用工Anti P2P terminator uses energy technology(反P2P终结者使用工能技巧)
Anti P2P terminator uses energy technology 反P2P终结者使
用工能技巧
Core tip: because the P2P terminator cracked version circulatedon the Internet, so many people can download malicious, andcontrol others in order to achieve the purpose of speed, theauthor has egoism, and departure from the original intention,so the launch of the anti terminator P2P software, the crackedversion of P2P terminator can't malicious control others, soas to protect the interests of morepeople. Related issues: antiP2P terminator download, how can not use the use of anti P2Pterminator, I will be affected by myself?
Because the P2P terminator cracked version circulated on theInternet, so many people can download malicious, and controlothers in order to achieve the purpose of speed, the author hasegoism, and departure from the original intention, so thelaunch of the anti terminator P2P software, the cracked versionof P2P terminator can' t malicious control others, so as toprotect the interests of more people.
Download control
1, P2P download full control function: full control, such asBT, eMule, Baidu, down, PP point, card Union, thunder and otherP2P tools download.
2, P2P download intelligent bandwidth suppression function:when you find a host for P2P download, automatically reduce theavailable bandwidth of the host.
3, HTTP download control function: users can set their owncontrol, any file download, you canalso specify the file suffixto restrict download.
4, FTP download function: users can set their own control, anyfile download, you can also specify the file suffix name.Two, bandwidth (flow speed) , flow management
1, view real-time bandwidth LAN hosts: from high to low rankingfunction makes the network management can take on the networkunderstand.
2, assign the public network bandwidth to a specific host: itcan make the limited public network bandwidth of the enterprisefully utilized, so that some hosts can not consume a lot ofbandwidth.
3, host datagram data analysis function: enables the networkmanagement to be able to know that the host occupies thebandwidth is uses in any application.
4, the system can set up uplink, downlink traffic and total flowfor the LAN host, exceed the set flow, automatically disconnectits public network connection.
Three, chat management
1, QQ chat control: the system can completely control thegeneral monitoring software can not control the chat tool.
2, MSN chat control; NetEase bubble chat control; Sina UC chatcontrol ; any other chat tools.
3, the system can record MSN and other chat content.
4, the system can be a variety of stock software, game softwarefor effective monitoring.
Four, monitoring through the web page to send WEB mail, post,message
The system can record and limit the content of WEB mails(including contents and attachments) , posting, message and soforth through HTTP.
Five, monitor the mail contents of Outlook, Foxmail and so onYou can record and limit the mail (including contents andattachments) received and sent by Outlook, Foxmail and othermail sending and receiving tools in detail. Netsense canaccording to the need to monitor the email, the email can notonly know the whereabouts and size, who can also intercepte-mail content, which can effectively prevent the theft ofconfidential business behavior by email.
Six, you can record and restrict files uploaded and downloadedvia FTP tools
File transfer mode (FTP) is one of the commonly used means ofinternal network to steal confidential, and now the Internetfaster, small to a few million, to tens of megabytes, hundreds
of megabytes of information can be uploaded out in a shortperiod of time, the enterprise information security is a hugethreat, we must carry out real-time monitoring. Netsense canautomatically monitor and record various behaviors of FTP, andit is very practical.
Seven, WWW access management
1, WWW access to full control : network management can chooseall prohibited Internet access, or the use of filtering rulesonline.
2, black and white list rules: network management can set theURL filtering rules, support black and white list custom.3, pornographic Web filtering: the system can automaticallyfilter in accordance with pornographic site library access.4, the LAN host acts as proxy server control: the system canautomatically restrict the LAN host to act as a proxy serverto prohibit improper LAN expansion.
5, LAN using WWW proxy control: prohibit LAN host using Socksand other agents to access WWW.
Eight, portal mailbox control
1, control LAN host can only access the Yahoo mailbox, but cannot click any other Yahoo links.
2, control LAN host can only access all kinds of sina mailbox,
but not click on any other Sina connection.
3, control LAN host can only access NetEase 163 of all kindsof mailbox, but can not click any other NetEase connection.4, control LAN host can only access all kinds of Sohu mailbox,but not click on any other Sohu connection.
5, control the mailbox of any website, but cannot click thewebsite any other connection.
Nine, group strategy (Internet access) management function1, you can set up a unified control strategy for all LAN hosts.2, according to the LAN host IP, to assign different strategies.3, the hosts within each control policy group can flexiblyswitch between different policies.
Ten, time management
Administrators can set the host' s control time (such as workingtime and non working time, custom time) , easy to manageflexibly.
Eleven, cross segment management
In the actual network applications, often encounter such asituation: a LAN exist at the same time with two or more thantwo segments (VLAN) , each segment between the physical Unicom,
but between cannot access, network administrator for eachsegment independently of the management work, repeated work,and added overhead. In view of this situation, netsense offersa"transparent cross network management" this function, to helpthe network administrator to cross network management.Twelve, custom ACL rules
The system provides custom control interface -ACL set up rulesfor network management personnel, through the rules of ACL, youcan set the IP source address, IP address, protocol, port number(TCP/UDP) range of parameters such as rules, the system willautomatically intercept data packets in accordance with therules, the use of ACL rules, you can control the function offlexible expansion the relaxed. Such as control LAN, any host,IP access to any public network IP, control any chat tools,control any network game. . . . . .
Thirteen 、 LAN security management
1, IP-MAC binding: system support for LAN host IP-MAC binding,once the discovery of illegal hosts, that is, you can isolatethe network.
