contentsamazonec2
amazonec2 时间:2021-03-26 阅读:()
Chapter18DIGITALWATERMARKINGOFVIRTUALMACHINEIMAGESKumikoTadano,MasahiroKawato,RyoFurukawa,FumioMachidaandYoshiharuMaenoAbstractThewidespreaduseofserveranddesktopvirtualizationtechnologiesincreasesthelikelihoodofunauthorizedanduncontrolleddistributionofvirtualmachine(VM)imagesthatcontainproprietarysoftware.
Thispaperattemptstoaddressthisissueusingaplatform-independentdig-italwatermarkingschemeapplicabletoavarietyofVMimages.
TheschemeembedsawatermarkintheformoflesinaVMimage;thewatermarkedVMimageisidentiedbasedontheembeddedles.
Toreducethepossibilityofdiscoverybyanattacker,thenamesoftheem-beddedlesareverysimilartothenamesofpre-existinglesintheVMimage.
Experimentsindicatethattheapproachisfastandaccu-rate,withaverageturnaroundtimesof24.
001secondsand7.
549secondsforwatermarkgenerationanddetection,respectively.
Keywords:Digitalwatermarking,virtualmachineimages1.
IntroductionInmodernenterprisecomputingthereisagrowingtrendtowardcon-solidatingvirtualmachines(VMs)intheserverandclientsidestoreducecostsandenhanceportabilityandsecurity.
SuchenvironmentsrequirethemeanstoexportVMimagestotestsoftwareandtobackupVMs.
Forexample,Amazon'sElasticComputeCloud[1]andSimpleStorageService[2]providethecommandec2-download-bundletodownloadVMimagesfromadatacentertolocalcomputers[3].
Unfortunately,thistechnologyalsofacilitatestheunauthorizeddisseminationofVMimagescontainingproprietarysoftware.
Oneapproachforaddressingthisissueistousehost-basedintru-siondetectionsystemssuchasTripWire,AIDEandXenFIT[8].
TheseK.
-P.
Chow,S.
Shenoi(Eds.
):AdvancesinDigitalForensicsVI,IFIPAICT337,pp.
257–268,2010.
cIFIPInternationalFederationforInformationProcessing2010258ADVANCESINDIGITALFORENSICSVIsystemsmonitorunauthorizedlesystemchangestodetectmaliciousactivityinvolvingVMs.
However,itisdiculttoidentifyVMimagesaftertheyhavebeendistributedoutsideofanenterprisenetwork(e.
g.
,usingpeer-to-peerlesharingsoftware).
Anotherapproachistoimplementstrictaccesscontrolandcopycon-trolofVMimages.
However,thesecontrolsoftenhinderthelegitimateuseofVMs.
Therefore,itisnecessarytoaddresstwoissues:(i)identifyVMim-agesevenaftertheyhavebeenillegallydistributed;and(ii)facilitatelegitimateuseofVMimages.
DigitalwatermarkingofVMimagescanaddressboththeseissues.
However,aswediscussbelow,watermark-ingtechniquesusedforaudioandvideolesarenotapplicabletoVMimages.
Digitalwatermarkingtechnologiestypicallymodifyredundantorun-useddigitalcontent(e.
g.
,inaudiblefrequencyrangesforaudioles)toembedwatermarks.
Inthecaseofaudioandvideoles,modifyingtheoriginalinformationfordigitalwatermarkingproducesimperceptibleef-fectswhenplayingtheles[7].
Incontrast,modifyingaVMimagecancausebootfailureswhenthewatermarkedimageisexecuted.
Ad-ditionally,dataonthewatermarkedVMisfrequentlychangedbecauseofsoftwareupdates,logging,etc.
Unlikeanaudioorvideolewhosecontentisunchanged,aVMimageisessentiallyvariable;consequently,inordertoidentifytheVMimage,theimagehastobewatermarkedaftereverychange.
Datahidingtechniques[5]canbeemployedforwatermarkingVMimages.
Datacanbehiddeninvariouslocations:Areasmarkedasnotinusebythepartitiontable.
Extendedleattributessuchasalternatedatastreams.
Unusedportionsofthelastdataunitsofles(slackspace).
Reservedi-nodesthatarenotusedbytheoperatingsystem.
Portionsthatareexcludedduringconsistencycheckingofajour-nalinglesystem.
Fileshiddenviasteganographyusingspeciallesystemdrivers[6].
Amajordeciencyofexistingdatahidingtechniquesisthelackofplatform-independence:thetechniquesworkonspeciclesystems(e.
g.
,NTFS),operatingsystems(e.
g.
,RedHatLinux)andOSkernelversions(e.
g.
,Linux2.
2.
x).
Itisdicult,ifnotimpossible,toapplyTadano,etal.
259thesetechniquestoVMsinheterogeneousenvironmentswheremultiplelesystems,operatingsystemsandOSkernelversionsareused.
Toaddressthisissue,weproposeadigitalwatermarkingschemeforVMimagesthatisindependentoflesystems,leformats,operatingsystems,OSkernelversionsandhardware.
Theschemeembedsawa-termarkderivedfromthenamesofthelespresentinaVM.
2.
BasicConceptsOurdigitalwatermarkingschemeforVMimagesuseslenamesasawatermark,notthecontentsoftheles.
AuniqueidentieriscreatedforeachVMimageandawatermarkcorrespondingtotheidentierisembeddedintheformoflesinthelesystemoftheVMimage.
Theseembeddedlesarecalled"watermarkfragmentles.
"Ifthenamesofthewatermarkfragmentlesarerandomlycreated,theywouldbereadilydistinguishablefromthenamesofthepre-existinglesontheVM,enablinganattackertoidentifyandsubsequentlyre-movethewatermarkfragmentles.
Thus,thewatermarkingschememakesthefragmentlesdiculttodetectbycreatingfragmentleswithnamesthataresimilartopre-existinglesintheVMandembed-dingthelesinrandomdirectoriesintheVM.
AsecuredatabaseisusedtostoretheidentierofeachVMimageandthecorrespondingwatermarkfragmentles.
3.
DesignandImplementationThissectiondescribesthedesignandimplementationofthedigitalwatermarkingscheme.
3.
1SystemComponentsThesystemhasthreecomponents:(i)awatermarkgenerator;(ii)awatermarkdetector;and(iii)awatermarkinformationdatabase.
Figure1illustratesthewatermarkgenerationanddetectionprocesses.
WatermarkGenerator:ThewatermarkgeneratoremploysthenamesofthewatermarkfragmentlesasthewatermarkforaVMimage.
ItcreatesawatermarkedVMimagebyembeddingthewatermarkfragmentlesintheVMimageandstoresthegeneratedlenamesinthewatermarkinformationdatabase.
