Application-centric
rewrite规则 时间:2021-01-12 阅读:()
securitypoliciesonunmodiedAndroidNikhileshReddyJinseongJeonJeffreyA.
VaughanToddMillsteinJeffreyS.
FosterUniversityofCalifornia,LosAngelesUniversityofMaryland,CollegeParkTechnicalReport#110017UCLAComputerScienceDepartmentJuly5,2011AbstractGoogle'sAndroidplatformusesafairlystandardresource-centricpermissionmodeltoprotectresourcessuchasthecamera,GPS,andInternetconnection.
Weclaimthatamuchbet-terpermissionmodelfordevelopersanduserswouldbeapplication-centric,withavocabularythatdirectlyrelatestoapplication-levelfunctionality,e.
g.
,onepermissioncouldallowcamerause,butonlyforbarcodescanning;anothercouldallowInternetaccess,butonlytocertaindo-mains.
Despitethelargeapparentgapbetweenresource-andapplication-centricpermissions,wearguethatAndroidalreadyprovidesthenecessarymechanismstosupportanexpressiveandpracticalformofapplication-centricpolicies.
Specically,eachapplication-centricper-missioncanberepresentedbyanewAndroidpermissionandcanbeenforcedbycouplingthepermissionwithatrustedservicerunninginitsownprocess.
Wepresentasurveyofthetop24freeAndroidappsandshowthatasmallvocabularyofapplication-centricpermissionscoversmuchofthefunctionalityofthoseapps.
Wealsodescribeaprototypeimplementationofourapproach.
1OverviewGoogle'sAndroidisoneofthemostpopularsmartphoneplatforms,withmorethan100millionactivateddevices,morethan200,000applicationsintheAndroidMarket,andanestimated4.
5bil-lionappsinstalledfromtheMarket[8].
SecurityofAndroidapplications(henceforth"apps")isapressingconcern,asappscancollectsensitivedatafromtheuser(e.
g.
,usernamesandpasswords),accesspersonaldatastoredonthedevice(e.
g.
,calendarandcontactinformation),andusesensitivedevicecapabilities(e.
g.
,telephony,GPS,andcamera).
Androidtakesan"open-publish"approachtoappdistribution,inwhichanyappcanbeinstalledonanyphone.
Tohelpaddresssecurityconcerns,theAndroidplatformprotectsaccesstosensitiveresources—includingthecamera,networksockets,andGPSreceiver—withpermissions.
EachappincludesanXMLmanifestlethatliststhepermissionsrequestedbytheapp.
Whenanappisinstalled,thosepermissionsareshowntotheuser,whothendecideswhetherornottoproceedwiththeinstallation.
Noadditionalpermissionsmaybeacquiredwhenanappruns,andasecurityexceptionisraisedifanapptriestoaccessaresourcewithoutpermission.
Androidpermissionstoday.
WhilepermissionsonAndroidprovideanimportantlevelofsecurity,wehaveobservedthat,inpractice,thedesignofAndroid'spermissionsystemroutinelyforcesappstoacquiremorepowerfulpermissionsthanshouldbenecessary.
Forexample,anappthatscansaproduct'sbarcodeandthensearchesforitinapublicdatabasemusthave(atleast)theTakePicturesandFullInternetAccesspermissions.
Asaresult,appswiththisfeature(ofwhichthereareseveralintheAndroidMarket)couldpotentiallydomuchmorethanjustbarcodescanning.
Forexample,theycouldaccessthegeotagonabarcodeimagetondtheuser'slocation.
Moremaliciously,theymaybeabletocovertlycaptureimagesofauser'ssurroundingsandtransmitthemanywhereontheInternet.
Inourview,thebasicproblemwithAndroid'spermissionsystemisthatitisresource-centric:eachpermissiontypicallycontrolsaccesstoaparticularhardwareorsoftwareresource.
Thus,enforceablesecuritypoliciesonlysaywhatresourcesareaccessed,withlittleornoindicationof1howorwhytheyareused.
Thisleavesdevelopersontheirowntoensuretheyusetheresourcessafelyandonlytotheextentnecessary.
Worse,whenusersarepresentedwithalistofpermissionsanapprequests,theyarelefttoguessatwhethertheappusesthosepermissionssafely.
Application-centricpermissionsonunmodiedAndroid.
Therearetwomajorchallengesthatanysolutiontothisissuemustaddress:First,Androidisevolvingrapidly,withnewhardwareandsoftwarecapabilitiesemergingregularly,andthusanysolutionmustbeagileandadaptable.
Second,thepermissionsrequiredbyappsmustcaptureapplication-centricsecuritypropertiesthatareintuitivelyunderstandabletobothdevelopersandusers.
ItistemptingtotrytoaddressthisproblembyenrichingAndroid'spermissionsysteminvari-ousways.
Forexample,eachexistingpermissioncouldbeslicedintosmallerpermissionsgrantingrightstocorrespondinglynerunitsofresourceaccess.
Asanotherexample,anapplication'smanifestcoulduseanauthorizationlanguage(e.
g.
,DCCorKeyNote)toestablishconstraintsonresourceaccess.
Aprogramanalysisortypesystem(e.
g.
,JIF)couldalsobeusedtotrackhowin-formationowsthroughanapp.
However,webelievesuchapproachesrequiremakingimportantarchitecturalcommitmentsup-front,andtheymaybedifculttoevolveonsucharapidlychangingplatform.
Furthermore,itisimperativethatthepolicylanguagebekeptsimplefordevelopersandusersalike.
Perhapssurprisingly,webelievethatAndroidalreadycontainsthekeyingredientsneededforapowerfulandpracticalsolutiontotheabovechallenges:interprocesscommunication,processiso-lation,anduser-denedpermissions.
Interprocesscommunicationenablesanapplicationtoaccessrichfunctionalityprovidedbytrustedthirdparties.
Processisolationensuresthatapplicationsonlyaccessthatfunctionalitythroughawell-denedinterface,therebyallowingthirdpartiestoenforcearbitrarilyexpressiveapplication-centricsecuritypolicies.
Finally,user-denedpermissionsallowthesepoliciestobeassociatedwithsimpleAndroidpermissionsthatapplicationsmustacquiretoaccessthedesiredfunctionality.
Consideragaintheproblemofsupportingsafebarcodescanning.
Anidealsecuritypolicywouldspecifythatthecameramayonlybeusedtoscanabarcode,andtheresultingimagesarethrownawayafterprocessing.
WeproposetorepresentthispolicyasanewAndroidpermission,ScanBarcodes,thatgrantsaccesstoatrustedlibrarythatobeysthepolicy.
Todoso,thelibrarycouldhaveasinglefunctionthatdisplaysthecurrentcameraimage,waitsforauserclick,andthenscanstheresultingimageforabarcode,andreturnsthebarcode'snumericalvaluetothecallingapp.
Furthermore,wecanimplementthelibraryasanAndroidservicethatrunsinaseparateprocess.
Therefore,whilethelibrarymustbegrantedfullcameraaccess,anappthatcallsintothelibraryneedonlybegrantedScanBarcodesaccess,therebyprovidingastrongandunderstandableguaranteetoboththeappdeveloperandusers.
Althoughatrstglanceitseemswemayneedmanysuchapplication-centricpermissions,ourhypothesisisthatinpracticeareasonablysmallsetcandramaticallyimprovethesecurityofawidevarietyofapplications.
Moreover,weenvisionanecosysteminwhichmanydifferentvendorspro-videservicesassociatedwithcommonlydesiredapplication-centricpermissions.
Theseserviceswillbefarsimplerthanfullappsandhenceshouldbeeasytoauditforsecurity,andtheyareat-tractivecomponentsforopen-sourcingsincetheylikelywillnotcontainproprietaryfeaturesofanapp.
Finally,bymodularizingeachapplication-centricpermissioninitsownabstractionboundary,2wedecreasethepotentialforharmduetopolicyviolationsintheselibraries.
Forexample,ourprice-checkingapplicationwouldnaturallyuseoneservicetoprovidethebarcodescanningandaseparateservicetoprovideaccesstoabarcodedatabaseontheInternet,therebygreatlyreducingthepotentialforvulnerabilitiescausedbytheinteractionofcameraandInternetpermissions.
