysis.
Evadingstaticanalysisisoutofthescopeofourwork.
Infact,suchtaskcouldbefullledbyoff-the-shelfobfuscatorsandpackers.
Wealsoassumethedynamicanalysisplatformsinteractwiththetestingappthrougheventsinjection,andtheexecutionlogicoftheappcannotbeforcefullyaltered,i.
e.
,bypassingPIDetectoranddirectlyinvokingmaliciouspayloads.
Thisstrategyisintheorypossiblebutrequirespreciseanalysisonapp'scodetoidentifythecriticalbranches,whichisquitechallengingandagainvulnerabletoobfuscationandpackingtechniques.
Thissettingisalsoadoptedbyallpreviousworksonevadingdynamicanalysis[21,28,14,17].
4.
ATTACKVECTORSInthissection,weelaborateseveralattackvectorsthatcanbeleveragedtodetectprogrammedinteractions.
Overall,thequaliedattackvectorsshouldfulllthethreerequirementsbelow:ReverseTuringTest–humanscanpass,butcurrentexplo-rationtoolscan'tpass.
Passive–hardtobediscoveredbyend-users.
Lightweight–easytobebuiltanddeployed.
Giventheseconstraints,wedesigntwoclassesofattackvectorstargetingthevulnerabilitiesunderlyingeventinjectionsandUIelementidenticationindynamicanalysis.
Tonotice,sometestingplatformsbuiltuponMonkeycanbetriviallyidentiedthroughinvokingtheisUserAMonkey()API[3]andinspectingthereturnedvalue.
Wedonotincludeitintotheattackvectorsasthere-turnedvaluecanbeeasilymanipulated(e.
g.
,itcanbebypassedbyUIAutomatorthroughcallingsetRunAsMonkey(false)[18]).
Weelaborateeachattackvectorinthefollowingsubsections.
4.
1DetectingSimulatedEventInjectionsWefoundthedataattachedtotwotypesofuserevents,Mo-tionEvent[6]fortouchscreentappingandKeyEvent[4]forkeypressing,canbeleveragedfordetection.
Itturnsoutthebothindividualeventandeventsequencerevealdistinguishablepatterns.
4.
1.
1SingleEventWhenauseroperatesamobiledevice,theeventsareinitiatedbytheonboardhardwareandtheinformationregardingthehardwareisattached.
Totheopposite,theeventsinjectedbydynamictestingtools,likeMonkey,arepassedfromexternalinterfacesandmostoftheparametersarelledwithdummyvalues.
Specically,whilethecoreparameters(e.
g.
,coordinatesofinputlocation)arelledwithrealvalues,theauxiliaryparameters(e.
g.
,keyboardtype)arenotlledsimilarly.
Table1andTable2listdifferencesbetweenthevaluesgeneratedfromreal-worldusageandMonkeytestingforMotionEventandKeyEvent.
Clearly,Monkeyllsthevaluesinadistinctivepatternthatcanbeidentied.
Forexample,theToolTypeparameterofKeyEventgeneratedbyMonkeyisalwaysTOOL_TYPE_UNKNOWN,whichcannotbeusedifthiseventisproducedbyhardware.
4.
1.
2EventSequenceToreachthehighcoverageofappbehaviorsinlimitedtime,dynamicanalyzerstendtoinjecteventsathighfrequencywhichTable1:MotionEvent:realvs.
simulated(byMonkey)ParameterRealSimulatedToolType1:TOOL_TYPE_FINGER0:TOOL_TYPE_UNKNOWNDeviceId[non-zerovalue]0DevicevalidnullRemarks:1)DeviceId:zeroindicatesthattheeventdoesnotcomefromaphysicaldeviceandmapstothedefaultkeymap.
Table2:KeyEvent:realvs.
simulated(byMonkey)ParameterRealSimulatedScanCode[non-xedvalue]0DeviceId[non-xedvalue]-1Device.
Name[non-xedvalue]VirtualDevice.
Generation[non-xedvalue]2Device.
Descriptor[non-xedvalue]af4d26ea4cdc857cc0f1ed1ed51996db77be1e4dDevice.
KeyboardType1:non-alphabetic2:alphabeticDevice.
Source[non-xedvalue]0x301:keyboarddpadRemarks:1)ScanCode:thehardwarekeyidofthekeyevent;2)Generation:thenumberisincrementedwheneverthedeviceisreconguredandthereforenotconstant;3)Descriptor:theuniqueidentierfortheinputdevice;4)KeyboadType:thevalueis"non-alphabetic"asthenowadayssmartphonemodelsdonotintegratehardwarekeyboards.
cannotbeperformedbyhumanusers.
Therefore,bymeasuringthefrequencyoftheeventsthedynamicanalyzerscouldbeidentied.
Also,thedistributionofeventsalongtimeseriesisalsouniquefordynamicanalyzers,andweshowhowthisobservationcouldbeleveragedforourpurposes.
Besides,thekeypressesareusuallyissuedatchangingspeedwhenausertypestextinEditTextwhiletheintervalisxedfordynamicanalyzers.
IMEpartiallycausesthis:anIMEwillshowupwhenausertapsEditTextandduetothevarianceofthedistancesbetweencharactersonIME,theintervalbetweenkeypressesuctuates.
FromtheaspectofMotionEventseries,Androidprovidesstan-dardAPIsforanapptorecognizetouchgesturesinputtedbyuser.
Atthesametime,aseriesofscreentouchingevents(MotionEvent)canbeobserved,andtheeventsareissuedmuchmoreregulariffromdynamicanalyzers.
Asanexample,weaskedaparticipanttoswipethetouchscreenonSamsungGalaxySIIIfromfarlefttofarrightanddirectedMonkeyRunnerforthesameaction.
Thetestwasran10timesandwedrawthetaplocationsinx-axis(floatxeldofMotionEvent)against20samplepointsatthesameintervalinFigure1.
Thetrajectoriesoftheswipesfromtheuserareratherdispersed,anddisplacementsatthestartandendoftheactionaresmaller.
Incontrast,Monkey'sswipesarehighlysimilarandaremovedatconstantspeed.
Suchdifferencecouldbemodeledthroughtimeseriessimilaritymeasurerelatedalgorithms.
4.
2ImplantingUITrapsToincreasethechanceoftriggeringmaliciousactivities,espe-ciallytheonesassociatedwithuserbehaviors,dynamicanalyzershavetoexploreandinteractwithasmanyUIelementsaspossible.
Suchdesign,however,leadstoadilemmathatcanbeexploited:theadversarycouldimplantUItrapsthatareinaccessibletohumanusersandunabletobedistinguishedbydynamicanalyzers.
Belowweelaboratethedesignsoftwosuchattackvectors:4.
2.
1IsolatedActivityAnAndroidappdenestheUIinterfaceandroutinesforeventprocessinginActivitycomponent,whichisalsodeclaredintheFigure1:Swipingtrajectory:realuservs.
explorationtoolFigure2:ExampleofisolatedActivityManifestle.
AnappusuallycontainsonemainActivityandsubsequentActivitiesthatcanbetransitionedto,asshowninFigure2.
Inaddition,developerscouldexportanActivitythatcanbelaunchedbyotherapps(Activity4inFigure2),throughsettingandroid:exported="true".
Commondynamican-alyzerstendtoparsetheManifestleandvisitActivitiesinbothcaseswhiletheusersfollowthedenedinteractionlogictovisitActivities.
ThismotivatesustocreateanisolatedActivitywhichcouldnotbereachedthroughinteractionasatrap:ifanunusedandexportedActivityisinvoked,thepartybehindshouldbedynamicanalyzer.
Suchtrapishardtobedetectedahead,astheinteractionlogicisdenedinapp'scodeandcanbeobfuscated.
4.
2.
2InvisibleUIElementsWedemonstrateanotherattackvectorherewhichmanipulatesthevisualeffectsofUIelements.
AhumanusernormallytapstheUIelementsshecanseetoinputinformation.
Ontheotherhand,dynamicanalyzerscouldinvokesystemAPIs(suchasparseViewHierarchyunderDeviceBridgeclass)toiden-tifyvalidelementsandsimulatetheinteraction.
Therefore,wecouldleaveavalidbut"invisible"controlinActivityasatrap,anduseittodetectthedynamicanalyzerfallingin.
Infact,AndroidUIlibraryprovidesasetofhighlycustomiz-ableUIcontrolsfordevelopers,includingButton,TextView,Switch,etc.
andtheycanbeeasilyconguredtobeinvisible.
OnesuchcontrolisImageButtonthatdisplaysimageasabuttonandacceptsclicks.
Iftheimageislledwiththesamecolorasthenearbypixelsofbackground,itwouldnotbediscoveredbythehumanuser.
Moreover,wecouldchangethelayoutandlocationofthecontrolsforthesamepurpose.
Forinstances,wecouldsetthecontroltobetiny(e.
g.
,1pixel)orfalloutofthescreen.
Figure3explainsthisidea.
Fromhuman'sview,onlyabutton(Test)andasentence(HelloWorld)canbeidentied.
