synchronizedrewritecond
rewritecond 时间:2021-01-11 阅读:()
CopyrightIBMCorporation2010TrademarksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage1of19Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentYangChaoFengLiShengShuangYuXiaoFengFebruary02,2010Inthisarticle,wediscusstheconfigurationofaKerberos-basedsinglesign-onsolutionfromaMicrosoftWindowsdesktoptoIBMLotusConnectionsrunningonIBMWebSphereApplicationServer.
Editor'snote:KnowalotaboutthistopicWanttoshareyourexpertiseParticipateintheIBMLotussoftwarewikiprogramtoday.
LotusConnectionswikiIntroductionBeforewestartourdiscussionofconfiguringsinglesing-oninIBMLotusConnection,weneedtoreviewsomeconceptsfirst:KerberosandSPNEGO.
Kerberosisacomputernetworkauthenticationprotocol,designedanddevelopedbyMIT,whichallowsnodescommunicatingoveranonsecurenetworktoprovetheiridentitytooneanotherinasecuremanner.
Kerberosversion5authenticationprotocolisanRFC(RequestForComments)standard.
SPNEGO(SimpleandProtectedGSSAPINegotiationMechanism)isaGSSAPIpseudo-mechanismthatisusedtonegotiateoneofanumberofpossiblerealmechanisms.
ItsmostvisibleuseisinMicrosoft'sHTTPNegotiateauthenticationextension.
ThenegotiablesubmechanismsincludeNTLM(NTLANManager)andKerberos,bothusedinMicrosoftActiveDirectory.
Moreinformationcanbefoundhere.
LotusConnectionscanleveragetheWebSphereApplicationServerSPNEGOTAI(trustassociationinterceptor)toprovidethesinglesign-on(SSO)capability,enablinguserstosignontotheMicrosoftWindowsdesktopandthenbeautomaticallysignedintoLotusConnectionsfeatureswithouthavingtoauthenticate.
Figure1showstherequest/responsedataflowintheWebSphereApplicationServerSPNEGOenvironment.
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage2of19Figure1.
SPNEGOdataflowdiagramYoucanreadmoreabouttheWebSphereApplicationServerSPNEGOTAIinitsInformationCenter.
Inthisarticle,weillustratehowyoucanenableLotusConnectionstoprovidethesinglesign-on(SSO)capabilityforusersbasedonthedeploymentshowninfigure2.
Figure2.
LotusConnectionsSPNEGOdeploymenttoplogyActiveDirectoryandKerberosKDC(keydistributioncenter)aredeployedonaMicrosoftWindows2003ServerEnterpriseEditionsystem.
TheMicrosoftWindowsclientsystemistheusers'Windowsclientsystemwithbrowsersandotherapplicationsdeployed.
LotusConnections2.
5serveristheLotusConnections2.
5environmentusingActiveDirectoryastheLDAPdirectory;LotusConnections2.
5servercanbeamultiple-nodesclusteroronesingle-nodeenvironment.
Inthisarticle,wedeployLotusConnections2.
5serverontheMicrosoftWindowssystem.
PrerequisitetasksonActiveDirectoryandKerberosKDChostThereareseveralprerequisitetaskstobefinishedbythesystemadministratorsontheActiveDirectoryandKerberosKDChostbeforewecanproceed.
InstallActiveDirectoryonMicrosoftWindows2003Refertohttp://technet.
microsoft.
com/en-us/library/aa998088.
aspxonHowtoinstallActiveDirectoryonWindows2003ServerEnterpriseEdition.
AfteryouhavesuccessfullyinstalledActiveDirectory,makesurethattheKerberoskeydistributioncentersystemservicesisconfiguredcorrectlyintheServiceslist.
Double-clicktheKerberosKeyDistributionCenterservicetoselectibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage3of19theKerberosKeyDistributionCenterpropertiesasshowninfigure3.
MakesurethattheStartuptypefieldisselectedasAutomatic(Automaticisselectedbydefault).
Figure3.
KerberosKeyDistributionCenterpropertiesTheKDCserviceenablesuserstologontothenetworkusingtheKerberosV5authenticationprotocol.
Ifthisserviceisstopped,usersareunabletologontothedomainandaccessservices.
Onanon-KDC-enabledsystem(notadomaincontroller),theKDCservicestartuptypeisdisabled.
YoucanreadmoreabouttheMicrosoftWindowsKDCservice.
YoucanlearnhowtomodifytheKerberosprotocolregistryentriesandKDCconfigurationkeysinMicrosoftWindowsServer2003.
Weusethedefaultvaluesinthisconfiguration.
MakesurethatyouinstallaDNSserveronthisWindows2003systemasdetailedinstep9ofthisprocess.
OntheDNSRegistrationDiagnosticspage,followthesesteps:1.
ClickInstallandconfiguretheDNSserveronthiscomputer.
2.
SetthiscomputertousethisDNSserverasitspreferredDNSserver.
3.
ClickNext.
4.
TheDNSservicerunsonthisMicrosoftWindows2003Server.
Double-clicktheDNSServerservicetoselecttheDNSServerpropertiesasshowninfigure4.
MakesurethattheStartuptypefieldisselectedasAutomatic(Automaticisselectedbydefault).
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage4of19Figure4.
DNSServerPropertieswindowTimesynchronizationfortheKerberosenvironmentTheMicrosoftWindowsServer2003hostingActiveDirectoryisusedasthedomaincontroller.
Iftimesynchronizationisnotaprobleminyourenterpriseintranet,youcanignorethissection.
Kerberosrequiresthattheclocksoftheinvolvedhostsaresynchronized.
Theticketshaveatimeavailabilityperiod,andifthehostclockisnotsynchronizedwiththeKerberosserverclock,theauthenticationfails.
WeoftenusethedomaincontrollerasthetimeserverandruntheWindowsScheduletaskontheinvolvedLotusConnectionsserverhoststodotimesynchronizationwiththedomaincontroller.
Figure5showsanexampletaskthatinvokesthesampleTimeSyn.
bateveryminute.
Figure5.
WindowsScheduledTasksfortimesynchronizationInourexample,usersneedtocreateabatchfilenamedTimeSyn.
batinC:\.
Ifexample.
yourdomain.
comisthedomaincontrollerandanNTPtimeserver,theTimeSyn.
batlookslikethecodeshowninlisting1.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage5of19Listing1.
SamplecodeforTimeSyn.
batw32tm/config/manualpeerlist:acme.
yourdomain.
com.
com,0x8/syncfromflags:MANUALnetstopw32timenetstartw32timew32tm/resyncInstallMicrosoftWindowssupporttoolsInstallMicrosoftWindowssupporttoolsontheWindows2003ServerEnterpriseEdition.
YouneedthistooltorunthektpasscommandonthedomaincontrollertosetSPNfortheserviceaccountandtogeneratethekeytabfile.
YoucangetdetailsabouthowtheKerberosprotocolworksinMicrosoftWindowsServer2003.
ConfiguretheLotusConnectionsservertosupporttheKerberosenvironment.
WhentheprerequisitetaskshavebeenfinishedwecanstarttheconfigurationontheLotusConnectionsserver.
ConfigureLotusConnectionstouseActiveDirectoryasauserrepositoryRefertotheLotusConnectionsInformationCentertolearnhowtoconfigurethesecuritytouseActiveDirectoryasauserrepositoryandhowtopopulatetheProfilesdatabase.