Toexploretheseideas,wehaveundertakenseveralpreliminarytasks.
WeperformedasurveyofpopularAndroidappstoidentifytheirapplication-centricpolicies(Section2).
WeimplementedourproposedapproachasanAndroidlibraryACPlib,whichcomprisesthreeapplication-centricpermissionsandtheassociatedservices.
Finally,wedevelopedRedexer,aDalvikbytecoderewrit-ingframeworkthatretrotsdownloadedappstouseapplication-centricpolicies.
WedescribeourpreliminaryexperienceusingACPlibandRedexertoenhancethesecurityofexistingandnewapps(Section3).
2FeasibilitystudyWeperformedapreliminarystudytoevaluatetheextenttowhichapplication-centricpermissionscanbesharedacrossavarietyofappstoenforcestrongersecuritypolicies.
MethodologyOurfeasibilitystudyconsideredthetop24freeappsonGoogle'sAndroidMar-ket1asofApril13,2011.
TheseappswereselectedbecausetheMarketwebsitedisplaysthemprominentlytousers;theyarewidelyinstalled(asreportedontheirMarkethomepages);andtheyrepresentaspectrumofapplicationdomains.
Theevaluationconsistedofinstallingandrunningeachapptounderstanditsfunctionality,readingEnglish-languageprivacypoliciesorotherdocumentationwhenavailable,and,sometimes,crudeanalysisofbinaries(usingtheUnixstringscommand).
InthecaseofWhatsApp,onlylimitedfunctionalitywastestedduetorestrictionsonappregistration.
Foreachapp,weevaluatedhowitusesitscurrentpermissionsetandidentiedapplication-centricpermissionsthatcouldreplacesomeofthesepermissions.
ResultsTheresultsofourstudyaresummarizedinFigure1.
Thetopleft-handcolumnofthetableshowsaselectionofAndroidpermissionsrequestedbyapps,andthebottomleft-handcolumnshowsapplication-centricpermissionsweidentiedaspotentialreplacements.
ThesepermissionsaredescribedbeneaththetableandrangefromcapturingspecicInternetusestorestrictinguseoflocationdata.
Wediscussseveralofourapplication-centricpermissionsindetail.
Internetpermissions.
Fourofthe11permissionspertaintotheInternet.
ThepermissionInter-netURL(domain)allowsnetworkconnectionsonlytodomainanditssubdomains.
Thisisusefulforthecommoncaseinwhichanappcommunicateswithonlyahandfulofknownwebservices,e.
g.
,Google'sSkyMapcanuseInternetURL(google.
com)inlieuofarbitraryInternetaccess.
1https://market.
android.
com/.
TheappssurveyedareAlchemy1.
10.
2,GoogleMaps5.
4.
0,Dropbox1.
1.
1,GasBuddy-FindCheapGas1.
14,StreetViewonGoogleMaps1.
6.
0.
6,AngryBirds1.
5.
3,BubbleBlast!
1.
0.
16,Shazam2.
5.
3-BB70302,ASTROFileManager2.
5.
2,PandoraRadio1.
5.
5,AdvancedTaskKiller1.
9.
6B76,BarcodeScanner3.
53,VaultyFreeHidesPictures2.
4.
1,FacebookforAndroid1.
5.
4,FreeMusicDownloader1.
8.
3LiveHoldemPokerPro3.
01,AngryBirdsRio1.
0.
0,Horoscope1.
5.
2,KakaoTalk2.
0.
1,FlashPlayer10.
2.
156.
12,BubbleBlast2ver.
1.
0.
18,GoogleSkyMap1.
6.
1,andWhatsAppMessenger2.
6.
2642.
3AlchemyAngryBirdsA.
BirdsRioASTROBarcodeBubbleBlastBub.
Blast2DropboxFacebookFlashplayerFreeMusicGasBuddyHoroscopeKakaoTalkLiveHoldemMapsPandoraShazamSkyMapStreetViewTaskKillerVaultyWhatsAppYouTubeFullInternetAccessStoragecontentsLocationne/coarseModifyglobalsettingsReadphonestate/idTakephotos/videosAdsPrivateAdsGeo++AnonUsageInternetURL(developer)InternetURL(other)LocationBlock+LocationVisibleMobileBilling+ScanBarcodes+SDCardOwnFiles++++SDCardShared+++ToggleGPS+++AdsPrivate:Maydisplaysads,butwithoutshar-ingpersonalinformationwithadvertisers.
AdsGeo:Maydisplaysadsandmayshareyourlocation,butnootherpersonalinformation,withadvertisers.
AnonUsage:Mayreportanonymoususagein-formationtoitsdevelopers,includingarandomnumberidentifyingyourcopyoftheapp,butnotyouoryourphone.
InternetURL(x):Mayaccesstheinternetserviceslocatedatdomainx.
LocationBlock:Mayaccessapproximatelocation,accurateto150m(aboutonecityblock).
LocationVisible:Mayacquireaccuratelocation,butonlywhentheapp'sinterfaceisshowing.
MobileBilling:Maybillyouviayourcarrier,afterrequestingpermissionwithaprompt.
ScanBarcodes:Mayusethecameratoreadbar-codesandQRcodes.
ToggleGPS:MayenableordisabletheGPSre-ceiver.
SDCardOwnFiles:MaymanagelesonitsownareaoftheSDcard;cannotread,edit,ordeleteotherles.
SDCardShared:Maymanageles,suchasmusicorphotos,thataresharedbyseveralapps;cannotread,edit,ordeletethatbelongtootherapps.
Figure1:App-centricpermissionsfortop24apps.
Notationindicatesabuilt-inAndroidpermissionthatcanbereplacedbyoneormoreapplication-centripermissions.
+indicatesapplication-centricpoliciestobeaddedandindicatespoliciesthatcannotobviouslyberemoved.
SomeAndroidpermissions,suchasthoserelatedtoaccountmanagmentareoutsidethescopeofthispaper,andnotshown.
4TheInternetURLpermissionistoocoarse-grainedtouseforin-appadvertising,sinceboththeadvertiserandtheappdeveloperhaveincentivestoextensivelyshareuserdata,violatingreasonableprivacyexpectations.
Yettotallyforbiddingcommunicationwithadvertisersisalsoundesirable,asadrevenueencouragesdeveloperstoreleasefreeapps.
ThepermissionsAdsPrivateandAdsGeomanagethistensionbyallowingadvertisingwhilerestrictingowsofprivatedata.
AsimilarAnonUsagepermissionisintendedforthecollectionofgeneral,anonymousanalyticsviaservicessuchasFlurry.
2.
(Analternativedesigncouldparametrizethepermissionbyadnetwork.
)Theapplication-centricInternetpermissionsaboveimposestrongrestrictionsonInternetac-cesswhilestillallowingmostdesiredfunctionality.
Ofthe23appsthatoriginallyrequiredFullinternetaccess,22canberewrittentouseonlyapplication-centricInternetpermissions.
There-mainingapp,Freemusic,downloadsmedialesfromdiversedomainsandlegitimatelyneedsfullInternetaccess.
Storagepermissions.
Android'sdefaulthandlingofexternalstorage,suchasSDcards,allowsanyapptomodifydatastoredbyanyotherapp.
Thispolicyisoverlybroadformanyapps,suchasFreemusic,thatshouldonlyaccessdeliberatelymodifymedialibraries,andforothers,suchasHoroscope,thatdonotappeartolegitimatelyneedmodifytosharedlesatall.
Indeed,webelievetherestrictiveSDCardOwnFilesandSDCardSharedpoliciescanreplaceAndroid'sbuilt-instoragepermissionforsixofthetenappsthatrequireit.
GPSpermissions.
WefoundthatfourofthesevenappsthatrequesttheModifyglobalset-tingspermissionseemtouseitsolelytotoggletheGPSunitonoroff,tosavepower(asdistinctfromtherighttoaccessGPSlocationdata,protectedbyadifferentpermission).
TheseappscanbegrantedthemorerestrictiveToggleGPSpermissioninstead.
PermissionsLocationBlockandLocationVisiblerestrictaccesstoGPSlocationdataintwodifferentways,andthesepermissionsappearsufcienttoreplaceAndroid'sGPSpermissioninsevenoutofeightapps.
