ssstrustview
trustview 时间:2021-01-28 阅读:()
RedHatEnterpriseLinux7WindowsIntegrationGuideIntegratingLinuxsystemswithActiveDirectoryenvironmentsLastUpdated:2020-08-11RedHatEnterpriseLinux7WindowsIntegrationGuideIntegratingLinuxsystemswithActiveDirectoryenvironmentsFlorianDelehayeRedHatCustomerContentServicesfdelehay@redhat.
comMarcMuehlfeldRedHatCustomerContentServicesFilipHanzelkaRedHatCustomerContentServicesLucieMaňáskováRedHatCustomerContentServicesAnetateflováPetrováRedHatCustomerContentServicesTomáapekRedHatCustomerContentServicesEllaDeonBallardRedHatCustomerContentServicesLegalNoticeCopyright2020RedHat,Inc.
ThisdocumentislicensedbyRedHatundertheCreativeCommonsAttribution-ShareAlike3.
0UnportedLicense.
Ifyoudistributethisdocument,oramodifiedversionofit,youmustprovideattributiontoRedHat,Inc.
andprovidealinktotheoriginal.
Ifthedocumentismodified,allRedHattrademarksmustberemoved.
RedHat,asthelicensorofthisdocument,waivestherighttoenforce,andagreesnottoassert,Section4dofCC-BY-SAtothefullestextentpermittedbyapplicablelaw.
RedHat,RedHatEnterpriseLinux,theShadowmanlogo,theRedHatlogo,JBoss,OpenShift,Fedora,theInfinitylogo,andRHCEaretrademarksofRedHat,Inc.
,registeredintheUnitedStatesandothercountries.
LinuxistheregisteredtrademarkofLinusTorvaldsintheUnitedStatesandothercountries.
JavaisaregisteredtrademarkofOracleand/oritsaffiliates.
XFSisatrademarkofSiliconGraphicsInternationalCorp.
oritssubsidiariesintheUnitedStatesand/orothercountries.
MySQLisaregisteredtrademarkofMySQLABintheUnitedStates,theEuropeanUnionandothercountries.
Node.
jsisanofficialtrademarkofJoyent.
RedHatisnotformallyrelatedtoorendorsedbytheofficialJoyentNode.
jsopensourceorcommercialproject.
TheOpenStackWordMarkandOpenStacklogoareeitherregisteredtrademarks/servicemarksortrademarks/servicemarksoftheOpenStackFoundation,intheUnitedStatesandothercountriesandareusedwiththeOpenStackFoundation'spermission.
Wearenotaffiliatedwith,endorsedorsponsoredbytheOpenStackFoundation,ortheOpenStackcommunity.
Allothertrademarksarethepropertyoftheirrespectiveowners.
AbstractHeterogeneousITenvironmentsoftencontainvariousdifferentdomainsandoperatingsystemsthatneedtobeabletoseamlesslycommunicate.
RedHatEnterpriseLinuxoffersmultiplewaystotightlyintegrateLinuxdomainswithActiveDirectory(AD)onMicrosoftWindows.
Theintegrationispossibleondifferentdomainobjectsthatincludeusers,groups,services,orsystems.
Thisguidealsocoversdifferentintegrationscenarios,rangingfromlightweightADpass-throughauthenticationtofull-fledgedKerberostrustedrealms.
Inadditiontothisguide,youcanfinddocumentationonotherfeaturesandservicesrelatedtoRedHatEnterpriseLinuxIdentityManagementinthefollowingguides:TheLinuxDomainIdentity,Authentication,andPolicyGuidedocumentsRedHatIdentityManagement,asolutionthatprovidesacentralizedandunifiedwaytomanageidentitystoresaswellasauthenticationandauthorizationpoliciesinaLinux-baseddomain.
TheSystem-LevelAuthenticationGuidedocumentsdifferentapplicationsandservicesavailabletoconfigureauthenticationonlocalsystems,includingtheauthconfigutility,theSystemSecurityServicesDaemon(SSSD)service,thePluggableAuthenticationModule(PAM)framework,Kerberos,thecertmongerutility,andsinglesign-on(SSO)forapplications.
TableofContentsCHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTS1.
1.
DEFININGWINDOWSINTEGRATION1.
2.
DIRECTINTEGRATION1.
3.
INDIRECTINTEGRATIONPARTI.
ADDINGASINGLELINUXSYSTEMTOANACTIVEDIRECTORYDOMAINCHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD2.
1.
HOWTHEADPROVIDERHANDLESTRUSTEDDOMAINS2.
2.
CONFIGURINGANADPROVIDERFORSSSD2.
3.
AUTOMATICKERBEROSHOSTKEYTABRENEWAL2.
4.
ENABLINGDYNAMICDNSUPDATES2.
5.
USINGRANGERETRIEVALSEARCHESWITHSSSD2.
6.
GROUPPOLICYOBJECTACCESSCONTROL2.
7.
CREATINGUSERPRIVATEGROUPSAUTOMATICALLYUSINGSSSD2.
8.
SSSDCLIENTSANDACTIVEDIRECTORYDNSSITEAUTODISCOVERY2.
9.
TROUBLESHOOTINGSSSDCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN3.
1.
SUPPORTEDDOMAINTYPESANDCLIENTS3.
2.
PREREQUISITESFORUSINGREALMD3.
3.
REALMDCOMMANDS3.
4.
DISCOVERINGANDJOININGIDENTITYDOMAINS3.
5.
REMOVINGASYSTEMFROMANIDENTITYDOMAIN3.
6.
LISTINGDOMAINS3.
7.
MANAGINGLOGINPERMISSIONSFORDOMAINUSERS3.
8.
CHANGINGDEFAULTUSERCONFIGURATION3.
9.
ADDITIONALCONFIGURATIONFORTHEACTIVEDIRECTORYDOMAINENTRYCHAPTER4.
USINGSAMBAFORACTIVEDIRECTORYINTEGRATION4.
1.
USINGWINBINDDTOAUTHENTICATEDOMAINUSERS4.
2.
USINGSMBSHARESWITHSSSDANDWINBIND4.
3.
ADDITIONALRESOURCESPARTII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:CROSS-FORESTTRUSTCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT5.
1.
INTRODUCTIONTOCROSS-FORESTTRUSTS5.
2.
CREATINGCROSS-FORESTTRUSTS5.
3.
MANAGINGANDCONFIGURINGACROSS-FORESTTRUSTENVIRONMENT5.
4.
CHANGINGTHELDAPSEARCHBASEFORUSERSANDGROUPSINATRUSTEDACTIVEDIRECTORYDOMAIN5.
5.
CHANGINGTHEFORMATOFUSERNAMESDISPLAYEDBYSSSD5.
6.
RESTRICTINGIDENTITYMANAGEMENTORSSSDTOSELECTEDACTIVEDIRECTORYSERVERSORSITESINATRUSTEDACTIVEDIRECTORYDOMAIN5.
7.
ACTIVEDIRECTORYTRUSTFORLEGACYLINUXCLIENTS5.
8.
TROUBLESHOOTINGCROSS-FORESTTRUSTSPARTIII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:SYNCHRONIZATIONCHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS6.
1.
SUPPORTEDWINDOWSPLATFORMS4457910101014141515171819202020202124252526272929293031323240638182838487899090TableofContents16.
2.
ABOUTACTIVEDIRECTORYANDIDENTITYMANAGEMENT6.
3.
ABOUTSYNCHRONIZEDATTRIBUTES6.
4.
SETTINGUPACTIVEDIRECTORYFORSYNCHRONIZATION6.
5.
MANAGINGSYNCHRONIZATIONAGREEMENTS6.
6.
MANAGINGPASSWORDSYNCHRONIZATIONCHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUST7.
1.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTAUTOMATICALLYUSINGIPA-WINSYNC-MIGRATE7.
2.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTMANUALLYUSINGIDVIEWSCHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS8.
1.
ACTIVEDIRECTORYDEFAULTTRUSTVIEW8.
2.
FIXINGIDCONFLICTS8.
3.
USINGIDVIEWSTODEFINEADUSERATTRIBUTES8.
4.
MIGRATINGNISDOMAINSTOIDM8.
5.
CONFIGURATIONOPTIONSFORUSINGSHORTNAMESTORESOLVEANDAUTHENTICATEUSERSANDGROUPSAPPENDIXA.
REVISIONHISTORY90939697104109109110112112113114114115118WindowsIntegrationGuide2TableofContents3CHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTSITenvironmentshaveastructure.
Thesystemsinthemarearrangedwithapurpose.
Integratingtwoseparateinfrastructuresrequiresanassessmentofthepurposeofeachofthoseenvironmentsandanunderstandingofhowandwheretheyinteract.
1.
1.
DEFININGWINDOWSINTEGRATIONWindowsintegrationcanmeanverydifferentthings,dependingontherequiredinteractionbetweentheLinuxenvironmentandtheWindowsenvironment.
ItcouldmeanthatindividualLinuxsystemsareenrolledintoaWindowsdomain,itcouldmeanthataLinuxdomainisconfiguredtobeapeertotheWindowsdomain,oritcouldsimplymeanthatinformationiscopiedbetweenenvironments.
ThereareseveralpointsofcontactbetweenaWindowsdomainandLinuxsystems.
Eachofthesepointsrevolvearoundidentifyingdifferentdomainobjects(users,groups,systems,services)andtheserviceswhichareusedinthatidentification.
UserIdentitiesandAuthenticationWhereareuseraccountslocated;inacentralauthenticationsystemrunningonWindows(ADdomain)orinacentralidentityandauthenticationserverrunningonLinuxHowareusersauthenticatedonaLinuxsystem;throughalocalLinuxauthenticationsystemoracentralauthenticationsystemrunningonWindowsHowisgroupmembershipconfiguredforusersHowisthatgroupmembershipdeterminedWillusersauthenticateusingausername/passwordpair,Kerberostickets,certificates,oracombinationofmethodsPOSIXattributesarerequiredtoaccessservicesonLinuxmachines.
Howaretheseattributesstored:aretheysetintheWindowsdomain,configuredlocallyontheLinuxsystem,ordynamicallymapped(forUID/GIDnumbersandWindowsSIDs)WhatuserswillbeaccessingwhatresourcesWillWindows-definedusersaccessLinuxresourcesWillLinux-definedusersaccessWindowsresourcesInmostenvironments,theActiveDirectorydomainisthecentralhubforuserinformation,whichmeansthatthereneedstobesomewayforLinuxsystemstoaccessthatuserinformationforauthenticationrequests.
Therealquestionthenishowtoobtainthatuserinformationandhowmuchofthatinformationisavailabletoexternalsystems.
TherealsoneedstobeabalancebetweeninformationrequiredforLinuxsystems(POSIXattributes)andLinuxusers(certainapplicationadministrators)andhowthatinformationismanaged.
HostandServicePrincipalsWhatresourceswillbeaccessedWhatauthenticationprotocolsarerequiredHowwillKerberosticketsbeobtainedHowwillSSLcertificatesberequestedorverifiedWillusersneedaccesstoasingledomainortobothLinuxandWindowsdomainsDNSDomains,Queries,andNameResolutionWindowsIntegrationGuide4WhatwillbetheDNSconfigurationIsthereasingleDNSdomainAretheresubdomainsHowwillsystemhostnamesberesolvedHowwillservicediscoverybeconfiguredSecurityPoliciesWhereareaccesscontrolinstructionssetWhichadministratorsareconfiguredforeachdomainChangeManagementHowfrequentlyaresystemsaddedtothedomainIftheunderlyingconfigurationforsomethingrelatedtoWindowsintegrationischanged,forexampletheDNSservice,howarethosechangespropagatedIsconfigurationmaintainedthroughdomain-relatedtoolsoraprovisioningsystemDoestheintegrationpathrequireadditionalapplicationsorconfigurationontheWindowsserverAsimportantaswhichelementsinthedomainsareintegrated,ishowthatintegrationismaintained.
Ifaparticularinstrumentofintegrationisheavilymanual,yettheenvironmenthasalargenumberofsystemswhicharefrequentlyupdated,thenthatoneinstrumentmaynotworkforthatenvironmentfromamaintenancestandpoint.
ThefollowingsectionsoutlinethemainscenariosforintegrationwithWindows.
Indirectintegration,LinuxsystemsareconnectedtoActiveDirectorywithoutanyadditionalintermediaries.
Indirectintegration,ontheotherhand,involvesanidentityserverthatcentrallymanagesLinuxsystemsandconnectsthewholeenvironmenttoActiveDirectoryoftheserver-to-serverlevel.
1.
2.
DIRECTINTEGRATIONYouneedtwocomponentstoconnectaLinuxsystemtoActiveDirectory(AD).
Onecomponentinteractswiththecentralidentityandauthenticationsource,whichisADinthiscase.
Theothercomponentdetectsavailabledomainsandconfiguresthefirstcomponenttoworkwiththerightidentitysource.
TherearedifferentoptionsthatcanbeusedtoretrieveinformationandperformauthenticationagainstAD.
Amongthemare:NativeLDAPandKerberosPAMandNSSmodulesAmongthesemodulesarenss_ldap,pam_ldap,andpam_krb5.
AsPAMandNSSmodulesareloadedintoeveryapplicationprocess,theydirectlyaffecttheexecutionenvironment.
Withnocaching,offlinesupport,orsufficientprotectionofaccesscredentials,useofthebasicLDAPandKerberosmodulesforNSSandPAMisdiscouragedduetotheirlimitedfunctionality.
SambaWinbindSambaWinbindhadbeenatraditionalwayofconnectingLinuxsystemstoAD.
WinbindemulatesaWindowsclientonaLinuxsystemandisabletocommunicatetoADservers.
Notethat:CHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTS5TheWinbindservicemustberunningifyouconfiguredSambaasadomainmember.
DirectintegrationwithWinbindinamulti-forestADsetuprequiresbidirectionaltrusts.
Remoteforestsmusttrustthelocalforesttoensurethattheidmap_adplug-inhandlesremoteforestuserscorrectly.
SystemSecurityServicesDaemon(SSSD)TheprimaryfunctionofSSSDistoaccessaremoteidentityandauthenticationresourcethroughacommonframeworkthatprovidescachingandofflinesupporttothesystem.
SSSDishighlyconfigurable;itprovidesPAMandNSSintegrationandadatabasetostorelocalusers,aswellascoreandextendeduserdataretrievedfromacentralserver.
SSSDistherecommendedcomponenttoconnectaLinuxsystemwithanidentityserverofyourchoice,beitActiveDirectory,IdentityManagement(IdM)inRedHatEnterpriseLinux,oranygenericLDAPorKerberosserver.
Notethat:DirectintegrationwithSSSDworksonlywithinasingleADforestbydefault.
Remoteforestsmusttrustthelocalforesttoensurethattheidmap_adplug-inhandlesremoteforestuserscorrectly.
ThemainreasontotransitionfromWinbindtoSSSDisthatSSSDcanbeusedforbothdirectandindirectintegrationandallowstoswitchfromoneintegrationapproachtoanotherwithoutsignificantmigrationcosts.
ThemostconvenientwaytoconfigureSSSDorWinbindinordertodirectlyintegrateaLinuxsystemwithADistousetherealmdservice.
Itallowscallerstoconfigurenetworkauthenticationanddomainmembershipinastandardway.
Therealmdserviceautomaticallydiscoversinformationaboutaccessibledomainsandrealmsanddoesnotrequireadvancedconfigurationtojoinadomainorrealm.
DirectintegrationisasimplewaytointroduceLinuxsystemstoADenvironment.
However,astheshareofLinuxsystemsgrows,thedeploymentsusuallyseetheneedforabettercentralizedmanagementoftheidentity-relatedpoliciessuchashost-basedaccesscontrol,sudo,orSELinuxusermappings.
Atfirst,theconfigurationoftheseaspectsoftheLinuxsystemscanbemaintainedinlocalconfigurationfiles.
Withagrowingnumberofsystemsthough,distributionandmanagementoftheconfigurationfilesiseasierwithaprovisioningsystemsuchasRedHatSatellite.
Thisapproachcreatesanoverheadofchangingtheconfigurationfilesandthendistributingthem.
Whendirectintegrationdoesnotscaleanymore,itismorebeneficialtoconsiderindirectintegrationdescribedinthenextsection.
1.
2.
1.
SupportedWindowsPlatformsfordirectintegrationYoucandirectlyintegrateyourLinuxmachinewithActiveDirectoryforeststhatusethefollowingforestanddomainfunctionallevels:Forestfunctionallevelrange:WindowsServer2008-WindowsServer2016[1]Domainfunctionallevelrange:WindowsServer2008-WindowsServer2016[1]Directintegrationhasbeentestedonthefollowingsupportedoperatingsystemsusingthementionedfunctionallevels:WindowsServer2019WindowsServer2016WindowsIntegrationGuide6WindowsServer2012R21.
3.
INDIRECTINTEGRATIONThemainadvantageoftheindirectintegrationistomanageLinuxsystemsandpoliciesrelatedtothosesystemscentrallywhileenablingusersfromActiveDirectory(AD)domainstotransparentlyaccessLinuxsystemsandservices.
Therearetwodifferentapproachestotheindirectintegration:Trust-basedsolutionTherecommendedapproachistoleverageIdentityManagement(IdM)inRedHatEnterpriseLinuxasthecentralservertocontrolLinuxsystemsandthenestablishcross-realmKerberostrustwithAD,enablingusersfromADtologontoandtousesinglesign-ontoaccessLinuxsystemsandresources.
ThissolutionusestheKerberoscapabilitytoestablishtrustsbetweendifferentidentitysources.
IdMpresentsitselftoADasaseparateforestandtakesadvantageoftheforest-leveltrustssupportedbyAD.
Incomplexenvironments,asingleIdMforestcanbeconnectedtomultipleADforests.
Thissetupenablesbetterseparationofdutiesfordifferentfunctionsintheorganization.
ADadministratorscanfocusonusersandpoliciesrelatedtouserswhileLinuxadministratorshavefullcontrolovertheLinuxinfrastructure.
Insuchacase,theLinuxrealmcontrolledbyIdMisanalogoustoanADresourcedomainorrealmbutwithLinuxsystemsinit.
NOTEInWindows,everydomainisaKerberosrealmandaDNSdomainatthesametime.
EverydomainmanagedbythedomaincontrollerneedstohaveitsowndedicatedDNSzone.
ThesameapplieswhenIdMistrustedbyADasaforest.
ADexpectsIdMtohaveitsownDNSdomain.
Forthetrustsetuptowork,theDNSdomainneedstobededicatedtotheLinuxenvironment.
Notethatintrustenvironments,IdMenablesyoutouseIDviewstoconfigurePOSIXattributesforADusersontheIdMserver.
Fordetails,see:Chapter8,UsingIDViewsinActiveDirectoryEnvironmentsSSSDClient-sideViewsintheSystem-LevelAuthenticationGuideSynchronization-basedsolutionAnalternativetoatrust-basedsolutionistoleverageusersynchronizationcapability,alsoavailableinIdMorRedHatDirectoryServer(RHDS),allowinguseraccounts(andwithRHDSalsogroupaccounts)tobesynchronizedfromADtoIdMorRHDS,butnotintheoppositedirection.