TheVMimagetobewatermarkediscreatedbycopyingthetemplateVMimagele.
SincethetemplateVMimagesareusedastheoriginaldataforwatermarking,theseimagesshouldbesecurelymanaged.
ThereasonisthatanattackerwhoobtainstheVMimagetemplate260ADVANCESINDIGITALFORENSICSVIIdentifierCertaintyWatermarkGenerationWatermarkDetectionWatermarkInformationDatabaseWatermarkGeneratorWatermarkDetectorWatermarkedVMImageVMImageTemplateWatermarkInformationDatabaseFigure1.
Watermarkgenerationanddetection.
wouldbeabletocomputethewatermarkfragmentlesasthedierencebetweenthetemplateVMimageandthewatermarkedVMimageles.
DetailsofthewatermarkgenerationalgorithmarepresentedinSection3.
2.
WatermarkedVMImageIDVMNameOwnerWatermarkFragmentFiles5ac8183d-e2cb-4ad2-a185-5c3beb0c17b8foo-desktopfoo/etc/yum/aaa.
conf,/var/log/dummy.
log42be8a40-5e6d-4677-84fb-e387f5638264bar-desktopbar/usr/local/bin/cmd,/etc/dummy.
conf…………WatermarkInformationDatabaseTableWatermarkFragmentFiles/etc/yum/aaa.
conf/var/log/dummy.
logID:5ac8183d-e2cb-4ad2-a185-5c3beb0c17b8Figure2.
Samplerecordsinthewatermarkinformationdatabase.
WatermarkInformationDatabase:Thewatermarkinforma-tiondatabase(WI-DB)storestheidentierofeachVMimageanditsattributes.
TheidentierforaVMimageisauniversallyuniqueidentier(UUID).
Theattributesincludethenamesofthewatermarkfragmentles,VMowner,etc.
(Figure2).
OnlyauthorizedusersshouldbepermittedtoreadandwriteWI-DBrecords.
Anattackerwithread/writeaccesscouldalterWI-DBrecordsoridentifyanddeletethewatermarkfragmentlesembeddedinaVMimage.
WatermarkDetector:ThewatermarkdetectoridentiesaVMusingthewatermarkfragmentlesembeddedinthetargetVMim-agebasedonWI-DBrecords.
WhenanunauthorizedleakofaVMimageissuspected,theadministratormayperformthedetectionprocesstoidentifytheVMimageanditsowner.
Tadano,etal.
261TargetVMImage/var//etc//usr//home//bin/…DirectoryTreeonVM1.
ObtainthenamesoftheWatermarkFragmentFiles2.
SearchthefilesintheVMImageIDVMNameOwnerWatermarkFragmentFiles5ac8183d-e2cb-4ad2-a185-5c3beb0c17b8foo-desktopfoo/etc/yum/aaa.
conf,/var/log/dummy.
log42be8a40-5e6d-4677-84fb-e387f5638264bar-desktopbar/usr/local/bin/cmd,/etc/dummy.
conf…………WatermarkInformationDatabaseTableID:unknownFigure3.
Watermarkdetection.
Figure3illustratesthedetectionprocess.
IftheidentierofthetargetVMcanbeguessed,thewatermarkgeneratorlooksupthecorrespondingWI-DBrecord.
Otherwise,thewatermarkdetectorcomparesthewatermarkfragmentlenamesinWI-DBrecordswiththoseinthetargetVMimage.
ThewatermarkgeneratorthenoutputsacertaintyvalueoftheidentierofthetargetVMimage.
ThecertaintyvalueiscomputedasthepercentageofthenamesofthewatermarkfragmentlesintheWI-DBrecordthatmatchlenamesintheVMimage.
Notethatsomewatermarkfragmentlesmayhavebeendeletedorrenamedonpurposeorbyaccident.
3.
2WatermarkGenerationAlgorithmThissectionbrieydescribestheprocessofgeneratingthewatermarkfragmentlesforthetargetVMimage.
Thealgorithmhasvesteps.
Step1:Inputtheparametersrequiredforwatermarkgeneration.
Step2:NumberthedirectoriesinthetargetVMimageindictio-naryorder.
Step3:Selectthedirectoriestoembedwatermarkfragmentles.
Step4:Generatethenamesofthewatermarkfragmentlestobecreated.
Step5:GeneratethecontentsofthewatermarkfragmentlesforthedirectoriesselectedinStep3.
262ADVANCESINDIGITALFORENSICSVITable1.
Directorycodelist.
NumberDirectoryName1/2/etc/3/etc/init.
d/4/etc/ldap/5/etc/skel/6/etc/ssh/7/etc/sysconfig/.
.
.
.
.
.
Step1(InputParametersforWatermarkGeneration):Thefollowinginputparametersarerequiredforwatermarkgeneration:NumberofWatermarkFragmentFiles:Thelargerthenum-berofwatermarkfragmentles,themoretamper-resistantisthewatermark.
However,thisincreasesthetimerequiredtogeneratewatermarkfragmentles.
ExcludedDirectories:Somedirectories(e.
g.
,temporarydirec-tories)shouldbeexcludedbecauselesinthesedirectorieschangefrequently.
ExcludedSuxes:Thesearesuxesthatshouldbeexcludedfromthenamesofthewatermarkfragmentles.
BitLength:ThebitlengthisaparameterusedbytheBlum-Blum-Shub(BBS)algorithm[4]togeneratecryptographically-sec-urepseudo-randomnumbers.
Thisparameteraectsthecomputa-tionaltimeandsecurity,andissetto1024bitsinourexperiments.
Step2(NumbertheDirectoriesintheTargetVMImage):ThewatermarkgeneratorsearchesallthedirectoriesinthetargetVMimagerecursivelyandgeneratesa"directorycodelist"(Table1).
TheexcludeddirectoriesidentiedinStep1arenotnumbered.
ThedirectorycodeofatemplateVMimagecanbereusedwhennewwatermarkedVMimagesarecreatedfromthesametemplateVMimagebecausetheyhavethesamedirectorytreestructure.
Thisreducestheprocessingtime.
Step3(SelectDirectoriestoEmbedWatermarkFragmentFiles):Thewatermarkgeneratorproducespseudo-randomnumbersforthewatermarkfragmentlesinputinStep1.
ThevaluesoftheTadano,etal.
263randomnumbersarelimitedtotherangeofdirectorycodes.
Thewa-termarkgeneratorextractsthenamesofdirectoriescorrespondingtothegeneratedrandomnumbersusingthedirectorycodelistgeneratedinStep2.
TheBBSpseudo-randomnumbergenerationalgorithmisusedtomaketherandomnumbersdicultforanattackertopredict.
Althoughthisalgorithmiscomputationallyintensive,theexperimentalresultspresentedinSection4.