CreateaserviceaccounttoholdSPNinActiveDirectoryAnSPN(serviceprincipalname)isneededforLotusConnectionsintheKerberosenvironmenttoidentifytheLotusConnectionsserver.
AserviceaccountisneededinActiveDirectorytoholdthatSPN.
Tocreatetheserviceaccount,logintothedomaincontroller,gotoManageYourServer-DomainController(ActiveDirectory)-ManageusersandcomputersinActiveDirectory,andclickthebutton.
OntheAccountpage,makesurethatyouselecttheUsercannotchangepasswordandPasswordneverexpiresoptionsasshowninfigure6.
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage6of19Figure6.
NewuseraccountpropertiesSetSPNandgeneratethekeytabfileRunthektpasscommandonthedomaincontrollertosetSPNfortheserviceaccountandgeneratethekeytabfile:ktpass–princ-out-mapuser-mapOpset–passwhereistheKerberosserviceprincipalname.
AKerberosprincipalisdividedintothreeparts:theprimary,theinstance,andtherealm.
TheformatofatypicalKerberosprincipalisprimary/instance@REALM.
IfLotusConnectionsishostedonthesystemSVTLCSPNEGO.
cn.
example.
comandthedomainnameisCN.
EXAMPLE.
COM,theSPNisHTTP/SVTLCSPNEGO.
cn.
example.
com@CN.
EXAMPLE.
COM.
isthelocationwhereyouwanttosavethekeytabfile.
istheserviceaccountname.
isthepasswordtotheserviceaccountname.
Assumethattheuseraccountcreatedinstep1islcserver01andthatthepasswordtotheserviceaccountisPassword1.
YouwanttosavethekeytabfileasC:\SVTLCSPNEGO.
keytab,sothecommandlookslikethefollowingcode:ktpass-princHTTP/SVTLCSPNEGO.
cn.
ibm.
com@CN.
IBM.
COM-outibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage7of19c:\SVTLCSPNEGO.
keytab-mapuserlcserver01-mapOpset-passPassw0rd1Thecommandoutputisshowninlisting2.
Listing2.
ktpasscommandoutputTargetingdomaincontroller:SVTLCSPNEGO.
cn.
ibm.
comUsinglegacypasswordsettingmethodSuccessfullymappedHTTP/SVTLCSPNEGO.
cn.
ibm.
comtolcserver01.
WARNING:pTypeandaccounttypedonotmatch.
Thismightcauseproblems.
Keycreated.
Outputkeytabtoc:\SVTLCSPNEGO.
keytab:Keytabversion:0x502keysize68HTTP/SVTLCSPNEGO.
cn.
ibm.
com@CN.
IBM.
COMptype0(KRB5_NT_UNKNOWN)vno4etype0x17(RC4-HMAC)keylength16(0x5858d47a41e40b40f294b3100bea611f)InaLotusConnectionscluster,youonlyneedtoselecttheIBMHTTPservernameorthevirtualhostname(usersaccesstheIBMHTTPserverorthevirtualhosttoexperienceLotusConnectionsfeatures)astheinstancenameintheKerberosserviceprincipalname.
ItisunnecessarytogeneratethekeytabfileforallnodesintheLotusConnectionscluster.
ConfigureSPNEGOTAIinWebSphereApplicationServerConfigureSPNEGOTAIintheWebSphereApplicationServeradministrativeconsolebytakingthesesteps:1.
NavigatetoSecurity-Secureadministration,applications,andinfrastructure,andexpandWebSecurity.
ClickTrustassociation.
2.
SelecttheEnabletrustassociationoptiontoenableTAI.
3.
SelectInterceptors-com.
ibm.
ws.
security.
spnego.
TrustAssociationInterceptorImpl-Customproperties.
4.
Addthecustompropertiesshowninlisting3.
Listing3.
CustompropertiesforSPNEGOTAIcom.
ibm.
ws.
security.
spnego.
SPN1.
hostName=com.
ibm.
ws.
security.
spnego.
SPN1.
NTLMTokenReceivedPage=com.
ibm.
ws.
security.
spnego.
SPN1.
spnegoNotSupportedPage=com.
ibm.
ws.
security.
spnego.
SPN1.
filter=request-url!
=/seedlist/authverify;request-url!
=/seedlist/server;request-url!
=/seedlist/myserver;request-url!
=noSPNEGOcom.
ibm.
ws.
security.
spnego.
SPN1.
filterClass=com.
ibm.
ws.
security.
spnego.
HTTPHeaderFilterwhereisthenameoftheserverwithwhichLotusConnectionsisaccessed(forexample,theIBMHTTPservernameorthevirtualhostname).
iswheretheSPNEGOTAIredirectpageiscreatedonthelocalfilesystem,forinstancefile:///Z:/share/TAIRedirect.
html.
YouneedtocreatethatHTMLfilemanually.
Thecontentisthecodeshowninlisting4.
Listing4.
SPNEGOTAIredirectpageTAIRedirect.
htmlvarorigUrl=""+document.
location;if(origUrl.
indexOf("noSPNEGO")=0)origUrl+="&noSPNEGO";elseorigUrl+="noSPNEGO";}functionredirTimer(){self.
setTimeout("self.
location.
href=origUrl;",0);}document.
write("Redirectto"+origUrl+"");5.
ClickOKtosavethechanges.
Figure7isascreencaptureofwhatdispaysinarealdeployment.
Figure7.
WebSphereadministrativeconsolescreencaptureforSPNEGOTAIcustompropertiesListing5isthesampleJACLcodethatcanfulfilltheWebSphereSPNEGOTAIsetupfromthewsadmininterface.
NamethefileasConfigTA.
jaclandrunitlikethis:wsadmin-fConfigTA.
jaclibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage9of19Remembertoreplacethecom.
ibm.
ws.
security.
spnego.
SPN1.
hostNamevaluewithyourrealconfigurationvariable.
Listing5.
ConfigTA.
jaclforWebSphereSPNEGOTAIsetupprocsaveConfig{}{globalAdminConfig$AdminConfigsave}procconfigTA{}{globalAdminConfigsettrustAssocConfigId[$AdminConfiglistTrustAssociation]settrust_attrib{}setmatchFound0settrust_assocEnabledysettrust_interceptorClassNamecom.
ibm.
ws.
security.
spnego.
TrustAssociationInterceptorImplif{$trust_assocEnabled!
={}}{if{[regexp$trust_assocEnabledy]}{lappendtrust_attrib[listenabled"true"]}else{lappendtrust_attrib[listenabled"false"]}$AdminConfigmodify$trustAssocConfigId$trust_attrib}if{$trust_interceptorClassName!
={}}{setlistOfTAI[$AdminConfiglistTAInterceptor]foreachtai$listOfTAI{setclassName[$AdminConfigshowAttribute$taiinterceptorClassName]if{[stringcompare$className$trust_interceptorClassName]==0}{setmatchFound1###break}}}if{$matchFound==1}{setinterceptorConfigId$taisettrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
hostName#replacewithyourIHShostsettrust_propertyValuesettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
filterClasssettrust_propertyValuecom.
ibm.
ws.
security.
spnego.
HTTPHeaderFiltersettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage10of19$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
filtersettrust_propertyValue"request-url!
=/seedlist/authverify;request-url!