Actually,5UIcontrolsareembeddedinthelayout:textview,imagebutton,switch,imagebutton,andbutton.
Theyareallvalidtodynamicanalyzers.
Forexample,weranGoogleUIAutomatortoparsetheUIlayoutanditrecognizesallcontrolsandextractstheinformationlistedbelow:(a)Reallaylout(b)Human'sviewFigure3:InvisibleUIelements:reallayoutvs.
human'sview(0)FrameLayout[0,0][720,1280](0)View[0,50][720,146](1)TextView:HelloWorld[32,178][178,216](2)ImageButton[176,178][178,180](3)Switch:ON[408,124][614,180](4)ImageButton[32,318][132,418](5)Button:Test[560,318][688,414]Allthesecontrolswillbeexercisedbydynamicanalyzers,butonlyandcouldbenoticedbyhuman.
Therefore,eventsredonothercontrolscouldindicatetheexistenceofdynamicanalyzers.
Toescapefromthistypeoftraps,dynamicanalyzershavetoaccuratelydeterminethevisibilityofUIcontrols(tohumaneyes),whichremainsanopenproblem.
5.
EVALUATIONInthissection,wepresenttheexperimentalresultsontheeffec-tivenessofPIDetector.
Thetestingmethodologyisintroducedrst,andtheresultsarediscussedafter.
TestingMethodology.
WedevelopedatestingappintegratingPIDetectorasaninternalcomponent.
OurgoalistoexaminewhetherPIDetectorcancorrectlydetectdynamicanalyzersthroughoneormoreattackvectors.
Therefore,thetestingapponlyhasbasicUIandfunctionalities,andwedidnotincludemaliciouspayloadintothetestingapptoreducetheimpacttotheoperationalizedplatforms.
Whentheappisloaded,PIDetectorstartstocollectrawlogsregardingredevents(detailsareprovidedbelow).
TherawlogsweresenttoanHTTPserversetuponAmazonElasticBeanstalk[1]andanalyzedthroughthemodelsimplementedbyus.
Wedecidetoexltratetheeventdatatogainabetterunderstandingofthebehaviorsoftestingplatforms.
Allanalysiscanbedonelocallywhenadoptedbyadversary'srealapp.
RawLogs.
Thecollectedrawlogsincludethefollowinginforma-tion:theparametersofcapturedMotionEventandKeyEventobjects,invokedActivities,visitedUIelements.
EveryreturnedlogispaddedwithauniqueIDtodistinguishdifferenttestingplatformsandtimesofrunning.
Onlytherst100logsaretransmittedtotheservertoobtainenoughdataandavoidexcessivenetworkconnec-tions,whichmightbeconsideredasanomalyactivitiesbytestingplatforms.
Wealsocollectedthecongurationinformationofeverytestedservice,suchasAndroidID,IMEI,Build.
SERIALandBuild.
MANUFACTURER,toseeifcountermeasuresagainstanti-emulationaredeployed.
TestingPlatforms.
Wetested10dynamicanalysisservicesbuiltformalwareanalysis,amongwhichfourcomefromtheacademiawhiletheotherscomefromthesecuritycompanies.
Inaddition,weuploadourtestingapptoGooglePlaytotestitsofcialdynamicanalyzer,GoogleBouncer.
These11servicesarelistedinTable3.
TheexperimentswereconductedinJanuaryandMarch2016.
Wewereabletoobtainvalidrawlogsfrom7services,andthenalresultsaresummarizedinTable3.
Amongtheremainingones,A5andCopperDroidrefusedtoanalyzeourapp,sincetheprocessingqueuehasbeenfullyoccupied.
NorawlogsorinformativemessagesarereturnedforPayloadSecurityandMalwr,andwespeculatethecausesare:1)theyonlylaunchstaticanalysisonourapp;2)Theoutboundnetworkconnectionsfromappareblocked.
Finding1.
Nearlyall(available)analysisservicesarevulnerabletoatleastoneattackvector.
Mostofthemcouldbeidentiedbyanalyzingsingleeventparameter,exceptTraceDroidforlackingenoughparametersandGoogleBouncerforllingvalidvalues.
Forexample,theInputDeviceparameteroftheKeyEventfromSandDroidwasalways"-1".
IsolatedActivityfeatureisalsoquiteeffective,andhalfoftheseonlineservicesfellintothistrap.
Ontheotherhand,onlyTecentHabohitinvisibleelements,andnoservicewasfoundtogeneratecontinuouseventsequence(e.
g.
,swipe).
WesuspectthattheseinteractionsaremissedbecausecomplexUIanalysisandinteractionsarenotperformed.
Finding2.
Emulatorcamouagingorphysicaldevicehasbeendeployedbyonlineanalysissystems.
Forexample,wefoundtheplatformcongurationofGoogleBouncerisquitelikephysicaldevice–GoogleNexus5or6,asshowingbelow:Version:6.
0.
1SDK_INT:23MODEL:Nexus6BRAND:googleBOARD:shamuDEVICE:shamuHARDWARE:shamuSERIAL:ZX1G22HMB3ID:MMB29KPRODUCT:shamuDISPLAY:MMB29KMANUFACTURER:motorolaHOST:wped2.
hot.
corp.
google.
comBOOTLOADER:moto-apq8084-71.
15FINGERPRINT:google/shamu/shamu:6.
0.
1/MMB29K/2419427:user/release-keysTonotice,emulatorcamouagehasbeenusedforotherpurposesonAndroidplatform.
BlueStacks[2],apopularemulatordesignedforrunningAndroidgamesonWindowsandMacplatforms,camouagesitselfascertainmodelsofSamsungdevicestoevadeemulatordetectionperformedbyapps.
Hence,webelieveourtechniquesforprogrammedinteractiondetectionismeaningfulevenintheshorttermtoattackers.
6.
DISCUSSIONLimitations.
Ascountermeasures,thedevelopersofdynamicanalyzerscouldchangetheUIinteractionpatternandmakethetestingprocessclosertohumanbeings.
Forexample,thedummyparametervaluesoftheinjectedMotionEventandKeyEventcouldbechangedtouserealdata.
Ontheotherhand,howtohideagainstthemorecomplicatedattackvectorswedevised(e.
g.
,eventsequence)isunclear.
Thoughuser'sinteractionsonAppUIcanberecordedandreplayed,challengeshavetobeaddressedonhowtoautomaticallyadjusttherecordedactionstodifferentapps.
7.
CONCLUSIONInthiswork,weproposeanewapproachtoevadeAndroidruntimeanalysis.
Thisapproachfocusesondetectingprogrammedinteractionstodeterminewhetheranappisunderanalysis,insteadofrelyingonthetraditionalemulatordetection.
Thepreliminaryexperimentalresultshavedemonstratedtheeffectivenessofourmethods.
Webelievetheevasivetechniquesleveragingsubtletiesofhuman-computerinteractionshouldbeseriouslyconsideredbyTable3:ExperimentalresultsforonlinedynamicanalysisservicesServiceNameURLSimulatedEventsUITrapsMotionEventParamtersKeyEventParametersEventSequenceIsolatedActivityInvisibleUIElementsNVISOApkScanhttps://apkscan.
nviso.
be√√SandDroidhttp://sanddroid.
xjtu.
edu.
cn√√√TraceDroid[27]http://tracedroid.
few.
vu.
nl**√Anubis[15]http://anubis.
iseclab.
org*√√TecentHabohttps://habo.
qq.
com/√√√VisualThreathttps://www.
visualthreat.
com√√GoogleBouncerN/A–nopubliclinkA5[29]http://dogo.
ece.
cmu.
edu/a5/Theuploadprocessalwaysreportederror.
CopperDroid[26]http://copperdroid.
isg.
rhul.
ac.
ukToomanysubmittedsampleswerequeued.
Malwrhttps://malwr.
comNorawlogwasreturned.
PayloadSecurityhttps://www.
hybrid-analysis.
comNorawlogwasreturned.
Remarks:1)"√":Judgedasprogrammedinteraction.
2)"*":Judgedashumaninteraction.
3)"":Nottriggeredorfound.
4)"":GoogleBouncerclickedallbuttonsonthemainActivitybutignoredtheimagebuttonwhichwascamouagedasanormalbuttonbyus.
WespeculateBounceronlytriggerstheUIcontrolswiththeButtonpropertybydesign.
Sincethisisindirectevidence,sowelabelitas"".
securitycommunityandcallforfurtherresearchonclosingthegapbetweenmachineandhumaninruntimebehaviors.
8.
ACKNOWLEDGEMENTSWethankanonymousreviewersfortheirinsightfulcomments.
ThisworkwaspartiallysupportedbyNSFC(GrantNo.
61572415),aswellastheDirectGrant(ProjectNo.
CUHK4055047)andEarlyCareerScheme(ProjectNo.
24207815)establishedundertheUni-versityGrantCommitteeoftheHongKongSpecialAdministrativeRegion,China.
9.
REFERENCES[1]AWSElasticBeanstalk.
http://aws.
amazon.
com/elasticbeanstalk/.
[2]BlueStacks.
http://www.
bluestacks.
com/.
