Win10盗版win8.1升级win10
盗版win8.1升级win10 时间:2021-01-20 阅读:()
1WindowsCredentialsAttackMitigationDefenseChadTilbury@chadtilburySeniorInstructorandCo-Author:FOR500:WindowsForensicsFOR508:AdvancedForensicsandIncidentResponseE-mail:chad.
tilbury@crowdstrike.
comLinkedIn:ChadTilburyTwitter:@chadtilburyComputerCrimeInvestigationsCrowdStrikeMandiantUSAirForceOSISpecialAgentCHADTILBURYTECHNICALADVISORCROWDSTRIKESERVICESSANSINSTITUTECONNECT15+YEARSPriority#1post-exploitationDomainadminisultimategoalNearlyeverythinginWindowsistiedtoanaccountDifficulttomovewithoutoneEasyandrelativelystealthymeanstotraversethenetworkAccountlimitationsarerare"Sleeper"credentialscanprovideaccessafterremediationCompromisingCredentials3PillageAchieveDomainAdminDumpMoarCredentials_MoveLaterallyDumpCredentialsGainFootholdUserAccessControl(UAC)ManagedServiceAccountsKB2871997SSPplaintextpasswordmitigationsLocaladminremotelogonrestrictionsProtectedProcessesRestrictedAdminDomainProtectedUsersSecurityGroupLSACachecleanupGroupManagedServiceAccountsCredentialGuardRemoteCredentialGuardDeviceGuard(preventexecutionofuntrustedcode)EvolutionofCredentialAttackMitigation4CompromisingCredentials:HashesThepasswordforeachuseraccountinWindowsisstoredinmultipleformats:LMandNThashesaremostwellknown.
TsPkg,WDigest,andLiveSSPcanbedecryptedtoprovideplaintextpasswords(priortoWin8.
1)HowaretheyacquiredandusedHashesareavailableintheLSASSprocessandcanbeextractedwithadminprivileges.
Oncedumped,hashescanbecrackedorusedimmediatelyinaPasstheHashattack.
Commontools:MimikatzfgdumpgsecdumpMetasploitSMBshellPWDumpXcreddumpWCEHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT5AdminActionLogonTypeCredentialsonTargetNotesConsolelogon2Yes**ExceptwhenCredentialGuardisenabledRunas2Yes**ExceptwhenCredentialGuardisenabledRemoteDesktop10Yes**ExceptforenabledRemoteCredentialGuardNetUse3NoIncluding/u:parameterPowerShellRemoting3NoInvoke-Command;Enter-PSSessionPsExecalternatecreds3+2Yes-u-pmicrosoft.
com/en-us/windows-server-docs/security/securing-privileged-access/securing-privileged-access-reference-materialHashDumping(Gsecdump)8PasstheHash(Mimikatz)10PreventadminaccountcompromiseStopremoteinteractivesessionswithhighlyprivilegedaccountsProperterminationofRDPsessionsWin8.
1+forcetheuseofRestrictedAdminWin10deployRemoteCredentialGuardUpgradetoWindows10CredentialGuardTsPkg,WDigest,etc.
--SSOcredsobsolescenceDomainProtectedUsersGroup(PtHmitigation)DefendingCredentials:Hashes12CompromisingCredentials:TokensDelegatetokensarepowerfulauthenticationresourcesusedforSSO.
Theyallowattackerstoimpersonateauser'ssecuritycontext,includingoverthenetwork.
HowaretheyacquiredandusedTheSeImpersonateprivilegeletstokensbecopiedfromprocesses.
Thenewtokencanthenbeusedtoauthenticateasthenewuser.
Atargetuserorservicemustbeloggedonorhaverunningprocesses.
Commontools:IncognitoMetasploitPowerShellMimikatzHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT13TokenStealing(Mimikatz)14PreventadminaccountcompromiseStopremoteinteractivesessionswithhighlyprivilegedaccountsProperterminationofRDPsessionsWin8.
1+forcetheuseofRestrictedAdminModeWin10deployRemoteCredentialGuardAccountdesignationof"AccountisSensitiveandCannotbeDelegated"inActiveDirectoryDomainProtectedUserssecuritygroupaccountsdonotcreatedelegatetokensDefendingCredentials:Tokens16CompromisingCredentials:CachedCredentialsStoreddomaincredentialstoallowlogonswhendomaincontrolleraccessisunavailable.
Mostsystemscachethelast10logonhashesbydefault.
HowaretheyacquiredandusedCachedcredentialsmustbecracked.
Hashesaresaltedandcase-sensitive,makingdecryptionveryslow.
ThesehashescannotbeusedforPasstheHashattacks.