2indicatethattheoverallperformanceofthewatermarkingschemeisacceptable.
Step4(GeneratetheNamesofWatermarkFragmentFiles):ThewatermarkgeneratorcreatesthenamesofthewatermarkfragmentlesthatareembeddedinthedirectoriesselectedinStep3.
Portionsofthenamesofpre-existinglesinthedirectoriesaremodiedtocreatelenamesthataresimilartothoseofthepre-existingles.
Alenameisgeneratedaccordingtothefollowingsteps.
Step4.
1:Getthenamesofexistinglesinthetargetdirectory.
Onlyregularles(notsubdirectories,hiddenles,etc.
)whosesuxesarenottobeexcludedareretrieved.
Step4.
2:Enumerateallthesubstringscorrespondingtothelenames.
Eachsubstringisobtainedfromthehead(i.
e.
,notinclud-ingthesux)ofalenameretrievedinStep4.
1.
Theresultofthisstepistheunionofsubstringsforallthelenames.
Forexam-ple,ifthetargetdirectoryhasalenamedabc.
txt,thepossiblesubstringsare:abc,abanda.
Step4.
3:Compute"similaritygroups"foreachextractedsub-string.
Asimilaritygroupisagroupoflesinthetargetdirectorythatmeetsthefollowingconditions:(i)thelenamestartswiththesubstring(prex)generatedinStep4.
2;(ii)alltheleshavethecommonsux(e.
g.
,.
txt);and(iii)asimilaritygroupcon-tainsatleasttwoles.
Forexample,iftherearevelesinatargetdirectory{s1.
txt,s2.
txt,s3.
dat,s4.
dat,s5.
conf}andsisthesubstring,thentwosimilaritygroupscanbecomputed:{s1.
txt,s2.
txt}and{s3.
dat,s4.
dat}.
Step4.
4:ComputetheDsimscoreforeachsimilaritygroup:Dsim=c1lp+c2nfc3ldwherelpisthelengthoftheprexofthesimilaritygroup;nfisthenumberoflesinthesimilaritygroup;ldisthemeanvalueofthedierencebetweenthelengthofthelename(excludingthe264ADVANCESINDIGITALFORENSICSVIsux)andlpinthesimilaritygroup;andc1,c2,c3areparametersthataresettoone.
ThesimilaritygroupwiththehighestDsimscoreiscalledthe"prototypelegroup.
"Step4.
5:Createthenameofthenewwatermarkfragmentle.
Oneormorerandomlettersareaddedtothetailoftheprexoftheselectedprototypelegroup.
Thelengthoftheaddedlet-ters(lt)isthelengthofthelenamerandomlyselectedfromtheprototypelegroup(excludingthesuxandprex).
Finally,thesuxofthelesintheprototypelegroupisaddedtothelename.
Forexample,iftheprexissampleandtheprototypelegroupis{sample.
dat,sample-bak.
dat}andifsample-bak.
datisselected,thenlt=4andapossiblenameissampledbha.
dat.
Step5(GeneratetheContentoftheWatermarkFragmentFiles):Thewatermarkgeneratorcreatesthecontentandattributescorrespondingtoeachwatermarkfragmentle.
Thecontentofawater-markfragmentleisarandomly-generatedbytesequence.
Attributesofawatermarkfragmentlearedeterminedaccordingtothefollowingrules.
Fortimestamps(creation/modication/access)andlesize,thewatermarkgeneratorassignsthemeanvaluesofthelesintheprototypelegrouptothenewwatermarkfragmentle.
Forotherattributessuchasownershipandpermission,thevaluescorrespondingtoarandomlyselectedleintheprototypelegroupareused.
3.
3ImplementationThedigitalwatermarkingschemewasimplementedinJava1.
5.
TheVMwareServervirtualizationsoftwarewasemployed.
Thecommandvmware-mount.
plwasissuedtotheVMwareServertomountthelesystemontheVMimageforembeddingwatermarkfragmentles.
TheVMimageofanylesystemoroperatingsystem,includingWindowsandLinux,canbewatermarked.
TheWI-DBwasimplementedusingMySQL5.
0.
4.
ExperimentalSetupandResultsThissectiondescribestheexperimentalsetupusedtoevaluatethewa-termarkingalgorithm.
Also,itpresentstheexperimentalresultsrelatedtowatermarkgenerationanddetection.
4.
1ExperimentalSetupAtestenvironmentwascreatedtoevaluatetheperformanceofthewatermarkingscheme.
Theenvironmentincludedonephysicalhost(Ta-Tadano,etal.
265Table2.
Testenvironment.
PhysicalHostCPUPentium41.
73GHzProcessorMemory1GBRAMHostOSUbuntuLinux8.
04ServerVMMVMwareServer2.
0GuestVMsGuestOSUbuntuLinux8.
04CentOS5.
1(JeOSedition)(default)VMImageSize183MB2,750MB(.
vmdkfile)Directories1,1207,429ble2).
TwotemplateVMimagesofdierentsizeswereusedtoclarifytheimpactofsizeonthewatermarkingscheme.
TheVMimagesusedwereanUbuntuLinux8.
04ServerJeOSedition(minimumcongurationforvirtualappliances)andadefaultinstallationofCentOS5.
1.
4.
2ExperimentalResultsThissectionpresentsourexperimentalresultsrelatedtowatermarkgenerationanddetection.
WatermarkGenerationTheVMimagetemplatesofUbuntuandCentOSwerecopiedandatotalof10and100watermarkfragmentleswereembeddedinthetwoVMimages.
Eachexperimentwasrepeated10timesandtheaverageturnaroundtimeswerecalculated.
Table3.
Turnaroundtimesforwatermarkgeneration.
Av.
GenerationTime(sec)Av.
Copying10Files100FilesTime(sec)UbuntuLinux8.
0413.
12124.
0016.
903CentOS5.
1168.
382177.
270142.
284Table3presentstheturnaroundtimesforcopyingVMimagesandgeneratingwatermarks.
Theexperimentsusedpreviously-createddirec-torycodesoftemplateVMimagesbecausethecodesaregeneratedonlythersttimethatthetemplateVMimagesareused.
Theresultsin-dicatethatthetimeforwatermarkgenerationexcludingthetimefor266ADVANCESINDIGITALFORENSICSVITable4.
Generatedwatermarkfragmentles.
FileNames/usr/share/zoneinfo/Pacific/kQGidyI/etc/console-tools/v2uQizvontwL8/lib/modules/2.
6.
24-16-virtual/kernel/sound/usb/snd-usb-INc.
ko/usr/lib/klibc/bin/hso.
shared/usr/lib/perl/5.
8.
8/IO/Socket/vS9jkE.
pm/usr/lib/python2.