=/seedlist/server;request-url!
=/seedlist/myserver;request-url!
=noSPNEGO"settrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
spnegoNotSupportedPagesettrust_propertyValuefile:///z:/TAIRedirect.
htmlsettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
NTLMTokenReceivedPagesettrust_propertyValuefile:///z:/TAIRedirect.
htmlsettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"}}#Mainprocedureputsstdout"Runlikethis:wsadmin-fConfigTA.
jacl"puts">configTA"configTAsaveConfigibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage11of19CreatetheKerberosconfigurationfileBeforeusingSPNEGOTAIinWebSphereApplicationServer,youneedtocreatetheKerberosconfigurationfile.
First,copythekeytabfiletotheserverwhereLotusConnectionsisinstalled.
ThenrunthecreateKrbConfigFilescriptwiththewsadmincommandlineutility,byissuingthecommandshowninlisting6.
Listing6.
wsadmincommandtocreatetheKerberosconfigurationfile$AdminTaskcreateKrbConfigFile{-krbPath\java\jre\lib\security\krb5.
conf-realm-kdcHost-dns-keytabPath}whereisthepathtotheWebSphereApplicationServerlocation,nottheLotusConnectionslocation.
istheKerberosrealmandmustbeshowninalluppercaseletters.
isthenameofthekeydistributioncenterhost.
istheDNSservername.
isthelocationofthekeytabfilegeneratedonthedomaincontroller.
EnabletheWebSphereSPNEGOTAIToenableSPNEGOTAI,logintotheWebSphereApplicationServeradministrativeconsole,andnavigatetoServers-Applicationservers.
Selecttheservername(typicallyserver1),expandJavaandProcessManagement,andselectProcessDefinition-JavaVirtualMachine-CustomProperties.
Addtwocustomproperties:com.
ibm.
ws.
security.
spnego.
isEnabled=truejava.
security.
krb5.
conf=IfyouinstallLotusConnectionsinmultipleserverinstances,youneedtorepeatthisstepforallserverinstances.
Listing7isthesampleJythoncodethatcanfulfillthetaskfromthewsadmininterface.
Namethefileasconfigspnegojvm.
pyandrunitlikethis:wsadmin-langjython-userwasadmin-passwordwasadmin-fconfigspnegojvm.
pyYour_Cell_NameYour_Node_NameYour_ServerInstance_Name.
Listing7.
configspnegojvm.
pyforenablingJVMSPNEGOcustompropertiesdefconfigspnegojvm(cellName,nodeName,serverName):globalAdminConfigkrb5conf="C:/IBM/WebSphere/AppServer/java/jre/lib/security/krb5.
conf"developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage12of19javasrv=AdminConfig.
getid("/Cell:"+cellName+"/Node:"+nodeName+"/Server:"+serverName+"/")#Checkingforexistenceofserverprint"Checkingforexistenceofserver"+serverNameiflen(javasrv)==0:print"Error--servernotfoundforname"+serverName+"::/Cell:"+cellName+"/Node:"+nodeName+"/Server:"+serverName+"/"returnelse:print"OK.
"+javasrvaddJVMCustomProperties=javaproc=AdminConfig.
list('JavaProcessDef',javasrv)prop=AdminConfig.
list('Property',javaproc)jvmp=AdminConfig.
list('JavaVirtualMachine',javaproc)if(prop.
find("com.
ibm.
ws.
security.
spnego.
isEnabled")>=0):print"INFO:JVMpropertiesseemalreadyexist:"printpropreturnAdminConfig.
create('Property',jvmp,[['name','com.
ibm.
ws.
security.
spnego.
isEnabled'],['value','true'],['required','false']])AdminConfig.
create('Property',jvmp,[['name','java.
security.
krb5.
conf'],['value',krb5conf],['required','false']])AdminConfig.
save()printCurrentJVMCustomProperties=prop=AdminConfig.
list('Property',jvmp)printprop#Main:#.
/wsadmin-langjython-userwasadmin-passwordwasadmin-fconfigspnegojvm.
pyYour_Cell_NameYour_Node_NameYour_ServerInstance_Nameif(len(sys.
argv)!
=3):print"Thisscriptrequires3parameters"print"e.
g.
:.
/wsadmin-langjython-userwasadmin-passwordwasadmin-fconfigspnegojvm.
pyYour_Cell_NameYour_Node_NameYour_ServerInstance_Name"else:cellName=sys.
argv[0]nodeName=sys.
argv[1]serverName=sys.
argv[2]print"cellName:"+cellNameprint"nodeName:"+nodeNameprint"serverName:"+serverNameprintconfigspnegojvm(cellName,nodeName,serverName)ConfiguretheAjaxproxyfortheLtpaTokencookieAddthefollowingpartintotheproxy-config.
tplfiletoconfiguretheAjaxproxytoproxyLtpaTokencookies.
Youcandothistaskwiththewsadminutilitytoextracttheconfigurationfilesfirst,addthefollowingcontent,andcheckintheconfiguration.
Youneedtorestarttheserverinstancestopickupthechanges.
Seelisting8.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage13of19Listing8.
proxy-config.
tplsettingsforAjaxproxyLtpaTokencookieJSESSIONIDLtpaTokenLtpaToken2ConfigureHTTPrewriterulestologouttoanunprotectedURISetURLrewriterulesintheIBMHTTPServerconfigurationfilenamedhttpd.
conftologouttoanunprotectedWebpage,sothatSPNEGOauthenticationdoesn'thappenagaintologintheuserautomatically.
Followthesesteps:1.
Openthehttpd.
conffileontheIBMHTTPServer,anduncommentthefollowinglines(removethe#):#LoadModulerewrite_modulemodules/mod_rewrite.
so2.
Thenaddthecodeshowninlisting9.
Listing9.
HTTPrewriterulesRewriteEngineOnRewriteCond%{REQUEST_URI}/(.
*)/ibm_security_logout(.
*)RewriteCond%{QUERY_STRING}!
=logoutExitPage=RewriteRule/(.
*)/ibm_security_logout(.
*)/$1/ibm_security_logoutlogoutExitPage=[noescape,L,R]whereistheunprotectedURLtowhichtheuserisredirectedafterlogout.
ItisanunprotectedURLtopreventSPNEGOauthentication.
BesuretoconfiguretheURLrewriteruleforbothHTTPandHTTPS.
ConfiguringtheclientbrowsertouseSPNEGOUsersneedtoconfiguretheirclientsbeforetheycanusetheLotusConnectionsservicesintheKerberosenvironment.
UserclientsystemtojointhedomainFirst,theuserclientsystemjoinsthedomain.
Theclientsystem'sDNSservervalueissetasthedomaincontrolleraddressintheTCP/IPPropertieswindowasshowninfigure8.
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage14of19Figure8.
TCP/IPPropertiesontheclientsystemNext,followthelinkhttp://support.
microsoft.
com/kb/295017tojointhedomain.
.
Aftertheclientsuccessfullyjoinsthedomain,theadministratorofthedomaincontrollercanseethenewlyjoinedmemberintheActiveDirectoryUsersandComputersviewasshowninfigure9.
Figure9.
ComputerslistbelongstothespecificdomainUserclientbrowserconfigurationSecond,usersneedtoconfiguretheirclientbrowserstouseSPNEGO.