Commontools:cachedumpMetasploitPWDumpXcreddumpHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT17Thecreddumputilitiescanextracthashes,cachedcredentialsandLSASecretsfromofflineregistryhives:github.
com/Neohapsis/creddump7OfflineCachedCredentialsExtraction(Creddump)18LocalNTHashesCachedHashesPreventadminaccountcompromiseLimitnumberofcachedlogonaccountsSOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon(cachedlogonscountvalue)AcachedlogonscountofzerooroneisnotalwaystherightanswerEnforcepasswordlengthandcomplexityrulesBruteforcecrackingisrequiredforthisattackDomainProtectedUserssecuritygroupaccountsdonotcachecredentialsDefendingCredentials:CachedCredentials20CompromisingCredentials:LSASecretsCredentialsstoredintheregistrytoallowservicesortaskstoberunwithuserprivileges.
Inadditiontoserviceaccounts,mayalsoholdapplicationpasswordslikeVPNorauto-logoncredentials.
HowaretheyacquiredandusedAdministratorprivilegesallowaccesstoencryptedregistrydataandthekeysnecessarytodecrypt.
PasswordsareplaintextCommontools:CainMetasploitMimikatzgsecdumpPWDumpXcreddumpPowerShellHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT21Get-LsaSecret.
ps1fromtheNishangPowerShellpentestframeworkusedtodump(anddecrypt)LSASecretshttps://github.
com/samratashok/nishangDecryptingLSASecrets(Nishang)22PreventadminaccountcompromiseDonotemployservicesorscheduletasksrequiringprivilegedaccountsonlowtrustsystemsReducenumberofservicesthatrequiredomainaccountstoexecuteHeavilyauditanyaccountsthatmustbeused(Group)ManagedServiceAccountsDefendingCredentials:LSASecrets23CompromisingCredentials:TicketsKerberosissuesticketstoauthenticatedusersthatcanbereusedwithoutadditionalauthentication.
Ticketsarecachedinmemoryandarevalidfor10hours.
HowaretheyacquiredandusedTicketscanbestolenfrommemoryandusedtoauthenticateelsewhere(PasstheTicket).
Further,accesstotheDCallowsticketstobecreatedforanyuserwithnoexpiration(GoldenTicket).
Serviceaccountticketscanberequestedandforged,includingofflinecrackingofserviceaccounthashes(Kerberoasting).
Commontools:MimikatzWCEkerberoastHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT24PasstheTicket(Mimikatz)25KerberosAttacks27PasstheTicketStealticketfrommemoryandpassorimportonothersystemsOverpasstheHashUseNThashtorequestaserviceticketforthesameaccountKerberoastingRequestserviceticketforhighlyprivilegedservice&crackNThashGoldenTicketKerberosTGTforanyaccountwithnoexpiration.
SurvivesfullpasswordresetSilverTicketAll-accesspassforasingleserviceorcomputerSkeletonKeyPatchLSASSondomaincontrollertoaddbackdoorpasswordthatworksforanydomainaccountCredentialGuard(Win10+)DomainProtectedUsersGroup(Win8+)–SomeattacksRemoteCredentialGuard(Win10+)RestrictedAdmin(Win8+)Long&complexpasswordsonserviceaccounts(topreventKerberoasting)ChangeserviceaccountpasswordsregularlyGroupManagedServiceAccountsareagreatmitigationAuditserviceaccountsforunusualactivityChangeKRBTGTpasswordregularly(yearly)DefendingCredentials:Tickets28AttackTypeDescriptionMitigationPasstheTicketStealticketfrommemoryandpassorimportonothersystemsCredentialGuard;RemoteCredentialGuardOverpasstheHashUseNThashtorequestaserviceticketforthesameaccountCredentialGuard;ProtectedUsersGroup;DisableRC4authenticationKerberoastingRequestserviceticketforhighlyprivilegedservice&crackNThashLongandcomplexserviceaccountpasswords;ManagedServiceAccountsGoldenTicketKerberosTGTforanyaccountwithnoexpiration.
SurvivesfullpasswordresetProtectdomainadminaccounts;ChangeKRBTGTpasswordregularlySilverTicketAll-accesspassforasingleserviceorcomputerRegularcomputeraccountpasswordupdatesSkeletonKeyPatchLSASSondomaincontrollertoaddbackdoorpasswordtoanyaccountProtectdomainadminaccounts;SmartcardusageforprivilegedaccountsKerberosAttackMitigations29CompromisingCredentials:NTDS.
DITHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DITActiveDirectoryDomainServices(ADDS)databaseholdsalluserandcomputeraccounthashes(LM/NT)inthedomain.