Usersynchronizationhascertainlimitations,including:duplicationofuserstheneedtosynchronizepasswords,whichrequiresaspecialcomponentonalldomaincontrollersinanADdomaintobeabletocapturepasswords,allusersmustfirstmanuallychangethemsynchronizationsupportsonlyasingledomainonlyonedomaincontrollerinADcanbeusedtosynchronizedatatooneinstanceofIdMorRHDSCHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTS7Insomeintegrationscenarios,theusersynchronizationmaybetheonlyavailableoption,butingeneral,useofthesynchronizationapproachisdiscouragedinfavorofthecross-realmtrust-basedintegration.
[1]WindowsServer2019doesnotintroduceanewfunctionallevel.
ThehighestfunctionallevelWindowsServer2019usesareWindowsServer2016.
WindowsIntegrationGuide8PARTI.
ADDINGASINGLELINUXSYSTEMTOANACTIVEDIRECTORYDOMAINPARTI.
ADDINGASINGLELINUXSYSTEMTOANACTIVEDIRECTORYDOMAIN9CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSDTheSystemSecurityServicesDaemon(SSSD)isasystemservicetoaccessremotedirectoriesandauthenticationmechanisms.
Itconnectsalocalsystem(anSSSDclient)toanexternalback-endsystem(adomain).
ThisprovidestheSSSDclientwithaccesstoidentityandauthenticationremoteservicesusinganSSSDprovider.
Forexample,theseremoteservicesinclude:anLDAPdirectory,anIdentityManagement(IdM)orActiveDirectory(AD)domain,oraKerberosrealm.
WhenusedasanidentitymanagementserviceforADintegration,SSSDisanalternativetoservicessuchasNISorWinbind.
ThischapterdescribeshowSSSDworkswithAD.
FormoredetailsonSSSD,seetheSystem-LevelAuthenticationGuide.
2.
1.
HOWTHEADPROVIDERHANDLESTRUSTEDDOMAINSThissectiondescribeshowSSSDhandlestrusteddomainsifyousetid_provider=adinthe/etc/sssd/sssd.
conffile.
SSSDonlysupportsdomainsinasingleActiveDirectoryforest.
IfSSSDrequiresaccesstomultipledomainsfrommultipleforests,considerusingIdMwithtrusts(preferred)orthewinbinddserviceinsteadofSSSD.
Bydefault,SSSDdiscoversalldomainsintheforestand,ifarequestforanobjectinatrusteddomainarrives,SSSDtriestoresolveit.
Ifthetrusteddomainsarenotreachableorgeographicallydistant,whichmakesthemslow,youcansetthead_enabled_domainsparameterin/etc/sssd/sssd.
conftolimitfromwhichtrusteddomainsSSSDresolvesobjects.
Bydefault,youmustusefully-qualifiedusernamestoresolveusersfromtrusteddomains.
2.
2.
CONFIGURINGANADPROVIDERFORSSSDTheADproviderenablesSSSDtousetheLDAPidentityproviderandtheKerberosauthenticationproviderwithoptimizationsforADenvironments.
2.
2.
1.
OverviewoftheIntegrationOptionsLinuxandWindowssystemsusedifferentidentifiersforusersandgroups:LinuxusesuserIDs(UID)andgroupIDs(GID).
SeeManagingUsersandGroupsintheSystemAdministrator'sGuide.
LinuxUIDsandGIDsarecompliantwiththePOSIXstandard.
WindowsusesecurityIDs(SID).
IMPORTANTDonotusethesameusernameinWindowsandActiveDirectory.
UsersauthenticatingtoaRedHatEnterpriseLinuxsystem,includingADusers,musthaveaUIDandGIDassigned.
Forthispurpose,SSSDprovidesthefollowingintegrationoptions:AutomaticallygeneratenewUIDsandGIDsforADusersSSSDcanusetheSIDofanADusertoalgorithmicallygeneratePOSIXIDsinaprocesscalledIDWindowsIntegrationGuide10SSSDcanusetheSIDofanADusertoalgorithmicallygeneratePOSIXIDsinaprocesscalledIDmapping.
IDmappingcreatesamapbetweenSIDsinADandIDsonLinux.
WhenSSSDdetectsanewADdomain,itassignsarangeofavailableIDstothenewdomain.
Therefore,eachADdomainhasthesameIDrangeoneverySSSDclientmachine.
WhenanADuserlogsintoanSSSDclientmachineforthefirsttime,SSSDcreatesanentryfortheuserintheSSSDcache,includingaUIDbasedontheuser'sSIDandtheIDrangeforthatdomain.
BecausetheIDsforanADuseraregeneratedinaconsistentwayfromthesameSID,theuserhasthesameUIDandGIDwhenloggingintoanyRedHatEnterpriseLinuxsystem.
SeeSection2.
2.
2,"ConfiguringanADDomainwithIDMappingasaProviderforSSSD".
NOTEWhenallclientsystemsuseSSSDtomapSIDstoLinuxIDs,themappingisconsistent.
Ifsomeclientsusedifferentsoftware,chooseoneofthefollowing:Ensurethatthesamemappingalgorithmisusedonallclients.
UseexplicitPOSIXattributes,asdescribedinUsePOSIXattributesdefinedinAD.
UsePOSIXattributesdefinedinADADcancreateandstorePOSIXattributes,suchasuidNumber,gidNumber,unixHomeDirectory,orloginShell.
WhenusingIDmappingdescribedinAutomaticallygeneratenewUIDsandGIDsforADusers,SSSDcreatesnewUIDsandGIDs,whichoverridesthevaluesdefinedinAD.
TokeeptheAD-definedvalues,youmustdisableIDmappinginSSSD.
SeeSection2.
2.
3,"ConfiguringSSSDtoUsePOSIXAttributesDefinedinAD".
2.
2.
2.
ConfiguringanADDomainwithIDMappingasaProviderforSSSDPrerequisitesMakesurethatboththeADsystemandtheLinuxsystemareproperlyconfigured:Verifytheconfigurationfornameresolution.
Inparticular,verifytheDNSSRVrecords.
Forexample,foradomainnamedad.
example.
com:ToverifytheDNSSRVLDAPrecords:#dig-tSRV_ldap.
_tcp.
ad.
example.
comToverifyADrecords:#dig-tSRV_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
comIfyoulaterconnectSSSDtoaparticularADdomaincontroller,itisnotnecessarytoverifytheDNSSRVrecords.
CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD11Verifythatsystemtimeonbothsystemsissynchronized.
ThisensuresthatKerberosisabletoworkproperly.
OpentherequiredportsonboththeLinuxsystemandallADdomaincontrollersinbothdirections:fromtheLinuxsystemtotheADdomaincontrollerandback.
Table2.
1.
PortsRequiredforDirectIntegrationofLinuxSystemsintoADUsingSSSDServicePortProtocolNotesDNS53UDPandTCPLDAP389UDPandTCPKerberos88UDPandTCPKerberos464UDPandTCPUsedbykadminforsettingandchangingapasswordLDAPGlobalCatalog3268TCPIftheid_provider=adoptionisbeingusedNTP123UDPOptionalConfiguretheLocalSystemRedHatrecommendsusingtherealmjoincommandtoconfigurethesystem.
SeeChapter3,UsingrealmdtoConnecttoanActiveDirectoryDomain.
Therealmdsuiteeditsallrequiredconfigurationfilesautomatically.
Forexample:#realmjoinad.
example.
comIfyoudonotwanttouserealmd,youcanconfigurethesystemmanually.
SeeManuallyConnectinganSSSDClienttoanActiveDirectoryDomainintheRedHatKnowledgebase.
Optional:ConfigureUserHomeDirectoriesandShellsThepam_oddjob_mkhomedir.
solibraryautomaticallycreateshomedirectorieswhenusersfirstlogintotheLinuxsystem.
Bydefault,SSSDretrievestheformatofthehomedirectoryfromtheADidentityprovider.
TocustomizethedirectoryformatonLinuxclients:1.
Openthe/etc/sssd/sssd.
conffile.
2.
Inthe[domain]section,useoneoftheseoptions:fallback_homedirsetsafallbackhomedirectoryformat,whichisusedonlyifahomedirectoryisnotdefinedinADoverride_homedirsetsahomedirectorytemplate,whichalwaysoverridesthehomedirectorydefinedinADForexample,toalwaysusetheformat/home/domain_name/user_name:WindowsIntegrationGuide12[domain/EXAMPLE][.
.
.
filetruncated.
.
.
]override_homedir=/home/%d/%uFordetails,seethesssd.
conf(5)manpage.
Bydefault,SSSDretrievesinformationaboutusershellsfromtheloginShellparameterconfiguredinAD.
TocustomizetheusershellsettingsonLinuxclients:1.
Openthe/etc/sssd/sssd.
conffile.
2.
Definetherequiredusershellsettingsusingtheseoptions:shell_fallbacksetsafallbackvalue,whichisusedonlyifnoshellsaredefinedinADoverride_shellsetsavaluethatalwaysoverridestheshelldefinedinADdefault_shellsetsadefaultshellvalueallowed_shellsandvetoed_shellssetlistsofallowedorblacklistedshellsFordetails,seethesssd.
conf(5)manpage.
LoadtheNewConfigurationRestartSSSDafterchangingtheconfigurationfile.
#systemctlrestartsssd.
serviceAdditionalResourcesSeethesssd-ldap(5)andsssd-krb5(5)manpagesforotherconfigurationoptionsforLDAPandKerberosproviders.
Seethesssd-ad(5)manpageforotherconfigurationoptionsforADproviders.
2.
2.
3.
ConfiguringSSSDtoUsePOSIXAttributesDefinedinADNOTEPreviously,theIdentityManagementforUNIXextensionwasavailabletoprovidePOSIXattributestouseraccounts.
Theextensionisnowdeprecated.
SeetheMicrosoftDeveloperNetworkfordetails.
IfyouhavebeenusingIdentityManagementforUNIX,seethisKnowledgebasearticleforanswerstofrequentlyaskedquestions.
ForoldproceduresthatreferenceIdentityManagementforUnixandtheServicesforUnixpackage,seetheseRedHatKnowledgebasearticles:ConfiguringanActiveDirectoryDomainwithPOSIXAttributesConfiguringActiveDirectoryasanLDAPDomainRecommendationsCHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD13Forbestperformance,publishthePOSIXattributestotheADglobalcatalog.
IfPOSIXattributesarenotpresentintheglobalcatalog,SSSDconnectstotheindividualdomaincontrollersdirectlyontheLDAPport.
JointheLinuxSystemtotheADDomainFollowthestepsinSection2.
2.
2,"ConfiguringanADDomainwithIDMappingasaProviderforSSSD".
DisableIDMappinginSSSD1.
Openthe/etc/sssd/sssd.
conffile.
2.
IntheADdomainsection,addtheldap_id_mapping=falsesetting.
NOTEIfyouusedtherealmutilitytojointhedomainandaddedthe--automatic-id-mapping=noswitch,therealmutilityalreadysetupSSSDwithldap_id_mapping=false.
3.
IfyoupreviouslyrequestedanyuserswiththedefaultIDmappingconfiguration,removetheSSSDcaches:rm-f/var/lib/sss/db/*SSSDwillnowusePOSIXattributesfromAD,insteadofcreatingthemlocally.
AdditionalResourcesForfurtherdetailsaboutIDmappingandtheldap_id_mappingparameter,seethesssd-ldap(8)manpage.
2.
3.
AUTOMATICKERBEROSHOSTKEYTABRENEWALSSSDautomaticallyrenewstheKerberoshostkeytabfileinanADenvironmentiftheadclipackageisinstalled.
Thedaemonchecksdailyifthemachineaccountpasswordisolderthantheconfiguredvalueandrenewsitifnecessary.
Thedefaultrenewalintervalis30days.
Tochangethedefault:1.
AddthefollowingparametertotheADproviderinyour/etc/sssd/sssd.
conffile:ad_maximum_machine_account_password_age=value_in_days2.
RestartSSSD:#systemctlrestartsssdTodisabletheautomaticKerberoshostkeytabrenewal,setad_maximum_machine_account_password_age=0.
2.
4.
ENABLINGDYNAMICDNSUPDATESADallowsitsclientstorefreshtheirDNSrecordsautomatically.
ADalsoactivelymaintainsDNSrecordsWindowsIntegrationGuide14ADallowsitsclientstorefreshtheirDNSrecordsautomatically.
ADalsoactivelymaintainsDNSrecordstomakesuretheyareupdated,includingtimingout(aging)andremoving(scavenging)inactiverecords.
DNSscavengingisnotenabledbydefaultontheADside.
SSSDallowstheLinuxsystemtoimitateaWindowsclientbyrefreshingitsDNSrecord,whichalsopreventsitsrecordfrombeingmarkedinactiveandremovedfromtheDNSrecord.
WhendynamicDNSupdatesareenabled,theclient'sDNSrecordisrefreshed:whentheidentityprovidercomesonline(always)whentheLinuxsystemreboots(always)ataspecifiedinterval(optionalconfiguration);bydefault,theADproviderupdatestheDNSrecordevery24hoursYoucansetthisbehaviortothesameintervalastheDHCPlease.
Inthiscase,theLinuxclientisrenewedaftertheleaseisrenewed.
DNSupdatesaresenttotheADserverusingKerberos/GSSAPIforDNS(GSS-TSIG).
Thismeansthatonlysecureconnectionsneedtobeenabled.
ThedynamicDNSconfigurationissetforeachdomain.
Forexample:[domain/ad.
example.
com]id_provider=adauth_provider=adchpass_provider=adaccess_provider=adldap_schema=addyndns_update=truedyndns_refresh_interval=43200dyndns_update_ptr=truedyndns_ttl=3600Fordetailsontheseoptions,seethesssd-ad(5)manpage.
2.
5.
USINGRANGERETRIEVALSEARCHESWITHSSSDSSSDsupportsAD'sSearchingUsingRangeRetrievalfeature.
Fordetailsonrangeretrievalsearches,seetheMicrosoftDeveloperNetwork.
IMPORTANTIfyousetcustomfiltersinthegrouporsearchbases,thefiltersmightnotworkwellwithverylargegroups.
2.
6.
GROUPPOLICYOBJECTACCESSCONTROLGroupPolicyisaMicrosoftWindowsfeaturethatenablesadministratorstocentrallymanagepoliciesforusersandcomputersinActiveDirectory(AD)environments.
Agrouppolicyobject(GPO)isacollectionofpolicysettingsthatarestoredonadomaincontroller(DC)andcanbeappliedtopolicytargets,suchascomputersandusers.
GPOpolicysettingsrelatedtoWindowslogonrightsarecommonlyusedtomanagecomputer-basedaccesscontrolinADenvironments.
CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD152.
6.
1.
HowSSSDWorkswithGPOAccessControlWhenyouconfigureSSSDtoapplyGPOaccesscontrol,SSSDretrievesGPOsapplicabletohostsystemsandADusers.
BasedontheretrievedGPOconfiguration,SSSDdeterminesifauserisallowedtologintoaparticularhost.
ThisenablestheadministratortodefineloginpolicieshonoredbybothLinuxandWindowsclientscentrallyontheADdomaincontroller.
IMPORTANTSecurityfilteringisafeaturethatenablesyoutofurtherlimitthescopeofGPOaccesscontroltospecificusers,groups,orhostsbylistingtheminthesecurityfilter.
However,SSSDonlysupportsusersandgroupsinthesecurityfilter.
SSSDignoreshostentriesinthesecurityfilter.
ToensurethatSSSDappliestheGPOaccesscontroltoaspecificsystem,createanewOUintheADdomain,movethesystemtotheOU,andthenlinktheGPOtothisOU.
2.
6.
2.
GPOSettingsSupportedbySSSDTable2.
2.
GPOaccesscontroloptionsretrievedbySSSDGPOoption[a]Correspondingsssd.
confoption[b]AllowlogonlocallyDenylogonlocallyad_gpo_map_interactiveAllowlogonthroughRemoteDesktopServicesDenylogonthroughRemoteDesktopServicesad_gpo_map_remote_interactiveAccessthiscomputerfromthenetworkDenyaccesstothiscomputerfromthenetworkad_gpo_map_networkAllowlogonasabatchjobDenylogonasabatchjobad_gpo_map_batchAllowlogonasaserviceDenylogonasaservicead_gpo_map_service[a]AsnamedintheGroupPolicyManagementEditoronWindows.
[b]Seethesssd-ad(5)manpagefordetailsabouttheseoptionsandforlistsofpluggableauthenticationmodule(PAM)servicestowhichtheGPOoptionsaremappedbydefault.
2.
6.
3.
ConfiguringGPO-basedAccessControlforSSSDGPO-basedaccesscontrolcanbeconfiguredinthe/etc/sssd/sssd.
conffile.
Thead_gpo_access_controloptionspecifiesthemodeinwhichtheGPO-basedaccesscontrolruns.
Itcanbesettothefollowingvalues:WindowsIntegrationGuide16ad_gpo_access_control=permissiveThepermissivevaluespecifiesthatGPO-basedaccesscontrolisevaluatedbutnotenforced;asyslogmessageisrecordedeverytimeaccesswouldbedenied.
Thisisthedefaultsetting.
ad_gpo_access_control=enforcingTheenforcingvaluespecifiesthatGPO-basedaccesscontrolisevaluatedandenforced.
ad_gpo_access_control=disabledThedisabledvaluespecifiesthatGPO-basedaccesscontrolisneitherevaluatednorenforced.
IMPORTANTBeforestartingtousetheGPO-basedaccesscontrolandsettingad_gpo_access_controltoenforcingmode,itisrecommendedtoensurethatad_gpo_access_controlissettopermissivemodeandexaminethelogs.
Byreviewingthesyslogmessages,youcantestandadjustthecurrentGPOsettingsasnecessarybeforefinallysettingtheenforcingmode.
ThefollowingparametersrelatedtotheGPO-basedaccesscontrolcanalsobespecifiedinthesssd.
conffile:Thead_gpo_map_*optionsandthead_gpo_default_rightoptionconfigurewhichPAMservicesaremappedtospecificWindowslogonrights.
ToaddaPAMservicetothedefaultlistofPAMservicesmappedtoaspecificGPOsetting,ortoremovetheservicefromthelist,usethead_gpo_map_*options.
Forexample,toremovethesuservicefromthelistofPAMservicesmappedtointeractivelogin(GPOsettingsAllowlogonlocallyandDenylogonlocally):ad_gpo_map_interactive=-suThead_gpo_cache_timeoutoptionspecifiestheintervalduringwhichsubsequentaccesscontrolrequestscanreusethefilesstoredinthecache,insteadofretrievingthemfromtheDCanew.
ForadetailedlistofavailableGPOparametersaswellastheirdescriptionsanddefaultvalues,seethesssd-ad(5)manpage.
2.
6.
4.
AdditionalResourcesFormoredetailsonconfiguringSSSDtoworkwithGPOs,seeConfigureSSSDtorespectActiveDirectorySSHorConsole/GUIGPOsinRedHatKnowledgebase.
2.
7.
CREATINGUSERPRIVATEGROUPSAUTOMATICALLYUSINGSSSDAnSSSDclientdirectlyintegratedintoADcanautomaticallycreateauserprivategroupforeveryADuserretrieved,ensuringthatitsGIDmatchestheuser'sUIDunlesstheGIDnumberisalreadytaken.
Toavoidconflicts,makesurethatnogroupswiththesameGIDsasuserUIDsexistontheserver.
TheGIDisnotstoredinAD.
ThisensuresthatADusersbenefitfromgroupfunctionality,whiletheLDAPCHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD17TheGIDisnotstoredinAD.
ThisensuresthatADusersbenefitfromgroupfunctionality,whiletheLDAPdatabasedoesnotcontainunnecessaryemptygroups.
2.
7.
1.