AssuggestedbyLocationBlock,webelievethedistinctionofGPSvs.
networklocationislessinterestingthanthedistinctionbetweenhighest-precession-possiblevs.
intentionally-degradedlocation.
Overall,oftherequestedAndroidpermissionswestudied,71%arereplaceablewithapplication-specicpermissionsthataremuchmorerestrictive,andyetshouldnotadverselyaffectfunction-ality.
ThepermissionsInternetURL,AdsPrivate,andAnonUsageareapplicabletoatleast1/3ofsurveyedapps,andInternetURLitselfisapplicableto2/3.
Finally,8ofthe11permissionsareapplicabletoatleast10%ofthesurveyedapps.
Thisstudythereforeprovidespreliminaryevi-dencethatformanyAndroidapps,asmallnumberofapplication-centricpermissionscanprovidesignicantlystrongersecurityguaranteeswithoutlossoffunctionality.
Implementingapplication-centricpermissionsThe11application-centricpermissionsweiden-tiedareintendedtobeenforceablebyinterposingastrongAPI,implementedviaaservice,be-tweenunderlyingresourcesandclientsapps.
Togiveaavorofhowthatmightwork,wesketchhowtwoofthepermissionscouldbeenforcedbyatrustedservice.
Forpurposesofexpositionweelidesomedetails,notablyAndroid'seventdrivenprogrammingmodelandpervasiveuseofobjects.
(TheprototypedescribedinSection3doesfollowAndroid'sprogrammingmodel.
)First,considertheInternetURL(domain)permission,whichallowsanapptoconnectto(sub-2http://www.
flurry.
com5domainsof)domain.
Thisfunctionalitycanbeimplementedbyaservicewiththefollowinginter-face:Connectionopen(stringurl);byte[]read(Connectionc);voidwrite(Connectionc,byte[]data);voidclose(Connectionc);InAndroid,globalstateisusedtotrackasecuritycontext,andopen(x)checksthecurrentcontextforapermissionoftheformInternetURL(y),wherexisasubdomainofy.
Ifsuchapermissionexists,openconnectstoasocketandreturnsavalidConnectionobject.
Otherwise,openraisesasecurityexception.
Whilethissecurekernelprovidesfewoperations,wrapperscanextendittoaricherinterface.
AlthoughAndroiddoesnotdirectlysupportparameterizedpermissionssuchasInternetURL,thesecanbeencodedusingpermissiontrees.
Apermissiontreeisafamilyofpermissionswhosenamesshareacommonprex.
ForinstanceInternetURL(google.
com)canbegivenfullnameac-plib.
perm.
URL.
googlecomwhichispartoftheacplib.
perm.
URLtree.
Servicesmustbeinstructedtopreregistertreeelementsbeforeclientinstallation,butthisdoesnotappeartobeafundamentallimitationoftheplatform.
Second,considertheAdsPrivatepermission.
Atrustedlibrarycanmediatebetweenappsandwell-knownadservicesusinganinterfacesuchas:enumAdService{ADMOB,JUMPTAPConnectionopen(AdServicea);byte[]newAd(Connectionc);voidclose(Connectionc);Thisinterfaceallowsadstobedisplayed(vianewAd),butpreventstheappfrompassinganyinformationtoanadvertiser.
Theservicecouldalsomitigatecoverttimingchannelsusingacom-binationofprefetchinganddelayingadrequests.
Onewrinkleisthatonlineadvertisingrequiresthatappsidentifythemselvesusingauniqueidsothattherightdevelopercanbepaidforclicks.
Theservicecanusetheglobalcontexttoidentifycallingapps,alongwithawell-knownmapfromappstoidsthatisconsultedthersttimeanapprequestsanadconnection.
Finally,whileitwouldbeappeardifculttoimplementandmaintainasinglemulti-advertiserabstractionlayer,companiessuchasAdWhirl3dothisalready,albeitwithoutoursecurityfocus.
3ACPlibandRedexerTogainpreliminaryexperiencewithsomeofthepermissionsdiscussedinSection2,weimple-mentedaprototypeapplication-centricpermissionsystemforAndroid.
Oursystemcomprisestwomaincomponents:ACPlib,whichprovidesanimplementationofapplication-centricpermissionsandtheirassociatedservices,andRedexer,aDalvik-to-Dalvikrewritingsystemthatcanmodifyapps,evenwithouthavingtheirsourcecode,touseACPlib.
3https://www.
adwhirl.
com6ACPlibACPlibiscollectionofAndroidservices,eachimplementingoneofthefollowingpermis-sions:InternetUrl,LocationBlock,orScanBarcodes.
Theserviceslistenforrequestmessagesfromotherclientsappsandensureclientappshaveappropriateprivilegesbeforeservicingrequests.
AsdescribedinSection2,securitydictatesthatACPlibservicesruninseparateprocessesfromtheirclients,withcommunicationonlyviaAndroid'sRPCmechanism.
Usingthisdirectlyismorecomplexthansimplycallingprivilegedsystemroutines.
Toamelioratethis,ACPlibprovidesdrop-inAPIreplacementsforsystemlibrariesthathandlenecessaryRPCcalls,ACPlibinternally.
Forexample,insteadofcallingjava.
net.
URLConnection.
openConnection()toopenanInternetconnection,usersnowcallapclib.
net.
URLConnection.
openConnection().
AdditionallyappsmustbindtoACPlib,typicallydoneintheapp'sonCreate()method.
RedexerACPlibcanbeusedas-isbysecurity-consciousdeveloperstoreducetheprivilegeleveloftheirapps.
WealsoexpectthatappuserswillwishtoretrotexistingappstouseACPlib,e.
g.
,torestrictthewebsitesappscanvisitorcoarsenthelocationinformationrevealedtoapps.
Tothisend,wehavebegundevelopmentofRedexer,aDalvikbinaryrewritingframeworkthatmodiesapplicationbundlestoreplaceAndroidAPIcallswithACPlibequivalents.
RedexeralsoaddstheDalvikcodeforACPlib'sreplacementAPIstotheapplication.
OnesurprisingchallengeindevelopingRedexeristherulesthatAndroid'sverierenforcesbeforeitwillexecuteaDalvikbytecodele.
Inparticular,Dalviklescontainseveralindexed"identierlists"ofdatathatissharedacrossmethods,e.
g.
,strings,types,eldandmethodde-nitions,etc.
TheAndroidverierrequiresthatsuchpoolsarebothduplicate-freeandsortedinaparticularorder.
ThiscausessomecomplicationswhenaddingtheACPlibAPItotheapp'sDalvikle.
Forexample,theremustbeonlyonestring"V"representingthetypevoidinaDalvikle,anditisalmostguaranteedthistypewillappearinboththeapp'scodeandintheACPlibAPIcode;thusuponmerging,wemusteliminateonecopyandrewriteoneortheotherleaccordingly.
AnotherchallengeforRedexeristhatsomeappscallACPlibservicesfromonCreate(),but(duetoAndroid'sevent-drivensemantics)theconnectiontoACPlibcannotbeestablisheduntilafteronCreate()returns.
Thus,RedexersplitsonCreate()intotwomethods:Itheuristi-callykeepsallthecodeuptoandincludingthesetContentView()call(whichsetsuptheuserinterface)inonCreate(),andthenappendsacalltoperformthebinding.
WemovetheremainderofthecodeintoanewdroidLibOnCreate()methodthatisinvokedbyACPlibafterthebindingcompletes.
Weexpecttomakethismechanismmorerobustinthefuture.
PreliminaryExperienceWhileACPlibandRedexerarefarfromfullymature,wewereabletomodifythesourceoftwoexistingappstouseACPlibandtorewritetwoappsautomaticallyusingRedexer.
WealsobuiltanewappfromscratchusingACPlib.
GoogleTranslate4isaverypopularappthatrequestsfullInternetpermissions,butonlycontactsthegoogleapis.
comdomain.
WemanuallyeditedthesourcecodeoftheapptouseInter-netURL(gooleapis.
com)instead.
Wefoundthenecessarychangeseasytomake,andaftermakingthechanges,theappcontinuestoworkcorrectly.
Maurauder'sMapisaroute-planningappwewrotepriortoACPlib.