5/wsgiref/hG272nT.
pyc/usr/share/debconf/jAGX7mQ.
sh/usr/share/zoneinfo/Mexico/irQ7KA/usr/share/zoneinfo/posix/Chile/5XwjAcopyingisessentiallyindependentofthesizeofthetemplateVMimage.
Theturnaroundtimesdropwhenfasterstoragedevicesareemployed.
Table4liststhegeneratedwatermarkfragmentles.
Thelenamessnd-usb-INc.
koandhso.
sharedarerelativelydiculttodistinguishfromthepre-existinglesinthetargetdirectories.
Incontrast,lenamessuchaskQGidyIareeasilydistinguishable.
Ingeneral,whentherearemanylesinthetargetdirectorywhosenameshavecommonextensionsandlongcommonsubstrings,thegeneratedlename(s)tendtobeindistinguishable.
Forexample,thelesnd-usb-INc.
kobelongsto/lib/modules/2.
6.
24-16-virtual/kernel/sound/usb/whosepre-existinglesaresnd-usb-audio.
koandsnd-usb-lib.
ko.
Meanwhile,ifonlyafewlenameshavecommonsubstrings/extensionsinthetargetdirec-tory,thegeneratedlename(s)tendtobecontrived.
WatermarkDetectionWatermarkdetectionexperimentswerecon-ductedtoidentify10and100watermarkfragmentlesfromthewater-markedUbuntu8.
04andCentOS5.
1VMimages.
Table5.
Turnaroundtimesforwatermarkdetection.
Av.
DetectionTime(sec)10Files100FilesUbuntuLinux8.
047.
5247.
549CentOS5.
17.
5267.
573Table5presentstheaverageturnaroundtimesforwatermarkdetec-tionbasedontenrepetitions.
Theresultsindicatethatthetimetakentodetectthewatermarkisalmostindependentofthesizeofthewater-markedVMimageandthenumberofwatermarkfragmentles.
Tadano,etal.
2675.
ConclusionsThedigitalwatermarkingschemeforVMimagesisindependentoflesystems,leformats,operatingsystems,kernelversionsandhardware.
Also,experimentsdemonstratethatwatermarkgenerationanddetectionarebothfastandeective.
Ourfutureworkwillfocusonenhancingthetamper-resistantcharac-teristicsofthewatermarkingscheme.
SeveralattackscouldbedevisedtoremoveormodifyVMimagewatermarks.
Forexample,watermarkscouldbedetectedusingamachinelearningalgorithmsuchtextcluster-ing[9]todiscriminateembeddedlesfrompre-existinglesbasedonlenamestringfeatures.
AnotherattackcoulduseinformationfromelsewhereintheVMsuchasthei-nodenumbersofles.
Filesinstalledatagiventimeareassignedsuccessivei-nodenumbers;alewithani-nodenumberthatisoutofsequencecouldcorrespondtoanembeddedle.
Otherproblemstobeinvestigatedincludehavingthecontentsofembeddedlesresemblethoseofpre-existingles,andaugmentingtheschemewithotherdatahidingapproachestoenhancetamperresistance.
Finally,ourresearchwillinvestigatetheapplicationofthewatermarkingschemetootherdigitalcontentsuchastarandziparchives.
References[1]AmazonWebServices,AmazonElasticComputeCloud,Seattle,Washington(aws.
amazon.
com/ec2).
[2]AmazonWebServices,AmazonSimpleStorageService,Seattle,Washington(s3.
amazonaws.
com).
[3]AmazonWebServices,ec2-download-bundle,Seattle,Wash-ington(docs.
amazonwebservices.
com/AmazonEC2/dg/2006-10-01/CLTRG-ami-download-bundle.
html).
[4]L.
Blum,M.
BlumandM.
Shub,Comparisonoftwopseudo-randomnumbergenerators,inAdvancesinCryptology:Proceed-ingsofCrypto1982,D.
Chaum,R.
RivestandA.
Sherman(Eds.
),Plenum,NewYork,pp.
61–78,1982.
[5]K.
EcksteinandM.
Jahnke,Datahidinginjournalinglesystems,ProceedingsoftheFifthAnnualDigitalForensicResearchWork-shop,2005.
[6]A.
McDonaldandM.
Kuhn,StegFS:AsteganographiclesystemforLinux,ProceedingsoftheThirdInternationalWorkshoponIn-formationHiding,pp.
463–477,2000.
268ADVANCESINDIGITALFORENSICSVI[7]F.
Perez-GonzalezandJ.
Hernandez,Atutorialondigitalwater-marking,ProceedingsoftheThirty-ThirdIEEEInternationalCar-nahanConferenceonSecurityTechnology,pp.
286–292,1999.
[8]N.
QuynhandY.
Takefuji,Anovelapproachforale-systemin-tegritymonitortoolforaXenvirtualmachine,ProceedingsoftheSecondACMSymposiumonInformation,ComputerandCommu-nicationsSecurity,pp.
194–202,2007.
[9]T.
Segaran,ProgrammingCollectiveIntelligence:BuildingSmartWeb2.
0Applications,O'Reilly,Sebastopol,California,2007.
Thispaperattemptstoaddressthisissueusingaplatform-independentdig-italwatermarkingschemeapplicabletoavarietyofVMimages.
TheschemeembedsawatermarkintheformoflesinaVMimage;thewatermarkedVMimageisidentiedbasedontheembeddedles.
Toreducethepossibilityofdiscoverybyanattacker,thenamesoftheem-beddedlesareverysimilartothenamesofpre-existinglesintheVMimage.
Experimentsindicatethattheapproachisfastandaccu-rate,withaverageturnaroundtimesof24.
001secondsand7.
549secondsforwatermarkgenerationanddetection,respectively.
Keywords:Digitalwatermarking,virtualmachineimages1.
IntroductionInmodernenterprisecomputingthereisagrowingtrendtowardcon-solidatingvirtualmachines(VMs)intheserverandclientsidestoreducecostsandenhanceportabilityandsecurity.
SuchenvironmentsrequirethemeanstoexportVMimagestotestsoftwareandtobackupVMs.
Forexample,Amazon'sElasticComputeCloud[1]andSimpleStorageService[2]providethecommandec2-download-bundletodownloadVMimagesfromadatacentertolocalcomputers[3].
Unfortunately,thistechnologyalsofacilitatestheunauthorizeddisseminationofVMimagescontainingproprietarysoftware.
Oneapproachforaddressingthisissueistousehost-basedintru-siondetectionsystemssuchasTripWire,AIDEandXenFIT[8].
TheseK.
-P.
Chow,S.
Shenoi(Eds.
):AdvancesinDigitalForensicsVI,IFIPAICT337,pp.