[3]isUserAMonkey().
http://developer.
android.
com/reference/android/app/ActivityManager.
html#isUserAMonkey().
[4]KeyEvent.
http://developer.
android.
com/reference/android/view/KeyEvent.
html.
[5]MonkeyRunner.
http://developer.
android.
com/tools/help/monkeyrunner_concepts.
html.
[6]MotionEvent.
https://developer.
android.
com/reference/android/view/MotionEvent.
html.
[7]TestingSupportLibrary.
https://developer.
android.
com/tools/testing-support-library/index.
html.
[8]UI/ApplicationExerciserMonkey.
http://developer.
android.
com/tools/help/monkey.
html.
[9]GDATAMobileMalwareReport-ThreatReport:Q4/2015.
https://secure.
gd/dl-us-mmwr201504,2016.
[10]P.
Carter,C.
Mulliner,M.
Lindorfer,W.
Robertson,andE.
Kirda.
CuriousDroid:AutomatedUserInterfaceInteractionforAndroidApplicationAnalysisSandboxes.
InFinancialCryptographyandDataSecurity-20thInternationalConference,FC2016,RevisedSelectedPapers,2016.
[11]C.
Dietzel.
PortingandImprovinganAndroidSandboxforAutomatedAssessmentofMalware.
Master'sthesis,HochschuleDarmstadt,2014.
[12]J.
Gajrani,J.
Sarswat,M.
Tripathi,V.
Laxmi,M.
S.
Gaur,andM.
Conti.
ARobustDynamicAnalysisSystemPreventingSandBoxDetectionbyAndroid.
InProceedingsofthe8thInternationalConferenceonSecurityofInformationandNetworks(SIN),2015.
[13]W.
HuandZ.
Xiao.
GuessWhereIam:DetectionandPreventionofEmulatorEvadingonAndroid.
XFocusInformationSecurityConference(XCon),2014.
[14]Y.
Jing,Z.
Zhao,G.
Ahn,andH.
Hu.
Morpheus:AutomaticallyGeneratingHeuristicstoDetectAndroidEmulators.
InProceedingsofthe30thAnnualComputerSecurityApplicationsConference(ACSAC),2014.
[15]M.
Lindorfer,M.
Neugschwandtner,L.
Weichselbaum,Y.
Fratantonio,V.
vanderVeen,andC.
Platzer.
ANDRUBIS-1,000,000AppsLater:AViewonCurrentAndroidMalwareBehaviors.
InProceedingsofthe3rdInternationalWorkshoponBuildingAnalysisDatasetsandGatheringExperienceReturnsforSecurity(BADGERS),2014.
[16]H.
Lockheimer.
AndroidandSecurity.
http://googlemobile.
blogspot.
com/2012/02/android-and-security.
html,2012.
[17]D.
Maier,M.
Protsenko,andT.
Müller.
AGameofDroidandMouse:TheThreatofSplit-PersonalityMalwareonAndroid.
Computers&Security,54:2–15,2015.
[18]A.
Momtaz.
Allowforsettingtesttypeasamonkey.
https://android.
googlesource.
com/platform/frameworks/base/+/8f6f1f4%5E!
/,2013.
[19]S.
Mutti,Y.
Fratantonio,A.
Bianchi,L.
Invernizzi,J.
Corbetta,D.
Kirat,C.
Kruegel,andG.
Vigna.
Baredroid:Large-scaleAnalysisofAndroidAppsonRealDevices.
InProceedingsofthe31stAnnualComputerSecurityApplicationsConference(ACSAC),2015.
[20]S.
Neuner,V.
vanderVeen,M.
Lindorfer,M.
Huber,G.
Merzdovnik,M.
Mulazzani,andE.
R.
Weippl.
EnterSandbox:AndroidSandboxComparison.
InProceedingsofthe2014IEEEMobileSecurityTechnologiesWorkshop(MoST),2014.
[21]T.
Petsas,G.
Voyatzis,E.
Athanasopoulos,M.
Polychronakis,andS.
Ioannidis.
RageAgainsttheVirtualMachine:HinderingDynamicAnalysisofAndroidMalware.
InProceedingsoftheSeventhEuropeanWorkshoponSystemSecurity(EuroSec),2014.
[22]V.
Rastogi,Y.
Chen,andW.
Enck.
AppsPlayground:AutomaticSecurityAnalysisofSmartphoneApplications.
InProceedingsoftheThirdACMConferenceonDataandApplicationSecurityandPrivacy(CODASPY),2013.
[23]V.
Rastogi,Y.
Chen,andX.
Jiang.
CatchMeIfYouCan:EvaluatingAndroidAnti-MalwareAgainstTransformationAttacks.
IEEETransactionsonInformationForensicsandSecurity(TIFS),9(1):99–108,2014.
[24]M.
Spreitzenbarth,F.
C.
Freiling,F.
Echtler,T.
Schreck,andJ.
Hoffmann.
Mobile-Sandbox:HavingaDeeperLookintoAndroidApplications.
InProceedingsofthe28thAnnualACMSymposiumonAppliedComputing(SAC),2013.
[25]A.
Takanen,J.
DeMott,andC.
Miller.
FuzzingOverview.
InFuzzingforSoftwareSecurityTestingandQualityAssurance.
ArtechHouse,2008.
[26]K.
Tam,S.
J.
Khan,A.
Fattori,andL.
Cavallaro.
CopperDroid:AutomaticReconstructionofAndroidMalwareBehaviors.
InProceedingsofthe22ndAnnualNetworkandDistributedSystemSecuritySymposium(NDSS),2015.
[27]V.
vanderVeen.
DynamicAnalysisofAndroidMalware.
Master'sthesis,VUUniversityAmsterdam,2013.
[28]T.
VidasandN.
Christin.
EvadingAndroidRuntimeAnalysisviaSandboxDetection.
InProceedingsofthe9thACMSymposiumonInformation,ComputerandCommunicationsSecurity(ASIACCS),2014.
[29]T.
Vidas,J.
Tan,J.
Nahata,C.
L.
Tan,N.
Christin,andP.
Tague.
A5:AutomatedAnalysisofAdversarialAndroidApplications.
InProceedingsofthe4thACMWorkshoponSecurityandPrivacyinSmartphones&MobileDevices(SPSM),2014.
[30]L.
vonAhn,M.
Blum,N.
J.
Hopper,andJ.
Langford.
CAPTCHA:UsingHardAIProblemsforSecurity.
InAdvancesinCryptology-EUROCRYPT2003,InternationalConferenceontheTheoryandApplicationsofCryptographicTechniques,Proceedings,2003.
[31]L.
YanandH.
Yin.
DroidScope:SeamlesslyReconstructingtheOSandDalvikSemanticViewsforDynamicAndroidMalwareAnalysis.
InProceedingsofthe21stUSENIXSecuritySymposium,2012.
[32]Y.
Zhang,M.
Yang,B.
Xu,Z.
Yang,G.
Gu,P.
Ning,X.
S.
Wang,andB.
Zang.
VettingUndesirableBehaviorsinAndroidAppswithPermissionUseAnalysis.
InProceedingsofthe2013ACMSIGSACConferenceonComputerandCommunicationsSecurity(CCS),2013.
[33]C.
Zheng,S.
Zhu,S.
Dai,G.
Gu,X.
Gong,X.
Han,andW.
Zou.
SmartDroid:anAutomaticSystemforRevealingUI-basedTriggerConditionsinAndroidApplications.
InProceedingsofthe2012ACMWorkshoponSecurityandPrivacyinSmartphonesandMobileDevices(SPSM),2012.
cuhk.
edu.
hkXiangyuLiuTheChineseUniversityofHongKonglx012@ie.
cuhk.
edu.
hkZhouLiACMMemberlzcarl@gmail.
comKehuanZhangTheChineseUniversityofHongKongkhzhang@ie.
cuhk.
edu.
hkABSTRACTDynamicanalysistechniquehasbeenwidelyusedinAndroidmalwaredetection.
Previousworksonevadingdynamicanalysisfocusondiscoveringthengerprintsofemulators.
However,suchmethodhasbeenchallengedsincetheintroductionofrealdevicesinrecentworks.
Inthispaper,weproposeanewapproachtoevadeautomatedruntimeanalysisthroughdetectingprogrammedinteractions.
Thisapproach,inessence,triestotelltheidentityofthecurrentappcontroller(humanuserorautomatedexplorationtool),byndingintrinsicdifferencesbetweenhumanuserandmachinetesterininteractionpatterns.
Theeffectivenessofourapproachhasbeendemonstratedthroughevaluationagainst11real-worldonlinedynamicanalysisservices.
KeywordsAndroidmalware;dynamicanalysis;programmedinteraction1.
INTRODUCTIONWiththeevolutionofmobilecomputingtechnology,smartphonehasexperiencedenormousgrowthinconsumermarket,amongwhichAndroiddeviceshavetakenthelion'sshare.
Unfortunately,Android'sopenecosystemalsoturnsitselfintoaplaygroundformalware.