IfyouareusingMicrosoftInternetExplorer,followthesesteps:1.
IntheInternetExplorerwindow,selectTools-InternetOptions-Security.
2.
SelecttheLocalintraneticon,andclickSites.
3.
Inthewindowthatdisplays,clickAdvanced.
IntheAddthisWebsitetothezonefield,entertheWebaddressofthehostnamesothatsinglesign-on(SSO)canbeenabledtothelistofWebsitesshownintheWebsitesfield.
4.
ClickClose,andthenclickOKtocompletethisstepandclosetheLocalintranetwindow.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage15of19Figure10.
Localintranetsettings5.
InthesectionofthewidowtitledSecuritylevelforthiszone,clickCustomLevel.
IntheSecuritySettingswindowthatdisplays,scrolltoUserAuthentication-LogonandselecttheAutomaticlogononlyinIntranetzoneoption.
ClickOKtoclosetheSecuritySettingswindow.
Seefigure11.
Figure11.
SecuritysettingsforthelocalintranetzonedeveloperWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage16of196.
IntheInternetOptionswindow,clicktheAdvancedtabandscrolltoSecuritysettings.
MakesurethattheEnableIntegratedWindowsAuthentication(requiresrestart)optionisselected.
Seefigure12.
Figure12.
InternetOptionssetting7.
ClickOK.
RestartyourInternetExplorerbrowsertoactivatethisconfiguration.
IfyouareusingtheMozillaFirefoxbrowser,followthesesteps:1.
OpenFirefox.
2.
Intheaddressfield,enterabout:config.
3.
IntheFilterfield,enternetwork.
n.
4.
Doubleclick.
negotiate-auth.
trusted-uris.
ThispreferenceliststhesitesthatarepermittedtoengageinSPNEGOauthenticationwiththebrowser.
Enteracomma-delimitedlistoftrusteddomainsorURLs.
NOTE:Youmustsetthevaluefornetwork.
negotiate-auth.
trusted-urisasshowninfigure13.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage17of19Figure13.
MozillaFirefoxbrowsersetting5.
IfthedeployedSPNEGOsolutionusestheadvancedKerberosfeatureofcredentialdelegation,double-clicknetwork.
negotiate-auth.
delegation-uris.
Thispreferenceliststhesitesforwhichthebrowsercandelegateuserauthorizationtotheserver.
Enteracomma-delimitedlistoftrusteddomainsorURLs.
6.
ClickOK.
Theconfigurationdisplaysasupdated.
7.
RestartyourFirefoxbrowsertoactivatethisconfiguration.
AccessLotusConnectionswiththesinglesign-oncapabilityintheKerberosenvironmentAfteralltasksintheprecedingstepsarefinished,userscanstarttoexperienceLotusConnectionswithsinglesign-on.
Theyneedtologontotheirsystems,andtheywillnotbechallengedwhenusingLotusConnectionsfeatures.
Figure14isascreencapturetakenfromanactualdeployment.
UserAamir_000_000logsontohisWindowsclient(whichhasjoinedthedomaincontrolledbythedomaincontroller),openstheFirefoxbrowser,enterstheLotusConnectionshomepageaddress,andlogsontoLotusConnectionsautomatically.
Figure14.
AutomaticallyloadedLotusConnectionshomepagedeveloperWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage18of19TroubleshootingIfyouhaveanyproblemswhenusingLotusConnectionsintheSPNEGOenvironment,youcanenabletracingonSPENGOandKerberosusingthesesettings:JVMcustompropertysettingcom.
ibm.
security.
jgss.
debug=allcom.
ibm.
security.
krb5.
Krb5Debug=allLogsandtracesettingcom.
ibm.
ws.
security.
*=all:com.
ibm.
ws.
security.
spnego.
*=allConclusionThisarticleintroducedtheMicrosoftWindowssinglesign-onSPNEGOconceptandconfigurationsforLotusConnections2.
5,providingdetailedexplanationsforeachconfigurationstep.
Thesamplecodelistings,whichareusefulforautomatingsystemadministrationwork,inthearticlehavebeenverifiedbythesystemtestteam.
TheconfigurationstepscanalsobeappliedtootherWebapplications.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage19of19RelatedtopicsReadtheWebSphereApplicationServerInformationCenterarticle,"Creatingasinglesign-onforHTTPrequestsusingtheSPNEGOTAI.
"RefertotheKerberosUser'sGuide.
CopyrightIBMCorporation2010(www.
ibm.
com/legal/copytrade.
shtml)Trademarks(www.
ibm.
com/developerworks/ibm/trademarks/)
Editor'snote:KnowalotaboutthistopicWanttoshareyourexpertiseParticipateintheIBMLotussoftwarewikiprogramtoday.
LotusConnectionswikiIntroductionBeforewestartourdiscussionofconfiguringsinglesing-oninIBMLotusConnection,weneedtoreviewsomeconceptsfirst:KerberosandSPNEGO.
Kerberosisacomputernetworkauthenticationprotocol,designedanddevelopedbyMIT,whichallowsnodescommunicatingoveranonsecurenetworktoprovetheiridentitytooneanotherinasecuremanner.
Kerberosversion5authenticationprotocolisanRFC(RequestForComments)standard.
SPNEGO(SimpleandProtectedGSSAPINegotiationMechanism)isaGSSAPIpseudo-mechanismthatisusedtonegotiateoneofanumberofpossiblerealmechanisms.
ItsmostvisibleuseisinMicrosoft'sHTTPNegotiateauthenticationextension.
ThenegotiablesubmechanismsincludeNTLM(NTLANManager)andKerberos,bothusedinMicrosoftActiveDirectory.
Moreinformationcanbefoundhere.
LotusConnectionscanleveragetheWebSphereApplicationServerSPNEGOTAI(trustassociationinterceptor)toprovidethesinglesign-on(SSO)capability,enablinguserstosignontotheMicrosoftWindowsdesktopandthenbeautomaticallysignedintoLotusConnectionsfeatureswithouthavingtoauthenticate.
Figure1showstherequest/responsedataflowintheWebSphereApplicationServerSPNEGOenvironment.
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage2of19Figure1.
SPNEGOdataflowdiagramYoucanreadmoreabouttheWebSphereApplicationServerSPNEGOTAIinitsInformationCenter.
Inthisarticle,weillustratehowyoucanenableLotusConnectionstoprovidethesinglesign-on(SSO)capabilityforusersbasedonthedeploymentshowninfigure2.
Figure2.
LotusConnectionsSPNEGOdeploymenttoplogyActiveDirectoryandKerberosKDC(keydistributioncenter)aredeployedonaMicrosoftWindows2003ServerEnterpriseEditionsystem.
TheMicrosoftWindowsclientsystemistheusers'Windowsclientsystemwithbrowsersandotherapplicationsdeployed.
LotusConnections2.
5serveristheLotusConnections2.
5environmentusingActiveDirectoryastheLDAPdirectory;LotusConnections2.
5servercanbeamultiple-nodesclusteroronesingle-nodeenvironment.
Inthisarticle,wedeployLotusConnections2.
5serverontheMicrosoftWindowssystem.
PrerequisitetasksonActiveDirectoryandKerberosKDChostThereareseveralprerequisitetaskstobefinishedbythesystemadministratorsontheActiveDirectoryandKerberosKDChostbeforewecanproceed.