257–268,2010.
cIFIPInternationalFederationforInformationProcessing2010258ADVANCESINDIGITALFORENSICSVIsystemsmonitorunauthorizedlesystemchangestodetectmaliciousactivityinvolvingVMs.
However,itisdiculttoidentifyVMimagesaftertheyhavebeendistributedoutsideofanenterprisenetwork(e.
g.
,usingpeer-to-peerlesharingsoftware).
Anotherapproachistoimplementstrictaccesscontrolandcopycon-trolofVMimages.
However,thesecontrolsoftenhinderthelegitimateuseofVMs.
Therefore,itisnecessarytoaddresstwoissues:(i)identifyVMim-agesevenaftertheyhavebeenillegallydistributed;and(ii)facilitatelegitimateuseofVMimages.
DigitalwatermarkingofVMimagescanaddressboththeseissues.
However,aswediscussbelow,watermark-ingtechniquesusedforaudioandvideolesarenotapplicabletoVMimages.
Digitalwatermarkingtechnologiestypicallymodifyredundantorun-useddigitalcontent(e.
g.
,inaudiblefrequencyrangesforaudioles)toembedwatermarks.
Inthecaseofaudioandvideoles,modifyingtheoriginalinformationfordigitalwatermarkingproducesimperceptibleef-fectswhenplayingtheles[7].
Incontrast,modifyingaVMimagecancausebootfailureswhenthewatermarkedimageisexecuted.
Ad-ditionally,dataonthewatermarkedVMisfrequentlychangedbecauseofsoftwareupdates,logging,etc.
Unlikeanaudioorvideolewhosecontentisunchanged,aVMimageisessentiallyvariable;consequently,inordertoidentifytheVMimage,theimagehastobewatermarkedaftereverychange.
Datahidingtechniques[5]canbeemployedforwatermarkingVMimages.
Datacanbehiddeninvariouslocations:Areasmarkedasnotinusebythepartitiontable.
Extendedleattributessuchasalternatedatastreams.
Unusedportionsofthelastdataunitsofles(slackspace).
Reservedi-nodesthatarenotusedbytheoperatingsystem.
Portionsthatareexcludedduringconsistencycheckingofajour-nalinglesystem.
Fileshiddenviasteganographyusingspeciallesystemdrivers[6].
Amajordeciencyofexistingdatahidingtechniquesisthelackofplatform-independence:thetechniquesworkonspeciclesystems(e.
g.
,NTFS),operatingsystems(e.
g.
,RedHatLinux)andOSkernelversions(e.
g.
,Linux2.
2.
x).
Itisdicult,ifnotimpossible,toapplyTadano,etal.
259thesetechniquestoVMsinheterogeneousenvironmentswheremultiplelesystems,operatingsystemsandOSkernelversionsareused.
Toaddressthisissue,weproposeadigitalwatermarkingschemeforVMimagesthatisindependentoflesystems,leformats,operatingsystems,OSkernelversionsandhardware.
Theschemeembedsawa-termarkderivedfromthenamesofthelespresentinaVM.
2.
BasicConceptsOurdigitalwatermarkingschemeforVMimagesuseslenamesasawatermark,notthecontentsoftheles.
AuniqueidentieriscreatedforeachVMimageandawatermarkcorrespondingtotheidentierisembeddedintheformoflesinthelesystemoftheVMimage.
Theseembeddedlesarecalled"watermarkfragmentles.
"Ifthenamesofthewatermarkfragmentlesarerandomlycreated,theywouldbereadilydistinguishablefromthenamesofthepre-existinglesontheVM,enablinganattackertoidentifyandsubsequentlyre-movethewatermarkfragmentles.
Thus,thewatermarkingschememakesthefragmentlesdiculttodetectbycreatingfragmentleswithnamesthataresimilartopre-existinglesintheVMandembed-dingthelesinrandomdirectoriesintheVM.
AsecuredatabaseisusedtostoretheidentierofeachVMimageandthecorrespondingwatermarkfragmentles.
3.
DesignandImplementationThissectiondescribesthedesignandimplementationofthedigitalwatermarkingscheme.
3.
1SystemComponentsThesystemhasthreecomponents:(i)awatermarkgenerator;(ii)awatermarkdetector;and(iii)awatermarkinformationdatabase.
Figure1illustratesthewatermarkgenerationanddetectionprocesses.
WatermarkGenerator:ThewatermarkgeneratoremploysthenamesofthewatermarkfragmentlesasthewatermarkforaVMimage.
ItcreatesawatermarkedVMimagebyembeddingthewatermarkfragmentlesintheVMimageandstoresthegeneratedlenamesinthewatermarkinformationdatabase.
TheVMimagetobewatermarkediscreatedbycopyingthetemplateVMimagele.
SincethetemplateVMimagesareusedastheoriginaldataforwatermarking,theseimagesshouldbesecurelymanaged.
ThereasonisthatanattackerwhoobtainstheVMimagetemplate260ADVANCESINDIGITALFORENSICSVIIdentifierCertaintyWatermarkGenerationWatermarkDetectionWatermarkInformationDatabaseWatermarkGeneratorWatermarkDetectorWatermarkedVMImageVMImageTemplateWatermarkInformationDatabaseFigure1.
Watermarkgenerationanddetection.
wouldbeabletocomputethewatermarkfragmentlesasthedierencebetweenthetemplateVMimageandthewatermarkedVMimageles.
DetailsofthewatermarkgenerationalgorithmarepresentedinSection3.
2.
WatermarkedVMImageIDVMNameOwnerWatermarkFragmentFiles5ac8183d-e2cb-4ad2-a185-5c3beb0c17b8foo-desktopfoo/etc/yum/aaa.
conf,/var/log/dummy.
log42be8a40-5e6d-4677-84fb-e387f5638264bar-desktopbar/usr/local/bin/cmd,/etc/dummy.
conf…………WatermarkInformationDatabaseTableWatermarkFragmentFiles/etc/yum/aaa.
conf/var/log/dummy.
logID:5ac8183d-e2cb-4ad2-a185-5c3beb0c17b8Figure2.
Samplerecordsinthewatermarkinformationdatabase.
WatermarkInformationDatabase:Thewatermarkinforma-tiondatabase(WI-DB)storestheidentierofeachVMimageanditsattributes.
TheidentierforaVMimageisauniversallyuniqueidentier(UUID).
Theattributesincludethenamesofthewatermarkfragmentles,VMowner,etc.
(Figure2).
OnlyauthorizedusersshouldbepermittedtoreadandwriteWI-DBrecords.
Anattackerwithread/writeaccesscouldalterWI-DBrecordsoridentifyanddeletethewatermarkfragmentlesembeddedinaVMimage.
WatermarkDetector:ThewatermarkdetectoridentiesaVMusingthewatermarkfragmentlesembeddedinthetargetVMim-agebasedonWI-DBrecords.