Accordingtoarecentreport[9],onaverage,8,240newAndroidmalwaresampleswerediscoveredinasingleday.
TocombatthemassivevolumeofAndroidmalwarenewlyemerged,automateddetectiontechniques(staticanddynamic)wereproposedandhavebecomethemainstreamsolutions.
Dy-namicanalysisframeworksmonitorthebehaviorsoftheappsam-plesexecutedinacontrolledenvironmentunderdifferentstimuli.
Comparedwithstaticanalysis,dynamicanalysisdoesnothavetounderstandthecomplicatedlogicinmaliciouscodeandisimmunetocodeobfuscationandpacking.
Moreover,lessnoticeablerun-timemaliciousbehaviorscouldbediscovered.
Thetraditionaldynamicanalysisplatformswerelargelybuiltuponemulatorstoenablefastandeconomicmalwareanalysis.
Permissiontomakedigitalorhardcopiesofallorpartofthisworkforpersonalorclassroomuseisgrantedwithoutfeeprovidedthatcopiesarenotmadeordistributedforprotorcommercialadvantageandthatcopiesbearthisnoticeandthefullcitationontherstpage.
Copyrightsforcomponentsofthisworkownedbyothersthantheauthor(s)mustbehonored.
Abstractingwithcreditispermitted.
Tocopyotherwise,orrepublish,topostonserversortoredistributetolists,requirespriorspecicpermissionand/orafee.
Requestpermissionsfrompermissions@acm.
org.
WiSec'16,July18–20,2016,Darmstadt,Germany.
2016Copyrightheldbytheowner/author(s).
PublicationrightslicensedtoACM.
ISBN978-1-4503-4270-4/16/07.
.
.
$15.
00DOI:http://dx.
doi.
org/10.
1145/2939918.
2939926Toevadedynamicanalysis,abroadspectrumofanti-emulationtechniqueshavebeenproposed[21,28,14,17]andadoptedbymalwareauthors.
Ingeneral,thesetechniquesweredesignedtongerprinttheruntimeenvironmentandlookforartifactsthatcantellphysicaldeviceandemulatorapart.
Thougheffectiveatrst,countermeasureshavebeendevelopedbythesecuritycommunitytodiminishtheefcacyofanti-emulation.
Recently,researchersproposedtousephysicaldevices[19]andmorphartifactsuniquetoemulators[12,11,13].
Thesemethodswreckedthebaseofanti-emulationtechniques,butwebelievethearmsracebetweendynamicanalysisandevasionhasnotyetended.
AutomatedExploration.
Differentfromthetraditionaldesktopmalware,Androidmalwareareevent-driven,meaningthatmali-ciousbehaviorsareusuallytriggeredaftercertaincombinationsofuseractionsorsystemevents.
Therefore,thesimpleinstall-then-executeanalysismodelisnoteffectivetotriggermalware'sruntimebehaviors.
Tosolvethisissue,automatedexplorationtechniquesareintegratedintodynamicanalysisframeworks,includingeventinjection,UIelementidentication,etc.
Theultimategoalofthemistoachievegoodcoverageofapp'sexecutionpathsinalimitedperiod.
NewEvadingTechniques.
Inthispaper,weproposeanewapproachtoevadeAndroidautomatedruntimeanalysisthroughdetectingprogrammedinteractions.
Thecoreideaofthisapproachistodeterminetheidentityofthepartyoperatingtheapp(ahumanuseroranautomatedexplorationtool)bymonitoringtheinteractionpatterns.
Tomalwareanalysis,thegoalofinteractionisdifferentfromthatofarealuser.
Forefciency,explorationtoolinjectssimulatedusereventsandavoidsaccessingtheunderlyingdevices.
Suchsimulatedeventsandhardwaregeneratedonesareinconsistentinmostcases.
Also,toachievehighcoverageofexecutionpaths,explorationtooltendstotriggerallvalidcontrols,amongwhichsomearenotsupposedtobetriggeredbyhuman.
WeleveragetheseinsightsandbuiltanevasivecomponentPIDetector,whichmonitorstheeventstreamandidentiestheeventsunlikelycomingfromarealuser.
Themaliciouspayloadwillbeheldfromexecutionifadynamicanalyzerisidentied.
Comparedwiththepreviousanti-emulationtechniques,ourapproachexploitsthegapbetweenhumanandmachineinrun-timebehaviors,insteadofrelyingonfeaturesregardingexecutionenvironment.
Oneprominentadvantageofourapproachisitsrobustnessagainstanytestingplatform,evenonecomposedofphysicaldevices.
Weimplementedaproof-of-conceptappandsubmitteditto11onlinedynamicanalysisservicesscreeningsamplessubmittedfromallsortsofsources.
Thepreliminaryresultshavealreadydemonstratedtheeffectivenessofourapproach:nearlyall(avail-able)surveyedservicesexhibitatleastonepre-denedpatternofprogrammedinteractions.
Asarecommendation,thedesignofthecurrentdynamicanalysisplatformsshouldberevisitedtodefendagainstsuchnewtypeofevasion.
Contributions.
Wesummarizethispaper'scontributionsasbelow:NewTechniqueandAttackSurface.
Weproposeanewap-proachtoevadeAndroidruntimeanalysis:programmedin-teractiondetection,whichprovidesanewvenueforevadingdynamicanalysisotherthanexistinganti-emulationworks.
ImplementationandEvaluation.
Weimplementedaproof-of-conceptappandtesteditonseveralreal-worldAndroiddynamicanalysisplatforms.
Theexperimentalresultsdemon-strateourapproachishighlyeffective.
2.
RELATEDWORKMostAndroiddynamicanalysisframeworksarebuiltuponem-ulators[20],whichiseasiertobedeployedandmoreeconomical,asthecostofpurchasingmobiledevicesisexempted.
Besides,theappbehaviorsonemulatorsareeasiertobemonitoredandcontrolled.
Suchframeworks,however,arenotrobustagainstevasivemalware,andanti-emulationtechniqueshavebeenwidelydiscussed.
Inthissection,wereviewthesetechniquesanddescribethecountermeasuresproposedbysecuritycommunity.
2.
1Anti-EmulationNearlyallpreviousanti-emulationtechniques[21,28,14,17]exploittheuniquefeaturesofthevirtualizedenvironmentandrefrainfromexecutingthecoremaliciouspayload(e.
g.
,sendingSMStopremiumnumber)whenthehostisfoundasanemulator.
Thefeaturesthatdifferentiateemulatorsfromrealmobiledevicesandareleveragedforanti-emulationarelistedbelow:FirmwareFeatures.
Themobiledevicesmanufacturedbyvendorsareassembledfromdistinctivermware,whichembedsuniqueIDorinformationreectingthehardwarespecication.
Onthecontrary,emulatorstendtousexeddummyvaluestollrmwarefeatures.
Forexample,nullandandroid-testarefedtormware-queryAPIslikeBuild.
SERIALandBuild.
HOSTbyemulators.
DeviceFeatures.
Alotofperipheraldevices,especiallysensors,havebeenintegratedintomobiledevices,likeaccelerometerandgyroscope.
Notallthesensorsaresupportedbyemulators,whichcanbeexploitedforemulatoridentication.
Forthesensorssimulatedbyemulators,thedatastreamproduceddifferssigni-cantly(usuallyconstant)fromwhatisgeneratedfromrealdevices(randomlydistributed)[28].
PerformanceFeatures.
Performance,particularlyprocessingspeed,isadisadvantageforemulators.
ThoughmoderndesktopPChasmoreprocessingpower,suchimprovementisoverwhelmedbypenaltyfrominstructiontranslation.
Asshownin[28],adversarycouldmeasureCPUandgraphicalperformance,andthendeterminetheexistenceofemulator.
Italsoturnsoutthatthereexistsahugenumberofheuristicscanbeemployedforemulatordetection.
Jingetal.
[14]proposedaframeworkwhichcanautomaticallydetectthediscrepanciesbetweenAndroidemulatorsandrealdevices,andmorethan10,000heuristicshavebeendiscovered.
Fixingthesediscrepanciesonemulatorsneedstremendouseffortsbyallmeans.
2.
2CountermeasuresTheanti-emulationtechniquessurveyedabovearequiteeffectivebutnotimpeccable.
Theyalllookforobservableartifactsproducedfromvirtualization,whichturnsouttobetheAchilles'heel.
Wedescribetwotypesofcountermeasuresforobscuringrunningplatformbelow:UsingPhysicalDevices.
Buildinganalysisplatformonphysicaldevicescouldthwartanti-emulationbehaviorsnaturally.
Vidasetal.
[29]proposedahybridsystemnamedA5,whichcombinesbothvirtualandphysicalpoolsofAndroiddevices.
Morerecently,Muttietal.
[19]proposedBareDroid,whichrunsbare-metalanalysisonAndroidapps.
Thesystemisbuiltsolelyuponoff-the-shelfAndroiddevicesandappliesseveralnoveltechniqueslikefastrestorationtoreducetheperformancecost.
Theevaluationresultsoftheseworksprovethatmalwarearenotabletodiscerntheanalysisplatformwithusers'devices.