InstallActiveDirectoryonMicrosoftWindows2003Refertohttp://technet.
microsoft.
com/en-us/library/aa998088.
aspxonHowtoinstallActiveDirectoryonWindows2003ServerEnterpriseEdition.
AfteryouhavesuccessfullyinstalledActiveDirectory,makesurethattheKerberoskeydistributioncentersystemservicesisconfiguredcorrectlyintheServiceslist.
Double-clicktheKerberosKeyDistributionCenterservicetoselectibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage3of19theKerberosKeyDistributionCenterpropertiesasshowninfigure3.
MakesurethattheStartuptypefieldisselectedasAutomatic(Automaticisselectedbydefault).
Figure3.
KerberosKeyDistributionCenterpropertiesTheKDCserviceenablesuserstologontothenetworkusingtheKerberosV5authenticationprotocol.
Ifthisserviceisstopped,usersareunabletologontothedomainandaccessservices.
Onanon-KDC-enabledsystem(notadomaincontroller),theKDCservicestartuptypeisdisabled.
YoucanreadmoreabouttheMicrosoftWindowsKDCservice.
YoucanlearnhowtomodifytheKerberosprotocolregistryentriesandKDCconfigurationkeysinMicrosoftWindowsServer2003.
Weusethedefaultvaluesinthisconfiguration.
MakesurethatyouinstallaDNSserveronthisWindows2003systemasdetailedinstep9ofthisprocess.
OntheDNSRegistrationDiagnosticspage,followthesesteps:1.
ClickInstallandconfiguretheDNSserveronthiscomputer.
2.
SetthiscomputertousethisDNSserverasitspreferredDNSserver.
3.
ClickNext.
4.
TheDNSservicerunsonthisMicrosoftWindows2003Server.
Double-clicktheDNSServerservicetoselecttheDNSServerpropertiesasshowninfigure4.
MakesurethattheStartuptypefieldisselectedasAutomatic(Automaticisselectedbydefault).
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage4of19Figure4.
DNSServerPropertieswindowTimesynchronizationfortheKerberosenvironmentTheMicrosoftWindowsServer2003hostingActiveDirectoryisusedasthedomaincontroller.
Iftimesynchronizationisnotaprobleminyourenterpriseintranet,youcanignorethissection.
Kerberosrequiresthattheclocksoftheinvolvedhostsaresynchronized.
Theticketshaveatimeavailabilityperiod,andifthehostclockisnotsynchronizedwiththeKerberosserverclock,theauthenticationfails.
WeoftenusethedomaincontrollerasthetimeserverandruntheWindowsScheduletaskontheinvolvedLotusConnectionsserverhoststodotimesynchronizationwiththedomaincontroller.
Figure5showsanexampletaskthatinvokesthesampleTimeSyn.
bateveryminute.
Figure5.
WindowsScheduledTasksfortimesynchronizationInourexample,usersneedtocreateabatchfilenamedTimeSyn.
batinC:\.
Ifexample.
yourdomain.
comisthedomaincontrollerandanNTPtimeserver,theTimeSyn.
batlookslikethecodeshowninlisting1.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage5of19Listing1.
SamplecodeforTimeSyn.
batw32tm/config/manualpeerlist:acme.
yourdomain.
com.
com,0x8/syncfromflags:MANUALnetstopw32timenetstartw32timew32tm/resyncInstallMicrosoftWindowssupporttoolsInstallMicrosoftWindowssupporttoolsontheWindows2003ServerEnterpriseEdition.
YouneedthistooltorunthektpasscommandonthedomaincontrollertosetSPNfortheserviceaccountandtogeneratethekeytabfile.
YoucangetdetailsabouthowtheKerberosprotocolworksinMicrosoftWindowsServer2003.
ConfiguretheLotusConnectionsservertosupporttheKerberosenvironment.
WhentheprerequisitetaskshavebeenfinishedwecanstarttheconfigurationontheLotusConnectionsserver.
ConfigureLotusConnectionstouseActiveDirectoryasauserrepositoryRefertotheLotusConnectionsInformationCentertolearnhowtoconfigurethesecuritytouseActiveDirectoryasauserrepositoryandhowtopopulatetheProfilesdatabase.
CreateaserviceaccounttoholdSPNinActiveDirectoryAnSPN(serviceprincipalname)isneededforLotusConnectionsintheKerberosenvironmenttoidentifytheLotusConnectionsserver.
AserviceaccountisneededinActiveDirectorytoholdthatSPN.
Tocreatetheserviceaccount,logintothedomaincontroller,gotoManageYourServer-DomainController(ActiveDirectory)-ManageusersandcomputersinActiveDirectory,andclickthebutton.
OntheAccountpage,makesurethatyouselecttheUsercannotchangepasswordandPasswordneverexpiresoptionsasshowninfigure6.
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage6of19Figure6.
NewuseraccountpropertiesSetSPNandgeneratethekeytabfileRunthektpasscommandonthedomaincontrollertosetSPNfortheserviceaccountandgeneratethekeytabfile:ktpass–princ-out-mapuser-mapOpset–passwhereistheKerberosserviceprincipalname.
AKerberosprincipalisdividedintothreeparts:theprimary,theinstance,andtherealm.
TheformatofatypicalKerberosprincipalisprimary/instance@REALM.
IfLotusConnectionsishostedonthesystemSVTLCSPNEGO.
cn.
example.
comandthedomainnameisCN.
EXAMPLE.
COM,theSPNisHTTP/SVTLCSPNEGO.
cn.
example.
com@CN.
EXAMPLE.
COM.
isthelocationwhereyouwanttosavethekeytabfile.
istheserviceaccountname.
isthepasswordtotheserviceaccountname.
Assumethattheuseraccountcreatedinstep1islcserver01andthatthepasswordtotheserviceaccountisPassword1.
YouwanttosavethekeytabfileasC:\SVTLCSPNEGO.
keytab,sothecommandlookslikethefollowingcode:ktpass-princHTTP/SVTLCSPNEGO.
cn.
ibm.
com@CN.
IBM.
COM-outibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage7of19c:\SVTLCSPNEGO.
keytab-mapuserlcserver01-mapOpset-passPassw0rd1Thecommandoutputisshowninlisting2.
Listing2.
ktpasscommandoutputTargetingdomaincontroller:SVTLCSPNEGO.
cn.
ibm.
comUsinglegacypasswordsettingmethodSuccessfullymappedHTTP/SVTLCSPNEGO.
cn.
ibm.
comtolcserver01.
WARNING:pTypeandaccounttypedonotmatch.
Thismightcauseproblems.
Keycreated.
Outputkeytabtoc:\SVTLCSPNEGO.
keytab:Keytabversion:0x502keysize68HTTP/SVTLCSPNEGO.
cn.
ibm.
com@CN.
IBM.
COMptype0(KRB5_NT_UNKNOWN)vno4etype0x17(RC4-HMAC)keylength16(0x5858d47a41e40b40f294b3100bea611f)InaLotusConnectionscluster,youonlyneedtoselecttheIBMHTTPservernameorthevirtualhostname(usersaccesstheIBMHTTPserverorthevirtualhosttoexperienceLotusConnectionsfeatures)astheinstancenameintheKerberosserviceprincipalname.
ItisunnecessarytogeneratethekeytabfileforallnodesintheLotusConnectionscluster.