Encrypted,butalgorithmiswellknownandeasytodefeat.
HowisitacquiredandusedLocatedinthe\Windows\NTDSfolderonthedomaincontroller.
Thefileislocked,soadminaccessisrequiredtoloadadrivertoaccessrawdisk,orusetheVolumeShadowCopyService.
Commontools:ntdsutilVSSAdminNTDSXtractVSSOwn.
vbsPowerShellntdsdump30CommandProcess:conhost.
exePid:141716CommandHistory:0x1b8f80Application:cmd.
exeFlags:Allocated,ResetCommandCount:12LastAdded:11LastDisplayed:11FirstCommand:0CommandCountMax:50ProcessHandle:0x60Cmd#0@0x196970:vssadminlistshadowsCmd#1@0x1bd240:cd\Cmd#2@0x1b9290:dirCmd#3@0x1bd260:cdtempCmd#4@0x1b92b0:dirCmd#5@0x19c6a0:copy\\\GLOBALROOT\Device\HarddiskVolumeShadowCopy49\windows\system32\config\SYSTEM.
Cmd#6@0x19c760:dirCmd#7@0x19c780:copy\\\GLOBALROOT\Device\HarddiskVolumeShadowCopy49\windows\system32\config\SAM.
Cmd#8@0x19c830:copy\\\GLOBALROOT\Device\HarddiskVolumeShadowCopy49\windows\ntds\ntds.
dit.
Cmd#9@0x1c1ab0:dirStealingNTDS.
DIT31Don'tallowDomainAdminaccountstobecompromised.
DefendingCredentials:NTDS.
DIT32CredentialAttackDetection33"Asanypass-the-ticketattack,theattackerreplaysthegoldenticketinastandardKerberosprotocol.
Therefore,thereisnoclearindicationofsuchattackinWindowslogs.
"34"GoldenTicketeventsmayhaveoneoftheseissues:TheAccountDomainfieldisblankwhenitshouldbeDOMAINTheAccountDomainfieldisDOMAINFQDNwhenitshouldbeDOMAIN.
"–SeanMetcalf,adsecurity.
org3536Asanexample…KerberoastingusesRC4encryptiondowngrade(butalmostnoonelogstheseevents)AuthenticationAuditingMappingAdmin$SharesPsExecScheduledTasksVSSAdminRDP/VPNactivityToolArtifactsNewServicesRandomFile/HostnamesCodeInjectionCrashesandSecurityAlertsBehavioralAnalysisLocalAdminAccountUseDomainAdminAnomaliesServiceAccountAnomaliesWorkstation-to-workstationconnectionsCredentialAttackDetection38EventlogsarecriticalfordetectionAuthenticationevents(EID4624,4762,4648,4720,etc.
)Newservices(EID7045)ApplicationandProcessCrashesFailedandanomalousSMBactivity(EID5140)AV/SecuritylogsDomainProtectedUsersecuritygrouplogsApplicationsandServicesLogs\Microsoft\Windows\Microsoft\AuthenticationProcesstrackingCommandlinecapturesPowerShellauditingCredentialAttackDetection39CredentialAttackDetection:PasstheHash40CredentialAttackDetection:PsExecandfgdumpInitiationoftwonear-simultaneousservicesbyhelpdeskaccount42CredentialAttackDetection:LSASSCrashSystemEventLogApplicationEventLog**ReviewandcorrelateyourAnti-Viruslogs**44CredentialAttackDetection:CapturingCommandLines46RegistrychangesDisabledcomputeraccountpwdupdates(SilverTickets)SYSTEM\CurrentControlSet\Services\Netlogon\ParametersDisablePasswordChange=1EnabledWDigestcredentials(postWin8.
1)SYSTEM\CurrentControlSet\Control\SecurityProviders\WdigestUseLogonCredential=1MemoryAnalysisProcessinjectionLoadeddriversKernel-levelsecurityagentdetectionsBehavioralAnalyticsCredentialAttackDetection:OtherDataSources48CredentialBestPractices49RestrictandProtectPrivilegedDomainAccountsReducethenumberofDomain/EnterpriseAdminsEnforcemulti-factorauthentication(MFA)forallnetworkandcloudadminaccountsSeparateadministrativeaccountsfromuseraccountsforadministrativepersonnelCreatespecificadministrativeworkstationhostsforadministratorsUsetheDomainProtectedUserssecuritygroup!