ChangingArtifacts.
Anotherdirectionistochangetheobservableartifactstomasqueradetheemulatorsasrealdevices.
Huetal.
[13],Dietzel[11]andGajranietal.
[12]followedthistrail.
TheycustomizedtheemulatorframeworkandhookedruntimeAPIs(inbothJavaandLinuxlayer)tofeedfakevaluestotheprobingfunctionsofmalware.
Themaliciousbehaviorscouldberevealedwhenthechecksforrealdevicesareallpassed.
3.
BACKGROUNDANDMOTIVATIONFromtheperspectiveoftheadversary,pursuingthedirectionofngerprintingexecutionenvironmentwouldleadtoadead-endinthetrendthatmoreandmoreanalysisplatformsaredrivenbyrealdevicesortailoredemulators.
Inthiswork,weexploreanewdirection:insteadofsensingwhatenvironmentrunstheapp,weinspectthebehaviorsofdynamicanalyzerandfocusonhowitinteractswiththeapp.
Werstbrieyoverviewthecurrentdynamicanalysistechniquesandthenintroducetheconceptofprogrammedinteractiontomotivateourresearch.
3.
1DynamicAnalysisDifferentfromstaticanalysistools,whichscrutinizethesourcecodeorbinarycodeoftheprogramtoidentifythemaliciouspayload,dynamicanalysisframeworksexecutetheprogramtocapturethemaliciousbehaviorsintheruntime.
Inparticular,theexecutionenvironmentfordynamicanalysisisinstrumented,andvarioussystemoruserinputs(e.
g.
,clickingUIbuttons)areinjectedtotriggerallsortsofapp'sbehaviors.
IfcertainmaliciousI/Opatternsorbehaviorsareidentied(e.
g.
,sendingSMStopremiumnumbers),theappisconsideredasmalware.
Thoughstaticanalysisavoidsthecostofrunningappandisusuallymoreefcient,itcouldbethwartedwhenobfuscationorpackingtechniquesareemployed.
AsshownintheworkbyRastogietal.
[23],commonmalwaretransformationtechniquescouldmakemaliciousappsevadepop-ularstaticanalysistoolsathighsuccessrate.
Ontheotherhand,dynamicanalysisisrobustagainstcode-levelevadingtechniquesandissuitableforprocessingappswithcomplicatedprogramlogics.
Acorpusofframeworkshavebeendevelopedandprovedtobeeffective,includingDroidScope[31],AppsPlayground[22],CopperDroid[26],etc.
Googlealsodevelopeditsdynamicanalysisframework,Bouncer[16],tocheckeveryappsubmittedtoGooglePlay.
3.
1.
1InputGenerationandAutomatedExplorationSinceapp'sruntimebehaviorsoftendependontheinputsfromtheuserorsystem,theeffectivenessofthedynamicanalysisframeworkhighlydependsonthestrategyofinputgeneration.
ComparingtothetraditionalPCmalware,whichtendtotakemaliciousactions(e.
g.
,controllingthesystem)onceexecuted,mobilemalwaretendtodelaythemaliciousactionstillasequenceofeventsareobserved(e.
g.
,hijackingthelegitimateappandstealingthereceivedmessages).
Therefore,thetestingplatformshouldbeabletogeneratetheinputinacontext-awaremannerandexploretheexecutionpathsautomatically.
Below,wedescribetwowidelyadoptedstrategiesinautomatedpathexploration:Fuzzing-basedExploration.
Fuzzingisablack-boxtestingtechniqueinwhichthesystemundertestisstressedwithinvalid,unexpectedorrandominputstransmittedfromexternalinterfacestoidentifythebugsinprograms[25].
OntheAndroidplatform,GoogleprovidesanofcialfuzzerMonkey[8],whichgeneratespseudo-randomstreamsofusereventssuchasclicks,touches,orgestures,aswellasanumberofsystem-leveleventsandinjectsthemintotheframeworkthroughAndroidDebugBridge(ADB).
SeveraldynamicanalysisframeworkshaveincorporatedMonkeyastheexplorationengine,suchasVetDroid[32]andAndrubis[15].
Model-basedExploration.
Onthecontrary,model-basedtestingaimsatinjectingeventsaligningwithaspecicpatternormodelwhichcouldbederivedbyanalyzingtheapp'scodeorUI.
Thetestcasesgeneratedareusuallymoreeffectiveandefcientindis-coveringmaliciousactivities.
Tosupportthistestingmode,GooglehasdevelopedanexplorationtoolnamedMonkeyRunner[5]whichallowstestingplatformtointeractwithanappinpre-denedeventsequences.
MonkeyRunnerhasbeenadoptedbyseveraltestingplatformsincludingMobile-Sandbox[24],CopperDroid[26],etc.
InthecourseofautomatedUIinteractions,alargenumberofinvalidactionscouldbetriggeredifthepropertiesofUIstructureisdisregarded.
Asasolution,GoogledevelopedUIAutomator[7],whichinspectsthelayouthierarchyanddevicestatustodecidethemeaningfulUIactions.
Besides,AppsPlayground[22]leveragedanumberofheuristicstocustomizeinputsforcertainUIcontrols(e.
g.
,loginbox).
CuriousDroid[10]decomposestheon-screenlay-outandcreatescontext-basedmodelon-the-y.
SmartDroid[33]usesahybridmodelwhichextractscallgraphsthroughstaticanalysisandinitiatesactionsleadingtosensitiveAPIs.
3.
2Motivation:ProgrammedInteractionThemaindesigngoaloftheaboveframeworksistoexploreallpotentialpathsleadingtomaliciousbehaviorsefciently.
Assuch,theinputeventstheygeneratedareusuallypredictable,redatregularandshortinterval,andmassiveforgoodcoverage,whichsignicantlydifferfromwhatareproducedbyhumanusers.
Hence,leveragingthisinsight,wedesignanewmechanismtocapturesuchprogrammedinteractionsanddistinguishhumanusersfromtestingplatforms.
Weenvisionourapproachcouldbeimplementedasacomponent(wecallitPIDetector),embeddedwithinAndroidmalwareandmonitoringthesystemeventsofitsinterests.
Beforetheexecutionofmaliciouspayload,thecollectedeventsequencewillbeanalyzedbyPIDetector,andtheexecutiononlypro-ceedswhentheeventsequenceisdeterminedtobeproducedbyhumanuser.
Comparedwithanti-emulationtechniques,ourapproachoffersanotherlayerofprotectiontomalwareevenanalyzedonbare-metalplatforms.
Itisalsorobustagainsttheupgradeswhichaltertheobservableartifactsbyanalysisframeworks.
Atthehighlevel,ourapproachcanbeconsideredasavariantofCAPTCHA[30]–humanscanpass,butcomputerprogramscan'tpass.
Infact,thestate-of-arttextorimagebasedCAPTCHAschemesmayachievethesameorevenbetteraccuracyindistinguishinghumanandcomputer.
However,askingusertosolveCAPTCHAbeforeusingtheappwoulddriveawaymanyusersandreducetheinfectionrate.
Incontrast,suchissuesarenotembodiedinourapproach.
3.
3AssumptionsOurapproachintendstoevadethedetectionbydynamicanal-ysis.
Evadingstaticanalysisisoutofthescopeofourwork.
Infact,suchtaskcouldbefullledbyoff-the-shelfobfuscatorsandpackers.
Wealsoassumethedynamicanalysisplatformsinteractwiththetestingappthrougheventsinjection,andtheexecutionlogicoftheappcannotbeforcefullyaltered,i.
e.
,bypassingPIDetectoranddirectlyinvokingmaliciouspayloads.
Thisstrategyisintheorypossiblebutrequirespreciseanalysisonapp'scodetoidentifythecriticalbranches,whichisquitechallengingandagainvulnerabletoobfuscationandpackingtechniques.
Thissettingisalsoadoptedbyallpreviousworksonevadingdynamicanalysis[21,28,14,17].
4.
ATTACKVECTORSInthissection,weelaborateseveralattackvectorsthatcanbeleveragedtodetectprogrammedinteractions.
Overall,thequaliedattackvectorsshouldfulllthethreerequirementsbelow:ReverseTuringTest–humanscanpass,butcurrentexplo-rationtoolscan'tpass.
Passive–hardtobediscoveredbyend-users.
Lightweight–easytobebuiltanddeployed.
Giventheseconstraints,wedesigntwoclassesofattackvectorstargetingthevulnerabilitiesunderlyingeventinjectionsandUIelementidenticationindynamicanalysis.
Tonotice,sometestingplatformsbuiltuponMonkeycanbetriviallyidentiedthroughinvokingtheisUserAMonkey()API[3]andinspectingthereturnedvalue.
Wedonotincludeitintotheattackvectorsasthere-turnedvaluecanbeeasilymanipulated(e.
g.
,itcanbebypassedbyUIAutomatorthroughcallingsetRunAsMonkey(false)[18]).
Weelaborateeachattackvectorinthefollowingsubsections.
4.