ActivatingtheAutomaticCreationofUserPrivateGroupsforADusersToactivatetheautomaticcreationofuserprivategroupsforADusers:1.
Editthe/etc/sssd/sssd.
conffile,addinginthe[domain/LDAP]section:auto_private_groups=true2.
Restartthesssdservice,removingthesssddatabase:#servicesssdstop;rm-rf/var/lib/sss/db/*;servicesssdstartAfterperformingthisprocedure,everyADuserhasaGIDwhichisidenticaltotheUID:#idad_user1uid=121298(ad_user1)gid=121298(ad_user1)groups=121298(ad_user1),10000(Group1)#idad_user2uid=121299(ad_user2)gid=121299(ad_user2)groups=121299(ad_user2),10000(Group1)2.
7.
2.
DeactivatingtheAutomaticCreationofUserPrivateGroupsforADusersTodeactivatetheautomaticcreationofuserprivategroupsforADusers:1.
Editthe/etc/sssd/sssd.
conffile,addinginthe[domain/LDAP]section:auto_private_groups=false2.
Restartthesssdservice,removingthesssddatabase:#servicesssdstop;rm-rf/var/lib/sss/db/*;servicesssdstartAfterperformingthisprocedure,allADusershaveanidentical,genericGID:#idad_user1uid=121298(ad_user1)gid=10000(group1)groups=10000(Group1)#idad_user2uid=121299(ad_user2)gid=10000(group1)groups=10000(Group1)2.
8.
SSSDCLIENTSANDACTIVEDIRECTORYDNSSITEAUTODISCOVERYActiveDirectoryforestscanbeverylarge,withnumerousdifferentdomaincontrollers,domainsandchilddomains,andphysicalsites.
ActiveDirectoryusestheconceptofsitestoidentifythephysicallocationforitsdomaincontrollers.
Thisenablesclientstoconnecttothedomaincontrollerthatisgeographicallyclosest,whichincreasesclientperformance.
Bydefault,SSSDclientsuseautodiscoverytofinditsADsiteandconnecttotheclosestdomaincontroller.
Theprocessconsistsofthesesteps:1.
SSSDqueriesSRVrecordsfromtheDNSserverintheADforest.
ThereturnedrecordscontainWindowsIntegrationGuide181.
SSSDqueriesSRVrecordsfromtheDNSserverintheADforest.
ThereturnedrecordscontainthenamesofDCsintheforest.
2.
SSSDsendsanLDAPpingtoeachoftheseDCs.
IfaDCdoesnotrespondwithinaconfiguredinterval,therequesttimesoutandSSSDsendstheLDAPpingtothenextone.
Iftheconnectionsucceeds,theresponsecontainsinformationabouttheADsitetheSSSDclientbelongsto.
3.
SSSDthenqueriesSRVrecordsfromtheDNSservertolocateDCswithinthesiteitbelongsto,andconnectstooneofthem.
NOTESSSDrememberstheADsiteitbelongstobydefault.
Inthisway,SSSDcansendtheLDAPpingdirectlytoaDCinthissiteduringtheautodiscoveryprocesstorefreshthesiteinformation.
Consequently,theprocedureofautodiscoveryisveryfastasnotimeoutsoccurnormally.
Ifthesitenolongerexistsortheclienthasmeanwhilebeenassignedtoadifferentsite,SSSDstartsqueryingforSRVrecordsintheforestandgoesthroughthewholeprocessagain.
Tooverridetheautodiscovery,specifytheADsitetowhichyouwanttheclienttoconnectbyusingthead_siteoptioninthe[domain]sectionofthe/etc/sssd/sssd.
conffile.
AdditionalResourcesSeethesssd-ad(5)manpagefordetailsonad_site.
ForenvironmentswithatrustbetweenIdentityManagementandActiveDirectory,seeSection5.
6,"RestrictingIdentityManagementorSSSDtoSelectedActiveDirectoryServersorSitesinaTrustedActiveDirectoryDomain".
2.
9.
TROUBLESHOOTINGSSSDFordetailsabouttroubleshootingSSSD,seetheTroubleshootingSSSDappendixintheSystem-LevelAuthenticationGuide.
CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD19CHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAINTherealmdsystemprovidesaclearandsimplewaytodiscoverandjoinidentitydomainstoachievedirectdomainintegration.
ItconfiguresunderlyingLinuxsystemservices,suchasSSSDorWinbind,toconnecttothedomain.
Chapter2,UsingActiveDirectoryasanIdentityProviderforSSSDdescribeshowtousetheSystemSecurityServicesDaemon(SSSD)onalocalsystemandActiveDirectoryasaback-endidentityprovider.
Ensuringthatthesystemisproperlyconfiguredforthiscanbeacomplextask:thereareanumberofdifferentconfigurationparametersforeachpossibleidentityproviderandforSSSDitself.
Inaddition,alldomaininformationmustbeavailableinadvanceandthenproperlyformattedintheSSSDconfigurationforSSSDtointegratethelocalsystemwithAD.
Therealmdsystemsimplifiesthatconfiguration.
ItcanrunadiscoverysearchtoidentifyavailableADandIdentityManagementdomainsandthenjointhesystemtothedomain,aswellassetuptherequiredclientservicesusedtoconnecttothegivenidentitydomainandmanageuseraccess.
Additionally,becauseSSSDasanunderlyingservicesupportsmultipledomains,realmdcandiscoverandsupportmultipledomainsaswell.
3.
1.
SUPPORTEDDOMAINTYPESANDCLIENTSTherealmdsystemsupportsthefollowingdomaintypes:MicrosoftActiveDirectoryRedHatEnterpriseLinuxIdentityManagementThefollowingdomainclientsaresupportedbyrealmd:SSSDforbothRedHatEnterpriseLinuxIdentityManagementandMicrosoftActiveDirectoryWinbindforMicrosoftActiveDirectory3.
2.
PREREQUISITESFORUSINGREALMDTousetherealmdsystem,installtherealmdpackage.
#yuminstallrealmdInaddition,makesurethattheoddjob,oddjob-mkhomedir,sssd,andadclipackagesareinstalled.
Thesepackagesarerequiredtobeabletomanagethesystemusingrealmd.
NOTEAsmentionedinSection3.
4,"DiscoveringandJoiningIdentityDomains",youcansimplyuserealmdtofindoutwhichpackagestoinstall.
3.
3.
REALMDCOMMANDSTherealmdsystemhastwomajortaskareas:managingsystemenrollmentinadomainWindowsIntegrationGuide20settingwhichdomainusersareallowedtoaccessthelocalsystemresourcesThecentralutilityinrealmdiscalledrealm.
Mostrealmcommandsrequiretheusertospecifytheactionthattheutilityshouldperform,andtheentity,suchasadomainoruseraccount,forwhichtoperformtheaction:realmcommandargumentsForexample:realmjoinad.
example.
comrealmpermituser_nameTable3.
1.
realmdCommandsCommandDescriptionRealmCommandsdiscoverRunadiscoveryscanfordomainsonthenetwork.
joinAddthesystemtothespecifieddomain.
leaveRemovethesystemfromthespecifieddomain.
listListallconfigureddomainsforthesystemoralldiscoveredandconfigureddomains.
LoginCommandspermitEnableaccessforspecifiedusersorforalluserswithinaconfigureddomaintoaccessthelocalsystem.
denyRestrictaccessforspecifiedusersorforalluserswithinaconfigureddomaintoaccessthelocalsystem.
Formoreinformationabouttherealmcommands,seetherealm(8)manpage.
3.
4.
DISCOVERINGANDJOININGIDENTITYDOMAINSTherealmdiscovercommandreturnscompletedomainconfigurationandalistofpackagesthatmustbeinstalledforthesystemtobeenrolledinthedomain.
Therealmjoincommandthensetsupthelocalmachineforusewithaspecifieddomainbyconfiguringboththelocalsystemservicesandtheentriesintheidentitydomain.
Theprocessrunbyrealmjoinfollowsthesesteps:1.
Runningadiscoveryscanforthespecifieddomain.
2.
Automaticinstallationofthepackagesrequiredtojointhesystemtothedomain.
ThisincludesSSSDandthePAMhomedirectoryjobpackages.
NotethattheautomaticCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN21ThisincludesSSSDandthePAMhomedirectoryjobpackages.
NotethattheautomaticinstallationofpackagesrequiresthePackageKitsuitetoberunning.
NOTEIfPackageKitisdisabled,thesystempromptsyouforthemissingpackages,andyouwillberequiredtoinstallthemmanuallyusingtheyumutility.
3.
Joiningthedomainbycreatinganaccountentryforthesysteminthedirectory.
4.
Creatingthe/etc/krb5.
keytabhostkeytabfile.
5.
ConfiguringthedomaininSSSDandrestartingtheservice.
6.
EnablingdomainusersforthesystemservicesinPAMconfigurationandthe/etc/nsswitch.
conffile.
DiscoveringDomainsWhenrunwithoutanyoptions,therealmdiscovercommanddisplaysinformationaboutthedefaultDNSdomain,whichisthedomainassignedthroughtheDynamicHostConfigurationProtocol(DHCP):#realmdiscoverad.
example.
comtype:kerberosrealm-name:AD.
EXAMPLE.
COMdomain-name:ad.
example.
comconfigured:noserver-software:active-directoryclient-software:sssdrequired-package:oddjobrequired-package:oddjob-mkhomedirrequired-package:sssdrequired-package:adclirequired-package:samba-commonItisalsopossibletorunadiscoveryforaspecificdomain.
Todothis,runrealmdiscoverandaddthenameofthedomainyouwanttodiscover:#realmdiscoverad.
example.
comTherealmdsystemwillthenuseDNSSRVlookupstofindthedomaincontrollersinthisdomainautomatically.
NOTETherealmdiscovercommandrequiresNetworkManagertoberunning;inparticular,itdependsontheD-BusinterfaceofNetworkManager.
IfyoursystemdoesnotuseNetworkManager,alwaysspecifythedomainnameintherealmdiscovercommand.
TherealmdsystemcandiscoverbothActiveDirectoryandIdentityManagementdomains.
Ifbothdomainsexistinyourenvironment,youcanlimitthediscoveryresultstoaspecifictypeofserverusingthe--server-softwareoption.
Forexample:WindowsIntegrationGuide22#realmdiscover--server-software=active-directoryOneoftheattributesreturnedinthediscoverysearchislogin-policy,whichshowsifdomainusersareallowedtologinassoonasthejoiniscomplete.
Ifloginsarenotallowedbydefault,youcanallowthemmanuallybyusingtherealmpermitcommand.
Fordetails,seeSection3.
7,"ManagingLoginPermissionsforDomainUsers".
Formoreinformationabouttherealmdiscovercommand,seetherealm(8)manpage.
JoiningaDomainIMPORTANTNotethatActiveDirectorydomainsrequireuniquecomputernamestobeused.
BothNetBIOScomputernameanditsDNShostnameshouldbeuniquelydefinedandcorrespondtoeachother.
Tojointhesystemtoanidentitydomain,usetherealmjoincommandandspecifythedomainname:#realmjoinad.
example.
comrealm:Joinedad.
example.
comdomainBydefault,thejoinisperformedasthedomainadministrator.
ForAD,theadministratoraccountiscalledAdministrator;forIdM,itiscalledadmin.
Toconnectasadifferentuser,usethe-Uoption:#realmjoinad.
example.
com-UuserThecommandfirstattemptstoconnectwithoutcredentials,butitpromptsforapasswordifrequired.
IfKerberosisproperlyconfiguredonaLinuxsystem,joiningcanalsobeperformedwithaKerberosticketforauthentication.
ToselectaKerberosprincipal,usethe-Uoption.
#kinituser#realmjoinad.
example.
com-UuserTherealmjoincommandacceptsseveralotherconfigurationoptions.
Formoreinformationabouttherealmjoincommand,seetherealm(8)manpage.
Example3.
1.
ExampleProcedureforEnrollingaSystemintoaDomain1.
Runtherealmdiscovercommandtodisplayinformationaboutthedomain.
#realmdiscoverad.
example.
comad.
example.
comtype:kerberosrealm-name:AD.
EXAMPLE.
COMdomain-name:ad.
example.
comconfigured:noserver-software:active-directoryclient-software:sssd2.
Runtherealmjoincommandandpassthedomainnametothecommand.
Providetheadministratorpasswordifthesystempromptsforit.
CHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN23#realmjoinad.
example.
comPasswordforAdministrator:passwordNotethatwhendiscoveringorjoiningadomain,realmdchecksfortheDNSSRVrecord:_ldap.
_tcp.
domain.
example.
com.
forIdentityManagementrecords_ldap.
_tcp.
dc.
_msdcs.
domain.
example.
com.
forActiveDirectoryrecordsTherecordiscreatedbydefaultwhenADisconfigured,whichenablesittobefoundbytheservicediscovery.
TestingtheSystemConfigurationafterJoiningaDomainTotestwhetherthesystemwassuccessfullyenrolledintoadomain,verifythatyoucanloginasauserfromthedomainandthattheuserinformationisdisplayedcorrectly:1.
Runtheiduser@domain_namecommandtodisplayinformationaboutauserfromthedomain.
#iduser@ad.
example.
comuid=1348601103(user@ad.
example.
com)gid=1348600513(domaingroup@ad.
example.
com)groups=1348600513(domaingroup@ad.
example.
com)2.
Usingthesshutility,loginasthesameuser.
#ssh-luser@ad.
example.
comlinux-client.
ad.
example.
comuser@ad.
example.
com@linux-client.
ad.
example.
com'spassword:Creatinghomedirectoryforuser@ad.
example.
com.
3.
Verifythatthepwdutilityprintstheuser'shomedirectory.
$pwd/home/ad.
example.
com/user4.
Verifythattheidutilityprintsthesameinformationastheiduser@domain_namecommandfromthefirststep.
$iduid=1348601103(user@ad.
example.
com)gid=1348600513(domaingroup@ad.
example.
com)groups=1348600513(domaingroup@ad.
example.
com)context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.
c1023Thekinitutilityisalsousefulwhentestingwhetherthedomainjoinwassuccessful.
Notethattousetheutility,thekrb5-workstationpackagemustbeinstalled.
3.
5.
REMOVINGASYSTEMFROMANIDENTITYDOMAINToremoveasystemfromanidentitydomain,usetherealmleavecommand.
ThecommandremovesthedomainconfigurationfromSSSDandthelocalsystem.
#realmleavead.
example.
comWindowsIntegrationGuide24Bydefault,theremovalisperformedasthedefaultadministrator.
ForAD,theadministratoraccountiscalledAdministrator;forIdM,itiscalledadmin.
Ifadifferentuserwasusedtojointothedomain,itmightberequiredtoperformtheremovalasthatuser.
Tospecifyadifferentuser,usethe-Uoption:#realmleavead.
example.
com-U'AD.
EXAMPLE.
COM\user'Thecommandfirstattemptstoconnectwithoutcredentials,butitpromptsforapasswordifrequired.
Notethatwhenaclientleavesadomain,thecomputeraccountisnotdeletedfromthedirectory;thelocalclientconfigurationisonlyremoved.
Ifyouwanttodeletethecomputeraccount,runthecommandwiththe--removeoptionspecified.
Formoreinformationabouttherealmleavecommand,seetherealm(8)manpage.
3.
6.
LISTINGDOMAINSTherealmlistcommandlistseveryconfigureddomainforthesystem,aswellasthefulldetailsanddefaultconfigurationforthatdomain.
Thisisthesameinformationasisreturnedbytherealmdiscoverycommand,onlyforadomainthatisalreadyinthesystemconfiguration.
#realmlist--all--name-onlyad.
example.
comThemostnotableoptionsacceptedbyrealmlistare:--allThe--alloptionlistsalldiscovereddomains,bothconfiguredandunconfigured.
--name-onlyThe--name-onlyoptionlimitstheresultstothedomainnamesanddoesnotdisplaythedomainconfigurationdetails.
Formoreinformationabouttherealmlistcommand,seetherealm(8)manpage.
3.
7.
MANAGINGLOGINPERMISSIONSFORDOMAINUSERSBydefault,domain-sideaccesscontrolisapplied,whichmeansthatloginpoliciesfordomainusersaredefinedinthedomainitself.
Thisdefaultbehaviorcanbeoverriddensothatclient-sideaccesscontrolisused.
Withclient-sideaccesscontrol,loginpermissionaredefinedbylocalpoliciesonly.
Ifadomainappliesclient-sideaccesscontrol,youcanusetherealmdsystemtoconfigurebasicallowordenyaccessrulesforusersfromthatdomain.
Notethattheseaccessruleseitherallowordenyaccesstoallservicesonthesystem.
Morespecificaccessrulesmustbesetonaspecificsystemresourceorinthedomain.
Tosettheaccessrules,usethefollowingtwocommands:realmdenyTherealmdenycommandsimplydeniesaccesstoalluserswithinthedomain.
Usethiscommandwiththe--alloption.
realmpermitCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN25Therealmpermitcommandcanbeusedto:grantaccesstoallusersbyusingthe--alloption,forexample:$realmpermit--allgrantaccesstospecifiedusers,forexample:$realmpermituser@example.
com$realmpermit'AD.
EXAMPLE.
COM\user'denyaccesstospecifiedusersbyusingthe-xoption,forexample:$realmpermit-x'AD.
EXAMPLE.
COM\user'Notethatallowingaccesscurrentlyonlyworksforusersinprimarydomains,notforusersintrusteddomains.
Thisisbecausewhileuserloginsmustcontainthedomainname,SSSDcurrentlycannotproviderealmdwithinformationaboutavailablechilddomains.
IMPORTANTItissafertoonlyallowaccesstospecificallyselectedusersorgroupsthantodenyaccesstosome,whileenablingittoeveryoneelse.
Therefore,itisnotrecommendedtoallowaccesstoallbydefaultwhileonlydenyingittospecifieduserswithrealmpermit-x.
Instead,RedHatrecommendstomaintainadefaultnoaccesspolicyforallusersandonlygrantaccesstoselectedusersusingrealmpermit.
Formoreinformationabouttherealmdenyandrealmpermitcommands,seetherealm(8)manpage.
3.
8.
CHANGINGDEFAULTUSERCONFIGURATIONTherealmdsystemsupportsmodifyingthedefaultuserhomedirectoryandshellPOSIXattributes.
Forexample,thismightberequiredwhensomePOSIXattributesarenotsetintheWindowsuseraccountsorwhentheseattributesaredifferentfromPOSIXattributesofotherusersonthelocalsystem.
IMPORTANTChangingtheconfigurationasdescribedinthissectiononlyworksiftherealmjoincommandhasnotbeenrunyet.
Ifasystemisalreadyjoined,changethedefaulthomedirectoryandshellinthe/etc/sssd/sssd.
conffile,asdescribedinthesectioncalled"Optional:ConfigureUserHomeDirectoriesandShells".
TooverridethedefaulthomedirectoryandshellPOSIXattributes,specifythefollowingoptionsinthe[users]sectioninthe/etc/realmd.
conffile:default-homeThedefault-homeoptionsetsatemplateforcreatingahomedirectoryforaccountsthathavenohomedirectoryexplicitlyset.
Acommonformatis/home/%d/%u,where%disthedomainnameand%uistheusername.
WindowsIntegrationGuide26default-shellThedefault-shelloptiondefinesthedefaultusershell.
Itacceptsanysupportedsystemshell.
Forexample:[users]default-home=/home/%udefault-shell=/bin/bashFormoreinformationabouttheoptions,seetherealmd.
conf(5)manpage.