WemanuallyupdateditssourcetouseLocationBlock,allowinguserstondreasonablerouteswithoutrevealingtheirexact4http://code.
google.
com/p/apps-for-android/7location.
Asbeforethechangeswereeasytomakeandtheappcontinuestoworkwell.
SlashdotRSSReader5isanappthatcontactstheslashdot.
orgdomaintoretrieveanRSSfeed,articles,andcomments.
WeusedRedexertorewritetheapptouseInternetURL(slashdot.
org).
ThedomainwasfoundautomaticallyusingRedexertosearchforURLsinthebinary.
WeimplementedaPriceCheckerappfromscratchthatusesScanBarcodestoscanbarcodesandInternetURL(searchupc.
com)tolookupthepriceforthescanneditem.
ThiswaseasytowriteusingACPlib'sbarcodescanninglibrary.
4RelatedWorkOthershavealsorecognizedthelimitationsofAndroid'sresource-centricpermissionmodel.
Bar-reraetal.
[1]andFeltetal[7]analyzethewaypermissionsareusedinAndroidandChromeOSapps.
BothgroupsobservethatonlyasmallnumberofAndroidpermissionsarewidelyusedbutthatsomeofthese,inparticularInternetpermissions,areoverlybroad.
SomeresearchershavedevelopedtoolsthathavefoundavarietyofsecurityissuesinAndroidapps[4,5].
Whileourap-proachcannotguaranteetheabsenceofthesecurityvulnerabilitiesfoundbysuchtools,webelieveitcanhelpmakeappsmoresecureinpractice.
WebelieveAPClibiscomplimentarytosuchtoolsastheyaddressdifferentsortsofsecurityproperties.
Furthermore,trustedlibrarieslikeACPlibareprimecandidatesforautomatedvalidation,asreuseallowsvericationcoststobeamortizedandhighsecurityrequirementscanjustifyremainingper-appcosts.
OthershavealsoproposedenhancedpermissionmechanismsforAndroid.
MockDroidchangesAndroidOSsothatuserscan"mock"asubsetofanapplication'sresource-centricpermissions,causingaccessestothoseresourcestosilentlyfail[2].
Apexissimilarandalsoletstheuserenforcesimpleconstraintssuchasthenumberoftimesperdayaresourcemaybeaccessed[9].
Kirinemploysasetofuser-denedsecurityrulestoagpotentialmalwareatinstalltime[6].
Thesetoolsallowuserstotradeoffappfunctionalityforprivacy,buttheyinherittheresource-centricnatureofAndroidpermissions,whichcanlimittheireffectiveness.
Forexample,denyingInternetaccesstoGoogleTranslatewouldrenderituseless,soaMockDroidusermustallowsuchaccess,whereasourapplication-centricpolicyprovidesamuchstrongerguarantee.
Moreover,ourapproachcanbeimplementedpurelyasalibrary,withnomodicationstotheunderlyingAndroidOS.
SaintenrichespermissionsonAndroidtosupportavarietyofinstallationconstraints,e.
g.
,apermissioncanincludeawhitelistofappsthatmayrequestit[10].
Inourlimitedexperience,wehavenotyetneededthiscapability.
ComDroid[3]analyzesinter-applicationcommunicationforpotentialsecurityrisks.
Thistoolcouldcomplementourproposedapproach,whichreliesheavilyoninter-applicationcommunicationwithtrustedthirdparties.
5http://code.
google.
com/p/slashdot/85ConclusionandFutureWorkWeintroducedtheideaofapplication-centricpermissionsandarguedthattheyareanexpressiveandpracticalapproachtoincreasethesecurityofAndroidappstoday.
Webelievethesameideacanalsobeappliedtootherpermissionsystems.
Inthefuture,weplantodevelopawidervocabularyofapplication-centricpermissions;implementmorepermissionsinACPlib;andimproveRedexersothatwecanautomaticallyrewritemoreapps.
Wealsohopetoconductastudytodeterminehowdevelopersanduserswouldunderstandanduseapplication-centricpermissions.
References[1]D.
Barrera,H.
Kayacik,P.
vanOorschot,andA.
Somayaji.
Amethodologyforempiricalanalysisofpermission-basedsecuritymodelsanditsapplicationtoandroid.
InCCS,pages73–84,2010.
[2]A.
R.
Beresford,A.
Rice,N.
Skehin,andR.
Sohan.
Mockdroid:tradingprivacyforapplicationfunctionalityonsmartphones.
InHotMobile,2011.
[3]E.
Chin,A.
P.
Felt,K.
Greenwood,andD.
Wagner.
AnalyzingInter-ApplicationCommunicationinAndroid.
InMobiSys,2011.
Toappear.
[4]W.
Enck,P.
Gilbert,B.
-G.
Chun,L.
P.
Cox,J.
Jung,P.
McDaniel,andA.
N.
Sheth.
Taintdroid:aninformation-owtrackingsystemforrealtimeprivacymonitoringonsmartphones.
InOSDI,2010.
[5]W.
Enck,D.
Octeau,P.
McDaniel,andS.
Chaudhuri.
Astudyofandroidapplicationsecurity.
InUSENIXSecurity,2011.
[6]W.
Enck,M.
Ongtang,andP.
McDaniel.
Onlightweightmobilephoneapplicationcertication.
InCCS,pages235–245,2009.
[7]A.
P.
Felt,K.
Greenwood,andD.
Wagner.
TheEffectivenessofApplicationPermissions.
InWebApps,2011.
Toappear.
[8]Google.
Android:momentum,mobileandmoreatGoogleI/O,May2011.
http://googleblog.
blogspot.
com/2011/05/android-momentum-mobile-and-more-at.
html.
[9]M.
Nauman,S.
Khan,andX.
Zhang.
Apex:extendingandroidpermissionmodelandenforcementwithuser-denedruntimeconstraints.
InASIACCS,pages328–332,2010.
[10]M.
Ongtang,S.
McLaughlin,W.
Enck,andP.
McDaniel.
Semanticallyrichapplication-centricsecurityinandroid.
InACSAC,pages340–349,2009.
VaughanToddMillsteinJeffreyS.
FosterUniversityofCalifornia,LosAngelesUniversityofMaryland,CollegeParkTechnicalReport#110017UCLAComputerScienceDepartmentJuly5,2011AbstractGoogle'sAndroidplatformusesafairlystandardresource-centricpermissionmodeltoprotectresourcessuchasthecamera,GPS,andInternetconnection.
Weclaimthatamuchbet-terpermissionmodelfordevelopersanduserswouldbeapplication-centric,withavocabularythatdirectlyrelatestoapplication-levelfunctionality,e.
g.
,onepermissioncouldallowcamerause,butonlyforbarcodescanning;anothercouldallowInternetaccess,butonlytocertaindo-mains.
Despitethelargeapparentgapbetweenresource-andapplication-centricpermissions,wearguethatAndroidalreadyprovidesthenecessarymechanismstosupportanexpressiveandpracticalformofapplication-centricpolicies.
Specically,eachapplication-centricper-missioncanberepresentedbyanewAndroidpermissionandcanbeenforcedbycouplingthepermissionwithatrustedservicerunninginitsownprocess.
Wepresentasurveyofthetop24freeAndroidappsandshowthatasmallvocabularyofapplication-centricpermissionscoversmuchofthefunctionalityofthoseapps.
Wealsodescribeaprototypeimplementationofourapproach.
1OverviewGoogle'sAndroidisoneofthemostpopularsmartphoneplatforms,withmorethan100millionactivateddevices,morethan200,000applicationsintheAndroidMarket,andanestimated4.
5bil-lionappsinstalledfromtheMarket[8].
SecurityofAndroidapplications(henceforth"apps")isapressingconcern,asappscancollectsensitivedatafromtheuser(e.
g.
,usernamesandpasswords),accesspersonaldatastoredonthedevice(e.
g.
,calendarandcontactinformation),andusesensitivedevicecapabilities(e.
g.
,telephony,GPS,andcamera).
Androidtakesan"open-publish"approachtoappdistribution,inwhichanyappcanbeinstalledonanyphone.
Tohelpaddresssecurityconcerns,theAndroidplatformprotectsaccesstosensitiveresources—includingthecamera,networksockets,andGPSreceiver—withpermissions.