BestPractices:ControlYourAdminAccounts50LimitLocalAdminAccountsDon'tgiveusersadminUniqueandcomplexpasswordsforlocaladmin(LAPS)DenynetworklogonsforlocalaccountsAuditaccountusageandmonitorforanomaliesBestPractices:ControlYourAdminAccounts(2)51Imagesource:LocalAdministratorPasswordSolutionhttps://technet.
microsoft.
com/en-us/mt227395.
aspxUseaTieredAdministrativeAccessModelAdministrationofADServersandApplicationsWorkstationsandDevicesBestPractices:ControlYourAdminAccounts(3)52Imagesource:SecuringPrivilegedAccessReferenceMaterialbyCoreyPlett(Microsoft)AuditandlimitthenumberofservicesrunningassystemanddomainaccountsUtilizeGroupManagedServiceAccounts…orregularlychangeanduselong&complexpasswordsUpgradetoWindows10/Server2016EnableCredentialGuard&RemoteCredentialGuardForceLSASSasprotectedprocessonlegacyWin8.
1EstablishremoteconnectionsusingnetworklogoninsteadofinteractivelogonwhenpossibleBestPractices:ReducetheCredentialAttackSurface53LimitworkstationtoworkstationcommunicationRestrictinboundNetBIOS,SMBtrafficusingtheWindowsFirewall…orVLANsegmentationofworkstationsSomanyhacktoolsleverageSMBauthenticationIsworkstationtoworkstationRDPreallynecessaryEnablestricterKerberossecurityDisableLM&NTLM(forceKerberos)ShortvalidityforticketsNoaccountdelegationBestPractices:ReducetheCredentialAttackSurface(2)54ChartbyBenjaminDelpy:https://goo.
gl/1K3AC7IncreaseAwarenessofNewAttacks5556Materialsfrom:http://dfir.
to/FOR508
tilbury@crowdstrike.
comLinkedIn:ChadTilburyTwitter:@chadtilburyComputerCrimeInvestigationsCrowdStrikeMandiantUSAirForceOSISpecialAgentCHADTILBURYTECHNICALADVISORCROWDSTRIKESERVICESSANSINSTITUTECONNECT15+YEARSPriority#1post-exploitationDomainadminisultimategoalNearlyeverythinginWindowsistiedtoanaccountDifficulttomovewithoutoneEasyandrelativelystealthymeanstotraversethenetworkAccountlimitationsarerare"Sleeper"credentialscanprovideaccessafterremediationCompromisingCredentials3PillageAchieveDomainAdminDumpMoarCredentials_MoveLaterallyDumpCredentialsGainFootholdUserAccessControl(UAC)ManagedServiceAccountsKB2871997SSPplaintextpasswordmitigationsLocaladminremotelogonrestrictionsProtectedProcessesRestrictedAdminDomainProtectedUsersSecurityGroupLSACachecleanupGroupManagedServiceAccountsCredentialGuardRemoteCredentialGuardDeviceGuard(preventexecutionofuntrustedcode)EvolutionofCredentialAttackMitigation4CompromisingCredentials:HashesThepasswordforeachuseraccountinWindowsisstoredinmultipleformats:LMandNThashesaremostwellknown.
TsPkg,WDigest,andLiveSSPcanbedecryptedtoprovideplaintextpasswords(priortoWin8.
1)HowaretheyacquiredandusedHashesareavailableintheLSASSprocessandcanbeextractedwithadminprivileges.
Oncedumped,hashescanbecrackedorusedimmediatelyinaPasstheHashattack.
Commontools:MimikatzfgdumpgsecdumpMetasploitSMBshellPWDumpXcreddumpWCEHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT5AdminActionLogonTypeCredentialsonTargetNotesConsolelogon2Yes**ExceptwhenCredentialGuardisenabledRunas2Yes**ExceptwhenCredentialGuardisenabledRemoteDesktop10Yes**ExceptforenabledRemoteCredentialGuardNetUse3NoIncluding/u:parameterPowerShellRemoting3NoInvoke-Command;Enter-PSSessionPsExecalternatecreds3+2Yes-u-p
com/en-us/windows-server-docs/security/securing-privileged-access/securing-privileged-access-reference-materialHashDumping(Gsecdump)8PasstheHash(Mimikatz)10PreventadminaccountcompromiseStopremoteinteractivesessionswithhighlyprivilegedaccountsProperterminationofRDPsessionsWin8.
1+forcetheuseofRestrictedAdminWin10deployRemoteCredentialGuardUpgradetoWindows10CredentialGuardTsPkg,WDigest,etc.
--SSOcredsobsolescenceDomainProtectedUsersGroup(PtHmitigation)DefendingCredentials:Hashes12CompromisingCredentials:TokensDelegatetokensarepowerfulauthenticationresourcesusedforSSO.
Theyallowattackerstoimpersonateauser'ssecuritycontext,includingoverthenetwork.