3.
9.
ADDITIONALCONFIGURATIONFORTHEACTIVEDIRECTORYDOMAINENTRYCustomsettingsforeachindividualdomaincanbedefinedinthe/etc/realmd.
conffile.
Eachdomaincanhaveitsownconfigurationsection;thenameofthesectionmustmatchthedomainname.
Forexample:[ad.
example.
com]attribute=valueattribute=valueIMPORTANTChangingtheconfigurationasdescribedinthissectiononlyworksiftherealmjoincommandhasnotbeenrunyet.
Ifasystemisalreadyjoined,changingthesesettingsdoesnothaveanyeffect.
Insuchsituations,youmustleavethedomain,asdescribedinSection3.
5,"RemovingaSystemfromanIdentityDomain",andthenjoinagain,asdescribedinthesectioncalled"JoiningaDomain".
Notethatjoiningrequiresthedomainadministrator'scredentials.
Tochangetheconfigurationforadomain,editthecorrespondingsectionin/etc/realmd.
conf.
ThefollowingexampledisablesIDmappingforthead.
example.
comdomain,setsthehostprincipal,andaddsthesystemtothespecifiedsubtree:[ad.
example.
com]computer-ou=ou=LinuxComputers,DC=domain,DC=example,DC=comuser-principal=host/linux-client@AD.
EXAMPLE.
COMautomatic-id-mapping=noNotethatthesameconfigurationcanalsobesetwhenoriginallyjoiningthesystemtothedomainusingtherealmjoincommand,describedinthesectioncalled"JoiningaDomain":#realmjoin--computer-ou="ou=LinuxComputers,dc=domain,dc=com"--automatic-id-mapping=no--user-principal=host/linux-client@AD.
EXAMPLE.
COMTable3.
2,"RealmConfigurationOptions"liststhemostnotableoptionsthatcanbesetinthedomaindefaultsectionin/etc/realmd.
conf.
Forcompleteinformationabouttheavailableconfigurationoptions,seetherealmd.
conf(5)manpage.
Table3.
2.
RealmConfigurationOptionsCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN27OptionDescriptioncomputer-ouSetsthedirectorylocationforaddingcomputeraccountstothedomain.
ThiscanbethefullDNoranRDN,relativetotherootentry.
Thesubtreemustalreadyexist.
user-principalSetstheuserPrincipalNameattributevalueofthecomputeraccounttotheprovidedKerberosprincipal.
automatic-id-mappingSetswhethertoenabledynamicIDmappingordisablethemappingandusePOSIXattributesconfiguredinActiveDirectory.
WindowsIntegrationGuide28CHAPTER4.
USINGSAMBAFORACTIVEDIRECTORYINTEGRATIONSambaimplementstheServerMessageBlock(SMB)protocolinRedHatEnterpriseLinux.
TheSMBprotocolisusedtoaccessresourcesonaserver,suchasfilesharesandsharedprinters.
YoucanuseSambatoauthenticateActiveDirectory(AD)domainuserstoaDomainController(DC).
Additionally,youcanuseSambatoshareprintersandlocaldirectoriestootherSMBclientsinthenetwork.
4.
1.
USINGWINBINDDTOAUTHENTICATEDOMAINUSERSSamba'swinbinddserviceprovidesaninterfacefortheNameServiceSwitch(NSS)andenablesdomainuserstoauthenticatetoADwhenloggingintothelocalsystem.
Usingwinbinddprovidesthebenefitthatyoucanenhancetheconfigurationtosharedirectoriesandprinterswithoutinstallingadditionalsoftware.
Forfurtherdetail,seethesectionaboutSambaintheRedHatSystemAdministrator'sGuide.
4.
1.
1.
JoininganADDomainIfyouwanttojoinanADdomainandusetheWinbindservice,usetherealmjoin--client-software=winbinddomain_namecommand.
Therealmutilityautomaticallyupdatestheconfigurationfiles,suchasthoseforSamba,Kerberos,andPAM.
Forfurtherdetailsandexamples,seetheSettingupSambaasaDomainMembersectionintheRedHatSystemAdministrator'sGuide.
4.
2.
USINGSMBSHARESWITHSSSDANDWINBINDThissectiondescribeshowyoucanuseSSSDclientstoaccessandfullyusesharesbasedontheServerMessageBlock(SMB)protocol,alsoknownastheCommonInternetFileSystem(CIFS)protocol.
IMPORTANTUsingSSSDasaclientinIdMorActiveDirectorydomainshascertainlimitations,andRedHatdoesnotrecommendusingSSSDasIDmappingplug-inforWinbind.
Forfurtherdetails,seethe"WhatisthesupportstatusforSambafileserverrunningonIdMclientsordirectlyenrolledADclientswhereSSSDisusedastheclientdaemon"article.
SSSDdoesnotsupportalltheservicesthatWinbindprovides.
Forexample,SSSDdoesnotsupportauthenticationusingtheNTLANManager(NTLM)orNetBIOSnamelookup.
Ifyouneedtheseservices,useWinbind.
NotethatinIdentityManagementdomains,KerberosauthenticationandDNSnamelookupareavailableforthesamepurposes.
4.
2.
1.
HowSSSDWorkswithSMBTheSMBfile-sharingprotocoliswidelyusedonWindowsmachines.
InRedHatEnterpriseLinuxenvironmentswithatrustbetweenIdentityManagementandActiveDirectory,SSSDenablesseamlessuseofSMBasifitwasastandardLinuxfilesystem.
ToaccessaSMBshare,thesystemmustbeabletotranslateWindowsSIDstoLinuxPOSIXUIDsandGIDs.
SSSDclientsusetheSID-to-IDorSID-to-namealgorithm,whichenablesthisIDmapping.
CHAPTER4.
USINGSAMBAFORACTIVEDIRECTORYINTEGRATION294.
2.
2.
SwitchingBetweenSSSDandWinbindforSMBShareAccessThisproceduredescribeshowyoucanswitchbetweenSSSDandWinbindplug-insthatareusedforaccessingSMBsharesfromSSSDclients.
ForWinbindtobeabletoaccessSMBshares,youneedtohavethecifs-utilspackageinstalledonyourclient.
Tomakesurethatcifs-utilsisinstalledonyourmachine:$rpm-qcifs-utils1.
Optional.
FindoutwhetheryouarecurrentlyusingSSSDorWinbindtoaccessSMBsharesfromtheSSSDclient:#alternatives--displaycifs-idmap-plugincifs-idmap-plugin-statusisauto.
linkcurrentlypointsto/usr/lib/cifs-utils/cifs_idmap_sss.
so/usr/lib/cifs-utils/cifs_idmap_sss.
so-priority20/usr/lib/cifs-utils/idmapwb.
so-priority10Current`best'versionis/usr/lib/cifs-utils/cifs_idmap_sss.
so.
IftheSSSDplug-in(cifs_idmap_sss.
so)isinstalled,ithasahigherprioritythantheWinbindplug-in(idmapwb.
so)bydefault.
2.
BeforeswitchingtotheWinbindplug-in,makesureWinbindisrunningonthesystem:#systemctlis-activewinbind.
serviceactiveBeforeswitchingtotheSSSDplug-in,makesureSSSDisrunningonthesystem:#systemctlis-activesssd.
serviceactive3.
Toswitchtoadifferentplug-in,usethealternatives--setcifs-idmap-plugincommand,andspecifythepathtotherequiredplug-in.
Forexample,toswitchtoWinbind:#alternatives--setcifs-idmap-plugin/usr/lib/cifs-utils/idmapwb.
so4.
3.
ADDITIONALRESOURCESFordetailsaboutSamba,seethecorrespondingsectionintheRedHatSystemAdministrator'sGuide.
WindowsIntegrationGuide30PARTII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:CROSS-FORESTTRUSTPARTII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:CROSS-FORESTTRUST31CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENTThischapterdescribescreatingcross-foresttrustsbetweenActiveDirectoryandIdentityManagement.
Across-foresttrustistherecommendedoneofthetwomethodstointegrateIdentityManagementandActiveDirectory(AD)environmentsindirectly.
Theothermethodissynchronization.
Ifyouareunsurewhichmethodtochooseforyourenvironment,readSection1.
3,"IndirectIntegration".
Kerberosimplementsaconceptofatrust.
Inatrust,aprincipalfromoneKerberosrealmcanrequestatickettoaserviceinanotherKerberosrealm.
Usingthisticket,theprincipalcanauthenticateagainstresourcesonmachinesbelongingtotheotherrealm.
KerberosalsohastheabilitytocreatearelationshipbetweentwootherwiseseparateKerberosrealms:across-realmtrust.
Realmsthatarepartofatrustuseasharedpairofaticketandkey;amemberofonerealmthencountsasamemberofbothrealms.
RedHatIdentityManagementsupportsconfiguringacross-foresttrustbetweenanIdMdomainandanActiveDirectorydomain.
5.
1.
INTRODUCTIONTOCROSS-FORESTTRUSTSKerberosrealmonlyconcernsauthentication.
OtherservicesandprotocolsareinvolvedincomplementingidentityandauthorizationforresourcesrunningonthemachinesintheKerberosrealm.
Assuch,establishingKerberoscross-realmtrustisnotenoughtoallowusersfromonerealmtoaccessresourcesintheotherrealm;asupportisrequiredatotherlevelsofcommunicationaswell.
5.
1.
1.
TheArchitectureofaTrustRelationshipBothActiveDirectoryandIdentityManagementmanageavarietyofcoreservicessuchasKerberos,LDAP,DNS,orcertificateservices.
Totransparentlyintegratethesetwodiverseenvironments,allcoreservicesmustinteractseamlesslywithoneanother.
ActiveDirectoryTrusts,Forests,andCross-forestTrustsKerberoscross-realmtrustplaysanimportantroleinauthenticationbetweenActiveDirectoryenvironments.
AllactivitiestoresolveuserandgroupnamesinatrustedADdomainrequireauthentication,regardlessofhowaccessisperformed:usingLDAPprotocoloraspartoftheDistributedComputingEnvironment/RemoteProcedureCalls(DCE/RPC)ontopoftheServerMessageBlock(SMB)protocol.
BecausetherearemoreprotocolsinvolvedinorganizingaccessbetweentwodifferentActiveDirectorydomains,trustrelationshiphasamoregenericname,ActiveDirectorytrust.
MultipleADdomainscanbeorganizedtogetherintoanActiveDirectoryforest.
Arootdomainoftheforestisthefirstdomaincreatedintheforest.
IdentityManagementdomaincannotbepartofanexistingADforest,thusitisalwaysseenasaseparateforest.
Whentrustrelationshipisestablishedbetweentwoseparateforestrootdomains,allowingusersandservicesfromdifferentADforeststocommunicate,atrustiscalledActiveDirectorycross-foresttrust.
TrustFlowandOne-wayTrustsAtrustestablishesanaccessrelationshipbetweentwodomains.
ActiveDirectoryenvironmentscanbecomplexsotherearedifferentpossibletypesandarrangementsforActiveDirectorytrusts,betweenchilddomains,rootdomains,orforests.
Atrustisapathfromonedomaintoanother.
Thewaythatidentitiesandinformationmovebetweenthedomainsiscalledatrustflow.
Thetrusteddomaincontainsusers,andthetrustingdomainallowsaccesstoresources.
Inaone-wayWindowsIntegrationGuide32trust,trustflowsonlyinonedirection:userscanaccessthetrustingdomain'sresourcesbutusersinthetrustingdomaincannotaccessresourcesinthetrusteddomain.
InFigure5.
1,"One-wayTrust",DomainAistrustedbyDomainB,butDomainBisnottrustedbyDomainA.
Figure5.
1.
One-wayTrustIdMallowstheadministratortoconfigurebothone-wayandtwo-waytrusts.
Fordetails,seeSection5.
1.
4,"One-WayandTwo-WayTrusts".
TransitiveandNon-transitiveTrustsTrustscanbetransitivesothatadomaintrustsanotherdomainandanyotherdomaintrustedbythatseconddomain.
Figure5.
2.
TransitiveTrustsTrustscanalsobenon-transitivewhichmeansthetrustislimitedonlytotheexplicitlyincludeddomains.
Cross-forestTrustinActiveDirectoryandIdentityManagementWithinanActiveDirectoryforest,trustrelationshipsbetweendomainsarenormallytwo-wayandtransitivebydefault.
BecausetrustbetweentwoADforestsisatrustbetweentwoforestrootdomains,itcanalsobetwo-wayorone-way.
Thetransitivityofthecross-foresttrustisexplicit:anydomaintrustwithinanADforestthatleadstotherootdomainoftheforestistransitiveoverthecross-foresttrust.
However,separatecross-foresttrustsarenottransitive.
Anexplicitcross-foresttrustmustbeestablishedbetweeneachADforestrootdomaintoanotherADforestrootdomain.
FromtheperspectiveofAD,IdentityManagementrepresentsaseparateADforestwithasingleADCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT33FromtheperspectiveofAD,IdentityManagementrepresentsaseparateADforestwithasingleADdomain.
Whencross-foresttrustbetweenanADforestrootdomainandanIdMdomainisestablished,usersfromtheADforestdomainscaninteractwithLinuxmachinesandservicesfromtheIdMdomain.
Figure5.
3.
TrustDirection5.
1.
2.
ActiveDirectorySecurityObjectsandTrustActiveDirectoryGlobalCatalogTheglobalcatalogcontainsinformationaboutobjectsofanActiveDirectory.
Itstoresafullcopyofobjectswithinitsowndomain.
FromobjectsofotherdomainsintheActiveDirectoryforest,onlyapartialcopyofthecommonlymostsearchedattributesisstoredintheglobalcatalog.
Additionally,sometypesofgroupsareonlyvalidwithinaspecificscopeandmightnotbepartoftheglobalcatalog.
Notethatthecross-foresttrustcontextiswiderthanasingledomain.
Therefore,someoftheseserver-localordomain-localsecuritygroupmembershipsfromatrustedforestmightnotbevisibletoIdMservers.
GlobalCatalogandPOSIXAttributesActiveDirectorydoesnotreplicatePOSIXattributeswithitsdefaultsettings.
IfitisrequiredtousePOSIXattributesthataredefinedinADRedHatstronglyrecommendstoreplicatethemtotheglobalcatalogservice.
5.
1.
3.
TrustArchitectureinIdMOntheIdentityManagementside,theIdMserverhastobeabletorecognizeActiveDirectoryidentitiesandappropriatelyprocesstheirgroupmembershipforaccesscontrols.
TheMicrosoftPAC(MS-PAC,PrivilegeAccountCertificate)containstherequiredinformationabouttheuser;theirsecurityID,domainusername,andgroupmemberships.
IdentityManagementhastwocomponentstoanalyzedatainthePAContheKerberosticket:SSSD,toperformidentitylookupsonActiveDirectoryandtoretrieveuserandgroupsecurityidentifiers(SIDs)forauthorization.
SSSDalsocachesuser,group,andticketinformationforusersandmapsKerberosandDNSdomains,IdentityManagement(Linuxdomainmanagement),toassociatetheActiveDirectoryuserwithanIdMgroupforIdMpoliciesandaccess.
NOTEWindowsIntegrationGuide34NOTEAccesscontrolrulesandpoliciesforLinuxdomainadministration,suchasSELinux,sudo,andhost-basedaccesscontrols,aredefinedandappliedthroughIdentityManagement.
AnyaccesscontrolrulessetontheActiveDirectorysidearenotevaluatedorusedbyIdM;theonlyActiveDirectoryconfigurationwhichisrelevantisgroupmembership.
TrustswithDifferentActiveDirectoryForestsIdMcanalsobepartoftrustrelationshipswithdifferentADforests.
Onceatrustisestablished,additionaltrustswithotherforestscanbeaddedlater,followingthesamecommandsandprocedures.
IdMcantrustmultipleentirelyunrelatedforestsatthesametime,allowingusersfromsuchunrelatedADforestsaccesstoresourcesinthesamesharedIdMdomain.
5.
1.
3.
1.
ActiveDirectoryPACsandIdMTicketsGroupinformationinActiveDirectoryisstoredinalistofidentifiersinthePrivilegeAttributeCertificate(MS-PACorPAC)dataset.
ThePACcontainsvariousauthorizationinformation,suchasgroupmembershiporadditionalcredentialsinformation.
Italsoincludessecurityidentifiers(SIDs)ofusersandgroupsintheActiveDirectorydomain.
SIDsareidentifiersassignedtoActiveDirectoryusersandgroupswhentheyarecreated.
Intrustenvironments,groupmembersareidentifiedbySIDs,ratherthanbynamesorDNs.
APACisembeddedintheKerberosservicerequestticketforActiveDirectoryusersasawayofidentifyingtheentitytootherWindowsclientsandserversintheWindowsdomain.
IdMmapsthegroupinformationinthePACtotheActiveDirectorygroupsandthentothecorrespondingIdMgroupstodetermineaccess.
WhenanActiveDirectoryuserrequestsaticketforaserviceonIdMresources,theprocessgoesasfollows:1.
TherequestforaservicecontainsthePACoftheuser.
TheIdMKerberosDistributionCentre(KDC)analyzesthePACbycomparingthelistofActiveDirectorygroupstomembershipsinIdMgroups.
2.
ForSIDsoftheKerberosprincipaldefinedintheMS-PAC,theIdMKDCevaluatesexternalgroupmembershipsdefinedintheIdMLDAP.
IfadditionalmappingsareavailableforanSID,theMS-PACrecordisextendedwithotherSIDsoftheIdMgroupstowhichtheSIDbelongs.
TheresultingMS-PACissignedbytheIdMKDC.
3.
TheserviceticketisreturnedtotheuserwiththeupdatedPACsignedbytheIdMKDC.
UsersbelongingtoADgroupsknowntotheIdMdomaincannowberecognizedbySSSDrunningontheIdMclientsbasedontheMS-PACcontentoftheserviceticket.
ThisallowstoreduceidentitytraffictodiscovergroupmembershipsbytheIdMclients.
WhentheIdMclientevaluatestheserviceticket,theprocessincludesthefollowingsteps:1.
TheKerberosclientlibrariesusedintheevaluationprocesssendthePACdatatotheSSSDPACresponder.
2.
ThePACresponderverifiesthegroupSIDsinthePACandaddstheusertothecorrespondinggroupsintheSSSDcache.
SSSDstoresmultipleTGTsandticketsforeachuserasnewservicesareaccessed.
3.
UsersbelongingtotheverifiedgroupscannowaccesstherequiredservicesontheIdMside.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT355.
1.
3.
2.
ActiveDirectoryUsersandIdentityManagementGroupsWhenmanagingActiveDirectoryusersandgroups,youcanaddindividualADusersandwholeADgroupstoIdentityManagementgroups.
ForadescriptionofhowtoconfigureIdMgroupsforADusers,seeSection5.
3.
3,"CreatingIdMGroupsforActiveDirectoryUsers".
Non-POSIXExternalGroupsandSIDMappingGroupmembershipintheIdMLDAPisexpressedbyspecifyingadistinguishedname(DN)ofanLDAPobjectthatisamemberofagroup.
ADentriesarenotsynchronizedorcopiedovertoIdM,whichmeansthatADusersandgroupshavenoLDAPobjectsintheIdMLDAP.
Therefore,theycannotbedirectlyusedtoexpressgroupmembershipintheIdMLDAP.
Forthisreason,IdMcreatesnon-POSIXexternalgroups:proxyLDAPobjectsthatcontainreferencestoSIDsofADusersandgroupsasstrings.