ConfigureSPNEGOTAIinWebSphereApplicationServerConfigureSPNEGOTAIintheWebSphereApplicationServeradministrativeconsolebytakingthesesteps:1.
NavigatetoSecurity-Secureadministration,applications,andinfrastructure,andexpandWebSecurity.
ClickTrustassociation.
2.
SelecttheEnabletrustassociationoptiontoenableTAI.
3.
SelectInterceptors-com.
ibm.
ws.
security.
spnego.
TrustAssociationInterceptorImpl-Customproperties.
4.
Addthecustompropertiesshowninlisting3.
Listing3.
CustompropertiesforSPNEGOTAIcom.
ibm.
ws.
security.
spnego.
SPN1.
hostName=com.
ibm.
ws.
security.
spnego.
SPN1.
NTLMTokenReceivedPage=com.
ibm.
ws.
security.
spnego.
SPN1.
spnegoNotSupportedPage=com.
ibm.
ws.
security.
spnego.
SPN1.
filter=request-url!
=/seedlist/authverify;request-url!
=/seedlist/server;request-url!
=/seedlist/myserver;request-url!
=noSPNEGOcom.
ibm.
ws.
security.
spnego.
SPN1.
filterClass=com.
ibm.
ws.
security.
spnego.
HTTPHeaderFilterwhereisthenameoftheserverwithwhichLotusConnectionsisaccessed(forexample,theIBMHTTPservernameorthevirtualhostname).
iswheretheSPNEGOTAIredirectpageiscreatedonthelocalfilesystem,forinstancefile:///Z:/share/TAIRedirect.
html.
YouneedtocreatethatHTMLfilemanually.
Thecontentisthecodeshowninlisting4.
Listing4.
SPNEGOTAIredirectpageTAIRedirect.
htmlvarorigUrl=""+document.
location;if(origUrl.
indexOf("noSPNEGO")=0)origUrl+="&noSPNEGO";elseorigUrl+="noSPNEGO";}functionredirTimer(){self.
setTimeout("self.
location.
href=origUrl;",0);}document.
write("Redirectto"+origUrl+"");5.
ClickOKtosavethechanges.
Figure7isascreencaptureofwhatdispaysinarealdeployment.
Figure7.
WebSphereadministrativeconsolescreencaptureforSPNEGOTAIcustompropertiesListing5isthesampleJACLcodethatcanfulfilltheWebSphereSPNEGOTAIsetupfromthewsadmininterface.
NamethefileasConfigTA.
jaclandrunitlikethis:wsadmin-fConfigTA.
jaclibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage9of19Remembertoreplacethecom.
ibm.
ws.
security.
spnego.
SPN1.
hostNamevaluewithyourrealconfigurationvariable.
Listing5.
ConfigTA.
jaclforWebSphereSPNEGOTAIsetupprocsaveConfig{}{globalAdminConfig$AdminConfigsave}procconfigTA{}{globalAdminConfigsettrustAssocConfigId[$AdminConfiglistTrustAssociation]settrust_attrib{}setmatchFound0settrust_assocEnabledysettrust_interceptorClassNamecom.
ibm.
ws.
security.
spnego.
TrustAssociationInterceptorImplif{$trust_assocEnabled!
={}}{if{[regexp$trust_assocEnabledy]}{lappendtrust_attrib[listenabled"true"]}else{lappendtrust_attrib[listenabled"false"]}$AdminConfigmodify$trustAssocConfigId$trust_attrib}if{$trust_interceptorClassName!
={}}{setlistOfTAI[$AdminConfiglistTAInterceptor]foreachtai$listOfTAI{setclassName[$AdminConfigshowAttribute$taiinterceptorClassName]if{[stringcompare$className$trust_interceptorClassName]==0}{setmatchFound1###break}}}if{$matchFound==1}{setinterceptorConfigId$taisettrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
hostName#replacewithyourIHShostsettrust_propertyValuesettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
filterClasssettrust_propertyValuecom.
ibm.
ws.
security.
spnego.
HTTPHeaderFiltersettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage10of19$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
filtersettrust_propertyValue"request-url!
=/seedlist/authverify;request-url!
=/seedlist/server;request-url!
=/seedlist/myserver;request-url!
=noSPNEGO"settrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
spnegoNotSupportedPagesettrust_propertyValuefile:///z:/TAIRedirect.
htmlsettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"settrust_propertyNamecom.
ibm.
ws.
security.
spnego.
SPN1.
NTLMTokenReceivedPagesettrust_propertyValuefile:///z:/TAIRedirect.
htmlsettrust_propertyRequiredfalsesetoptions_attrib{}lappendoptions_attrib[listname$trust_propertyName]lappendoptions_attrib[listvalue$trust_propertyValue]lappendoptions_attrib[listrequired$trust_propertyRequired]$AdminConfigmodify$interceptorConfigId[list[listtrustProperties[list$options_attrib]]]settrustAttrs[$AdminConfigshowall$interceptorConfigId]putsstdout"trustAttrs=$trustAttrs"}}#Mainprocedureputsstdout"Runlikethis:wsadmin-fConfigTA.
jacl"puts">configTA"configTAsaveConfigibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage11of19CreatetheKerberosconfigurationfileBeforeusingSPNEGOTAIinWebSphereApplicationServer,youneedtocreatetheKerberosconfigurationfile.
First,copythekeytabfiletotheserverwhereLotusConnectionsisinstalled.
ThenrunthecreateKrbConfigFilescriptwiththewsadmincommandlineutility,byissuingthecommandshowninlisting6.
Listing6.
wsadmincommandtocreatetheKerberosconfigurationfile$AdminTaskcreateKrbConfigFile{-krbPath\java\jre\lib\security\krb5.
conf-realm-kdcHost-dns-keytabPath}whereisthepathtotheWebSphereApplicationServerlocation,nottheLotusConnectionslocation.
istheKerberosrealmandmustbeshowninalluppercaseletters.
isthenameofthekeydistributioncenterhost.
istheDNSservername.
isthelocationofthekeytabfilegeneratedonthedomaincontroller.
EnabletheWebSphereSPNEGOTAIToenableSPNEGOTAI,logintotheWebSphereApplicationServeradministrativeconsole,andnavigatetoServers-Applicationservers.
Selecttheservername(typicallyserver1),expandJavaandProcessManagement,andselectProcessDefinition-JavaVirtualMachine-CustomProperties.
Addtwocustomproperties:com.
ibm.
ws.
security.
spnego.
isEnabled=truejava.
security.
krb5.
conf=IfyouinstallLotusConnectionsinmultipleserverinstances,youneedtorepeatthisstepforallserverinstances.
Listing7isthesampleJythoncodethatcanfulfillthetaskfromthewsadmininterface.
Namethefileasconfigspnegojvm.
pyandrunitlikethis:wsadmin-langjython-userwasadmin-passwordwasadmin-fconfigspnegojvm.
pyYour_Cell_NameYour_Node_NameYour_ServerInstance_Name.
Listing7.
configspnegojvm.
pyforenablingJVMSPNEGOcustompropertiesdefconfigspnegojvm(cellName,nodeName,serverName):globalAdminConfigkrb5conf="C:/IBM/WebSphere/AppServer/java/jre/lib/security/krb5.
conf"developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage12of19javasrv=AdminConfig.
getid("/Cell:"+cellName+"/Node:"+nodeName+"/Server:"+serverName+"/")#Checkingforexistenceofserverprint"Checkingforexistenceofserver"+serverNameiflen(javasrv)==0:print"Error--servernotfoundforname"+serverName+"::/Cell:"+cellName+"/Node:"+nodeName+"/Server:"+serverName+"/"returnelse:print"OK.