EachappincludesanXMLmanifestlethatliststhepermissionsrequestedbytheapp.
Whenanappisinstalled,thosepermissionsareshowntotheuser,whothendecideswhetherornottoproceedwiththeinstallation.
Noadditionalpermissionsmaybeacquiredwhenanappruns,andasecurityexceptionisraisedifanapptriestoaccessaresourcewithoutpermission.
Androidpermissionstoday.
WhilepermissionsonAndroidprovideanimportantlevelofsecurity,wehaveobservedthat,inpractice,thedesignofAndroid'spermissionsystemroutinelyforcesappstoacquiremorepowerfulpermissionsthanshouldbenecessary.
Forexample,anappthatscansaproduct'sbarcodeandthensearchesforitinapublicdatabasemusthave(atleast)theTakePicturesandFullInternetAccesspermissions.
Asaresult,appswiththisfeature(ofwhichthereareseveralintheAndroidMarket)couldpotentiallydomuchmorethanjustbarcodescanning.
Forexample,theycouldaccessthegeotagonabarcodeimagetondtheuser'slocation.
Moremaliciously,theymaybeabletocovertlycaptureimagesofauser'ssurroundingsandtransmitthemanywhereontheInternet.
Inourview,thebasicproblemwithAndroid'spermissionsystemisthatitisresource-centric:eachpermissiontypicallycontrolsaccesstoaparticularhardwareorsoftwareresource.
Thus,enforceablesecuritypoliciesonlysaywhatresourcesareaccessed,withlittleornoindicationof1howorwhytheyareused.
Thisleavesdevelopersontheirowntoensuretheyusetheresourcessafelyandonlytotheextentnecessary.
Worse,whenusersarepresentedwithalistofpermissionsanapprequests,theyarelefttoguessatwhethertheappusesthosepermissionssafely.
Application-centricpermissionsonunmodiedAndroid.
Therearetwomajorchallengesthatanysolutiontothisissuemustaddress:First,Androidisevolvingrapidly,withnewhardwareandsoftwarecapabilitiesemergingregularly,andthusanysolutionmustbeagileandadaptable.
Second,thepermissionsrequiredbyappsmustcaptureapplication-centricsecuritypropertiesthatareintuitivelyunderstandabletobothdevelopersandusers.
ItistemptingtotrytoaddressthisproblembyenrichingAndroid'spermissionsysteminvari-ousways.
Forexample,eachexistingpermissioncouldbeslicedintosmallerpermissionsgrantingrightstocorrespondinglynerunitsofresourceaccess.
Asanotherexample,anapplication'smanifestcoulduseanauthorizationlanguage(e.
g.
,DCCorKeyNote)toestablishconstraintsonresourceaccess.
Aprogramanalysisortypesystem(e.
g.
,JIF)couldalsobeusedtotrackhowin-formationowsthroughanapp.
However,webelievesuchapproachesrequiremakingimportantarchitecturalcommitmentsup-front,andtheymaybedifculttoevolveonsucharapidlychangingplatform.
Furthermore,itisimperativethatthepolicylanguagebekeptsimplefordevelopersandusersalike.
Perhapssurprisingly,webelievethatAndroidalreadycontainsthekeyingredientsneededforapowerfulandpracticalsolutiontotheabovechallenges:interprocesscommunication,processiso-lation,anduser-denedpermissions.
Interprocesscommunicationenablesanapplicationtoaccessrichfunctionalityprovidedbytrustedthirdparties.
Processisolationensuresthatapplicationsonlyaccessthatfunctionalitythroughawell-denedinterface,therebyallowingthirdpartiestoenforcearbitrarilyexpressiveapplication-centricsecuritypolicies.
Finally,user-denedpermissionsallowthesepoliciestobeassociatedwithsimpleAndroidpermissionsthatapplicationsmustacquiretoaccessthedesiredfunctionality.
Consideragaintheproblemofsupportingsafebarcodescanning.
Anidealsecuritypolicywouldspecifythatthecameramayonlybeusedtoscanabarcode,andtheresultingimagesarethrownawayafterprocessing.
WeproposetorepresentthispolicyasanewAndroidpermission,ScanBarcodes,thatgrantsaccesstoatrustedlibrarythatobeysthepolicy.
Todoso,thelibrarycouldhaveasinglefunctionthatdisplaysthecurrentcameraimage,waitsforauserclick,andthenscanstheresultingimageforabarcode,andreturnsthebarcode'snumericalvaluetothecallingapp.
Furthermore,wecanimplementthelibraryasanAndroidservicethatrunsinaseparateprocess.
Therefore,whilethelibrarymustbegrantedfullcameraaccess,anappthatcallsintothelibraryneedonlybegrantedScanBarcodesaccess,therebyprovidingastrongandunderstandableguaranteetoboththeappdeveloperandusers.
Althoughatrstglanceitseemswemayneedmanysuchapplication-centricpermissions,ourhypothesisisthatinpracticeareasonablysmallsetcandramaticallyimprovethesecurityofawidevarietyofapplications.
Moreover,weenvisionanecosysteminwhichmanydifferentvendorspro-videservicesassociatedwithcommonlydesiredapplication-centricpermissions.
Theseserviceswillbefarsimplerthanfullappsandhenceshouldbeeasytoauditforsecurity,andtheyareat-tractivecomponentsforopen-sourcingsincetheylikelywillnotcontainproprietaryfeaturesofanapp.
Finally,bymodularizingeachapplication-centricpermissioninitsownabstractionboundary,2wedecreasethepotentialforharmduetopolicyviolationsintheselibraries.
Forexample,ourprice-checkingapplicationwouldnaturallyuseoneservicetoprovidethebarcodescanningandaseparateservicetoprovideaccesstoabarcodedatabaseontheInternet,therebygreatlyreducingthepotentialforvulnerabilitiescausedbytheinteractionofcameraandInternetpermissions.
Toexploretheseideas,wehaveundertakenseveralpreliminarytasks.
WeperformedasurveyofpopularAndroidappstoidentifytheirapplication-centricpolicies(Section2).
WeimplementedourproposedapproachasanAndroidlibraryACPlib,whichcomprisesthreeapplication-centricpermissionsandtheassociatedservices.
Finally,wedevelopedRedexer,aDalvikbytecoderewrit-ingframeworkthatretrotsdownloadedappstouseapplication-centricpolicies.
WedescribeourpreliminaryexperienceusingACPlibandRedexertoenhancethesecurityofexistingandnewapps(Section3).
2FeasibilitystudyWeperformedapreliminarystudytoevaluatetheextenttowhichapplication-centricpermissionscanbesharedacrossavarietyofappstoenforcestrongersecuritypolicies.
MethodologyOurfeasibilitystudyconsideredthetop24freeappsonGoogle'sAndroidMar-ket1asofApril13,2011.
TheseappswereselectedbecausetheMarketwebsitedisplaysthemprominentlytousers;theyarewidelyinstalled(asreportedontheirMarkethomepages);andtheyrepresentaspectrumofapplicationdomains.
Theevaluationconsistedofinstallingandrunningeachapptounderstanditsfunctionality,readingEnglish-languageprivacypoliciesorotherdocumentationwhenavailable,and,sometimes,crudeanalysisofbinaries(usingtheUnixstringscommand).
InthecaseofWhatsApp,onlylimitedfunctionalitywastestedduetorestrictionsonappregistration.
Foreachapp,weevaluatedhowitusesitscurrentpermissionsetandidentiedapplication-centricpermissionsthatcouldreplacesomeofthesepermissions.
ResultsTheresultsofourstudyaresummarizedinFigure1.
Thetopleft-handcolumnofthetableshowsaselectionofAndroidpermissionsrequestedbyapps,andthebottomleft-handcolumnshowsapplication-centricpermissionsweidentiedaspotentialreplacements.
ThesepermissionsaredescribedbeneaththetableandrangefromcapturingspecicInternetusestorestrictinguseoflocationdata.
Wediscussseveralofourapplication-centricpermissionsindetail.
Internetpermissions.
Fourofthe11permissionspertaintotheInternet.
ThepermissionInter-netURL(domain)allowsnetworkconnectionsonlytodomainanditssubdomains.
Thisisusefulforthecommoncaseinwhichanappcommunicateswithonlyahandfulofknownwebservices,e.
g.