1DetectingSimulatedEventInjectionsWefoundthedataattachedtotwotypesofuserevents,Mo-tionEvent[6]fortouchscreentappingandKeyEvent[4]forkeypressing,canbeleveragedfordetection.
Itturnsoutthebothindividualeventandeventsequencerevealdistinguishablepatterns.
4.
1.
1SingleEventWhenauseroperatesamobiledevice,theeventsareinitiatedbytheonboardhardwareandtheinformationregardingthehardwareisattached.
Totheopposite,theeventsinjectedbydynamictestingtools,likeMonkey,arepassedfromexternalinterfacesandmostoftheparametersarelledwithdummyvalues.
Specically,whilethecoreparameters(e.
g.
,coordinatesofinputlocation)arelledwithrealvalues,theauxiliaryparameters(e.
g.
,keyboardtype)arenotlledsimilarly.
Table1andTable2listdifferencesbetweenthevaluesgeneratedfromreal-worldusageandMonkeytestingforMotionEventandKeyEvent.
Clearly,Monkeyllsthevaluesinadistinctivepatternthatcanbeidentied.
Forexample,theToolTypeparameterofKeyEventgeneratedbyMonkeyisalwaysTOOL_TYPE_UNKNOWN,whichcannotbeusedifthiseventisproducedbyhardware.
4.
1.
2EventSequenceToreachthehighcoverageofappbehaviorsinlimitedtime,dynamicanalyzerstendtoinjecteventsathighfrequencywhichTable1:MotionEvent:realvs.
simulated(byMonkey)ParameterRealSimulatedToolType1:TOOL_TYPE_FINGER0:TOOL_TYPE_UNKNOWNDeviceId[non-zerovalue]0DevicevalidnullRemarks:1)DeviceId:zeroindicatesthattheeventdoesnotcomefromaphysicaldeviceandmapstothedefaultkeymap.
Table2:KeyEvent:realvs.
simulated(byMonkey)ParameterRealSimulatedScanCode[non-xedvalue]0DeviceId[non-xedvalue]-1Device.
Name[non-xedvalue]VirtualDevice.
Generation[non-xedvalue]2Device.
Descriptor[non-xedvalue]af4d26ea4cdc857cc0f1ed1ed51996db77be1e4dDevice.
KeyboardType1:non-alphabetic2:alphabeticDevice.
Source[non-xedvalue]0x301:keyboarddpadRemarks:1)ScanCode:thehardwarekeyidofthekeyevent;2)Generation:thenumberisincrementedwheneverthedeviceisreconguredandthereforenotconstant;3)Descriptor:theuniqueidentierfortheinputdevice;4)KeyboadType:thevalueis"non-alphabetic"asthenowadayssmartphonemodelsdonotintegratehardwarekeyboards.
cannotbeperformedbyhumanusers.
Therefore,bymeasuringthefrequencyoftheeventsthedynamicanalyzerscouldbeidentied.
Also,thedistributionofeventsalongtimeseriesisalsouniquefordynamicanalyzers,andweshowhowthisobservationcouldbeleveragedforourpurposes.
Besides,thekeypressesareusuallyissuedatchangingspeedwhenausertypestextinEditTextwhiletheintervalisxedfordynamicanalyzers.
IMEpartiallycausesthis:anIMEwillshowupwhenausertapsEditTextandduetothevarianceofthedistancesbetweencharactersonIME,theintervalbetweenkeypressesuctuates.
FromtheaspectofMotionEventseries,Androidprovidesstan-dardAPIsforanapptorecognizetouchgesturesinputtedbyuser.
Atthesametime,aseriesofscreentouchingevents(MotionEvent)canbeobserved,andtheeventsareissuedmuchmoreregulariffromdynamicanalyzers.
Asanexample,weaskedaparticipanttoswipethetouchscreenonSamsungGalaxySIIIfromfarlefttofarrightanddirectedMonkeyRunnerforthesameaction.
Thetestwasran10timesandwedrawthetaplocationsinx-axis(floatxeldofMotionEvent)against20samplepointsatthesameintervalinFigure1.
Thetrajectoriesoftheswipesfromtheuserareratherdispersed,anddisplacementsatthestartandendoftheactionaresmaller.
Incontrast,Monkey'sswipesarehighlysimilarandaremovedatconstantspeed.
Suchdifferencecouldbemodeledthroughtimeseriessimilaritymeasurerelatedalgorithms.
4.
2ImplantingUITrapsToincreasethechanceoftriggeringmaliciousactivities,espe-ciallytheonesassociatedwithuserbehaviors,dynamicanalyzershavetoexploreandinteractwithasmanyUIelementsaspossible.
Suchdesign,however,leadstoadilemmathatcanbeexploited:theadversarycouldimplantUItrapsthatareinaccessibletohumanusersandunabletobedistinguishedbydynamicanalyzers.
Belowweelaboratethedesignsoftwosuchattackvectors:4.
2.
1IsolatedActivityAnAndroidappdenestheUIinterfaceandroutinesforeventprocessinginActivitycomponent,whichisalsodeclaredintheFigure1:Swipingtrajectory:realuservs.
explorationtoolFigure2:ExampleofisolatedActivityManifestle.
AnappusuallycontainsonemainActivityandsubsequentActivitiesthatcanbetransitionedto,asshowninFigure2.
Inaddition,developerscouldexportanActivitythatcanbelaunchedbyotherapps(Activity4inFigure2),throughsettingandroid:exported="true".
Commondynamican-alyzerstendtoparsetheManifestleandvisitActivitiesinbothcaseswhiletheusersfollowthedenedinteractionlogictovisitActivities.
ThismotivatesustocreateanisolatedActivitywhichcouldnotbereachedthroughinteractionasatrap:ifanunusedandexportedActivityisinvoked,thepartybehindshouldbedynamicanalyzer.
Suchtrapishardtobedetectedahead,astheinteractionlogicisdenedinapp'scodeandcanbeobfuscated.
4.
2.
2InvisibleUIElementsWedemonstrateanotherattackvectorherewhichmanipulatesthevisualeffectsofUIelements.
AhumanusernormallytapstheUIelementsshecanseetoinputinformation.
Ontheotherhand,dynamicanalyzerscouldinvokesystemAPIs(suchasparseViewHierarchyunderDeviceBridgeclass)toiden-tifyvalidelementsandsimulatetheinteraction.
Therefore,wecouldleaveavalidbut"invisible"controlinActivityasatrap,anduseittodetectthedynamicanalyzerfallingin.
Infact,AndroidUIlibraryprovidesasetofhighlycustomiz-ableUIcontrolsfordevelopers,includingButton,TextView,Switch,etc.
andtheycanbeeasilyconguredtobeinvisible.
OnesuchcontrolisImageButtonthatdisplaysimageasabuttonandacceptsclicks.
Iftheimageislledwiththesamecolorasthenearbypixelsofbackground,itwouldnotbediscoveredbythehumanuser.
Moreover,wecouldchangethelayoutandlocationofthecontrolsforthesamepurpose.
Forinstances,wecouldsetthecontroltobetiny(e.
g.
,1pixel)orfalloutofthescreen.
Figure3explainsthisidea.
Fromhuman'sview,onlyabutton(Test)andasentence(HelloWorld)canbeidentied.
Actually,5UIcontrolsareembeddedinthelayout:textview,imagebutton,switch,imagebutton,andbutton.
Theyareallvalidtodynamicanalyzers.
Forexample,weranGoogleUIAutomatortoparsetheUIlayoutanditrecognizesallcontrolsandextractstheinformationlistedbelow:(a)Reallaylout(b)Human'sviewFigure3:InvisibleUIelements:reallayoutvs.
human'sview(0)FrameLayout[0,0][720,1280](0)View[0,50][720,146](1)TextView:HelloWorld[32,178][178,216](2)ImageButton[176,178][178,180](3)Switch:ON[408,124][614,180](4)ImageButton[32,318][132,418](5)Button:Test[560,318][688,414]Allthesecontrolswillbeexercisedbydynamicanalyzers,butonlyandcouldbenoticedbyhuman.
Therefore,eventsredonothercontrolscouldindicatetheexistenceofdynamicanalyzers.
Toescapefromthistypeoftraps,dynamicanalyzershavetoaccuratelydeterminethevisibilityofUIcontrols(tohumaneyes),whichremainsanopenproblem.
5.
EVALUATIONInthissection,wepresenttheexperimentalresultsontheeffec-tivenessofPIDetector.
Thetestingmethodologyisintroducedrst,andtheresultsarediscussedafter.
TestingMethodology.
WedevelopedatestingappintegratingPIDetectorasaninternalcomponent.
OurgoalistoexaminewhetherPIDetectorcancorrectlydetectdynamicanalyzersthroughoneormoreattackvectors.
Therefore,thetestingapponlyhasbasicUIandfunctionalities,andwedidnotincludemaliciouspayloadintothetestingapptoreducetheimpacttotheoperationalizedplatforms.
Whentheappisloaded,PIDetectorstartstocollectrawlogsregardingredevents(detailsareprovidedbelow).
TherawlogsweresenttoanHTTPserversetuponAmazonElasticBeanstalk[1]andanalyzedthroughthemodelsimplementedbyus.