HowaretheyacquiredandusedTheSeImpersonateprivilegeletstokensbecopiedfromprocesses.
Thenewtokencanthenbeusedtoauthenticateasthenewuser.
Atargetuserorservicemustbeloggedonorhaverunningprocesses.
Commontools:IncognitoMetasploitPowerShellMimikatzHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT13TokenStealing(Mimikatz)14PreventadminaccountcompromiseStopremoteinteractivesessionswithhighlyprivilegedaccountsProperterminationofRDPsessionsWin8.
1+forcetheuseofRestrictedAdminModeWin10deployRemoteCredentialGuardAccountdesignationof"AccountisSensitiveandCannotbeDelegated"inActiveDirectoryDomainProtectedUserssecuritygroupaccountsdonotcreatedelegatetokensDefendingCredentials:Tokens16CompromisingCredentials:CachedCredentialsStoreddomaincredentialstoallowlogonswhendomaincontrolleraccessisunavailable.
Mostsystemscachethelast10logonhashesbydefault.
HowaretheyacquiredandusedCachedcredentialsmustbecracked.
Hashesaresaltedandcase-sensitive,makingdecryptionveryslow.
ThesehashescannotbeusedforPasstheHashattacks.
Commontools:cachedumpMetasploitPWDumpXcreddumpHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT17Thecreddumputilitiescanextracthashes,cachedcredentialsandLSASecretsfromofflineregistryhives:github.
com/Neohapsis/creddump7OfflineCachedCredentialsExtraction(Creddump)18LocalNTHashesCachedHashesPreventadminaccountcompromiseLimitnumberofcachedlogonaccountsSOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon(cachedlogonscountvalue)AcachedlogonscountofzerooroneisnotalwaystherightanswerEnforcepasswordlengthandcomplexityrulesBruteforcecrackingisrequiredforthisattackDomainProtectedUserssecuritygroupaccountsdonotcachecredentialsDefendingCredentials:CachedCredentials20CompromisingCredentials:LSASecretsCredentialsstoredintheregistrytoallowservicesortaskstoberunwithuserprivileges.
Inadditiontoserviceaccounts,mayalsoholdapplicationpasswordslikeVPNorauto-logoncredentials.
HowaretheyacquiredandusedAdministratorprivilegesallowaccesstoencryptedregistrydataandthekeysnecessarytodecrypt.
PasswordsareplaintextCommontools:CainMetasploitMimikatzgsecdumpPWDumpXcreddumpPowerShellHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT21Get-LsaSecret.
ps1fromtheNishangPowerShellpentestframeworkusedtodump(anddecrypt)LSASecretshttps://github.
com/samratashok/nishangDecryptingLSASecrets(Nishang)22PreventadminaccountcompromiseDonotemployservicesorscheduletasksrequiringprivilegedaccountsonlowtrustsystemsReducenumberofservicesthatrequiredomainaccountstoexecuteHeavilyauditanyaccountsthatmustbeused(Group)ManagedServiceAccountsDefendingCredentials:LSASecrets23CompromisingCredentials:TicketsKerberosissuesticketstoauthenticatedusersthatcanbereusedwithoutadditionalauthentication.
Ticketsarecachedinmemoryandarevalidfor10hours.
HowaretheyacquiredandusedTicketscanbestolenfrommemoryandusedtoauthenticateelsewhere(PasstheTicket).
Further,accesstotheDCallowsticketstobecreatedforanyuserwithnoexpiration(GoldenTicket).
Serviceaccountticketscanberequestedandforged,includingofflinecrackingofserviceaccounthashes(Kerberoasting).
Commontools:MimikatzWCEkerberoastHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DIT24PasstheTicket(Mimikatz)25KerberosAttacks27PasstheTicketStealticketfrommemoryandpassorimportonothersystemsOverpasstheHashUseNThashtorequestaserviceticketforthesameaccountKerberoastingRequestserviceticketforhighlyprivilegedservice&crackNThashGoldenTicketKerberosTGTforanyaccountwithnoexpiration.
SurvivesfullpasswordresetSilverTicketAll-accesspassforasingleserviceorcomputerSkeletonKeyPatchLSASSondomaincontrollertoaddbackdoorpasswordthatworksforanydomainaccountCredentialGuard(Win10+)DomainProtectedUsersGroup(Win8+)–SomeattacksRemoteCredentialGuard(Win10+)RestrictedAdmin(Win8+)Long&complexpasswordsonserviceaccounts(topreventKerberoasting)ChangeserviceaccountpasswordsregularlyGroupManagedServiceAccountsareagreatmitigationAuditserviceaccountsforunusualactivityChangeKRBTGTpasswordregularly(yearly)DefendingCredentials:Tickets28AttackTypeDescriptionMitigationPasstheTicketStealticketfrommemoryandpassorimportonothersystemsCredentialGuard;RemoteCredentialGuardOverpasstheHashUseNThashtorequestaserviceticketforthesameaccountCredentialGuard;ProtectedUsersGroup;DisableRC4authenticationKerberoastingRequestserviceticketforhighlyprivilegedservice&crackNThashLongandcomplexserviceaccountpasswords;ManagedServiceAccountsGoldenTicketKerberosTGTforanyaccountwithnoexpiration.