WhenanunauthorizedleakofaVMimageissuspected,theadministratormayperformthedetectionprocesstoidentifytheVMimageanditsowner.
Tadano,etal.
261TargetVMImage/var//etc//usr//home//bin/…DirectoryTreeonVM1.
ObtainthenamesoftheWatermarkFragmentFiles2.
SearchthefilesintheVMImageIDVMNameOwnerWatermarkFragmentFiles5ac8183d-e2cb-4ad2-a185-5c3beb0c17b8foo-desktopfoo/etc/yum/aaa.
conf,/var/log/dummy.
log42be8a40-5e6d-4677-84fb-e387f5638264bar-desktopbar/usr/local/bin/cmd,/etc/dummy.
conf…………WatermarkInformationDatabaseTableID:unknownFigure3.
Watermarkdetection.
Figure3illustratesthedetectionprocess.
IftheidentierofthetargetVMcanbeguessed,thewatermarkgeneratorlooksupthecorrespondingWI-DBrecord.
Otherwise,thewatermarkdetectorcomparesthewatermarkfragmentlenamesinWI-DBrecordswiththoseinthetargetVMimage.
ThewatermarkgeneratorthenoutputsacertaintyvalueoftheidentierofthetargetVMimage.
ThecertaintyvalueiscomputedasthepercentageofthenamesofthewatermarkfragmentlesintheWI-DBrecordthatmatchlenamesintheVMimage.
Notethatsomewatermarkfragmentlesmayhavebeendeletedorrenamedonpurposeorbyaccident.
3.
2WatermarkGenerationAlgorithmThissectionbrieydescribestheprocessofgeneratingthewatermarkfragmentlesforthetargetVMimage.
Thealgorithmhasvesteps.
Step1:Inputtheparametersrequiredforwatermarkgeneration.
Step2:NumberthedirectoriesinthetargetVMimageindictio-naryorder.
Step3:Selectthedirectoriestoembedwatermarkfragmentles.
Step4:Generatethenamesofthewatermarkfragmentlestobecreated.
Step5:GeneratethecontentsofthewatermarkfragmentlesforthedirectoriesselectedinStep3.
262ADVANCESINDIGITALFORENSICSVITable1.
Directorycodelist.
NumberDirectoryName1/2/etc/3/etc/init.
d/4/etc/ldap/5/etc/skel/6/etc/ssh/7/etc/sysconfig/.
.
.
.
.
.
Step1(InputParametersforWatermarkGeneration):Thefollowinginputparametersarerequiredforwatermarkgeneration:NumberofWatermarkFragmentFiles:Thelargerthenum-berofwatermarkfragmentles,themoretamper-resistantisthewatermark.
However,thisincreasesthetimerequiredtogeneratewatermarkfragmentles.
ExcludedDirectories:Somedirectories(e.
g.
,temporarydirec-tories)shouldbeexcludedbecauselesinthesedirectorieschangefrequently.
ExcludedSuxes:Thesearesuxesthatshouldbeexcludedfromthenamesofthewatermarkfragmentles.
BitLength:ThebitlengthisaparameterusedbytheBlum-Blum-Shub(BBS)algorithm[4]togeneratecryptographically-sec-urepseudo-randomnumbers.
Thisparameteraectsthecomputa-tionaltimeandsecurity,andissetto1024bitsinourexperiments.
Step2(NumbertheDirectoriesintheTargetVMImage):ThewatermarkgeneratorsearchesallthedirectoriesinthetargetVMimagerecursivelyandgeneratesa"directorycodelist"(Table1).
TheexcludeddirectoriesidentiedinStep1arenotnumbered.
ThedirectorycodeofatemplateVMimagecanbereusedwhennewwatermarkedVMimagesarecreatedfromthesametemplateVMimagebecausetheyhavethesamedirectorytreestructure.
Thisreducestheprocessingtime.
Step3(SelectDirectoriestoEmbedWatermarkFragmentFiles):Thewatermarkgeneratorproducespseudo-randomnumbersforthewatermarkfragmentlesinputinStep1.
ThevaluesoftheTadano,etal.
263randomnumbersarelimitedtotherangeofdirectorycodes.
Thewa-termarkgeneratorextractsthenamesofdirectoriescorrespondingtothegeneratedrandomnumbersusingthedirectorycodelistgeneratedinStep2.
TheBBSpseudo-randomnumbergenerationalgorithmisusedtomaketherandomnumbersdicultforanattackertopredict.
Althoughthisalgorithmiscomputationallyintensive,theexperimentalresultspresentedinSection4.
2indicatethattheoverallperformanceofthewatermarkingschemeisacceptable.
Step4(GeneratetheNamesofWatermarkFragmentFiles):ThewatermarkgeneratorcreatesthenamesofthewatermarkfragmentlesthatareembeddedinthedirectoriesselectedinStep3.
Portionsofthenamesofpre-existinglesinthedirectoriesaremodiedtocreatelenamesthataresimilartothoseofthepre-existingles.
Alenameisgeneratedaccordingtothefollowingsteps.
Step4.
1:Getthenamesofexistinglesinthetargetdirectory.
Onlyregularles(notsubdirectories,hiddenles,etc.
)whosesuxesarenottobeexcludedareretrieved.
Step4.
2:Enumerateallthesubstringscorrespondingtothelenames.
Eachsubstringisobtainedfromthehead(i.
e.
,notinclud-ingthesux)ofalenameretrievedinStep4.
1.
Theresultofthisstepistheunionofsubstringsforallthelenames.
Forexam-ple,ifthetargetdirectoryhasalenamedabc.
txt,thepossiblesubstringsare:abc,abanda.
Step4.
3:Compute"similaritygroups"foreachextractedsub-string.
Asimilaritygroupisagroupoflesinthetargetdirectorythatmeetsthefollowingconditions:(i)thelenamestartswiththesubstring(prex)generatedinStep4.
2;(ii)alltheleshavethecommonsux(e.
g.
,.
txt);and(iii)asimilaritygroupcon-tainsatleasttwoles.
Forexample,iftherearevelesinatargetdirectory{s1.
txt,s2.
txt,s3.
dat,s4.
dat,s5.
conf}andsisthesubstring,thentwosimilaritygroupscanbecomputed:{s1.
txt,s2.
txt}and{s3.
dat,s4.
dat}.
Step4.
4:ComputetheDsimscoreforeachsimilaritygroup:Dsim=c1lp+c2nfc3ldwherelpisthelengthoftheprexofthesimilaritygroup;nfisthenumberoflesinthesimilaritygroup;ldisthemeanvalueofthedierencebetweenthelengthofthelename(excludingthe264ADVANCESINDIGITALFORENSICSVIsux)andlpinthesimilaritygroup;andc1,c2,c3areparametersthataresettoone.