Non-POSIXexternalgroupsarethenreferencedasnormalIdMLDAPobjectstosignifygroupmembershipforADusersandgroupsinIdM.
SIDsofnon-POSIXexternalgroupsareprocessedbySSSD;SSSDmapsSIDsofgroupstowhichanADuserbelongstoPOSIXgroupsinIdM.
TheSIDsontheADsideareassociatedwithusernames.
WhentheusernameisusedtoaccessIdMresources,SSSDinIdMresolvesthatusernametoitsSID,andthenlooksuptheinformationforthatSIDwithintheADdomain,asdescribedinSection5.
1.
3.
1,"ActiveDirectoryPACsandIdMTickets".
IDRangesWhenauseriscreatedinLinux,itisassignedauserIDnumber.
Inaddition,aprivategroupiscreatedfortheuser.
TheprivategroupIDnumberisthesameastheuserIDnumber.
InLinuxenvironment,thisdoesnotcreateaconflict.
OnWindows,however,thesecurityIDnumbermustbeuniqueforeveryobjectinthedomain.
TrustedADusersrequireaUIDandGIDnumberonaLinuxsystem.
ThisUIDandGIDnumbercanbegeneratedbyIdM,butiftheADentryalreadyhasUIDandGIDnumbersassigned,assigningdifferentnumberscreatesaconflict.
Toavoidsuchconflicts,itispossibletousetheAD-definedPOSIXattributes,includingtheUIDandGIDnumberandpreferredloginshell.
NOTEADstoresasubsetofinformationforallobjectswithintheforestinaglobalcatalog.
Theglobalcatalogincludeseveryentryforeverydomainintheforest.
IfyouwanttouseAD-definedPOSIXattributes,RedHatstronglyrecommendsthatyoufirstreplicatetheattributestotheglobalcatalog.
Whenatrustiscreated,IdMautomaticallydetectswhatkindofIDrangetouseandcreatesauniqueIDrangefortheADdomainaddedtothetrust.
Youcanalsochoosethismanuallybypassingoneofthefollowingoptionstotheipatrust-addcommand:ipa-ad-trustThisrangeoptionisusedforIDsalgorithmicallygeneratedbyIdMbasedontheSID.
IfIdMgeneratestheSIDsusingSID-to-POSIXIDmapping,theIDrangesforADandIdMusersandgroupsmusthaveunique,non-overlappingIDrangesavailable.
ipa-ad-trust-posixThisrangeoptionisusedforIDsdefinedinPOSIXattributesintheADentry.
WindowsIntegrationGuide36IdMobtainsthePOSIXattributes,includinguidNumberandgidNumber,fromtheglobalcataloginADorfromthedirectorycontroller.
IftheADdomainismanagedcorrectlyandwithoutIDconflicts,theIDnumbersgeneratedinthiswayareunique.
Inthiscase,noIDvalidationorIDrangeisrequired.
Forexample:[root@ipaserver~]#ipatrust-addname_of_the_trust--range-type=ipa-ad-trust-posixRecreatingatrustwiththeotherIDrangeIftheIDrangeofthecreatedtrustdoesnotsuityourdeployment,youcanre-createthetrustusingtheother--range-typeoption:1.
ViewalltheIDrangesthatarecurrentlyinuse:[root@ipaserver~]#ipaidrange-findInthelist,identifythenameoftheIDrangethatwascreatedbytheipatrust-addcommand.
ThefirstpartofthenameoftheIDrangeisthenameofthetrust:name_of_the_trust_id_range,forexamplead.
example.
com.
2.
(Optional)Ifyoudonotknowwhich--range-typeoption,ipa-ad-trustoripa-ad-trust-posix,wasusedwhenthetrustwascreated,identifytheoption:[root@ipaserver~]#ipaidrange-showname_of_the_trust_id_rangeMakenoteofthetypesothatyouchoosetheoppositetypeforthenewtrustinStep5.
3.
Removetherangethatwascreatedbytheipatrust-addcommand:[root@ipaserver~]#ipaidrange-delname_of_the_trust_id_range4.
Removethetrust:[root@ipaserver~]#ipatrust-delname_of_the_trust5.
Createanewtrustwiththecorrect--range-typeoption.
Forexample:[root@ipaserver~]#ipatrust-addname_of_the_trust--range-type=ipa-ad-trust5.
1.
3.
3.
ActiveDirectoryUsersandIdMPoliciesandConfigurationSeveralIdMpolicydefinitions,suchasSELinux,host-basedaccesscontrol,sudo,andnetgroups,relyonusergroupstoidentifyhowthepoliciesareapplied.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT37Figure5.
4.
ActiveDirectoryUsersandIdMGroupsandPoliciesActiveDirectoryusersareexternaltotheIdMdomain,buttheycanstillbeaddedasgroupmemberstoIdMgroups,aslongasthosegroupsareconfiguredasexternalgroupsdescribedinSection5.
1.
3.
2,"ActiveDirectoryUsersandIdentityManagementGroups".
Insuchcases,thesudo,host-basedaccesscontrols,andotherpoliciesareappliedtotheexternalPOSIXgroupand,ultimately,totheADuserwhenaccessingIdMdomainresources.
TheuserSIDinthePACintheticketisresolvedtotheADidentity.
ThismeansthatActiveDirectoryuserscanbeaddedasgroupmembersusingtheirfully-qualifiedusernameortheirSID.
5.
1.
4.
One-WayandTwo-WayTrustsIdMsupportstwotypesoftrustagreements,dependingonwhethertheentitiesthatcanestablishconnectiontoservicesinIdMarelimitedtoonlyADorcanincludeIdMentitiesaswell.
One-waytrustOne-waytrustenablesADusersandgroupstoaccessresourcesinIdM,butnottheotherwayaround.
TheIdMdomaintruststheADforest,buttheADforestdoesnottrusttheIdMdomain.
One-waytrustisthedefaultmodeforcreatingatrust.
Two-waytrustTwo-waytrustenablesADusersandgroupstoaccessresourcesinIdM.
However,thetwo-waytrustinIdMdoesnotgivetheusersanyadditionalrightscomparedtotheone-waytrustsolutioninAD.
Bothsolutionsareconsideredequallysecurebecauseofdefaultcross-foresttrustSIDfilteringsettings.
Formoregeneralinformationonone-wayandtwo-waytrusts,seeSection5.
1.
1,"TheArchitectureofaTrustRelationship".
Afteratrustisestablished,itisnotpossibletomodifyitstype.
Ifyourequireadifferenttypeoftrust,runtheipatrust-addcommandagain;bydoingthis,youcandeletetheexistingtrustandestablishanewone.
5.
1.
5.
ExternalTruststoActiveDirectoryAnexternaltrustisatrustrelationshipbetweendomainsthatareinadifferentforests.
WhileforestWindowsIntegrationGuide38Anexternaltrustisatrustrelationshipbetweendomainsthatareinadifferentforests.
WhileforesttrustsalwaysrequiretoestablishthetrustbetweentherootdomainsofActiveDirectoryforests,youcanestablishanexternaltrusttoanydomainwithintheforest.
Externaltrustsarenon-transitive.
Forthisreason,usersandgroupsfromotherActiveDirectorydomainshavenoaccesstoIdMresources.
Forfurtherinformation,seethesectioncalled"TransitiveandNon-transitiveTrusts".
5.
1.
6.
TrustControllersandTrustAgentsIdMprovidesthefollowingtypesofIdMserversthatsupporttrusttoActiveDirectory:TrustcontrollersIdMserversthatcancontrolthetrustandperformidentitylookupsagainstActiveDirectorydomaincontrollers(DC).
ActiveDirectorydomaincontrollerscontacttrustcontrollerswhenestablishingandverifyingthetrusttoActiveDirectory.
Thefirsttrustcontrolleriscreatedwhenyouconfigurethetrust.
FordetailsaboutconfiguringanIdMserverasatrustcontroller,seeSection5.
2.
2,"CreatingTrusts".
Trustcontrollersrunanincreasedamountofnetwork-facingservicescomparedtotrustagents,andthuspresentagreaterattacksurfaceforpotentialintruders.
TrustagentsIdMserversthatcanperformidentitylookupsagainstActiveDirectorydomaincontrollers.
FordetailsaboutconfiguringanIdMserverasatrustagent,seeSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
Inadditiontotrustcontrollersandagents,theIdMdomaincanalsoincludereplicaswithoutanyrole.
However,theseserversdonotcommunicatewithActiveDirectory.
Therefore,clientsthatcommunicatewiththeseserverscannotresolveActiveDirectoryusersandgroupsorauthenticateandauthorizeActiveDirectoryusers.
Table5.
1.
AcomparisonofthecapabilitiesprovidedbytrustcontrollersandtrustagentsCapabilityTrustcontrollersTrustagentsResolveActiveDirectoryusersandgroupsYesYesEnrollIdMclientsthatrunservicesaccessiblebyusersfromtrustedActiveDirectoryforestsYesYesManagethetrust(forexample,addtrustagreements)YesNoWhenplanningthedeploymentoftrustcontrollersandtrustagents,considertheseguidelines:ConfigureatleasttwotrustcontrollersperIdentityManagementdeployment.
Configureatleasttwotrustcontrollersineachdatacenter.
Ifyoueverwanttocreateadditionaltrustcontrollersorifanexistingtrustcontrollerfails,createanewCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT39Ifyoueverwanttocreateadditionaltrustcontrollersorifanexistingtrustcontrollerfails,createanewtrustcontrollerbypromotingatrustagentorareplica.
Todothis,usetheipa-adtrust-installutilityontheIdMserverasdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
IMPORTANTYoucannotdowngradeanexistingtrustcontrollertoatrustagent.
5.
2.
CREATINGCROSS-FORESTTRUSTS5.
2.
1.
EnvironmentandMachineRequirementsBeforeconfiguringatrustagreement,makesurethatboththeActiveDirectoryandIdentityManagementservers,machines,andenvironmentsmeettherequirementsandsettingsdescribedinthissection.
5.
2.
1.
1.
SupportedWindowsPlatformsYoucanestablishatrustrelationshipwithActiveDirectoryforeststhatusethefollowingforestanddomainfunctionallevels:Forestfunctionallevelrange:WindowsServer2008-WindowsServer2016Domainfunctionallevelrange:WindowsServer2008-WindowsServer2016Thefollowingoperatingsystemsaresupportedandtestedforestablishingatrustusingthementionedfunctionallevels:WindowsServer2012R2WindowsServer2016PreviousversionsofWindowsServerarenotsupportedforestablishingatrust.
5.
2.
1.
2.
DNSandRealmSettingsToestablishatrust,ActiveDirectoryandIdentityManagementrequirespecificDNSconfiguration:UniqueprimaryDNSdomainsEachsystemmusthaveitsownuniqueprimaryDNSdomainconfigured.
Forexample:ad.
example.
comforADandidm.
example.
comforIdMexample.
comforADandidm.
example.
comforIdMad.
example.
comforADandexample.
comforIdMIMPORTANTIftheIdMdomainistheparentdomainoftheADdomain,theIdMserversmustrunonRedHatEnterpriseLinux7.
5orlater.
ThemostconvenientmanagementsolutionisanenvironmentwhereeachDNSdomainismanagedWindowsIntegrationGuide40ThemostconvenientmanagementsolutionisanenvironmentwhereeachDNSdomainismanagedbyintegratedDNSservers,butitispossibletouseanyotherstandard-compliantDNSserveraswell.
ItisnotpossibleforADorIdMtosharetheprimaryDNSdomainwithanothersystemforidentitymanagement.
Formoreinformation,seedocumentationforhostnameandDNSconfigurationrequirementsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
Kerberosrealmnamesasupper-caseversionsofprimaryDNSdomainnamesKerberosrealmnamesmustbethesameastheprimaryDNSdomainnames,withalllettersuppercase.
Forexample,ifthedomainnamesaread.
example.
comforADandidm.
example.
comforIdM,theKerberosrealmnamesarerequiredtobeAD.
EXAMPLE.
COMandIDM.
EXAMPLE.
COM.
DNSrecordsresolvablefromallDNSdomainsinthetrustAllmachinesmustbeabletoresolveDNSrecordsfromallDNSdomainsinvolvedinthetrustrelationship:WhenconfiguringIdMDNS,followtheinstructionsdescribedinthesectiononconfiguringDNSserviceswithintheIdMdomainandsectiononmanagingDNSforwardingintheLinuxDomainIdentity,Authentication,andPolicyGuide.
IfyouareusingIdMwithoutintegratedDNS,followtheinstructionsdescribedinthesectiondescribingtheserverinstallationwithoutintegratedDNSintheLinuxDomainIdentity,Authentication,andPolicyGuide.
NooverlapbetweenIdMandADDNSdomainsMachinesjoinedtoIdMcanbedistributedovermultipleDNSdomains.
DNSdomainscontainingIdMclientsmustnotoverlapwithDNSdomainscontainingmachinesjoinedtoAD.
TheprimaryIdMDNSdomainmusthaveproperSRVrecordstosupportADtrusts.
YoucanacquirealistoftherequiredSRVrecordsspecifictoyoursystemsetupbyrunningthe$ipadns-update-system-records--dry-runcommand.
Thegeneratedlistcanlookforexamplelikethis:$ipadns-update-system-records--dry-runIPADNSrecords:_kerberos-master.
_tcp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos-master.
_udp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos.
_tcp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos.
_udp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos.
example.
com.
86400INTXT"EXAMPLE.
COM"_kpasswd.
_tcp.
example.
com.
86400INSRV0100464server.
example.
com.
_kpasswd.
_udp.
example.
com.
86400INSRV0100464server.
example.
com.
_ldap.
_tcp.
example.
com.
86400INSRV0100389server.
example.
com.
_ntp.
_udp.
example.
com.
86400INSRV0100123server.
example.
com.
ForotherDNSdomainsthatarepartofthesameIdMrealm,itisnotrequiredfortheSRVrecordstobeconfiguredwhenthetrusttoADisconfigured.
ThereasonisthatADdomaincontrollersdonotuseSRVrecordstodiscoverKDCsbutratherbasetheKDCdiscoveryonnamesuffixroutinginformationforthetrust.
VerifyingtheDNSConfigurationCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT41Beforeconfiguringtrust,verifythattheIdentityManagementandActiveDirectoryserverscanresolvethemselvesandalsoeachother.
Ifrunningthecommandsdescribedbelowdoesnotdisplaytheexpectedresults,inspecttheDNSconfigurationonthehostwherethecommandswereexecuted.
Ifthehostconfigurationseemscorrect,makesurethatDNSdelegationsfromtheparenttochilddomainsaresetupcorrectly.
NotethatADcachestheresultsofDNSlookups,andchangesyoumakeinDNSarethereforesometimesnotvisibleimmediately.
Youcandeletethecurrentcachebyrunningtheipconfig/flushdnscommand.
VerifythattheIdM-hostedservicesareresolvablefromtheIdMdomainserverusedforestablishingtrust1.
RunaDNSqueryfortheKerberosoverUDPandLDAPoverTCPservicerecords.
[root@ipaserver~]#dig+short-tSRV_kerberos.
_udp.
ipa.
example.
com.
010088ipamaster1.
ipa.
example.
com.
[root@ipaserver~]#dig+short-tSRV_ldap.
_tcp.
ipa.
example.
com.
0100389ipamaster1.
ipa.
example.
com.
ThecommandsareexpectedtolistallIdMservers.
2.
RunaDNSqueryfortheTXTrecordwiththeIdMKerberosrealmname.
TheobtainedvalueisexpectedtomatchtheKerberosrealmthatyouspecifiedwheninstallingIdM.
[root@ipaserver~]#dig+short-tTXT_kerberos.
ipa.
example.
com.
IPA.
EXAMPLE.
COM3.
Afteryouexecutetheipa-adtrust-installutility,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust",runaDNSqueryfortheMSDCKerberosoverUDPandLDAPoverTCPservicerecords.
[root@ipaserver~]#dig+short-tSRV_kerberos.
_udp.
dc.
_msdcs.
ipa.
example.
com.
010088ipamaster1.
ipa.
example.
com.
[root@ipaserver~]#dig+short-tSRV_ldap.
_tcp.
dc.
_msdcs.
ipa.
example.
com.
0100389ipamaster1.
ipa.
example.
com.
ThecommandsareexpectedtolistallIdMserversonwhichipa-adtrust-installhasbeenexecuted.
Notethattheoutputisemptyifipa-adtrust-installhasnotbeenexecutedonanyIdMserver,whichistypicallybeforeestablishingtheveryfirsttrustrelationship.
VerifythatIdMisabletoresolveservicerecordsforADRunaDNSqueryfortheKerberosoverUDPandLDAPoverTCPservicerecords.
[root@ipaserver~]#dig+short-tSRV_kerberos.
_udp.
dc.
_msdcs.
ad.
example.
com.
010088addc1.
ad.
example.
com.
[root@ipaserver~]#dig+short-tSRV_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
com.
0100389addc1.
ad.
example.
com.
ThesecommandsareexpectedtoreturnthenamesofADdomaincontrollers.
WindowsIntegrationGuide42VerifythattheIdM-hostedservicesareresolvablefromtheADserver1.
OntheADserver,setthenslookup.
exeutilitytolookupservicerecords.
C:\>nslookup.
exe>settype=SRV2.
EnterthedomainnamefortheKerberosoverUDPandLDAPoverTCPservicerecords.
>_kerberos.
_udp.
ipa.
example.
com.
_kerberos.
_udp.
ipa.
example.
com.
SRVservicelocation:priority=0weight=100port=88svrhostname=ipamaster1.
ipa.
example.
com>_ldap.
_tcp.
ipa.
example.
com_ldap.
_tcp.
ipa.
example.
comSRVservicelocation:priority=0weight=100port=389svrhostname=ipamaster1.
ipa.
example.
comTheexpectedoutputcontainsthesamesetofIdMserversasdisplayedinVerifythattheIdM-hostedservicesareresolvablefromtheIdMdomainserverusedforestablishingtrust.
3.
ChangetheservicetypetoTXTandrunaDNSqueryfortheTXTrecordwiththeIdMKerberosrealmname.
C:\>nslookup.
exe>settype=TXT>_kerberos.
ipa.
example.
com.
_kerberos.
ipa.
example.
com.
text="IPA.
EXAMPLE.
COM"TheoutputisexpectedtocontainthesamevalueasdisplayedinVerifythattheIdM-hostedservicesareresolvablefromtheIdMdomainserverusedforestablishingtrust.
4.
Afteryouexecutetheipa-adtrust-installutility,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust",runaDNSqueryfortheMSDCKerberosoverUDPandLDAPoverTCPservicerecords.
C:\>nslookup.
exe>settype=SRV>_kerberos.
_udp.
dc.
_msdcs.
ipa.
example.
com.
_kerberos.
_udp.
dc.
_msdcs.
ipa.
example.
com.
SRVservicelocation:priority=0weight=100port=88svrhostname=ipamaster1.
ipa.
example.
com>_ldap.
_tcp.
dc.
_msdcs.
ipa.
example.
com.
_ldap.
_tcp.
dc.
_msdcs.
ipa.
example.
com.
SRVservicelocation:priority=0CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT43weight=100port=389svrhostname=ipamaster1.
ipa.
example.
comThecommandisexpectedtolistallIdMserversonwhichtheipa-adtrust-installutilityhasbeenexecuted.
Notethattheoutputisemptyifipa-adtrust-installhasnotbeenexecutedonanyIdMserver,whichistypicallybeforeestablishingtheveryfirsttrustrelationship.