SurvivesfullpasswordresetProtectdomainadminaccounts;ChangeKRBTGTpasswordregularlySilverTicketAll-accesspassforasingleserviceorcomputerRegularcomputeraccountpasswordupdatesSkeletonKeyPatchLSASSondomaincontrollertoaddbackdoorpasswordtoanyaccountProtectdomainadminaccounts;SmartcardusageforprivilegedaccountsKerberosAttackMitigations29CompromisingCredentials:NTDS.
DITHashesTokensCachedCredentialsLSASecretsTicketsNTDS.
DITActiveDirectoryDomainServices(ADDS)databaseholdsalluserandcomputeraccounthashes(LM/NT)inthedomain.
Encrypted,butalgorithmiswellknownandeasytodefeat.
HowisitacquiredandusedLocatedinthe\Windows\NTDSfolderonthedomaincontroller.
Thefileislocked,soadminaccessisrequiredtoloadadrivertoaccessrawdisk,orusetheVolumeShadowCopyService.
Commontools:ntdsutilVSSAdminNTDSXtractVSSOwn.
vbsPowerShellntdsdump30CommandProcess:conhost.
exePid:141716CommandHistory:0x1b8f80Application:cmd.
exeFlags:Allocated,ResetCommandCount:12LastAdded:11LastDisplayed:11FirstCommand:0CommandCountMax:50ProcessHandle:0x60Cmd#0@0x196970:vssadminlistshadowsCmd#1@0x1bd240:cd\Cmd#2@0x1b9290:dirCmd#3@0x1bd260:cdtempCmd#4@0x1b92b0:dirCmd#5@0x19c6a0:copy\\\GLOBALROOT\Device\HarddiskVolumeShadowCopy49\windows\system32\config\SYSTEM.
Cmd#6@0x19c760:dirCmd#7@0x19c780:copy\\\GLOBALROOT\Device\HarddiskVolumeShadowCopy49\windows\system32\config\SAM.
Cmd#8@0x19c830:copy\\\GLOBALROOT\Device\HarddiskVolumeShadowCopy49\windows\ntds\ntds.
dit.
Cmd#9@0x1c1ab0:dirStealingNTDS.
DIT31Don'tallowDomainAdminaccountstobecompromised.
DefendingCredentials:NTDS.
DIT32CredentialAttackDetection33"Asanypass-the-ticketattack,theattackerreplaysthegoldenticketinastandardKerberosprotocol.
Therefore,thereisnoclearindicationofsuchattackinWindowslogs.
"34"GoldenTicketeventsmayhaveoneoftheseissues:TheAccountDomainfieldisblankwhenitshouldbeDOMAINTheAccountDomainfieldisDOMAINFQDNwhenitshouldbeDOMAIN.
"–SeanMetcalf,adsecurity.
org3536Asanexample…KerberoastingusesRC4encryptiondowngrade(butalmostnoonelogstheseevents)AuthenticationAuditingMappingAdmin$SharesPsExecScheduledTasksVSSAdminRDP/VPNactivityToolArtifactsNewServicesRandomFile/HostnamesCodeInjectionCrashesandSecurityAlertsBehavioralAnalysisLocalAdminAccountUseDomainAdminAnomaliesServiceAccountAnomaliesWorkstation-to-workstationconnectionsCredentialAttackDetection38EventlogsarecriticalfordetectionAuthenticationevents(EID4624,4762,4648,4720,etc.
)Newservices(EID7045)ApplicationandProcessCrashesFailedandanomalousSMBactivity(EID5140)AV/SecuritylogsDomainProtectedUsersecuritygrouplogsApplicationsandServicesLogs\Microsoft\Windows\Microsoft\AuthenticationProcesstrackingCommandlinecapturesPowerShellauditingCredentialAttackDetection39CredentialAttackDetection:PasstheHash40CredentialAttackDetection:PsExecandfgdumpInitiationoftwonear-simultaneousservicesbyhelpdeskaccount42CredentialAttackDetection:LSASSCrashSystemEventLogApplicationEventLog**ReviewandcorrelateyourAnti-Viruslogs**44CredentialAttackDetection:CapturingCommandLines46RegistrychangesDisabledcomputeraccountpwdupdates(SilverTickets)SYSTEM\CurrentControlSet\Services\Netlogon\ParametersDisablePasswordChange=1EnabledWDigestcredentials(postWin8.