ThesimilaritygroupwiththehighestDsimscoreiscalledthe"prototypelegroup.
"Step4.
5:Createthenameofthenewwatermarkfragmentle.
Oneormorerandomlettersareaddedtothetailoftheprexoftheselectedprototypelegroup.
Thelengthoftheaddedlet-ters(lt)isthelengthofthelenamerandomlyselectedfromtheprototypelegroup(excludingthesuxandprex).
Finally,thesuxofthelesintheprototypelegroupisaddedtothelename.
Forexample,iftheprexissampleandtheprototypelegroupis{sample.
dat,sample-bak.
dat}andifsample-bak.
datisselected,thenlt=4andapossiblenameissampledbha.
dat.
Step5(GeneratetheContentoftheWatermarkFragmentFiles):Thewatermarkgeneratorcreatesthecontentandattributescorrespondingtoeachwatermarkfragmentle.
Thecontentofawater-markfragmentleisarandomly-generatedbytesequence.
Attributesofawatermarkfragmentlearedeterminedaccordingtothefollowingrules.
Fortimestamps(creation/modication/access)andlesize,thewatermarkgeneratorassignsthemeanvaluesofthelesintheprototypelegrouptothenewwatermarkfragmentle.
Forotherattributessuchasownershipandpermission,thevaluescorrespondingtoarandomlyselectedleintheprototypelegroupareused.
3.
3ImplementationThedigitalwatermarkingschemewasimplementedinJava1.
5.
TheVMwareServervirtualizationsoftwarewasemployed.
Thecommandvmware-mount.
plwasissuedtotheVMwareServertomountthelesystemontheVMimageforembeddingwatermarkfragmentles.
TheVMimageofanylesystemoroperatingsystem,includingWindowsandLinux,canbewatermarked.
TheWI-DBwasimplementedusingMySQL5.
0.
4.
ExperimentalSetupandResultsThissectiondescribestheexperimentalsetupusedtoevaluatethewa-termarkingalgorithm.
Also,itpresentstheexperimentalresultsrelatedtowatermarkgenerationanddetection.
4.
1ExperimentalSetupAtestenvironmentwascreatedtoevaluatetheperformanceofthewatermarkingscheme.
Theenvironmentincludedonephysicalhost(Ta-Tadano,etal.
265Table2.
Testenvironment.
PhysicalHostCPUPentium41.
73GHzProcessorMemory1GBRAMHostOSUbuntuLinux8.
04ServerVMMVMwareServer2.
0GuestVMsGuestOSUbuntuLinux8.
04CentOS5.
1(JeOSedition)(default)VMImageSize183MB2,750MB(.
vmdkfile)Directories1,1207,429ble2).
TwotemplateVMimagesofdierentsizeswereusedtoclarifytheimpactofsizeonthewatermarkingscheme.
TheVMimagesusedwereanUbuntuLinux8.
04ServerJeOSedition(minimumcongurationforvirtualappliances)andadefaultinstallationofCentOS5.
1.
4.
2ExperimentalResultsThissectionpresentsourexperimentalresultsrelatedtowatermarkgenerationanddetection.
WatermarkGenerationTheVMimagetemplatesofUbuntuandCentOSwerecopiedandatotalof10and100watermarkfragmentleswereembeddedinthetwoVMimages.
Eachexperimentwasrepeated10timesandtheaverageturnaroundtimeswerecalculated.
Table3.
Turnaroundtimesforwatermarkgeneration.
Av.
GenerationTime(sec)Av.
Copying10Files100FilesTime(sec)UbuntuLinux8.
0413.
12124.
0016.
903CentOS5.
1168.
382177.
270142.
284Table3presentstheturnaroundtimesforcopyingVMimagesandgeneratingwatermarks.
Theexperimentsusedpreviously-createddirec-torycodesoftemplateVMimagesbecausethecodesaregeneratedonlythersttimethatthetemplateVMimagesareused.
Theresultsin-dicatethatthetimeforwatermarkgenerationexcludingthetimefor266ADVANCESINDIGITALFORENSICSVITable4.
Generatedwatermarkfragmentles.
FileNames/usr/share/zoneinfo/Pacific/kQGidyI/etc/console-tools/v2uQizvontwL8/lib/modules/2.
6.
24-16-virtual/kernel/sound/usb/snd-usb-INc.
ko/usr/lib/klibc/bin/hso.
shared/usr/lib/perl/5.
8.
8/IO/Socket/vS9jkE.
pm/usr/lib/python2.
5/wsgiref/hG272nT.
pyc/usr/share/debconf/jAGX7mQ.
sh/usr/share/zoneinfo/Mexico/irQ7KA/usr/share/zoneinfo/posix/Chile/5XwjAcopyingisessentiallyindependentofthesizeofthetemplateVMimage.
Theturnaroundtimesdropwhenfasterstoragedevicesareemployed.
Table4liststhegeneratedwatermarkfragmentles.
Thelenamessnd-usb-INc.
koandhso.
sharedarerelativelydiculttodistinguishfromthepre-existinglesinthetargetdirectories.
Incontrast,lenamessuchaskQGidyIareeasilydistinguishable.
Ingeneral,whentherearemanylesinthetargetdirectorywhosenameshavecommonextensionsandlongcommonsubstrings,thegeneratedlename(s)tendtobeindistinguishable.
Forexample,thelesnd-usb-INc.
kobelongsto/lib/modules/2.
6.
24-16-virtual/kernel/sound/usb/whosepre-existinglesaresnd-usb-audio.
koandsnd-usb-lib.
ko.
Meanwhile,ifonlyafewlenameshavecommonsubstrings/extensionsinthetargetdirec-tory,thegeneratedlename(s)tendtobecontrived.
WatermarkDetectionWatermarkdetectionexperimentswerecon-ductedtoidentify10and100watermarkfragmentlesfromthewater-markedUbuntu8.
04andCentOS5.
1VMimages.
Table5.
Turnaroundtimesforwatermarkdetection.
Av.
DetectionTime(sec)10Files100FilesUbuntuLinux8.
047.
5247.
549CentOS5.
17.
5267.
573Table5presentstheaverageturnaroundtimesforwatermarkdetec-tionbasedontenrepetitions.
Theresultsindicatethatthetimetakentodetectthewatermarkisalmostindependentofthesizeofthewater-markedVMimageandthenumberofwatermarkfragmentles.
Tadano,etal.
2675.
ConclusionsThedigitalwatermarkingschemeforVMimagesisindependentoflesystems,leformats,operatingsystems,kernelversionsandhardware.
Also,experimentsdemonstratethatwatermarkgenerationanddetectionarebothfastandeective.