,Google'sSkyMapcanuseInternetURL(google.
com)inlieuofarbitraryInternetaccess.
1https://market.
android.
com/.
TheappssurveyedareAlchemy1.
10.
2,GoogleMaps5.
4.
0,Dropbox1.
1.
1,GasBuddy-FindCheapGas1.
14,StreetViewonGoogleMaps1.
6.
0.
6,AngryBirds1.
5.
3,BubbleBlast!
1.
0.
16,Shazam2.
5.
3-BB70302,ASTROFileManager2.
5.
2,PandoraRadio1.
5.
5,AdvancedTaskKiller1.
9.
6B76,BarcodeScanner3.
53,VaultyFreeHidesPictures2.
4.
1,FacebookforAndroid1.
5.
4,FreeMusicDownloader1.
8.
3LiveHoldemPokerPro3.
01,AngryBirdsRio1.
0.
0,Horoscope1.
5.
2,KakaoTalk2.
0.
1,FlashPlayer10.
2.
156.
12,BubbleBlast2ver.
1.
0.
18,GoogleSkyMap1.
6.
1,andWhatsAppMessenger2.
6.
2642.
3AlchemyAngryBirdsA.
BirdsRioASTROBarcodeBubbleBlastBub.
Blast2DropboxFacebookFlashplayerFreeMusicGasBuddyHoroscopeKakaoTalkLiveHoldemMapsPandoraShazamSkyMapStreetViewTaskKillerVaultyWhatsAppYouTubeFullInternetAccessStoragecontentsLocationne/coarseModifyglobalsettingsReadphonestate/idTakephotos/videosAdsPrivateAdsGeo++AnonUsageInternetURL(developer)InternetURL(other)LocationBlock+LocationVisibleMobileBilling+ScanBarcodes+SDCardOwnFiles++++SDCardShared+++ToggleGPS+++AdsPrivate:Maydisplaysads,butwithoutshar-ingpersonalinformationwithadvertisers.
AdsGeo:Maydisplaysadsandmayshareyourlocation,butnootherpersonalinformation,withadvertisers.
AnonUsage:Mayreportanonymoususagein-formationtoitsdevelopers,includingarandomnumberidentifyingyourcopyoftheapp,butnotyouoryourphone.
InternetURL(x):Mayaccesstheinternetserviceslocatedatdomainx.
LocationBlock:Mayaccessapproximatelocation,accurateto150m(aboutonecityblock).
LocationVisible:Mayacquireaccuratelocation,butonlywhentheapp'sinterfaceisshowing.
MobileBilling:Maybillyouviayourcarrier,afterrequestingpermissionwithaprompt.
ScanBarcodes:Mayusethecameratoreadbar-codesandQRcodes.
ToggleGPS:MayenableordisabletheGPSre-ceiver.
SDCardOwnFiles:MaymanagelesonitsownareaoftheSDcard;cannotread,edit,ordeleteotherles.
SDCardShared:Maymanageles,suchasmusicorphotos,thataresharedbyseveralapps;cannotread,edit,ordeletethatbelongtootherapps.
Figure1:App-centricpermissionsfortop24apps.
Notationindicatesabuilt-inAndroidpermissionthatcanbereplacedbyoneormoreapplication-centripermissions.
+indicatesapplication-centricpoliciestobeaddedandindicatespoliciesthatcannotobviouslyberemoved.
SomeAndroidpermissions,suchasthoserelatedtoaccountmanagmentareoutsidethescopeofthispaper,andnotshown.
4TheInternetURLpermissionistoocoarse-grainedtouseforin-appadvertising,sinceboththeadvertiserandtheappdeveloperhaveincentivestoextensivelyshareuserdata,violatingreasonableprivacyexpectations.
Yettotallyforbiddingcommunicationwithadvertisersisalsoundesirable,asadrevenueencouragesdeveloperstoreleasefreeapps.
ThepermissionsAdsPrivateandAdsGeomanagethistensionbyallowingadvertisingwhilerestrictingowsofprivatedata.
AsimilarAnonUsagepermissionisintendedforthecollectionofgeneral,anonymousanalyticsviaservicessuchasFlurry.
2.
(Analternativedesigncouldparametrizethepermissionbyadnetwork.
)Theapplication-centricInternetpermissionsaboveimposestrongrestrictionsonInternetac-cesswhilestillallowingmostdesiredfunctionality.
Ofthe23appsthatoriginallyrequiredFullinternetaccess,22canberewrittentouseonlyapplication-centricInternetpermissions.
There-mainingapp,Freemusic,downloadsmedialesfromdiversedomainsandlegitimatelyneedsfullInternetaccess.
Storagepermissions.
Android'sdefaulthandlingofexternalstorage,suchasSDcards,allowsanyapptomodifydatastoredbyanyotherapp.
Thispolicyisoverlybroadformanyapps,suchasFreemusic,thatshouldonlyaccessdeliberatelymodifymedialibraries,andforothers,suchasHoroscope,thatdonotappeartolegitimatelyneedmodifytosharedlesatall.
Indeed,webelievetherestrictiveSDCardOwnFilesandSDCardSharedpoliciescanreplaceAndroid'sbuilt-instoragepermissionforsixofthetenappsthatrequireit.
GPSpermissions.
WefoundthatfourofthesevenappsthatrequesttheModifyglobalset-tingspermissionseemtouseitsolelytotoggletheGPSunitonoroff,tosavepower(asdistinctfromtherighttoaccessGPSlocationdata,protectedbyadifferentpermission).
TheseappscanbegrantedthemorerestrictiveToggleGPSpermissioninstead.
PermissionsLocationBlockandLocationVisiblerestrictaccesstoGPSlocationdataintwodifferentways,andthesepermissionsappearsufcienttoreplaceAndroid'sGPSpermissioninsevenoutofeightapps.
AssuggestedbyLocationBlock,webelievethedistinctionofGPSvs.
networklocationislessinterestingthanthedistinctionbetweenhighest-precession-possiblevs.
intentionally-degradedlocation.
Overall,oftherequestedAndroidpermissionswestudied,71%arereplaceablewithapplication-specicpermissionsthataremuchmorerestrictive,andyetshouldnotadverselyaffectfunction-ality.
ThepermissionsInternetURL,AdsPrivate,andAnonUsageareapplicabletoatleast1/3ofsurveyedapps,andInternetURLitselfisapplicableto2/3.
Finally,8ofthe11permissionsareapplicabletoatleast10%ofthesurveyedapps.
Thisstudythereforeprovidespreliminaryevi-dencethatformanyAndroidapps,asmallnumberofapplication-centricpermissionscanprovidesignicantlystrongersecurityguaranteeswithoutlossoffunctionality.
Implementingapplication-centricpermissionsThe11application-centricpermissionsweiden-tiedareintendedtobeenforceablebyinterposingastrongAPI,implementedviaaservice,be-tweenunderlyingresourcesandclientsapps.
Togiveaavorofhowthatmightwork,wesketchhowtwoofthepermissionscouldbeenforcedbyatrustedservice.
Forpurposesofexpositionweelidesomedetails,notablyAndroid'seventdrivenprogrammingmodelandpervasiveuseofobjects.
(TheprototypedescribedinSection3doesfollowAndroid'sprogrammingmodel.
)First,considertheInternetURL(domain)permission,whichallowsanapptoconnectto(sub-2http://www.
flurry.
com5domainsof)domain.
Thisfunctionalitycanbeimplementedbyaservicewiththefollowinginter-face:Connectionopen(stringurl);byte[]read(Connectionc);voidwrite(Connectionc,byte[]data);voidclose(Connectionc);InAndroid,globalstateisusedtotrackasecuritycontext,andopen(x)checksthecurrentcontextforapermissionoftheformInternetURL(y),wherexisasubdomainofy.
Ifsuchapermissionexists,openconnectstoasocketandreturnsavalidConnectionobject.
Otherwise,openraisesasecurityexception.
Whilethissecurekernelprovidesfewoperations,wrapperscanextendittoaricherinterface.
AlthoughAndroiddoesnotdirectlysupportparameterizedpermissionssuchasInternetURL,thesecanbeencodedusingpermissiontrees.