1)SYSTEM\CurrentControlSet\Control\SecurityProviders\WdigestUseLogonCredential=1MemoryAnalysisProcessinjectionLoadeddriversKernel-levelsecurityagentdetectionsBehavioralAnalyticsCredentialAttackDetection:OtherDataSources48CredentialBestPractices49RestrictandProtectPrivilegedDomainAccountsReducethenumberofDomain/EnterpriseAdminsEnforcemulti-factorauthentication(MFA)forallnetworkandcloudadminaccountsSeparateadministrativeaccountsfromuseraccountsforadministrativepersonnelCreatespecificadministrativeworkstationhostsforadministratorsUsetheDomainProtectedUserssecuritygroup!
BestPractices:ControlYourAdminAccounts50LimitLocalAdminAccountsDon'tgiveusersadminUniqueandcomplexpasswordsforlocaladmin(LAPS)DenynetworklogonsforlocalaccountsAuditaccountusageandmonitorforanomaliesBestPractices:ControlYourAdminAccounts(2)51Imagesource:LocalAdministratorPasswordSolutionhttps://technet.
microsoft.
com/en-us/mt227395.
aspxUseaTieredAdministrativeAccessModelAdministrationofADServersandApplicationsWorkstationsandDevicesBestPractices:ControlYourAdminAccounts(3)52Imagesource:SecuringPrivilegedAccessReferenceMaterialbyCoreyPlett(Microsoft)AuditandlimitthenumberofservicesrunningassystemanddomainaccountsUtilizeGroupManagedServiceAccounts…orregularlychangeanduselong&complexpasswordsUpgradetoWindows10/Server2016EnableCredentialGuard&RemoteCredentialGuardForceLSASSasprotectedprocessonlegacyWin8.
1EstablishremoteconnectionsusingnetworklogoninsteadofinteractivelogonwhenpossibleBestPractices:ReducetheCredentialAttackSurface53LimitworkstationtoworkstationcommunicationRestrictinboundNetBIOS,SMBtrafficusingtheWindowsFirewall…orVLANsegmentationofworkstationsSomanyhacktoolsleverageSMBauthenticationIsworkstationtoworkstationRDPreallynecessaryEnablestricterKerberossecurityDisableLM&NTLM(forceKerberos)ShortvalidityforticketsNoaccountdelegationBestPractices:ReducetheCredentialAttackSurface(2)54ChartbyBenjaminDelpy:https://goo.
gl/1K3AC7IncreaseAwarenessofNewAttacks5556Materialsfrom:http://dfir.
to/FOR508
- Win10盗版win8.1升级win10相关文档
- 项目编号:宣公共采【2017】57号
- 惠普盗版win8.1升级win10
- Brownian盗版win8.1升级win10
- 投标人盗版win8.1升级win10
- 互联网网络安全信息通报
- 广州盗版win8.1升级win10
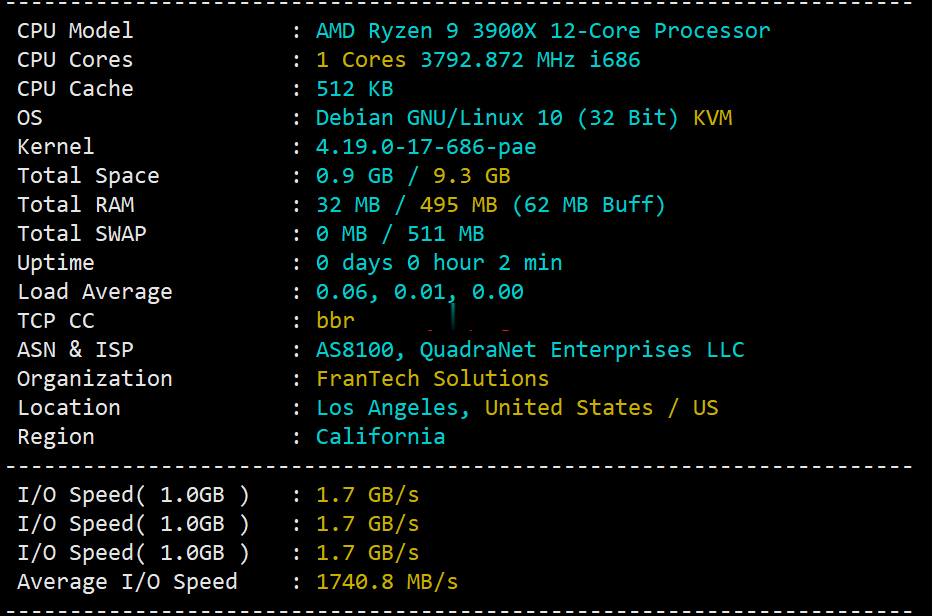
buyvm迈阿密机房VPS国内首发测评,高性能平台:AMD Ryzen 9 3900x+DDR4+NVMe+1Gbps带宽不限流量
buyvm的第四个数据中心上线了,位于美国东南沿海的迈阿密市。迈阿密的VPS依旧和buyvm其他机房的一样,KVM虚拟,Ryzen 9 3900x、DDR4、NVMe、1Gbps带宽、不限流量。目前还没有看见buyvm上架迈阿密的block storage,估计不久也会有的。 官方网站:https://my.frantech.ca/cart.php?gid=48 加密货币、信用卡、PayPal、...