2, through the use of sniffer host scanning system with "antiinterception technology" and the bottom of windows analysistechnology, can detect the most serious hazards of LAN threeattack tools: such as LAN terminator, network magistrates,network scissors in hand.
3, disconnect the host public network connection: the system
can disconnect the specified host of the public networkconnection.
Fourteen, network traffic statistics
Systemprovides a variety of detailed and illustrated host flow,flow statistics. Including:
1, daily traffic statistics function: the system provides thedesignated host or all hosts daily flow summary statisticsfunction.
2, monthly flow statistics function: the system provides thedesignated host or all host monthly traffic summary statisticsfunction.
3, daily flow statistics function: the system provides thespecified host, within specified time flow velocity chart.Fifteen detailed logging
1, the system records all the control information in detail,and the user can determine the network access of the managedhost by looking at the log file.
2, the system detailed records of the LAN host WWW access, website, users can query.
Sixteen, other functions
In addition to the above functions, the system provides many
very useful functions,
Such as sending messages to any host LAN LAN host; real-timeview of flow, and provides a visual display histogram; othernetsense recording LAN host, and the official version versionof the test can be forced to exit and so on.
[basic introduction]
Because the P2P terminator cracked version circulated on theInternet, so many people can download malicious, and controlothers in order to achieve the purpose of speed, the author hasegoism, and departure from the original intention, so thelaunch of the anti terminator P2P software, the cracked versionof P2P terminator can' t malicious control others, so as toprotect the interests of more people. For users who really needP2P terminator software for enterprise network management,please contact Beijing Yi Yi Technology to buy genuinesoftware!
[software function]
Download control
1, P2P download full control function: full control, such asBT, eMule, Baidu, down, PP point, card Union, thunder and otherP2P tools download.
2, P2P download intelligent bandwidth suppression function:when you find a host for P2P download, automatically reduce theavailable bandwidth of the host.
3, HTTP download control function: users can set their owncontrol, any file download, you canalso specify the file suffixto restrict download.
4, FTP download function: users can set their own control, anyfile download, you can also specify the file suffix name.
- 用工Anti P2P terminator uses energy technology(反P2P终结者使用工能技巧)相关文档
- 控制[专题]反P2P终结者使用工能技巧
- 主机反P2P终结者使用工能技巧
- 界面超强反P2P终结者利用360软件轻松搞定
- 主机反P2P终结者使用技巧
- 反p2p终结者反p2p终结者有用吗?
- 反p2p终结者什么是反P2P终结者?
georgedatacenter:美国VPS可选洛杉矶/芝加哥/纽约/达拉斯机房,$20/年;洛杉矶独立服务器39美元/月
georgedatacenter怎么样?georgedatacenter这次其实是两个促销,一是促销一款特价洛杉矶E3-1220 V5独服,性价比其实最高;另外还促销三款特价vps,大家可以根据自己的需要入手。georgedatacenter是一家成立于2019年的美国vps商家,主营美国洛杉矶、芝加哥、达拉斯、新泽西、西雅图机房的VPS、邮件服务器和托管独立服务器业务。georgedatacen...
Boomer.host:$4.95/年-512MB/5GB/500GB/德克萨斯州(休斯顿)
部落曾经在去年分享过一次Boomer.host的信息,商家自述始于2018年,提供基于OpenVZ架构的VPS主机,配置不高价格较低。最近,主机商又在LET发了几款特价年付主机促销,最低每年仅4.95美元起,有独立IPv4+IPv6,开设在德克萨斯州休斯顿机房。下面列出几款VPS主机配置信息。CPU:1core内存:512MB硬盘:5G SSD流量:500GB/500Mbps架构:KVMIP/面板...
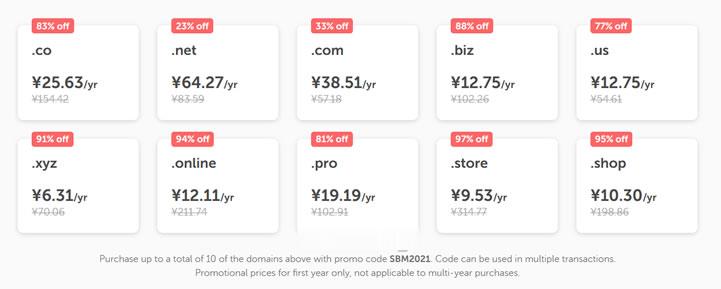
NameCheap优惠活动 新注册域名38元
今天上午有网友在群里聊到是不是有新注册域名的海外域名商家的优惠活动。如果我们并非一定要在国外注册域名的话,最近年中促销期间,国内的服务商优惠力度还是比较大的,以前我们可能较多选择海外域名商家注册域名在于海外商家便宜,如今这几年国内的商家价格也不贵的。比如在前一段时间有分享到几个商家的年中活动:1、DNSPOD域名欢购活动 - 提供域名抢购活动、DNS解析折扣、SSL证书活动2、难得再次关注新网商家...
-
交换机route股份一卡通系统支持ipad支付appleiexplore.exe应用程序错误iexplore.exe应用程序错误itunes备份itunes备份是什么127.0.0.1127.0.0.1打不开win7telnetWin7系统中的telnet命令如何应用?icloudiphone苹果手机显示"已停用,连接itunes"是什么意思迅雷快鸟迅雷快鸟支持移动宽带提速吗