Ourfutureworkwillfocusonenhancingthetamper-resistantcharac-teristicsofthewatermarkingscheme.
SeveralattackscouldbedevisedtoremoveormodifyVMimagewatermarks.
Forexample,watermarkscouldbedetectedusingamachinelearningalgorithmsuchtextcluster-ing[9]todiscriminateembeddedlesfrompre-existinglesbasedonlenamestringfeatures.
AnotherattackcoulduseinformationfromelsewhereintheVMsuchasthei-nodenumbersofles.
Filesinstalledatagiventimeareassignedsuccessivei-nodenumbers;alewithani-nodenumberthatisoutofsequencecouldcorrespondtoanembeddedle.
Otherproblemstobeinvestigatedincludehavingthecontentsofembeddedlesresemblethoseofpre-existingles,andaugmentingtheschemewithotherdatahidingapproachestoenhancetamperresistance.
Finally,ourresearchwillinvestigatetheapplicationofthewatermarkingschemetootherdigitalcontentsuchastarandziparchives.
References[1]AmazonWebServices,AmazonElasticComputeCloud,Seattle,Washington(aws.
amazon.
com/ec2).
[2]AmazonWebServices,AmazonSimpleStorageService,Seattle,Washington(s3.
amazonaws.
com).
[3]AmazonWebServices,ec2-download-bundle,Seattle,Wash-ington(docs.
amazonwebservices.
com/AmazonEC2/dg/2006-10-01/CLTRG-ami-download-bundle.
html).
[4]L.
Blum,M.
BlumandM.
Shub,Comparisonoftwopseudo-randomnumbergenerators,inAdvancesinCryptology:Proceed-ingsofCrypto1982,D.
Chaum,R.
RivestandA.
Sherman(Eds.
),Plenum,NewYork,pp.
61–78,1982.
[5]K.
EcksteinandM.
Jahnke,Datahidinginjournalinglesystems,ProceedingsoftheFifthAnnualDigitalForensicResearchWork-shop,2005.
[6]A.
McDonaldandM.
Kuhn,StegFS:AsteganographiclesystemforLinux,ProceedingsoftheThirdInternationalWorkshoponIn-formationHiding,pp.
463–477,2000.
268ADVANCESINDIGITALFORENSICSVI[7]F.
Perez-GonzalezandJ.
Hernandez,Atutorialondigitalwater-marking,ProceedingsoftheThirty-ThirdIEEEInternationalCar-nahanConferenceonSecurityTechnology,pp.
286–292,1999.
[8]N.
QuynhandY.
Takefuji,Anovelapproachforale-systemin-tegritymonitortoolforaXenvirtualmachine,ProceedingsoftheSecondACMSymposiumonInformation,ComputerandCommu-nicationsSecurity,pp.
194–202,2007.
[9]T.
Segaran,ProgrammingCollectiveIntelligence:BuildingSmartWeb2.
0Applications,O'Reilly,Sebastopol,California,2007.
- contentsamazonec2相关文档
- 中国amazonec2
- submissionamazonec2
- focusedamazonec2
- activityamazonec2
- publiclyamazonec2
- implementedamazonec2
HostDare($33.79/年)CKVM和QKVM套餐 可选CN2 GIA线路
关于HostDare服务商在之前的文章中有介绍过几次,算是比较老牌的服务商,但是商家背景财力不是特别雄厚,算是比较小众的个人服务商。目前主流提供CKVM和QKVM套餐。前者是电信CN2 GIA,不过库存储备也不是很足,这不九月份发布新的补货库存活动,有提供九折优惠CN2 GIA,以及六五折优惠QKVM普通线路方案。这次活动截止到9月30日,不清楚商家这次库存补货多少。比如 QKVM基础的五个方案都...
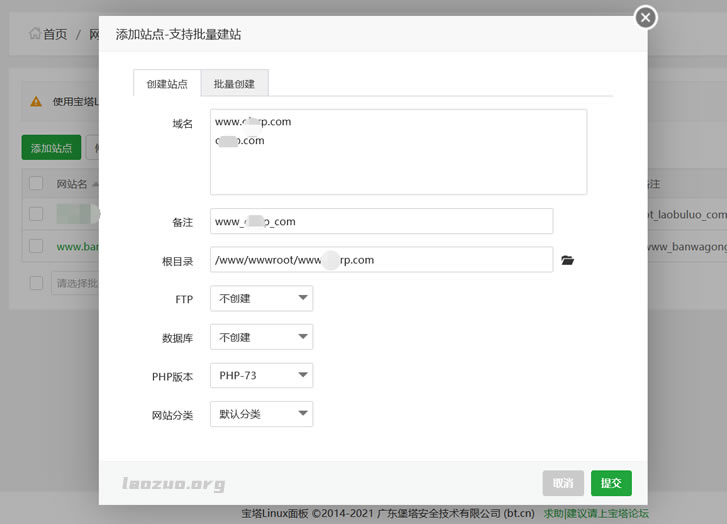
阿里云服务器绑定域名的几个流程整理
今天遇到一个网友,他之前一直在用阿里云虚拟主机,我们知道虚拟主机绑定域名是直接在面板上绑定的。这里由于他的网站项目流量比较大,虚拟主机是不够的,而且我看他虚拟主机已经有升级过。这里要说的是,用过阿里云虚拟主机的朋友可能会比较一下价格,实际上虚拟主机价格比云服务器还贵。所以,基于成本和性能的考虑,建议他选择云服务器。毕竟他的备案都接入在阿里云。这里在选择阿里云服务器后,他就蒙圈不知道如何绑定域名。这...
DMIT:香港国际线路vps,1.5GB内存/20GB SSD空间/4TB流量/1Gbps/KVM,$9.81/月
DMIT怎么样?DMIT是一家美国主机商,主要提供KVM VPS、独立服务器等,主要提供香港CN2、洛杉矶CN2 GIA等KVM VPS,稳定性、网络都很不错。支持中文客服,可Paypal、支付宝付款。2020年推出的香港国际线路的KVM VPS,大带宽,适合中转落地使用。现在有永久9折优惠码:July-4-Lite-10OFF,季付及以上还有折扣,非 中国路由优化;AS4134,AS4837 均...
amazonec2为你推荐
-
太空国家在载人航天领域排名前三的国家是什么?酒店回应名媛拼单酒店分房时出现单男单女时,怎样处理?.cn域名cn是什么域名?12306崩溃12306网站显示异常,什么原因啊云计算什么是云计算?商标注册流程及费用注册商标的程序及费用?777k7.comwww 地址 777rv怎么打不开了,还有好看的吗>com789se.com莫非现在的789mmm珍的com不管了789se.comwuwu8.com这个站长是谁?www.03ggg.comwww.tvb33.com这里好像有中国性戏观看吧??