TTcloud:日本独立服务器促销活动,价格$70/月起,季付送10Mbps带宽
ttcloud怎么样?ttcloud是一家海外服务器厂商,运营服务器已经有10年时间,公司注册地址在香港地区,业务范围包括服务器托管,机柜托管,独立服务器等在内的多种服务。我们后台工单支持英文和中文服务。TTcloud最近推出了新上架的日本独立服务器促销活动,价格 $70/月起,季付送10Mbps带宽。也可以跟进客户的需求进行各种DIY定制。点击进入:ttcloud官方网站地址TTcloud拥有自...
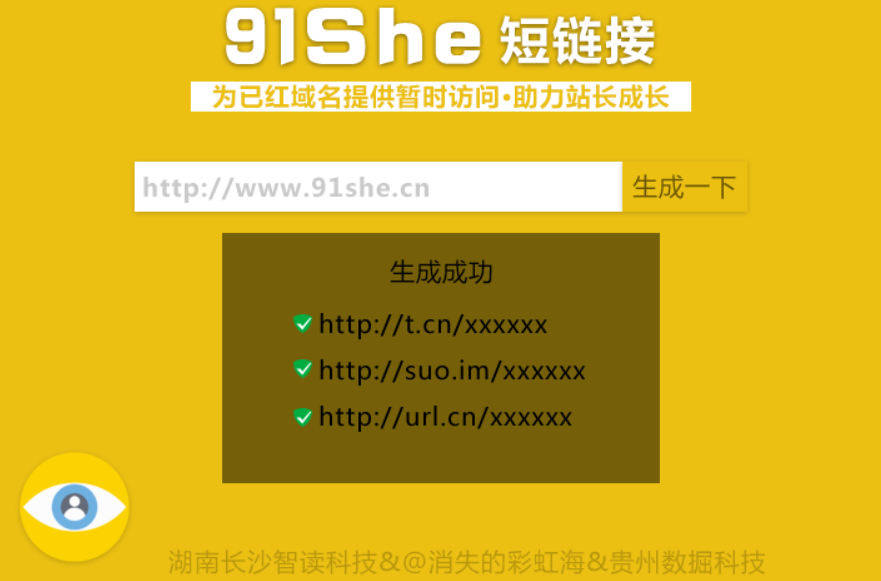
QQ防红跳转短网址生成网站源码(91she完整源码)
使用此源码可以生成QQ自动跳转到浏览器的短链接,无视QQ报毒,任意网址均可生成。新版特色:全新界面,网站背景图采用Bing随机壁纸支持生成多种短链接兼容电脑和手机页面生成网址记录功能,域名黑名单功能网站后台可管理数据安装说明:由于此版本增加了记录和黑名单功能,所以用到了数据库。安装方法为修改config.php里面的数据库信息,导入install.sql到数据库。...
盗版win8.1升级win10为你推荐
-
软银亏损65亿美元马云仅仅持有阿里8.9%的股份,就有270多亿美元,孙正义的软银占有那么多股份,怎么还不是亚洲首富桌面背景图片大全谁能给我个 游戏桌面图标大全视频制作软件哪个好哪款视频编辑软件比较好用?莫代尔和纯棉哪个好纯棉含莫代尔和100%莫代尔哪个好莫代尔和纯棉哪个好莫代尔和纯棉的区别,莫代尔和纯棉哪个好手机浏览器哪个好手机浏览器哪个好?手机浏览器哪个好用?传奇类手游哪个好传奇手游版哪个好玩人多?音乐播放器哪个好最好的音乐播放器下载浮动利率和固定利率哪个好银行贷款是选固定利率好还是浮动利率绝地求生加速器哪个好绝地求生的加速器哪个好用?