VerifythatADservicesareresolvablefromtheADserver1.
OntheADserver,setthenslookup.
exeutilitytolookupservicerecords.
C:\>nslookup.
exe>settype=SRV2.
EnterthedomainnamefortheKerberosoverUDPandLDAPoverTCPservicerecords.
>_kerberos.
_udp.
dc.
_msdcs.
ad.
example.
com.
_kerberos.
_udp.
dc.
_msdcs.
ad.
example.
com.
SRVservicelocation:priority=0weight=100port=88svrhostname=addc1.
ad.
example.
com>_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
com.
_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
com.
SRVservicelocation:priority=0weight=100port=389svrhostname=addc1.
ad.
example.
comTheexpectedoutputcontainsthesamesetofADserversasdisplayedinVerifythatIdMisabletoresolveservicerecordsforAD.
5.
2.
1.
3.
NetBIOSNamesTheNetBIOSnameiscriticalforidentifyingtheActiveDirectory(AD)domainand,ifIdMhasatrustconfiguredwithAD,foridentifyingtheIdMdomainandservices.
Asaconsequence,youmustuseadifferentNetBIOSnamefortheIdMdomainthantheNetBIOSnamesusedintheADdomainstowhichyouwanttoestablishtheforesttrust.
TheNetBIOSnameofanActiveDirectoryorIdMdomainisusuallythefar-leftcomponentofthecorrespondingDNSdomain.
Forexample,iftheDNSdomainisad.
example.
com,theNetBIOSnameistypicallyAD.
NOTEThemaximumlengthofaNetBIOSnameis15characters.
5.
2.
1.
4.
FirewallsandPortsToenablecommunicationbetweenADdomaincontrollersandIdMservers,makesureyoumeetthefollowingportrequirements:WindowsIntegrationGuide44OpenportsrequiredforanADtrustandportsrequiredbyanIdMserverinanADtrustonIdMserversandallADdomaincontrollersinbothdirections:fromtheIdMserverstotheADdomaincontrollersandback.
OpentheportrequiredbyanIdMclientinanADtrustonallADdomaincontrollersofthetrustedADforest.
OntheIdMclients,makesuretheportisopenintheoutgoingdirection(seePrerequisitesforInstallingaClientintheLinuxDomainIdentity,Authentication,andPolicyGuide).
Table5.
2.
PortsRequiredforanADTrustServicePortProtocolEndpointresolutionportmapper135TCPNetBIOS-DGM138TCPandUDPNetBIOS-SSN139TCPandUDPMicrosoft-DS445TCPandUDPEndpointmapperlistenerrange1024-1300TCPADGlobalCatalog3268TCPLDAP389TCP[a]andUDP[a]TheTCPport389isnotrequiredtobeopenonIdMserversfortrust,butitisnecessaryforclientscommunicatingwiththeIdMserver.
Table5.
3.
PortsRequiredbyIdMServersinaTrustServicePortProtocolKerberosSeePortRequirementsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
LDAPDNSTable5.
4.
PortsRequiredbyIdMClientsinanADTrustServicePortProtocolNotesCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT45Kerberos88UDPandTCPThelibkrb5libraryusesUDPandfalls-backtotheTCPprotocolifthedatasentfromtheKerberosDistributionCenter(KDC)istoolarge.
ActiveDirectoryattachesaPrivilegeAttributeCertificate(PAC)totheKerberosticket,whichincreasesthesizeandrequiresinmostcasestousetheTCPprotocol.
Toavoidthefall-backandresendingtherequest,bydefault,SSSDinRedHatEnterpriseLinux7.
4andlaterusesTCPforuserauthentication.
Toconfigurethesizebeforelibkrb5usesTCP,settheudp_preference_limitinthe/etc/krb.
5.
conffile.
Fordetails,seethekrb5.
conf(5)manpage.
ServicePortProtocolNotesAdditionalResourcesForadviceonhowtoopentherequiredports,seePortRequirementsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
5.
2.
1.
5.
IPv6SettingsTheIdMsystemmusthavetheIPv6protocolenabledinthekernel.
IfIPv6isdisabled,thentheCLDAPplug-inusedbytheIdMservicesfailstoinitialize.
5.
2.
1.
6.
ClockSettingsBoththeActiveDirectoryserverandtheIdMservermusthavetheirclocksinsync.
5.
2.
1.
7.
CreatingaConditionalForwarderfortheIdMDomaininADPreparetheADDNSservertoforwardqueriesfortheIdMdomaintotheIdMDNSserver:1.
OnaWindowsADdomaincontroller,opentheActiveDirectory(AD)DNSconsole.
2.
Right-clickConditionalForwarders,selectNewConditionalForwarder.
3.
EntertheIdMDNSdomainnameandtheIPaddressoftheIdMDNSserver4.
SelectStorethisconditionalforwarderinActiveDirectory,andreplicateitasfollows,andselectthereplicationsettingthatmatchesyourenvironment.
5.
ClickOK.
WindowsIntegrationGuide466.
ToverifythattheADdomaincontroller(DC)canresolveDNSentriesfromtheIdMdomain,openacommandpromptandenter:C:\>nslookupserver.
idm.
example.
comIfthecommandreturnstheIPaddressoftheIdMserver,theconditionalforwarderisworkingcorrectly.
5.
2.
1.
8.
CreatingaForwardZonefortheADDomaininIdMPreparetheIdMDNSservertoforwardqueriesfortheADdomaintotheADDNSserver:1.
OntheIdMserver,createaforwardzoneentryfortheADDNSdomain.
ForfurtherdetailsaboutcreatingaDNSforwardzoneinIdMseetheConfiguringForwardZonessectionintheLinuxDomainIdentity,Authentication,andPolicyGuide.
2.
IftheADDNSserverdoesnotsupportDNSSEC,disableDNSSECvalidationontheIdMserver:a.
Editthe/etc/named.
conffileandsetthednssec-validationparametertono:dnssec-validationno;b.
Restartthenamed-pkcs11service:#systemctlrestartnamed-pkcs113.
ToverifythattheIdMservercanresolveDNSentriesfromtheADdomain,enter:CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT47#hostserver.
ad.
example.
comIfthecommandreturnstheIPaddressoftheADDC,theforwardzoneisworkingcorrectly.
5.
2.
1.
9.
SupportedUserNameFormatsIdMperformsusernamemappinginthelocalSSSDclient.
ThedefaultoutputusernameformatforusersfromtrusteddomainssupportedbySSSDisuser_name@domain.
ActiveDirectorysupportsseveraldifferentkindsofnameformats:user_name,user_name@DOMAIN_NAME,andDOMAIN_NAME\user_name.
Userscanuseeitheronlytheirusername(user_name)ortheirfully-qualifiedusername(user_name@domain_name),forexample,toauthenticatetothesystem.
WARNINGPreferably,usethefully-qualifiedusernametoavoidconflictsifthesameusernameexistsinmultipledomains.
Ifauserspecifiesonlytheusernamewithoutthedomain,SSSDsearchestheaccountinalldomainsconfiguredinthe/etc/sssd/sssd.
conffileandintrusteddomains.
IfyouconfiguredadomainresolutionorderasdescribedinSection8.
5.
3,"ConfiguringtheDomainResolutionOrderonanIdMClient",SSSDsearchesfortheuserinthedefinedorder.
Inanycase,SSSDusesthefirstentryfound.
Thiscanleadtoproblemsorconfusionifthesameusernameexistsinmultipledomainsandthefirstentryfoundisnottheexpectedone.
Bydefault,SSSDdisplaysusernamesalwaysinthefully-qualifiedformat.
Fordetailsaboutchangingtheformat,seeSection5.
5,"ChangingtheFormatofUserNamesDisplayedbySSSD".
Toidentifytheusernameandthedomaintowhichtheusernamebelongs,SSSDusesaregularexpressiondefinedinthere_expressionoption.
TheregularexpressionisusedforIdMbackendsorADbackendsandsupportsallthementionedformats:re_expression=(((PPPPP5.
2.
2.
CreatingTrustsThefollowingsectionsdescribecreatingtrustsinvariousconfigurationscenarios.
Section5.
2.
2.
1,"CreatingaTrustfromtheCommandLine"containsthefullprocedureforconfiguringatrustfromthecommandline.
Theothersectionsdescribethestepswhicharedifferentfromthisbasicconfigurationscenarioandreferencethebasicprocedureforallothersteps.
NOTEIfyousetupareplicainanexistingtrustenvironment,thereplicaisnotautomaticallyconfiguredasatrustcontroller.
Toconfigurethereplicaasanadditionaltrustcontroller,followtheproceduresinthissection.
WindowsIntegrationGuide48Aftercreatingatrust,seeSection5.
2.
3,"Post-installationConsiderationsforCross-forestTrusts".
5.
2.
2.
1.
CreatingaTrustfromtheCommandLineCreatingatrustrelationshipbetweentheIdMandActiveDirectoryKerberosrealmsinvolvesthefollowingsteps:1.
PreparingtheIdMserverforthetrust,describedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust"2.
Creatingatrustagreement,describedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement"3.
VerifyingtheKerberosconfiguration,describedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration"5.
2.
2.
1.
1.
PreparingtheIdMServerforTrustTosetuptheIdMserverforatrustrelationshipwithAD,followthesesteps:1.
InstalltherequiredIdM,trust,andSambapackages:[root@ipaserver]#yuminstallipa-serveripa-server-trust-adsamba-client2.
ConfiguretheIdMservertoenabletrustservices.
Youcanskipthisstepifyouinstalledtheserverwiththeipa-replica-install--setup-adtrustcommand.
a.
Runtheipa-adtrust-installutility:[root@ipaserver]#ipa-adtrust-installTheutilityaddsDNSservicerecordsrequiredforADtrusts.
TheserecordsarecreatedautomaticallyifIdMwasinstalledwithanintegratedDNSserver.
IfIdMwasinstalledwithoutanintegratedDNSserver,ipa-adtrust-installprintsalistofservicerecordsthatyoumustmanuallyaddtotheDNSbeforeyoucancontinue.
IMPORTANTRedHatstronglyrecommendstoverifytheDNSconfigurationasdescribedinthesectioncalled"VerifyingtheDNSConfiguration"everytimeafterrunningipa-adtrust-install,especiallyifIdMorADdonotuseintegratedDNSservers.
b.
Thescriptpromptstoconfiguretheslapi-nisplug-in,acompatibilityplug-inthatallowsolderLinuxclientstoworkwithtrustedusers.
DoyouwanttoenablesupportfortrusteddomainsinSchemaCompatibilitypluginThiswillallowclientsolderthanSSSD1.
9andnon-Linuxclientstoworkwithtrustedusers.
Enabletrusteddomainssupportinslapi-nis[no]:yc.
Atleastoneuser(theIdMadministrator)existswhenthedirectoryisfirstinstalled.
TheSIDCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT49c.
Atleastoneuser(theIdMadministrator)existswhenthedirectoryisfirstinstalled.
TheSIDgenerationtaskcancreateaSIDforanyexistinguserstosupportthetrustenvironment.
Thisisaresource-intensivetask;forahighnumberofusers,thiscanberunseparately.
Doyouwanttoruntheipa-sidgentask[no]:yes3.
MakesurethatDNSisproperlyconfigured,asdescribedinSection5.
2.
1.
2,"DNSandRealmSettings".
4.
Startthesmbservice:[root@ipaserver~]#systemctlstartsmb5.
Optionally,configurethatthesmbservicestartsautomaticallywhenthesystemboots:[root@ipaserver~]#systemctlenablesmb6.
Optionally,usethesmbclientutilitytoverifythatSambarespondstoKerberosauthenticationfromtheIdMside.
[root@ipaserver~]#smbclient-Lipaserver.
ipa.
example.
com-klp_load_ex:changingtoconfigbackendregistrySharenameTypeCommentIPC$IPCIPCService(Samba4.
9.
1)ReconnectingwithSMB1forworkgrouplisting.
ServerCommentWorkgroupMaster5.
2.
2.
1.
2.
CreatingaTrustAgreementCreateatrustagreementfortheActiveDirectorydomainandtheIdMdomainbyusingtheipatrust-addcommand:#ipatrust-add--type=typead_domain_name--adminad_admin_username--passwordTheipatrust-addcommandsetsupaone-waytrustbydefault.
Toestablishatwo-waytrust,passthe--two-way=trueoption.
SeeSection5.
1.
4,"One-WayandTwo-WayTrusts"fordetails.
Toestablishanexternaltrust,passthe--external=trueoptiontotheipatrust-addcommand.
SeeSection5.
1.
5,"ExternalTruststoActiveDirectory"fordetails.
NOTETheipatrust-addcommandconfigurestheserverasatrustcontrollerbydefault.
SeeSection5.
1.
6,"TrustControllersandTrustAgents"fordetails.
Thefollowingexampleestablishesatwo-waytrustbyusingthe--two-way=trueoption:WindowsIntegrationGuide50[root@ipaserver~]#ipatrust-add--type=adad.
example.
com--adminAdministrator--password--two-way=trueActiveDirectorydomainadministrator'spassword:AddedActiveDirectorytrustforrealm"ad.
example.
com"Realm-Name:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912SIDblacklistincoming:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18SIDblacklistoutgoing:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18Trustdirection:Two-waytrustTrusttype:ActiveDirectorydomainTruststatus:Establishedandverified5.
2.
2.
1.
3.
VerifyingtheKerberosConfigurationToverifytheKerberosconfiguration,testifitispossibletoobtainaticketforanIdMuserandiftheIdMusercanrequestservicetickets.
Toverifyatwo-waytrust:1.
RequestaticketforanIdMuser:[root@ipaserver~]#kinituser2.
RequestserviceticketsforaservicewithintheIdMdomain:[root@ipaserver~]#kvno-Shostipaserver.
example.
com3.
RequestserviceticketsforaservicewithintheADdomain:[root@ipaserver~]#kvno-Scifsadserver.
example.
comIftheADserviceticketissuccessfullygranted,thereisacross-realmticket-grantingticket(TGT)listedwithalloftheotherrequestedtickets.
TheTGTisnamedkrbtgt/AD.
DOMAIN@IPA.
DOMAIN.
[root@ipaserver]#klistTicketcache:FILE:/tmp/krb5cc_0Defaultprincipal:user@IPA.
DOMAINValidstartingExpiresServiceprincipal06/15/1212:13:0406/16/1212:12:55krbtgt/IPA.
DOMAIN@IPA.
DOMAIN06/15/1212:13:1306/16/1212:12:55host/ipaserver.
ipa.
example.
com@IPA.
DOMAIN06/15/1212:13:2306/16/1212:12:55krbtgt/AD.
DOMAIN@IPA.
DOMAIN06/15/1212:14:5806/15/1222:14:58cifs/adserver.
ad.
example.
com@AD.
DOMAINCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT51Toverifyaone-waytrustfromtheIdMside:1.
RequestaticketforanActiveDirectoryuser:[root@ipaserver~]#kinituser@AD.
DOMAIN2.
RequestserviceticketsforaservicewithintheIdMdomain:[root@ipaserver~]#kvno-Shostipaserver.
example.
comIftheADserviceticketissuccessfullygranted,thereisacross-realmticket-grantingticket(TGT)listedwithalloftheotherrequestedtickets.
TheTGTisnamedkrbtgt/IPA.
DOMAIN@AD.
DOMAIN.
[root@ipaserver]#klistTicketcache:KEYRING:persistent:0:krb_ccache_hRtox00Defaultprincipal:user@AD.
DOMAINValidstartingExpiresServiceprincipal03.
05.
201618:31:0604.
05.
201604:31:01host/ipaserver.
ipa.
example.
com@IPA.
DOMAINrenewuntil04.
05.
201618:31:0003.
05.
201618:31:0604.
05.
201604:31:01krbtgt/IPA.
DOMAIN@AD.
DOMAINrenewuntil04.
05.
201618:31:0003.
05.
201618:31:0104.
05.
201604:31:01krbtgt/AD.
DOMAIN@AD.
DOMAINrenewuntil04.
05.
201618:31:00Thelocalauthplug-inmapsKerberosprincipalstolocalSSSDusernames.
ThisallowsADuserstouseKerberosauthenticationandaccessLinuxservices,whichsupportGSSAPIauthenticationdirectly.
NOTEFormoreinformationabouttheplug-in,seeSection5.
3.
7.
2,"UsingSSHWithoutPasswords".
5.
2.
2.
2.
CreatingaTrustUsingaSharedSecretAsharedsecretisapasswordthatisknowntotrustedpeersandcanbeusedbyotherdomainstojointhetrust.
Thesharedsecretcanconfigurebothone-wayandtwo-waytrustswithinActiveDirectory(AD).
InAD,thesharedsecretisstoredasatrusteddomainobject(TDO)withinthetrustconfiguration.
IdMsupportscreatingaone-wayortwo-waytrustusingasharedsecretinsteadoftheADadministratorcredentials.
SettingupsuchatrustrequirestheadministratortocreatethesharedsecretinADandmanuallyvalidatethetrustontheADside.
5.
2.
2.
2.
1.
CreatingaTwo-WayTrustUsingaSharedSecretTocreateatwo-waytrustwithasharedsecretwithaMicrosoftWindowsServer2012,2012R2,or2016:1.
PreparetheIdMserverforthetrust,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
2.
IftheIdMandADhostsuseaDNSserverthatcannotresolvebothdomains,setupforwardingfortheDNSzones:WindowsIntegrationGuide52a.
PreparetheADDNSservertoforwardqueriesfortheIdMdomaintotheIdMDNSserver.
Fordetails,seeSection5.
2.
1.
7,"CreatingaConditionalForwarderfortheIdMDomaininAD".
b.
PreparetheIdMDNSservertoforwardqueriesfortheADdomaintotheADDNSserver.
Fordetails,seeSection5.
2.
1.
8,"CreatingaForwardZonefortheADDomaininIdM".
3.
ConfigureatrustintheActiveDirectoryDomainsandTrustsconsole.
Inparticular:Createanewtrust.
GivethetrusttheIdMdomainname,forexampleidm.
example.
com.
Specifythatthisisaforesttypeoftrust.
Specifythatthisisatwo-waytypeoftrust.
Specifythatthisisaforest-wideauthentication.
Setthetrustpassword.
NOTEThesamepasswordmustbeusedwhenconfiguringthetrustinIdM.
Whenaskedtoconfirmtheincomingtrust,selectNo.
4.
Createatrustagreement,asdescribedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement".
Whenrunningtheipatrust-addcommand,usethe--type,--trust-secretand--two-way=Trueoptions,andomitthe--adminoption.
Forexample:[root@ipaserver~]#ipatrust-add--type=adad.
example.
com--trust-secret--two-way=TrueSharedsecretforthetrust:AddedActiveDirectorytrustforrealm"ad.
example.
com"Realm-Name:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912SIDblacklistincoming:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18SIDblacklistoutgoing:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18Trustdirection:TrustingforestTrusttype:ActiveDirectorydomainTruststatus:Waitingforconfirmationbyremoteside5.
Retrievethelistofdomains:[root@ipaserver~]#ipatrust-fetch-domainsad_domainCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT536.
OntheIdMserver,verifythatthetrustrelationshipisestablishedbyusingtheipatrust-showcommand.
[root@ipaserver~]#ipatrust-showad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912Trustdirection:TrustingforestTrusttype:ActiveDirectorydomain7.