"+javasrvaddJVMCustomProperties=javaproc=AdminConfig.
list('JavaProcessDef',javasrv)prop=AdminConfig.
list('Property',javaproc)jvmp=AdminConfig.
list('JavaVirtualMachine',javaproc)if(prop.
find("com.
ibm.
ws.
security.
spnego.
isEnabled")>=0):print"INFO:JVMpropertiesseemalreadyexist:"printpropreturnAdminConfig.
create('Property',jvmp,[['name','com.
ibm.
ws.
security.
spnego.
isEnabled'],['value','true'],['required','false']])AdminConfig.
create('Property',jvmp,[['name','java.
security.
krb5.
conf'],['value',krb5conf],['required','false']])AdminConfig.
save()printCurrentJVMCustomProperties=prop=AdminConfig.
list('Property',jvmp)printprop#Main:#.
/wsadmin-langjython-userwasadmin-passwordwasadmin-fconfigspnegojvm.
pyYour_Cell_NameYour_Node_NameYour_ServerInstance_Nameif(len(sys.
argv)!
=3):print"Thisscriptrequires3parameters"print"e.
g.
:.
/wsadmin-langjython-userwasadmin-passwordwasadmin-fconfigspnegojvm.
pyYour_Cell_NameYour_Node_NameYour_ServerInstance_Name"else:cellName=sys.
argv[0]nodeName=sys.
argv[1]serverName=sys.
argv[2]print"cellName:"+cellNameprint"nodeName:"+nodeNameprint"serverName:"+serverNameprintconfigspnegojvm(cellName,nodeName,serverName)ConfiguretheAjaxproxyfortheLtpaTokencookieAddthefollowingpartintotheproxy-config.
tplfiletoconfiguretheAjaxproxytoproxyLtpaTokencookies.
Youcandothistaskwiththewsadminutilitytoextracttheconfigurationfilesfirst,addthefollowingcontent,andcheckintheconfiguration.
Youneedtorestarttheserverinstancestopickupthechanges.
Seelisting8.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage13of19Listing8.
proxy-config.
tplsettingsforAjaxproxyLtpaTokencookieJSESSIONIDLtpaTokenLtpaToken2ConfigureHTTPrewriterulestologouttoanunprotectedURISetURLrewriterulesintheIBMHTTPServerconfigurationfilenamedhttpd.
conftologouttoanunprotectedWebpage,sothatSPNEGOauthenticationdoesn'thappenagaintologintheuserautomatically.
Followthesesteps:1.
Openthehttpd.
conffileontheIBMHTTPServer,anduncommentthefollowinglines(removethe#):#LoadModulerewrite_modulemodules/mod_rewrite.
so2.
Thenaddthecodeshowninlisting9.
Listing9.
HTTPrewriterulesRewriteEngineOnRewriteCond%{REQUEST_URI}/(.
*)/ibm_security_logout(.
*)RewriteCond%{QUERY_STRING}!
=logoutExitPage=RewriteRule/(.
*)/ibm_security_logout(.
*)/$1/ibm_security_logoutlogoutExitPage=[noescape,L,R]whereistheunprotectedURLtowhichtheuserisredirectedafterlogout.
ItisanunprotectedURLtopreventSPNEGOauthentication.
BesuretoconfiguretheURLrewriteruleforbothHTTPandHTTPS.
ConfiguringtheclientbrowsertouseSPNEGOUsersneedtoconfiguretheirclientsbeforetheycanusetheLotusConnectionsservicesintheKerberosenvironment.
UserclientsystemtojointhedomainFirst,theuserclientsystemjoinsthedomain.
Theclientsystem'sDNSservervalueissetasthedomaincontrolleraddressintheTCP/IPPropertieswindowasshowninfigure8.
developerWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage14of19Figure8.
TCP/IPPropertiesontheclientsystemNext,followthelinkhttp://support.
microsoft.
com/kb/295017tojointhedomain.
.
Aftertheclientsuccessfullyjoinsthedomain,theadministratorofthedomaincontrollercanseethenewlyjoinedmemberintheActiveDirectoryUsersandComputersviewasshowninfigure9.
Figure9.
ComputerslistbelongstothespecificdomainUserclientbrowserconfigurationSecond,usersneedtoconfiguretheirclientbrowserstouseSPNEGO.
IfyouareusingMicrosoftInternetExplorer,followthesesteps:1.
IntheInternetExplorerwindow,selectTools-InternetOptions-Security.
2.
SelecttheLocalintraneticon,andclickSites.
3.
Inthewindowthatdisplays,clickAdvanced.
IntheAddthisWebsitetothezonefield,entertheWebaddressofthehostnamesothatsinglesign-on(SSO)canbeenabledtothelistofWebsitesshownintheWebsitesfield.
4.
ClickClose,andthenclickOKtocompletethisstepandclosetheLocalintranetwindow.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage15of19Figure10.
Localintranetsettings5.
InthesectionofthewidowtitledSecuritylevelforthiszone,clickCustomLevel.
IntheSecuritySettingswindowthatdisplays,scrolltoUserAuthentication-LogonandselecttheAutomaticlogononlyinIntranetzoneoption.
ClickOKtoclosetheSecuritySettingswindow.
Seefigure11.
Figure11.
SecuritysettingsforthelocalintranetzonedeveloperWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage16of196.
IntheInternetOptionswindow,clicktheAdvancedtabandscrolltoSecuritysettings.
MakesurethattheEnableIntegratedWindowsAuthentication(requiresrestart)optionisselected.
Seefigure12.
Figure12.
InternetOptionssetting7.
ClickOK.
RestartyourInternetExplorerbrowsertoactivatethisconfiguration.
IfyouareusingtheMozillaFirefoxbrowser,followthesesteps:1.
OpenFirefox.
2.
Intheaddressfield,enterabout:config.
3.
IntheFilterfield,enternetwork.
n.
4.
Doubleclick.
negotiate-auth.
trusted-uris.
ThispreferenceliststhesitesthatarepermittedtoengageinSPNEGOauthenticationwiththebrowser.
Enteracomma-delimitedlistoftrusteddomainsorURLs.
NOTE:Youmustsetthevaluefornetwork.
negotiate-auth.
trusted-urisasshowninfigure13.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage17of19Figure13.
MozillaFirefoxbrowsersetting5.
IfthedeployedSPNEGOsolutionusestheadvancedKerberosfeatureofcredentialdelegation,double-clicknetwork.
negotiate-auth.
delegation-uris.
Thispreferenceliststhesitesforwhichthebrowsercandelegateuserauthorizationtotheserver.
Enteracomma-delimitedlistoftrusteddomainsorURLs.
6.
ClickOK.
Theconfigurationdisplaysasupdated.
7.
RestartyourFirefoxbrowsertoactivatethisconfiguration.
AccessLotusConnectionswiththesinglesign-oncapabilityintheKerberosenvironmentAfteralltasksintheprecedingstepsarefinished,userscanstarttoexperienceLotusConnectionswithsinglesign-on.