Wedecidetoexltratetheeventdatatogainabetterunderstandingofthebehaviorsoftestingplatforms.
Allanalysiscanbedonelocallywhenadoptedbyadversary'srealapp.
RawLogs.
Thecollectedrawlogsincludethefollowinginforma-tion:theparametersofcapturedMotionEventandKeyEventobjects,invokedActivities,visitedUIelements.
EveryreturnedlogispaddedwithauniqueIDtodistinguishdifferenttestingplatformsandtimesofrunning.
Onlytherst100logsaretransmittedtotheservertoobtainenoughdataandavoidexcessivenetworkconnec-tions,whichmightbeconsideredasanomalyactivitiesbytestingplatforms.
Wealsocollectedthecongurationinformationofeverytestedservice,suchasAndroidID,IMEI,Build.
SERIALandBuild.
MANUFACTURER,toseeifcountermeasuresagainstanti-emulationaredeployed.
TestingPlatforms.
Wetested10dynamicanalysisservicesbuiltformalwareanalysis,amongwhichfourcomefromtheacademiawhiletheotherscomefromthesecuritycompanies.
Inaddition,weuploadourtestingapptoGooglePlaytotestitsofcialdynamicanalyzer,GoogleBouncer.
These11servicesarelistedinTable3.
TheexperimentswereconductedinJanuaryandMarch2016.
Wewereabletoobtainvalidrawlogsfrom7services,andthenalresultsaresummarizedinTable3.
Amongtheremainingones,A5andCopperDroidrefusedtoanalyzeourapp,sincetheprocessingqueuehasbeenfullyoccupied.
NorawlogsorinformativemessagesarereturnedforPayloadSecurityandMalwr,andwespeculatethecausesare:1)theyonlylaunchstaticanalysisonourapp;2)Theoutboundnetworkconnectionsfromappareblocked.
Finding1.
Nearlyall(available)analysisservicesarevulnerabletoatleastoneattackvector.
Mostofthemcouldbeidentiedbyanalyzingsingleeventparameter,exceptTraceDroidforlackingenoughparametersandGoogleBouncerforllingvalidvalues.
Forexample,theInputDeviceparameteroftheKeyEventfromSandDroidwasalways"-1".
IsolatedActivityfeatureisalsoquiteeffective,andhalfoftheseonlineservicesfellintothistrap.
Ontheotherhand,onlyTecentHabohitinvisibleelements,andnoservicewasfoundtogeneratecontinuouseventsequence(e.
g.
,swipe).
WesuspectthattheseinteractionsaremissedbecausecomplexUIanalysisandinteractionsarenotperformed.
Finding2.
Emulatorcamouagingorphysicaldevicehasbeendeployedbyonlineanalysissystems.
Forexample,wefoundtheplatformcongurationofGoogleBouncerisquitelikephysicaldevice–GoogleNexus5or6,asshowingbelow:Version:6.
0.
1SDK_INT:23MODEL:Nexus6BRAND:googleBOARD:shamuDEVICE:shamuHARDWARE:shamuSERIAL:ZX1G22HMB3ID:MMB29KPRODUCT:shamuDISPLAY:MMB29KMANUFACTURER:motorolaHOST:wped2.
hot.
corp.
google.
comBOOTLOADER:moto-apq8084-71.
15FINGERPRINT:google/shamu/shamu:6.
0.
1/MMB29K/2419427:user/release-keysTonotice,emulatorcamouagehasbeenusedforotherpurposesonAndroidplatform.
BlueStacks[2],apopularemulatordesignedforrunningAndroidgamesonWindowsandMacplatforms,camouagesitselfascertainmodelsofSamsungdevicestoevadeemulatordetectionperformedbyapps.
Hence,webelieveourtechniquesforprogrammedinteractiondetectionismeaningfulevenintheshorttermtoattackers.
6.
DISCUSSIONLimitations.
Ascountermeasures,thedevelopersofdynamicanalyzerscouldchangetheUIinteractionpatternandmakethetestingprocessclosertohumanbeings.
Forexample,thedummyparametervaluesoftheinjectedMotionEventandKeyEventcouldbechangedtouserealdata.
Ontheotherhand,howtohideagainstthemorecomplicatedattackvectorswedevised(e.
g.
,eventsequence)isunclear.
Thoughuser'sinteractionsonAppUIcanberecordedandreplayed,challengeshavetobeaddressedonhowtoautomaticallyadjusttherecordedactionstodifferentapps.
7.
CONCLUSIONInthiswork,weproposeanewapproachtoevadeAndroidruntimeanalysis.
Thisapproachfocusesondetectingprogrammedinteractionstodeterminewhetheranappisunderanalysis,insteadofrelyingonthetraditionalemulatordetection.
Thepreliminaryexperimentalresultshavedemonstratedtheeffectivenessofourmethods.
Webelievetheevasivetechniquesleveragingsubtletiesofhuman-computerinteractionshouldbeseriouslyconsideredbyTable3:ExperimentalresultsforonlinedynamicanalysisservicesServiceNameURLSimulatedEventsUITrapsMotionEventParamtersKeyEventParametersEventSequenceIsolatedActivityInvisibleUIElementsNVISOApkScanhttps://apkscan.
nviso.
be√√SandDroidhttp://sanddroid.
xjtu.
edu.
cn√√√TraceDroid[27]http://tracedroid.
few.
vu.
nl**√Anubis[15]http://anubis.
iseclab.
org*√√TecentHabohttps://habo.
qq.
com/√√√VisualThreathttps://www.
visualthreat.
com√√GoogleBouncerN/A–nopubliclinkA5[29]http://dogo.
ece.
cmu.
edu/a5/Theuploadprocessalwaysreportederror.
CopperDroid[26]http://copperdroid.
isg.
rhul.
ac.
ukToomanysubmittedsampleswerequeued.
Malwrhttps://malwr.
comNorawlogwasreturned.
PayloadSecurityhttps://www.
hybrid-analysis.
comNorawlogwasreturned.
Remarks:1)"√":Judgedasprogrammedinteraction.
2)"*":Judgedashumaninteraction.
3)"":Nottriggeredorfound.
4)"":GoogleBouncerclickedallbuttonsonthemainActivitybutignoredtheimagebuttonwhichwascamouagedasanormalbuttonbyus.
WespeculateBounceronlytriggerstheUIcontrolswiththeButtonpropertybydesign.
Sincethisisindirectevidence,sowelabelitas"".
securitycommunityandcallforfurtherresearchonclosingthegapbetweenmachineandhumaninruntimebehaviors.
8.
ACKNOWLEDGEMENTSWethankanonymousreviewersfortheirinsightfulcomments.
ThisworkwaspartiallysupportedbyNSFC(GrantNo.
61572415),aswellastheDirectGrant(ProjectNo.
CUHK4055047)andEarlyCareerScheme(ProjectNo.
24207815)establishedundertheUni-versityGrantCommitteeoftheHongKongSpecialAdministrativeRegion,China.
9.
REFERENCES[1]AWSElasticBeanstalk.
http://aws.
amazon.
com/elasticbeanstalk/.
[2]BlueStacks.
http://www.
bluestacks.
com/.
[3]isUserAMonkey().
http://developer.
android.
com/reference/android/app/ActivityManager.
html#isUserAMonkey().
[4]KeyEvent.
http://developer.
android.
com/reference/android/view/KeyEvent.
html.
[5]MonkeyRunner.
http://developer.
android.
com/tools/help/monkeyrunner_concepts.
html.
[6]MotionEvent.
https://developer.
android.
com/reference/android/view/MotionEvent.
html.
[7]TestingSupportLibrary.
https://developer.
android.
com/tools/testing-support-library/index.
html.
[8]UI/ApplicationExerciserMonkey.
http://developer.
android.
com/tools/help/monkey.
html.
[9]GDATAMobileMalwareReport-ThreatReport:Q4/2015.
https://secure.
gd/dl-us-mmwr201504,2016.
[10]P.
Carter,C.
Mulliner,M.
Lindorfer,W.
Robertson,andE.
Kirda.
CuriousDroid:AutomatedUserInterfaceInteractionforAndroidApplicationAnalysisSandboxes.
InFinancialCryptographyandDataSecurity-20thInternationalConference,FC2016,RevisedSelectedPapers,2016.
[11]C.
Dietzel.
PortingandImprovinganAndroidSandboxforAutomatedAssessmentofMalware.
Master'sthesis,HochschuleDarmstadt,2014.
[12]J.
Gajrani,J.
Sarswat,M.
Tripathi,V.
Laxmi,M.
S.
Gaur,andM.
Conti.
ARobustDynamicAnalysisSystemPreventingSandBoxDetectionbyAndroid.
InProceedingsofthe8thInternationalConferenceonSecurityofInformationandNetworks(SIN),2015.
[13]W.
HuandZ.
Xiao.
GuessWhereIam:DetectionandPreventionofEmulatorEvadingonAndroid.
XFocusInformationSecurityConference(XCon),2014.
[14]Y.
Jing,Z.
Zhao,G.