Optionally,searchforthetrusteddomain:[root@ipaserver~]#ipatrustdomain-findad.
example.
comDomainname:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912Domainenabled:True8.
VerifytheKerberosconfiguration,asdescribedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration".
5.
2.
2.
2.
2.
CreatingaOne-WayTrustUsingaSharedSecretTocreateaone-waytrustusingasharedsecretwithaMicrosoftWindowsServer2012,2012R2or2016:1.
PreparetheIdMserverforthetrust,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
2.
IftheIdMandADhostsuseaDNSserverthatcannotresolvebothdomains,setupforwardingfortheDNSzones:a.
PreparetheADDNSservertoforwardqueriesfortheIdMdomaintotheIdMDNSserver.
Fordetails,seeSection5.
2.
1.
7,"CreatingaConditionalForwarderfortheIdMDomaininAD".
b.
PreparetheIdMDNSservertoforwardqueriesfortheADdomaintotheADDNSserver.
Fordetails,seeSection5.
2.
1.
8,"CreatingaForwardZonefortheADDomaininIdM".
3.
ConfigureatrustintheActiveDirectoryDomainsandTrustsconsole:a.
Rightclicktothedomainname,andselectProperties.
b.
OntheTruststab,clickNewTrust.
c.
EntertheIdMdomainname,andclickNext.
d.
SelectForesttrust,andclickNext.
e.
SelectOne-way:incoming,andclickNext.
f.
SelectThisdomainonly,andclickNext.
g.
Enterasharedsecret(trustpassword),andclickNext.
h.
Verifythesettings,andclickNext.
WindowsIntegrationGuide54i.
Whenthesystemasksifyouwanttoconfirmtheincomingtrust,selectNo,donotconfirmtheincomingtrust,andclickNext.
j.
ClickFinish.
4.
Createatrustagreement:[root@ipaserver~]#ipatrust-add--type=ad--trust-secretad.
example.
comSharedsecretforthetrust:passwordAddedActiveDirectorytrustforrealm"ad.
example.
com"Realmname:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-1762709870-351891212-3141221786Trustdirection:TrustingforestTrusttype:ActiveDirectorydomainTruststatus:WaitingforconfirmationbyremotesideEnterthesharedsecretyousetintheADDomainsandTrustsconsole.
5.
ValidatethetrustintheActiveDirectoryDomainsandTrustsconsole:a.
Rightclicktothedomainname,andselectProperties.
b.
OntheTruststab,selectthedomainintheDomainsthattrustthisdomain(incomingtrusts)pane,andclickProperties.
c.
ClicktheValidatebutton.
d.
SelectYes,validatetheincomingtrust,andenterthecredentialsoftheIdMadminuser.
6.
Updatethelistoftrusteddomains:[root@ipaserver~]#ipatrust-fetch-domainsad.
example.
comCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT55Listoftrustdomainssuccessfullyrefreshed.
Usetrustdomain-findcommandtolistthem.
Numberofentriesreturned07.
Listthetrusteddomains:[root@ipaserver~]#ipatrustdomain-findad.
example.
comDomainname:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-1762709870-351891212-3141221786Domainenabled:TrueNumberofentriesreturned18.
Optionally,verifythattheIdMservercanretrieveuserinformationfromADdomain:[root@ipaserver~]#getentpasswdadministrator@ad.
example.
comadministrator@ad.
example.
com:*:610600500:610600500:Administrator:/home/ad.
example.
com/administrator:5.
2.
2.
3.
VerifyingtheIDMappingToverifytheIDmapping:1.
RunthefollowingcommandonaWindowsActiveDirectorydomaincontroller(DC)tolistthehighestID:C:\>dcdiag/v/test:ridmanager/s:ad.
example.
com.
.
.
AvailableRIDPoolfortheDomainis1600to1073741823.
.
.
2.
ListtheIDrangesonanIdMserver:[root@ipaserver~]#ipaidrange-find1rangematchedRangename:AD.
EXAMPLE.
COM_id_rangeFirstPosixIDoftherange:610600000NumberofIDsintherange:200000FirstRIDofthecorrespondingRIDrange:0DomainSIDofthetrusteddomain:S-1-5-21-796215754-1239681026-23416912Rangetype:ActiveDirectorydomainrangeNumberofentriesreturned1YourequirethefirstPOSIXIDvalueinalaterstep.
WindowsIntegrationGuide563.
OntheActiveDirectoryDC,displaythesecurityidentifier(SID)orauser.
Forexample,todisplaytheSIDofadministrator:C:\>wmicuseraccountwherename="administrator"getsidS-1-5-21-796215754-1239681026-23416912-500ThelastpartoftheSIDistherelativeidentifier(RID).
Yourequiretheuser'sRIDinthenextstep.
NOTEIftheRIDishigherthanthedefaultIDrange(200000),usetheipaidrange-modcommandtoextendtherange.
Forexample:#ipaidrange-mod--range-size=1000000AD.
EXAMPLE.
COM_id_range4.
DisplaytheuserIDofthesameuserontheIdMserver:[root@ipaserver~]#idad\\administratoruid=610600500(administrator@ad.
example.
com).
.
.
5.
IfyouaddthefirstPOSIXIDvalue(610600000)totheRID(500),itmustmatchtheuserIDdisplayedontheIdMserver(610600500).
5.
2.
2.
4.
CreatingaTrustonanExistingIdMInstanceWhenconfiguringatrustforanexistingIdMinstance,certainsettingsfortheIdMserverandentrieswithinitsdomainarealreadyconfigured.
However,youmustsettheDNSconfigurationfortheActiveDirectorydomainandassignActiveDirectorySIDstoallexistingIdMusersandgroups.
1.
PreparetheIdMserverforthetrust,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
2.
Createatrustagreement,asdescribedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement".
3.
GenerateSIDsforeachIdMuser.
NOTEDonotperformthisstepiftheSIDsweregeneratedwhentheipa-adtrust-installutilitywasusedtoestablishthetrust.
a.
AddanewipaNTSecurityIdentifierattribute,containingaSID,automaticallyforeachentrybyrunningtheipa-sidgen-taskoperationontheback-endLDAPdirectory.
[root@ipaserver]#ldapmodify-x-Hldap://ipaserver.
ipa.
example.
com:389-D"cn=directorymanager"-wpassworddn:cn=sidgen,cn=ipa-sidgen-task,cn=tasks,cn=configchangetype:addobjectClass:topobjectClass:extensibleObjectCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT57cn:sidgennsslapd-basedn:dc=ipadomain,dc=comdelay:0addingnewentry"cn=sidgen,cn=ipa-sidgen-task,cn=tasks,cn=config"b.
Afterthetaskcompletessuccessfully,amessageisrecordedintheerrorlogsthattheSIDgenerationtask(Sidgentask)finishedwithastatusofzero(0).
[root@ipaserver]#grep"sidgen_task_thread"/var/log/dirsrv/slapd-IDM-EXAMPLE-COM/errors[20/Jul/2012:18:17:16+051800]sidgen_task_thread-[fileipa_sidgen_task.
c,line191]:Sidgentaskstarts.
.
.
[20/Jul/2012:18:17:16+051800]sidgen_task_thread-[fileipa_sidgen_task.
c,line196]:Sidgentaskfinished[0].
4.
VerifytheKerberosconfiguration,asdescribedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration".
5.
2.
2.
5.
AddingaSecondTrustWhenaddingatrustonanIdMserverthatalreadyhasoneormoretrustagreementsconfigured,certaingeneralIdMtrustsettings,suchasinstallingthetrust-relatedpackagesorconfiguringSIDs,isnolongerrequired.
Toaddanadditionaltrust,youonlymustconfigureDNSandestablishatrustagreement.
1.
MakesurethatDNSisproperlyconfigured,asdescribedinSection5.
2.
1.
2,"DNSandRealmSettings".
2.
Createatrustagreement,asdescribedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement".
5.
2.
2.
6.
CreatingaTrustintheWebUIBeforecreatingatrustinthewebUI,preparetheIdMserverforthetrust.
Thistrustconfigurationiseasiesttoperformfromthecommandline,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
Oncetheinitialconfigurationisset,atrustagreementcanbeaddedintheIdMwebUI:1.
OpentheIdMwebUI:https://ipaserver.
example.
com2.
OpentheIPAServermaintab,andselecttheTrustssubtab.
3.
IntheTrustssubtab,clickAddtoopenthenewtrustconfigurationwindow.
4.
Fillintherequiredinformationaboutthetrust:a.
ProvidetheADdomainnameintheDomainfield.
b.
Tosetupthetrustastwo-way,selecttheTwo-waytrustcheckbox.
Tosetupthetrustasone-way,leaveTwo-waytrustunselected.
Formoreinformationaboutone-wayandtwo-waytrusts,seeSection5.
1.
4,"One-WayandTwo-WayTrusts".
WindowsIntegrationGuide58c.
Toestablishanexternaltrusttoadomaininanotherforest,selecttheExternalTrustcheckbox.
Formoreinformation,seeSection5.
1.
5,"ExternalTruststoActiveDirectory".
d.
TheEstablishusingsectiondefineshowthetrustistobeestablished:ToestablishthetrustusingtheADadministrator'susernameandpassword,selectAdministrativeaccountandprovidetherequiredcredentials.
Alternatively,toestablishthetrustwithasharedpassword,selectPre-sharedpasswordandprovidethetrustpassword.
e.
DefinetheIDconfigurationforthetrust:TheRangetypeoptionallowsyoutochoosetheIDrangetype.
IfyouwantIdMtoautomaticallydetectwhatkindofIDrangetouse,selectDetect.
TodefinethestartingIDoftheIDrange,usetheBaseIDfield.
TodefinethesizeoftheIDrange,usetheRangesizefield.
IfyouwantIdMtousedefaultvaluesfortheIDrange,donotspecifytheseoptions.
FormoreinformationaboutIDranges,seethesectioncalled"IDRanges".
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT59Figure5.
5.
AddingaTrustintheWebUI5.
ClickAddtosavethenewtrust.
Afterthis,verifytheKerberosconfiguration,asdescribedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration".
5.
2.
3.
Post-installationConsiderationsforCross-forestTrusts5.
2.
3.
1.
PotentialBehaviorIssueswithActiveDirectoryTrust5.
2.
3.
1.
1.
ActiveDirectoryUsersandIdMAdministrationCurrently,ActiveDirectory(AD)usersandadministratorscanonlyseetheirself-servicepageafterloggingintotheIdMWebUI.
ADadministratorscannotaccesstheadministrator'sviewofIdMWebUI.
Fordetails,seethecorrespondingsectionoftheLinux_Domain_Identity_Authentication_and_Policy_Guide.
Additionally,ADuserscurrentlycannotmanagetheirownIDoverrides.
OnlyIdMuserscanaddandWindowsIntegrationGuide60Additionally,ADuserscurrentlycannotmanagetheirownIDoverrides.
OnlyIdMuserscanaddandmanageIDoverrides.
5.
2.
3.
1.
2.
AuthenticatingDeletedActiveDirectoryUsersBydefault,everyIdMclientusestheSSSDservicetocacheuseridentitiesandcredentials.
IftheIdMorADback-endprovideristemporarilyunavailable,SSSDenablesthelocalsystemtoreferenceidentitiesforuserswhohavealreadyloggedinsuccessfullyonce.
BecauseSSSDmaintainsalistofuserslocally,changesthataremadeonthebackendmightnotbeimmediatelyvisibletoclientsthatrunSSSDoffline.
Onsuchclients,userswhohavepreviouslyloggedintoIdMresourcesandwhosehashedpasswordsarestoredintheSSSDcacheareabletologinagaineveniftheiruseraccountshavebeendeletedinAD.
Iftheaboveconditionsaremet,theuseridentityiscachedinSSSD,andtheADuserisabletologintoIdMresourceseveniftheuseraccountisdeletedAD.
ThisproblemwillpersistuntilSSSDbecomesonlineandisabletoverifyADuserlogonagainstADdomaincontrollers.
IftheclientsystemrunsSSSDonline,thepasswordprovidedbytheuserisvalidatedbyanADdomaincontroller.
ThisensuresthatdeletedADusersarenotallowedtologin.
5.
2.
3.
1.
3.
CredentialCacheCollectionsandSelectingActiveDirectoryPrincipalsTheKerberoscredentialscacheattemptstomatchaclientprincipaltoaserverprincipalbasedonthefollowingidentifiersinthisorder:1.
servicename2.
hostname3.
realmnameWhentheclientandservermappingisbasedonthehostnameorrealnameandcredentialcachecollectionsareused,unexpectedbehaviorcanoccurinbindingasanADuser.
ThisisbecausetherealmnameoftheActiveDirectoryuserisdifferentthantherealmnameoftheIdMsystem.
IfanADuserobtainsaticketusingthekinitutilityandthenusesSSHtoconnecttoanIdMresource,theprincipalisnotselectedfortheresourceticket.
anIdMprincipalisusedbecausetheIdMprincipalmatchestherealmnameoftheresource.
Forexample,iftheADuserisAdministratorandthedomainisADEXAMPLE.
ADREALM,theprincipalisAdministrator@ADEXAMPLE.
ADREALM.
[root@server~]#kinitAdministrator@ADEXAMPLE.
ADREALMPasswordforAdministrator@ADEXAMPLE.
ADREALM:[root@server~]#klistTicketcache:KEYRING:persistent:0:0Defaultprincipal:Administrator@ADEXAMPLE.
ADREALMValidstartingExpiresServiceprincipal27.
11.
201511:25:2327.
11.
201521:25:23krbtgt/ADEXAMPLE.
ADREALM@ADEXAMPLE.
ADREALMrenewuntil28.
11.
201511:25:16ThisissetasthedefaultprincipalintheActiveDirectoryticketcache.
However,ifanyIdMuseralsohasaKerberosticket(suchasadmin),thenthereisaseparateIdMcredentialscache,withanIdMdefaultCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT61principal.
ThatIdMdefaultprincipalisselectedforahostticketiftheActiveDirectoryuserusesSSHtoconnecttoaresource.
[root@vm-197~]#ssh-lAdministrator@adexample.
adrealmipaclient.
example.
comAdministrator@adexample.
adrealm@ipaclient.
example.
com'spassword:[root@vm-197~]#klist-ATicketcache:KEYRING:persistent:0:0Defaultprincipal:Administrator@ADEXAMPLE.
ADREALMValidstartingExpiresServiceprincipal27.
11.
201511:25:2327.
11.
201521:25:23krbtgt/ADEXAMPLE.
ADREALM@ADEXAMPLE.
ADREALMrenewuntil28.
11.
201511:25:16Ticketcache:KEYRING:persistent:0:0Defaultprincipal:admin@EXAMPLE.
COM>>>>>IdMuserValidstartingExpiresServiceprincipal27.
11.
201511:25:1828.
11.
201511:25:16krbtgt/EXAMPLE.
COM@EXAMPLE.
COM27.
11.
201511:25:4828.
11.
201511:25:16host/ipaclient.
example.
com@EXAMPLE.
COM>>>>>hostprincipalThisisbecausetherealmnameoftheIdMprincipalmatchestherealmoftheIdMresource.
5.
2.
3.
1.
4.
ResolvingGroupSIDsLosingKerberosTicketsRunningacommandtoobtainaSIDfromtheSambaservice,suchasnetgetlocalsidornetgetdomainsid,removesanyexistingadminticketfromtheKerberoscache.
NOTEYouarenotrequiredtoruncommandssuchasnetgetlocalsidornetgetdomainsidinordertouseActiveDirectorytrusts.
CannotVerifyGroupMembershipforUsersItisnotpossibletoverifythataspecifictrusteduserisassociatedwithaspecificIdMgroup,externalorPOSIX.
CannotDisplayRemoteActiveDirectoryGroupMembershipsforanActiveDirectoryUserIMPORTANTNotethatthisproblemnolongeroccursiftheIdMserverandclientrunonRedHatEnterpriseLinux7.
1orlater.
TheidutilitycanbeusedtodisplaylocalgroupassociationsforLinuxsystemusers.
However,iddoesnotdisplayActiveDirectorygroupmembershipsforActiveDirectoryusers,eventhoughSambatoolsdodisplaythem.
Toworkaroundthis,youcanusethesshutilitytologintoanIdMclientmachineasthegivenADuser.
WindowsIntegrationGuide62Toworkaroundthis,youcanusethesshutilitytologintoanIdMclientmachineasthegivenADuser.
AftertheADuserlogsinsuccessfullyforthefirsttime,theidsearchdetectsanddisplaystheADgroupmemberships:[root@ipaserver~]#idADDOMAIN\useruid=1921801107(user@ad.
example.
com)gid=1921801107(user@ad.
example.
com)groups=1921801107(user@ad.
example.
com),129600004(ad_users),1921800513(domainusers@ad.
example.
com)5.
2.
3.
2.
ConfiguringTrustAgentsAfteryousetupanewreplicainatrustenvironment,thereplicadoesnotautomaticallyhavetheADtrustagentroleinstalled.
Toconfigurethereplicaasatrustagent:1.
Onanexistingtrustcontroller,runtheipa-adtrust-install--add-agentscommand:[root@existing_trust_controller]#ipa-adtrust-install--add-agentsThecommandstartsaninteractiveconfigurationsessionandpromptsyoufortheinformationrequiredtosetuptheagent.
Forfurtherinformationaboutthe--add-agentsoption,seetheipa-adtrust-install(1)manpage.
2.
Onthenewreplica:a.
RestarttheIdMservice:[root@new_trust_controller]#ipactlrestartb.
RemoveallentriesfromtheSSSDcache:[root@new_trust_controller]#sssctlcache-removeNOTETousethesssctlcommand,thesssd-toolspackagemustbeinstalled.
c.
Optionally,verifythatthereplicahastheADtrustagentroleinstalled:[root@new_trust_controller]#ipaserver-shownew_replica.
idm.
example.
com.
.
.
Enabledserverroles:CAserver,NTPserver,ADtrustagent5.
3.
MANAGINGANDCONFIGURINGACROSS-FORESTTRUSTENVIRONMENT5.
3.
1.
UserPrincipalNamesinaTrustedDomainsEnvironmentIdMsupportsthelogginginusinguserprincipalnames(UPN).
AUPNisanalternativetotheusernametoauthenticatewith,andhastheformatusername@KERBEROS-REALM.
InanActiveDirectoryforestitispossibletoconfigureadditionalUPNsuffixes.
TheseenterpriseprincipalnamesareusedtoprovideCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT63alternativeloginstothedefaultUPN.
Forexample,ifacompanyusestheKerberosrealmAD.
EXAMPLE.
COM,thedefaultUPNforauserisuser@ad.
example.
com.
Howeveroftenacompanywantinsteadtheiruserstobeabletologinusingtheiremailaddresses,likeuser@example.
com.
InthiscasetheadministratoraddsanadditionalUPNsuffixexample.
comtotheActiveDirectoryforestandsetsthenewsuffixintheuser'saccountproperties.
WhenyouaddorremoveUPNsuffixesinatrustedADforest,youhavetorefreshtheinformationforthetrustedforestontheIdMmaster:[root@ipaserver~]#ipatrust-fetch-domainsRealm-Name:ad.
example.
comNonewtrustdomainswerefoundNumberofentriesreturned0VerifythatthealternativeUPNwasfetched,byrunning:[root@ipaserver~]#ipatrust-showRealm-Name:ad.
example.
comRealm-Name:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912Trustdirection:Two-waytrustTrusttype:ActiveDirectorydomainUPNsuffixes:example.
comTheUPNsuffixesforadomainarestoredinthemulti-valueattributeipaNTAdditionalSuffixesinthecn=trusted_domain_name,cn=ad,cn=trusts,dc=idm,dc=example,dc=comsubtree.