Apermissiontreeisafamilyofpermissionswhosenamesshareacommonprex.
ForinstanceInternetURL(google.
com)canbegivenfullnameac-plib.
perm.
URL.
googlecomwhichispartoftheacplib.
perm.
URLtree.
Servicesmustbeinstructedtopreregistertreeelementsbeforeclientinstallation,butthisdoesnotappeartobeafundamentallimitationoftheplatform.
Second,considertheAdsPrivatepermission.
Atrustedlibrarycanmediatebetweenappsandwell-knownadservicesusinganinterfacesuchas:enumAdService{ADMOB,JUMPTAPConnectionopen(AdServicea);byte[]newAd(Connectionc);voidclose(Connectionc);Thisinterfaceallowsadstobedisplayed(vianewAd),butpreventstheappfrompassinganyinformationtoanadvertiser.
Theservicecouldalsomitigatecoverttimingchannelsusingacom-binationofprefetchinganddelayingadrequests.
Onewrinkleisthatonlineadvertisingrequiresthatappsidentifythemselvesusingauniqueidsothattherightdevelopercanbepaidforclicks.
Theservicecanusetheglobalcontexttoidentifycallingapps,alongwithawell-knownmapfromappstoidsthatisconsultedthersttimeanapprequestsanadconnection.
Finally,whileitwouldbeappeardifculttoimplementandmaintainasinglemulti-advertiserabstractionlayer,companiessuchasAdWhirl3dothisalready,albeitwithoutoursecurityfocus.
3ACPlibandRedexerTogainpreliminaryexperiencewithsomeofthepermissionsdiscussedinSection2,weimple-mentedaprototypeapplication-centricpermissionsystemforAndroid.
Oursystemcomprisestwomaincomponents:ACPlib,whichprovidesanimplementationofapplication-centricpermissionsandtheirassociatedservices,andRedexer,aDalvik-to-Dalvikrewritingsystemthatcanmodifyapps,evenwithouthavingtheirsourcecode,touseACPlib.
3https://www.
adwhirl.
com6ACPlibACPlibiscollectionofAndroidservices,eachimplementingoneofthefollowingpermis-sions:InternetUrl,LocationBlock,orScanBarcodes.
Theserviceslistenforrequestmessagesfromotherclientsappsandensureclientappshaveappropriateprivilegesbeforeservicingrequests.
AsdescribedinSection2,securitydictatesthatACPlibservicesruninseparateprocessesfromtheirclients,withcommunicationonlyviaAndroid'sRPCmechanism.
Usingthisdirectlyismorecomplexthansimplycallingprivilegedsystemroutines.
Toamelioratethis,ACPlibprovidesdrop-inAPIreplacementsforsystemlibrariesthathandlenecessaryRPCcalls,ACPlibinternally.
Forexample,insteadofcallingjava.
net.
URLConnection.
openConnection()toopenanInternetconnection,usersnowcallapclib.
net.
URLConnection.
openConnection().
AdditionallyappsmustbindtoACPlib,typicallydoneintheapp'sonCreate()method.
RedexerACPlibcanbeusedas-isbysecurity-consciousdeveloperstoreducetheprivilegeleveloftheirapps.
WealsoexpectthatappuserswillwishtoretrotexistingappstouseACPlib,e.
g.
,torestrictthewebsitesappscanvisitorcoarsenthelocationinformationrevealedtoapps.
Tothisend,wehavebegundevelopmentofRedexer,aDalvikbinaryrewritingframeworkthatmodiesapplicationbundlestoreplaceAndroidAPIcallswithACPlibequivalents.
RedexeralsoaddstheDalvikcodeforACPlib'sreplacementAPIstotheapplication.
OnesurprisingchallengeindevelopingRedexeristherulesthatAndroid'sverierenforcesbeforeitwillexecuteaDalvikbytecodele.
Inparticular,Dalviklescontainseveralindexed"identierlists"ofdatathatissharedacrossmethods,e.
g.
,strings,types,eldandmethodde-nitions,etc.
TheAndroidverierrequiresthatsuchpoolsarebothduplicate-freeandsortedinaparticularorder.
ThiscausessomecomplicationswhenaddingtheACPlibAPItotheapp'sDalvikle.
Forexample,theremustbeonlyonestring"V"representingthetypevoidinaDalvikle,anditisalmostguaranteedthistypewillappearinboththeapp'scodeandintheACPlibAPIcode;thusuponmerging,wemusteliminateonecopyandrewriteoneortheotherleaccordingly.
AnotherchallengeforRedexeristhatsomeappscallACPlibservicesfromonCreate(),but(duetoAndroid'sevent-drivensemantics)theconnectiontoACPlibcannotbeestablisheduntilafteronCreate()returns.
Thus,RedexersplitsonCreate()intotwomethods:Itheuristi-callykeepsallthecodeuptoandincludingthesetContentView()call(whichsetsuptheuserinterface)inonCreate(),andthenappendsacalltoperformthebinding.
WemovetheremainderofthecodeintoanewdroidLibOnCreate()methodthatisinvokedbyACPlibafterthebindingcompletes.
Weexpecttomakethismechanismmorerobustinthefuture.
PreliminaryExperienceWhileACPlibandRedexerarefarfromfullymature,wewereabletomodifythesourceoftwoexistingappstouseACPlibandtorewritetwoappsautomaticallyusingRedexer.
WealsobuiltanewappfromscratchusingACPlib.
GoogleTranslate4isaverypopularappthatrequestsfullInternetpermissions,butonlycontactsthegoogleapis.
comdomain.
WemanuallyeditedthesourcecodeoftheapptouseInter-netURL(gooleapis.
com)instead.
Wefoundthenecessarychangeseasytomake,andaftermakingthechanges,theappcontinuestoworkcorrectly.
Maurauder'sMapisaroute-planningappwewrotepriortoACPlib.
WemanuallyupdateditssourcetouseLocationBlock,allowinguserstondreasonablerouteswithoutrevealingtheirexact4http://code.
google.
com/p/apps-for-android/7location.
Asbeforethechangeswereeasytomakeandtheappcontinuestoworkwell.
SlashdotRSSReader5isanappthatcontactstheslashdot.
orgdomaintoretrieveanRSSfeed,articles,andcomments.
WeusedRedexertorewritetheapptouseInternetURL(slashdot.
org).
ThedomainwasfoundautomaticallyusingRedexertosearchforURLsinthebinary.
WeimplementedaPriceCheckerappfromscratchthatusesScanBarcodestoscanbarcodesandInternetURL(searchupc.
com)tolookupthepriceforthescanneditem.
ThiswaseasytowriteusingACPlib'sbarcodescanninglibrary.
4RelatedWorkOthershavealsorecognizedthelimitationsofAndroid'sresource-centricpermissionmodel.
Bar-reraetal.
[1]andFeltetal[7]analyzethewaypermissionsareusedinAndroidandChromeOSapps.
BothgroupsobservethatonlyasmallnumberofAndroidpermissionsarewidelyusedbutthatsomeofthese,inparticularInternetpermissions,areoverlybroad.
SomeresearchershavedevelopedtoolsthathavefoundavarietyofsecurityissuesinAndroidapps[4,5].
Whileourap-proachcannotguaranteetheabsenceofthesecurityvulnerabilitiesfoundbysuchtools,webelieveitcanhelpmakeappsmoresecureinpractice.
WebelieveAPClibiscomplimentarytosuchtoolsastheyaddressdifferentsortsofsecurityproperties.
Furthermore,trustedlibrarieslikeACPlibareprimecandidatesforautomatedvalidation,asreuseallowsvericationcoststobeamortizedandhighsecurityrequirementscanjustifyremainingper-appcosts.
OthershavealsoproposedenhancedpermissionmechanismsforAndroid.
MockDroidchangesAndroidOSsothatuserscan"mock"asubsetofanapplication'sresource-centricpermissions,causingaccessestothoseresourcestosilentlyfail[2].
Apexissimilarandalsoletstheuserenforcesimpleconstraintssuchasthenumberoftimesperdayaresourcemaybeaccessed[9].
Kirinemploysasetofuser-denedsecurityrulestoagpotentialmalwareatinstalltime[6].