Ahn,andH.
Hu.
Morpheus:AutomaticallyGeneratingHeuristicstoDetectAndroidEmulators.
InProceedingsofthe30thAnnualComputerSecurityApplicationsConference(ACSAC),2014.
[15]M.
Lindorfer,M.
Neugschwandtner,L.
Weichselbaum,Y.
Fratantonio,V.
vanderVeen,andC.
Platzer.
ANDRUBIS-1,000,000AppsLater:AViewonCurrentAndroidMalwareBehaviors.
InProceedingsofthe3rdInternationalWorkshoponBuildingAnalysisDatasetsandGatheringExperienceReturnsforSecurity(BADGERS),2014.
[16]H.
Lockheimer.
AndroidandSecurity.
http://googlemobile.
blogspot.
com/2012/02/android-and-security.
html,2012.
[17]D.
Maier,M.
Protsenko,andT.
Müller.
AGameofDroidandMouse:TheThreatofSplit-PersonalityMalwareonAndroid.
Computers&Security,54:2–15,2015.
[18]A.
Momtaz.
Allowforsettingtesttypeasamonkey.
https://android.
googlesource.
com/platform/frameworks/base/+/8f6f1f4%5E!
/,2013.
[19]S.
Mutti,Y.
Fratantonio,A.
Bianchi,L.
Invernizzi,J.
Corbetta,D.
Kirat,C.
Kruegel,andG.
Vigna.
Baredroid:Large-scaleAnalysisofAndroidAppsonRealDevices.
InProceedingsofthe31stAnnualComputerSecurityApplicationsConference(ACSAC),2015.
[20]S.
Neuner,V.
vanderVeen,M.
Lindorfer,M.
Huber,G.
Merzdovnik,M.
Mulazzani,andE.
R.
Weippl.
EnterSandbox:AndroidSandboxComparison.
InProceedingsofthe2014IEEEMobileSecurityTechnologiesWorkshop(MoST),2014.
[21]T.
Petsas,G.
Voyatzis,E.
Athanasopoulos,M.
Polychronakis,andS.
Ioannidis.
RageAgainsttheVirtualMachine:HinderingDynamicAnalysisofAndroidMalware.
InProceedingsoftheSeventhEuropeanWorkshoponSystemSecurity(EuroSec),2014.
[22]V.
Rastogi,Y.
Chen,andW.
Enck.
AppsPlayground:AutomaticSecurityAnalysisofSmartphoneApplications.
InProceedingsoftheThirdACMConferenceonDataandApplicationSecurityandPrivacy(CODASPY),2013.
[23]V.
Rastogi,Y.
Chen,andX.
Jiang.
CatchMeIfYouCan:EvaluatingAndroidAnti-MalwareAgainstTransformationAttacks.
IEEETransactionsonInformationForensicsandSecurity(TIFS),9(1):99–108,2014.
[24]M.
Spreitzenbarth,F.
C.
Freiling,F.
Echtler,T.
Schreck,andJ.
Hoffmann.
Mobile-Sandbox:HavingaDeeperLookintoAndroidApplications.
InProceedingsofthe28thAnnualACMSymposiumonAppliedComputing(SAC),2013.
[25]A.
Takanen,J.
DeMott,andC.
Miller.
FuzzingOverview.
InFuzzingforSoftwareSecurityTestingandQualityAssurance.
ArtechHouse,2008.
[26]K.
Tam,S.
J.
Khan,A.
Fattori,andL.
Cavallaro.
CopperDroid:AutomaticReconstructionofAndroidMalwareBehaviors.
InProceedingsofthe22ndAnnualNetworkandDistributedSystemSecuritySymposium(NDSS),2015.
[27]V.
vanderVeen.
DynamicAnalysisofAndroidMalware.
Master'sthesis,VUUniversityAmsterdam,2013.
[28]T.
VidasandN.
Christin.
EvadingAndroidRuntimeAnalysisviaSandboxDetection.
InProceedingsofthe9thACMSymposiumonInformation,ComputerandCommunicationsSecurity(ASIACCS),2014.
[29]T.
Vidas,J.
Tan,J.
Nahata,C.
L.
Tan,N.
Christin,andP.
Tague.
A5:AutomatedAnalysisofAdversarialAndroidApplications.
InProceedingsofthe4thACMWorkshoponSecurityandPrivacyinSmartphones&MobileDevices(SPSM),2014.
[30]L.
vonAhn,M.
Blum,N.
J.
Hopper,andJ.
Langford.
CAPTCHA:UsingHardAIProblemsforSecurity.
InAdvancesinCryptology-EUROCRYPT2003,InternationalConferenceontheTheoryandApplicationsofCryptographicTechniques,Proceedings,2003.
[31]L.
YanandH.
Yin.
DroidScope:SeamlesslyReconstructingtheOSandDalvikSemanticViewsforDynamicAndroidMalwareAnalysis.
InProceedingsofthe21stUSENIXSecuritySymposium,2012.
[32]Y.
Zhang,M.
Yang,B.
Xu,Z.
Yang,G.
Gu,P.
Ning,X.
S.
Wang,andB.
Zang.
VettingUndesirableBehaviorsinAndroidAppswithPermissionUseAnalysis.
InProceedingsofthe2013ACMSIGSACConferenceonComputerandCommunicationsSecurity(CCS),2013.
[33]C.
Zheng,S.
Zhu,S.
Dai,G.
Gu,X.
Gong,X.
Han,andW.
Zou.
SmartDroid:anAutomaticSystemforRevealingUI-basedTriggerConditionsinAndroidApplications.
InProceedingsofthe2012ACMWorkshoponSecurityandPrivacyinSmartphonesandMobileDevices(SPSM),2012.
- reducebluestacks相关文档
- 设置bluestacks
- ptsbluestacks
- 证券研究报告行业报告行业周报平安电子
- formatsbluestacks
- wrapbluestacks
- CES展示了不少最新平板電腦,如支援同時在屏幕
华纳云E5处理器16G内存100Mbps688元/月
近日华纳云商家正式上线了美国服务器产品,这次美国机房上线的产品包括美国云服务器、美国独立服务器、美国高防御服务器以及美国高防云服务器等产品,新产品上线华纳云推出了史上优惠力度最高的特价优惠活动,美国云服务器低至3折,1核心1G内存5Mbps带宽低至24元/月,20G ddos高防御服务器低至688元/月,年付周期再送2个月、两年送4个月、三年送6个月,终身续费同价,有需要的朋友可以关注一下。华纳云...
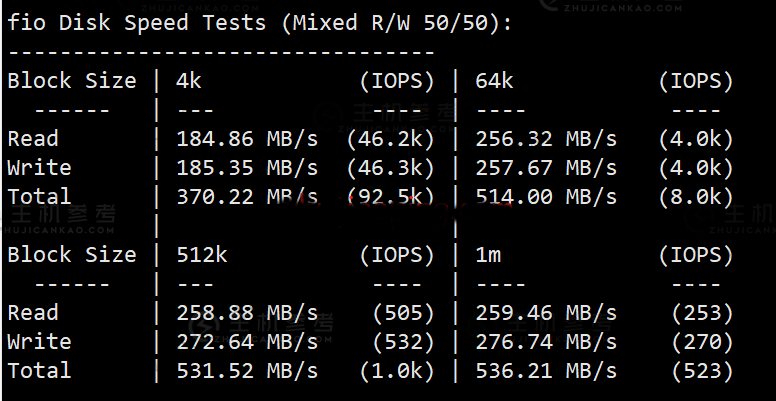
远程登录VNC无法连接出现
今天有网友提到自己在Linux服务器中安装VNC桌面的时候安装都没有问题,但是在登录远程的时候居然有出现灰色界面,有三行代码提示"Accept clipboard from viewers,Send clipboard to viewers,Send primary selection to viewers"。即便我们重新登录也不行,这个到底如何解决呢?这里找几个可以解决的可能办法,我们多多尝试。...
CloudCone中国新年特别套餐,洛杉矶1G内存VPS年付13.5美元起
CloudCone针对中国农历新年推出了几款特别套餐, 其中2019年前注册的用户可以以13.5美元/年的价格购买一款1G内存特价套餐,以及另外提供了两款不限制注册时间的用户可购买年付套餐。CloudCone是Quadcone旗下成立于2017年的子品牌,提供VPS及独立服务器租用,也是较早提供按小时计费VPS的商家之一,支持使用PayPal或者支付宝等付款方式。下面列出几款特别套餐配置信息。CP...
bluestacks为你推荐
-
weipin唯品单号为16060958116346的快递在哪了呢?人人时光机五月天的专辑都有哪些?bluestacksBlueStacks是什么?在PC上畅玩Android 45万款应用伪静态伪静态和真静态哪种静态方式好1433端口怎么去看1433端口百度手写百度如何手写:ps抠图技巧photoshop抠图技巧唱吧电脑版官方下载电脑上可以安装唱吧吗?安装迅雷看看播放器迅雷看看不能播放,说我尚未安装迅雷看看播放器机械键盘轴打游戏用机械键盘到底什么轴好?