Theyneedtologontotheirsystems,andtheywillnotbechallengedwhenusingLotusConnectionsfeatures.
Figure14isascreencapturetakenfromanactualdeployment.
UserAamir_000_000logsontohisWindowsclient(whichhasjoinedthedomaincontrolledbythedomaincontroller),openstheFirefoxbrowser,enterstheLotusConnectionshomepageaddress,andlogsontoLotusConnectionsautomatically.
Figure14.
AutomaticallyloadedLotusConnectionshomepagedeveloperWorksibm.
com/developerWorks/Configuringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage18of19TroubleshootingIfyouhaveanyproblemswhenusingLotusConnectionsintheSPNEGOenvironment,youcanenabletracingonSPENGOandKerberosusingthesesettings:JVMcustompropertysettingcom.
ibm.
security.
jgss.
debug=allcom.
ibm.
security.
krb5.
Krb5Debug=allLogsandtracesettingcom.
ibm.
ws.
security.
*=all:com.
ibm.
ws.
security.
spnego.
*=allConclusionThisarticleintroducedtheMicrosoftWindowssinglesign-onSPNEGOconceptandconfigurationsforLotusConnections2.
5,providingdetailedexplanationsforeachconfigurationstep.
Thesamplecodelistings,whichareusefulforautomatingsystemadministrationwork,inthearticlehavebeenverifiedbythesystemtestteam.
TheconfigurationstepscanalsobeappliedtootherWebapplications.
ibm.
com/developerWorks/developerWorksConfiguringsinglesign-onforIBMLotusConnectionsintheKerberosenvironmentPage19of19RelatedtopicsReadtheWebSphereApplicationServerInformationCenterarticle,"Creatingasinglesign-onforHTTPrequestsusingtheSPNEGOTAI.
"RefertotheKerberosUser'sGuide.
CopyrightIBMCorporation2010(www.
ibm.
com/legal/copytrade.
shtml)Trademarks(www.
ibm.
com/developerworks/ibm/trademarks/)
- synchronizedrewritecond相关文档
- COUNTrewritecond
- SCPRGrewritecond
- bruterewritecond
- dspacedbrewritecond
- cursesrewritecond
- addressrewritecond
DiyVM独立服务器:香港沙田服务器,5M带宽CN2线路,L5630*2/16G内存/120G SSD硬盘,499元/月
diyvm怎么样?diyvm商家VPS主机均2GB内存起步,三个地区机房可选,使用优惠码后每月69元起;DiyVM独立服务器开设在香港沙田电信机房,CN2线路,5M带宽,自动化开通上架,最低499元/月,配置是L5630*2/16G内存/120G SSD硬盘。DiyVM是一家成立于2009年的国人主机商,提供的产品包括VPS主机、独立服务器租用等,产品数据中心包括中国香港、日本大阪和美国洛杉矶等,...
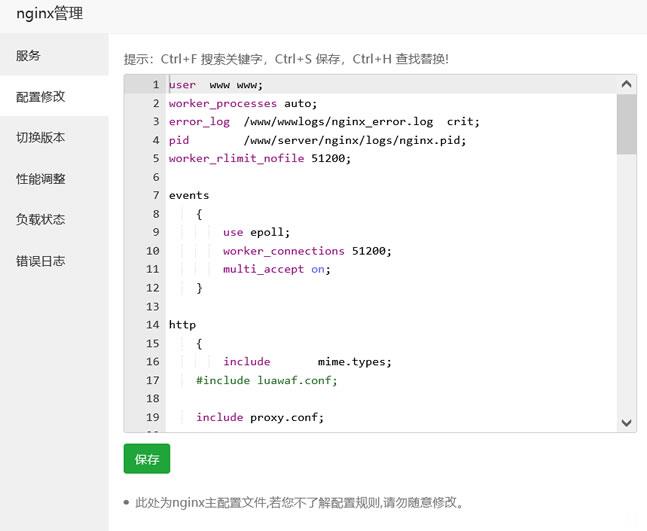
宝塔面板批量设置站点404页面
今天遇到一个网友,他在一个服务器中搭建有十几个网站,但是他之前都是采集站点数据很大,但是现在他删除数据之后希望设置可能有索引的文章给予404跳转页面。虽然他程序有默认的404页面,但是达不到他引流的目的,他希望设置统一的404页面。实际上设置还是很简单的,我们找到他是Nginx还是Apache,直接在引擎配置文件中设置即可。这里有看到他采用的是宝塔面板,直接在他的Nginx中设置。这里我们找到当前...
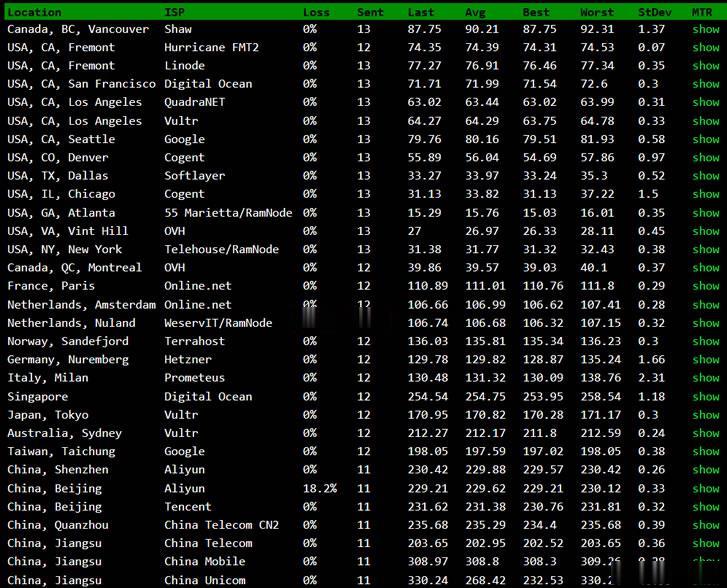
BuyVM新设立的迈阿密机房速度怎么样?简单的测评速度性能
BuyVM商家算是一家比较老牌的海外主机商,公司设立在加拿大,曾经是低价便宜VPS主机的代表,目前为止有提供纽约、拉斯维加斯、卢森堡机房,以及新增加的美国迈阿密机房。如果我们有需要选择BuyVM商家的机器需要注意的是注册信息的时候一定要规范,否则很容易出现欺诈订单,甚至你开通后都有可能被禁止账户,也是这个原因,曾经被很多人吐槽的。这里我们简单的对于BuyVM商家新增加的迈阿密机房进行简单的测评。如...
rewritecond为你推荐
-
网络域名注册什么叫做网络域名 怎么注册网络域名 以及它的收费方式域名备案查询怎么查看域名在什么空间备案的?域名购买域名购买的流程是什么?海外域名我想了解一下“国内域名”,“国外域名”以及“海外服务器”这三个方面的一些知识大连虚拟主机找个大连企业建站公司,大家给推荐一下吧。淘宝虚拟主机淘宝里卖虚拟主机、独立服务器、VPS的都是怎么进货的。windows虚拟主机虚拟机的windows和原来的windows什么关系虚拟主机排名换一台虚拟主机会影响排名吗?shopex虚拟主机西部数码虚拟主机,适合做独立shopex或者echsop网店吗,我想开网店,推荐一下哪个型号的好沈阳虚拟主机沈阳盘古网络技术有限公司的介绍