Thesetoolsallowuserstotradeoffappfunctionalityforprivacy,buttheyinherittheresource-centricnatureofAndroidpermissions,whichcanlimittheireffectiveness.
Forexample,denyingInternetaccesstoGoogleTranslatewouldrenderituseless,soaMockDroidusermustallowsuchaccess,whereasourapplication-centricpolicyprovidesamuchstrongerguarantee.
Moreover,ourapproachcanbeimplementedpurelyasalibrary,withnomodicationstotheunderlyingAndroidOS.
SaintenrichespermissionsonAndroidtosupportavarietyofinstallationconstraints,e.
g.
,apermissioncanincludeawhitelistofappsthatmayrequestit[10].
Inourlimitedexperience,wehavenotyetneededthiscapability.
ComDroid[3]analyzesinter-applicationcommunicationforpotentialsecurityrisks.
Thistoolcouldcomplementourproposedapproach,whichreliesheavilyoninter-applicationcommunicationwithtrustedthirdparties.
5http://code.
google.
com/p/slashdot/85ConclusionandFutureWorkWeintroducedtheideaofapplication-centricpermissionsandarguedthattheyareanexpressiveandpracticalapproachtoincreasethesecurityofAndroidappstoday.
Webelievethesameideacanalsobeappliedtootherpermissionsystems.
Inthefuture,weplantodevelopawidervocabularyofapplication-centricpermissions;implementmorepermissionsinACPlib;andimproveRedexersothatwecanautomaticallyrewritemoreapps.
Wealsohopetoconductastudytodeterminehowdevelopersanduserswouldunderstandanduseapplication-centricpermissions.
References[1]D.
Barrera,H.
Kayacik,P.
vanOorschot,andA.
Somayaji.
Amethodologyforempiricalanalysisofpermission-basedsecuritymodelsanditsapplicationtoandroid.
InCCS,pages73–84,2010.
[2]A.
R.
Beresford,A.
Rice,N.
Skehin,andR.
Sohan.
Mockdroid:tradingprivacyforapplicationfunctionalityonsmartphones.
InHotMobile,2011.
[3]E.
Chin,A.
P.
Felt,K.
Greenwood,andD.
Wagner.
AnalyzingInter-ApplicationCommunicationinAndroid.
InMobiSys,2011.
Toappear.
[4]W.
Enck,P.
Gilbert,B.
-G.
Chun,L.
P.
Cox,J.
Jung,P.
McDaniel,andA.
N.
Sheth.
Taintdroid:aninformation-owtrackingsystemforrealtimeprivacymonitoringonsmartphones.
InOSDI,2010.
[5]W.
Enck,D.
Octeau,P.
McDaniel,andS.
Chaudhuri.
Astudyofandroidapplicationsecurity.
InUSENIXSecurity,2011.
[6]W.
Enck,M.
Ongtang,andP.
McDaniel.
Onlightweightmobilephoneapplicationcertication.
InCCS,pages235–245,2009.
[7]A.
P.
Felt,K.
Greenwood,andD.
Wagner.
TheEffectivenessofApplicationPermissions.
InWebApps,2011.
Toappear.
[8]Google.
Android:momentum,mobileandmoreatGoogleI/O,May2011.
http://googleblog.
blogspot.
com/2011/05/android-momentum-mobile-and-more-at.
html.
[9]M.
Nauman,S.
Khan,andX.
Zhang.
Apex:extendingandroidpermissionmodelandenforcementwithuser-denedruntimeconstraints.
InASIACCS,pages328–332,2010.
[10]M.
Ongtang,S.
McLaughlin,W.
Enck,andP.
McDaniel.
Semanticallyrichapplication-centricsecurityinandroid.
InACSAC,pages340–349,2009.
- Application-centric相关文档
- differencedrewrite规则
- seinrewrite规则
- Akrewrite规则
- 银行rewrite规则
- Dueckrewrite规则
- Pizirewrite规则
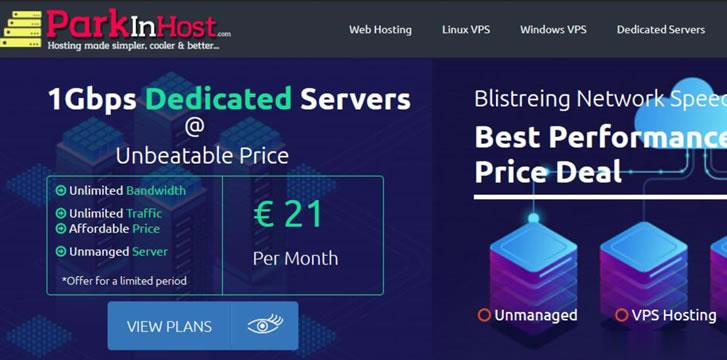
ParkInHost - 俄罗斯VPS主机 抗投诉 55折,月付2.75欧元起
ParkInHost主机商是首次介绍到的主机商,这个商家是2013年的印度主机商,隶属于印度DiggDigital公司,主营业务有俄罗斯、荷兰、德国等机房的抗投诉虚拟主机、VPS主机和独立服务器。也看到商家的数据中心还有中国香港和美国、法国等,不过香港机房肯定不是直连的。根据曾经对于抗投诉外贸主机的了解,虽然ParkInHost以无视DMCA的抗投诉VPS和抗投诉服务器,但是,我们还是要做好数据备...
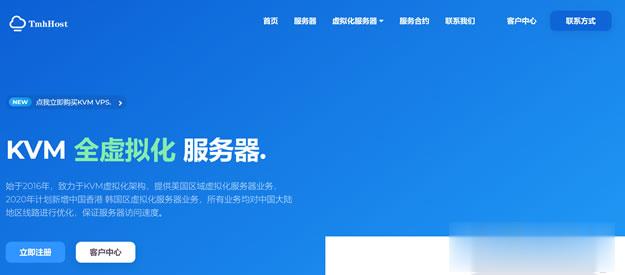
TmhHost 全场八折优惠且充值返10% 多款CN2线路
TmhHost 商家是一家成立于2019年的国人主机品牌。目前主营的是美国VPS以及美国、香港、韩国、菲律宾的独立服务器等,其中VPS业务涵盖香港CN2、香港NTT、美国CN2回程高防、美国CN2 GIA、日本软银、韩国cn2等,均为亚太中国直连优质线路,TmhHost提供全中文界面,支持支付宝付款。 TmhHost黑五优惠活动发布了,全场云服务器、独立服务器提供8折,另有充值返现、特价服务器促销...
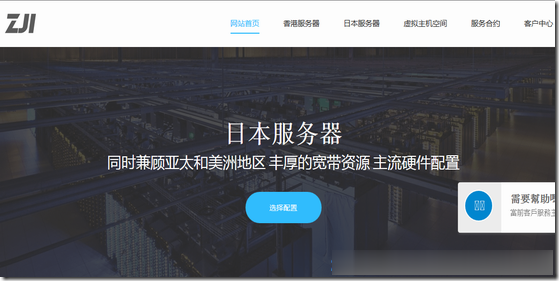
ZJI韩国BGP+CN2服务器,440元起
ZJI又上新了!商家是原Wordpress圈知名主机商:维翔主机,成立于2011年,2018年9月启用新域名ZJI,提供中国香港、台湾、日本、美国独立服务器(自营/数据中心直营)租用及VDS、虚拟主机空间、域名注册等业务。本次商家新上韩国BGP+CN2线路服务器,国内三网访问速度优秀,适用8折优惠码,优惠后韩国服务器最低每月440元起。韩国一型CPU:Intel 2×E5-2620 十二核二十四线...
rewrite规则为你推荐
-
国外虚拟空间哪里买的100m海外虚拟空间便宜稳定?域名服务域名服务器是什么?域名服务商请问那些域名服务商是怎么捣鼓这么多域名的? 它们为什么可以做这个国内ip代理找一个好用的国内电信IP代理?虚拟主机申请在哪里可以申请到虚拟主机呢重庆虚拟空间重庆合川宝龙城市广场有前途么虚拟主机控制面板如何利用虚拟主机控制面板对网站进行管理虚拟主机服务商现在市场上那家服务商的虚拟主机性价比最高?山东虚拟主机山东东营制作网站的公司在哪里?虚拟主机排名IDC全国十强是哪几个服务商