5.
3.
2.
IdMClientsinanActiveDirectoryDNSDomainInsomeenvironmentswithtrustsbetweenIdMandActiveDirectory,youcanconfigureuserstoaccessanIdMclientusingahostnamefromtheActiveDirectoryDNSdomain,whiletheclientitselfisjoinedtoIdMtobenefitfromitsLinux-focusedfeatures.
IMPORTANTThisisnotarecommendedconfigurationandhassomelimitations.
RedHatrecommendstoalwaysdeployIdMclientsinaDNSzonedifferentfromtheonesownedbyActiveDirectoryandaccessIdMclientsthroughtheirIdMhostnames.
5.
3.
2.
1.
KerberosSingleSign-ontotheIdMClientisnotRequiredForIdMclientssetupintheActiveDirectoryDNSdomain,onlypasswordauthenticationisavailabletoaccessresourcesonthisIdMhost.
Toconfiguretheclientforthisscenario:1.
ToensurethattheSystemSecurityServiceDaemon(SSSD)ontheclientcancommunicatewiththeIdMservers,installtheIdMclientwiththe--domain=IPA_DNS_Domainoption:WindowsIntegrationGuide64[root@idm-client.
ad.
example.
com~]#ipa-client-install--domain=idm.
example.
comThisoptiondisablestheSRVrecordauto-detectionfortheActiveDirectoryDNSdomain.
2.
LocatetheexistingmappingfortheActiveDirectorydomaininthe[domain_realm]sectionofthe/etc/krb5.
confconfigurationfile:.
ad.
example.
com=IDM.
EXAMPLE.
COMad.
example.
com=IDM.
EXAMPLE.
COMReplacebothlineswithamappingentryfortheLinuxclientsfullyqualifieddomainname(FQDN)intheActiveDirectoryDNSzonetotheIdMrealm:idm-client.
ad.
example.
com=IDM.
EXAMPLE.
COMReplacingthedefaultmappingpreventsKerberosfromsendingitsrequestsfortheActiveDirectorydomaintotheIdMKerberosDistributionCenter(KDC).
InsteadKerberosusesauto-discoverythroughSRVDNSrecordstolocatetheKDC.
Onlyfortheaddedhostidm-client.
ad.
example.
comtheIdMKDCisset.
NOTEAuthenticatingtoresourcesonclientsthatarenotwithinanIdM-ownedDNSzoneisonlypossiblebyusingusernameandpassword.
HandlingofSSLcertificatesSSL-basedservicesrequireacertificatewithdNSNameextensionrecordsthatcoverallsystemhostnames,becausebothoriginal(A/AAAA)andCNAMErecordsmustbeinthecertificate.
Currently,IdMonlyissuescertificatestohostobjectsintheIdMdatabase.
Inthedescribedsetupwithoutsinglesign-onavailable,IdMalreadyhasahostobjectfortheFQDNinthedatabase,andcertmongercanrequestacertificateforthisname:[root@idm-client.
ad.
example.
com~]#ipa-getcertrequest-r\-f/etc/httpd/alias/server.
crt\-k/etc/httpd/alias/server.
key\-NCN=ipa-client.
ad.
example.
com\-Dipa-client.
ad.
example.
com\-Khost/idm-client.
ad.
example.
com@IDM.
EXAMPLE.
COM\-Uid-kp-serverAuthThecertmongerserviceusesthedefaulthostkeystoredinthe/etc/krb5.
keytabfiletoauthenticatetotheIdMCertificateAuthority(CA).
5.
3.
2.
2.
KerberosSingleSign-ontotheIdMClientisRequiredIfyourequireKerberossinglesign-ontoaccessresourcesontheIdMclient,theclientmustbewithintheIdMDNSdomain,forexampleidm-client.
idm.
example.
com.
YoumustcreateaCNAMErecordidm-client.
ad.
example.
comintheActiveDirectoryDNSdomainpointingtotheA/AAAArecordoftheIdMclient.
ForKerberos-basedapplicationservers,MITKerberossupportsamethodtoallowtheacceptanceofanyhost-basedprincipalavailableintheapplication'skeytab.
TodisablethestrictchecksonwhatCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT65KerberosprincipalwasusedtotargettheKerberosserver,setthefollowingoptioninthe[libdefaults]sectionofthe/etc/krb5.
confconfigurationfile:ignore_acceptor_hostname=trueHandlingofSSLcertificatesSSL-basedservicesrequireacertificatewithdNSNameextensionrecordsthatcoverallsystemhostnames,becausebothoriginal(A/AAAA)andCNAMErecordsmustbeinthecertificate.
Currently,IdMonlyissuescertificatestohostobjectsintheIdMdatabase.
Inthedescribedsetupwithoutsinglesign-onavailable,IdMalreadyhasahostobjectfortheFQDNinthedatabase,andcertmongercanrequestacertificateforthisname:1.
Createanewhostobject:[root@idm-server.
idm.
example.
com~]#ipahost-addidm-client.
ad.
example.
com--forceUsethe--forceoption,becausethehostnameisaCNAMEandnotanA/AAAArecord.
2.
AllowtheIdMDNShostnametomanagetheActiveDirectoryhostentryintheIdMdatabase:[root@idm-server.
idm.
example.
com~]#ipahost-add-managedbyidm-client.
ad.
example.
com\--hosts=idm-client.
idm.
example.
comWiththissetup,theIdMclientcanrequestanSSLcertificatewithdNSNameextensionrecordforitshostnamewithintheActiveDirectoryDNSdomain:[root@idm-client.
idm.
example.
com~]#ipa-getcertrequest-r\-f/etc/httpd/alias/server.
crt\-k/etc/httpd/alias/server.
key\-NCN=`hostname--fqdn`\-D`hostname--fqdn`\-Didm-client.
ad.
example.
com\-Khost/idm-client.
idm.
example.
com@IDM.
EXAMPLE.
COM\-Uid-kp-serverAuth5.
3.
3.
CreatingIdMGroupsforActiveDirectoryUsersUsergroupsarerequiredtosetaccesspermissions,host-basedaccesscontrol,sudorules,andothercontrolsonIdMusers.
ThesegroupsarewhatgrantaccesstoIdMdomainresources,aswellasrestrictingaccess.
BothADusersandADgroupscanbeaddeddirectlytoIdMusergroups.
Todothat,firstaddtheADusersorgroupstoanon-POSIXIdMexternalgroupandthentoalocalIdMPOSIXgroup.
ThePOSIXgroupcanthenbeusedforuserandrolemanagementoftheADusers.
Theprinciplesofhandlingnon-POSIXgroupsinIdMaredescribedinSection5.
1.
3.
2,"ActiveDirectoryUsersandIdentityManagementGroups".
NOTEWindowsIntegrationGuide66NOTEItisalsopossibletoaddADusergroupsasmemberstoIdMexternalgroups.
ThismightmakeiteasiertodefinepoliciesforWindowsusers,bykeepingtheuserandgroupmanagementwithinthesingleADrealm.
1.
Optional.
CreateorselectthegroupintheADdomaintousetomanageADusersintheIdMrealm.
MultiplegroupscanbeusedandaddedtodifferentgroupsontheIdMside.
2.
CreateanexternalgroupintheIdMdomainfortheActiveDirectoryusersbyaddingthe--externaloptiontotheipagroup-addcommand.
The--externaloptionindicatesthatthisgroupisintendedtocontainmembersfromoutsidetheIdMdomain.
Forexample:[root@ipaserver~]#ipagroup-add--desc='ADusersexternalmap'ad_users_external--externalAddedgroup"ad_users_external"Groupname:ad_users_externalDescription:ADusersexternalmapNOTETheexternalgroupmustbelinkedtoaadditionalgroupofauserandnottotheuser'sprimarygroup.
ActiveDirectorystoresgroupmembersinmemberattributesofagroup,andIdMusesthisattributetoresolvethemembers.
However,ActiveDirectorystorestheprimarygroupofusersintheprimaryGroupIDattributeintheuser'sentry,whichisnotresolved.
3.
CreateanewIdMPOSIXgrouporselectanexistingoneforadministeringtheIdMpolicies.
Forexample,tocreateanewgroup:[root@ipaserver~]#ipagroup-add--desc='ADusers'ad_usersAddedgroup"ad_users"Groupname:ad_usersDescription:ADusersGID:1296000044.
AddtheADusersorgroupstotheIdMexternalgroupasanexternalmember.
TheADmemberisidentifiedbyitsfully-qualifiedname,suchasDOMAIN\group_nameorDOMAIN\username.
TheADidentityisthenmappedtotheActiveDirectorySIDfortheuserorgroup.
Forexample,foranADgroup:[root@ipaserver~]#ipagroup-add-memberad_users_external--external"AD\DomainUsers"[memberuser]:[membergroup]:Groupname:ad_users_externalDescription:ADusersexternalmapExternalmember:S-1-5-21-3655990580-1375374850-1633065477-513CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT67SID_DOM_GROUP(2)Numberofmembersadded15.
AddtheexternalIdMgrouptothePOSIXIdMgroupasamember.
Forexample:[root@ipaserver~]#ipagroup-add-memberad_users--groupsad_users_externalGroupname:ad_usersDescription:ADusersGID:129600004Membergroups:ad_users_externalNumberofmembersadded15.
3.
4.
MaintainingTrustsTrustmanagementinvolvesseveralareas,suchasglobaltrustconfiguration,Kerberostrustconfiguration,DNSrealmconfiguration,orIDrangesassignmenttoActiveDirectoryusers.
5.
3.
4.
1.
EditingtheGlobalTrustConfigurationTheipa-adtrust-installutilityautomaticallyautomaticallyconfiguresbackgroundinformationfortheIdMdomainwhichisrequiredtocreateatrustwiththeActiveDirectorydomain.
Theglobaltrustconfigurationcontainsfiveattributes:AWindows-stylesecurityID(SID);thisattributeisautogeneratedandcannotbemodifiedAdomainGUID;thisattributeisautogeneratedandcannotbemodifiedAKerberosdomainname;thisattributecomesfromtheIdMconfigurationandcannotbemodifiedThedefaultgrouptowhichtoaddIdMusers;thisattributecanbemodifiedTheNetBIOSname;itisnotrecommendedtomodifythisattributeThetrustconfigurationisstoredinthecn=domain,cn=ad,cn=etc,dc=example,dc=comsubtree.
5.
3.
4.
1.
1.
ChangingtheNetBIOSNameIMPORTANTChangingtheNetBIOSnameinmostcasesrequirestore-establishallexistingtrusts.
Therefore,RedHatrecommendsnottochangetheattribute.
ANetBIOSnamecompatiblewithinanActiveDirectorytopologyisconfiguredfortheIdMserverwhenrunningtheipa-adtrust-installutility.
Tochangeitlater,runipa-adtrust-installagainandspecifythenewNetBIOSnameusingthe--netbios-nameoption:[root@ipaserver]#ipa-adtrust-install--netbios-name=NEWBIOSNAMEWindowsIntegrationGuide685.
3.
4.
1.
2.
ChangingtheDefaultGroupforWindowsUsersWhenIdentityManagementisconfiguredtotrustanActiveDirectoryforest,anMS-PACrecordisaddedtotheKerberosticketsofIdMusers.
AnMS-PACrecordcontainssecurityidentifiers(SIDs)ofthegroupstowhichanIdMuserbelongs.
IftheprimarygroupoftheIdMuserhasnoSIDassigned,thevalueofthesecurityidentifierdefinedfortheDefaultSMBGroupwillbeused.
ThesamelogicisappliedbytheSambasuitewhentheADdomaincontrollerrequestsuserinformationfromtheIdMtrustcontroller.
TheDefaultSMBGroupisafallbackgroupcreatedautomaticallybytheipa-adtrust-installutility.
Thedefaultgroupcannotbedeleted,butyoucanusetheglobaltrustconfigurationtospecifyanotherIdMgrouptobeusedasafallbackfortheprimarygroupoftheIdMusers.
Tosetthedefaultgroupfromthecommandline,usetheipatrustconfig-modcommand:[root@server~]#kinitadmin[root@server~]#ipatrustconfig-mod--fallback-primary-group="ExampleWindowsGroup"TosetthedefaultgroupfromtheIdMwebUI:1.
OpentheIdMwebUI.
https://ipaserver.
example.
com2.
UndertheIPAServermaintab,selecttheTrustssubtab,andthenopentheGlobalConfigurationsection.
3.
SelectanewgroupfromalloftheIdMgroupsintheFallbackprimarygroupdrop-downlist.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT69Figure5.
6.
ConfiguringtheDefaultGroupforWindowsUsers4.
ClickSavetosavethenewconfiguration.
5.
3.
4.
2.
Discovering,Enabling,andDisablingTrustDomainsAtransitivetrustmeansthatthetrustpathcanfollowachainofdomains.
ItisdescribedinmoredetailinSection5.
1.
1,"TheArchitectureofaTrustRelationship".
IdMhasatrustwiththerootdomaininaforestand,duetotransitivity,allofitschilddomainsandotherdomainsfromthesameforestareimplicitlyincludedinthattrust.
IdMfollowsthattopologyasWindowsusersfromanywhereintheforestattempttoaccessIdMresources.
EachdomainandchilddomainisatrustdomainintheIdMtrustconfiguration.
Eachdomainisstoredinitsownentry,cn=subdomain,cn=trust_name,cn=ad,cn=trusts,dc=example,dc=cominthetrustssubtree.
IdMattemptstodiscoverandmapthefullActiveDirectorytopologywhenthetrustisfirstconfigured,althoughinsomecasesitisrequiredorbeneficialtoretrievethattopologymanually.
Thatisdonewiththetrust-fetch-domainscommand:[root@ipaserver~]#kinitadmin[root@ipaserver~]#ipatrust-fetch-domainsad.
example.
comListoftrustdomainssuccessfullyrefreshedRealmname:test.
ad.
example.
comDomainNetBIOSname:TESTDomainSecurityIdentifier:S-1-5-21-87535643-5658642561-5780864324WindowsIntegrationGuide70Realmname:users.
ad.
example.
comDomainNetBIOSname:USERSDomainSecurityIdentifier:S-1-5-21-91314187-2404433721-1858927112Realmname:prod.
ad.
example.
comDomainNetBIOSname:PRODDomainSecurityIdentifier:S-1-5-21-46580863-3346886432-4578854233Numberofentriesreturned3NOTEWhenaddingatrustwithasharedsecret,youneedtomanuallyretrievetopologyoftheADforest.
Afterrunningtheipatrust-addad.
domain--trust-secretcommand,validateincomingtrustatADsideusingforesttrustpropertiesintheADDomainsandTruststool.
Then,runtheipatrust-fetch-domainsad.
domaincommand.
IdMwillreceiveinformationaboutthetrust,whichwillthenbeusable.
Oncethetopologyisretrieved(throughautomaticormanualdiscovery),individualdomainsandchilddomainsinthattopologycanbeenabled,disabled,orremovedentirelywithintheIdMtrustconfiguration.
Forexample,todisallowusersfromaspecificchilddomainfromusingIdMresources,disablethattrustdomain:[root@ipaserver~]#kinitadmin[root@ipaserver~]#ipatrustdomain-disabletest.
ad.
example.
comDisabledtrustdomain"test.
ad.
example.
com"Thattrustdomaincanbere-enabledusingthetrustdomain-enablecommand.
Ifadomainshouldbepermanentlyremovedfromthetopology,thanitcanbedeletedfromtheIdMtrustconfiguration.
[root@ipaserver~]#kinitadmin[root@ipaserver~]#ipatrustdomain-delprod.
ad.
example.
comRemovedinformationaboutthetrusteddomain""prod.
ad.
example.
com"5.
3.
4.
3.
ViewingandmanagingdomainsassociatedwithIdMKerberosrealmDomainsthatareassociatedwiththeIdMKerberosrealmarestoredinthecn=RealmDomains,cn=ipa,cn=etc,dc=example,dc=comsubtreeintheIdMdirectory.
ThelistofdomainsisusedbyIdMwhenitestablishesatrustwithActiveDirectory.
KnowingthefulllistofdomainsmanagedbyIdMallowstheADdomaincontrollertoknowwhichauthenticationrequeststoroutetotheIdMKDC.
ThelistofconfigureddomainsassociatedwithIdMrealmcanbedisplayedusingtherealmdomains-showcommand:CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT71[root@ipaserver~]#kinitadmin[root@ipaserver~]#iparealmdomains-showDomain:ipa.
example.
org,ipa.
example.
com,example.
comInanIdMsetupwithintegratedDNS:AdomainisautomaticallyaddedtothedomainslistafteranewDNSzoneisaddedtoIdMusingtheipadnszone-addcommand.
Runningiparealmdomains-showshowsthenewdomaininthelistofdomainscontrolledbytheIdMKDC:#kinitadmin#ipadnszone-addipa2.
example.
com#iparealmdomains-showDomain:ipa.
example.
org,ipa.
example.
com,example.
com,ipa2.
example.
comDeletionandothertypesofmodificationofdomainsassociatedwiththeIdMKerberosrealmarealsotakencareofautomatically.
InanIdMsetupwithoutintegratedDNS:IfaDNSzonehasbeenaddedthatispartoftheIdMKerberosrealm,thenewdomainhastobeaddedmanuallytotheIdMlistofdomainsunderthecontroloftheIdMKDC.
Addthenewdomainusingtheiparealmdomains-modcommandwiththe--add-domainoption:[root@ipaserver~]#kinitadmin[root@ipaserver~]#iparealmdomains-mod--add-domain=ipa2.
example.
comDomain:ipa.
example.
org,ipa.
example.
com,example.
com,ipa2.
example.
comIfaDNSzonehasbeendeleted,youneedtodeletethedomainassociatedwiththeIdMKerberosrealmmanually,too:[root@ipaserver~]#kinitadmin[root@ipaserver~]#iparealmdomains-mod--del-domain=ipa2.
example.
comDomain:ipa.
example.
org,ipa.
example.
com,example.
comIftherearemultiplechangestobemadetothelistofdomains,thelistitselfcanbemodifiedandreplacedusingthe--domainoption.
[root@ipaserver~]#iparealmdomains-mod--domain={ipa.
example.
org,ipa2.
example.
com}5.
3.
4.
4.
AddingRangesforUIDandGIDNumbersinaTransitiveTrustCreatingIDrangesatthetimewhenatrustisoriginallyconfiguredisdescribedinthesectioncalled"IDRanges".
ToaddanIDrangelater,usetheipaidrange-addcommandwiththefollowingoptions:the--base-idoptionsetsthebaseIDforthePOSIXrange,whichisthestartingnumberThe--range-sizeoptionsetsthesizeofthePOSIXIDrangeIdMuses.
IdMmapstheRIDofusersandgroupsinatrustedADdomaintoPOSIXIDs.
The--range-sizeoptiondefinesthemaximumnumberofIDsIdMcreates.
ADusesanewRIDforeachuserandgroupyoucreate.
Ifyoudeleteauserorgroup,ADwillnotre-usetheRIDforfutureADentries.
Therefore,therangemustbelargeenoughforIdMtoassignanIDtoeachexistingADuserandgroupaswellastheonesyoucreateinthefuture.
Forexample,ifanadministratordeletes20000of50000ADusersandwill,duringthetime,create10000newaccounts,therangemustbeatleastsettoWindowsIntegrationGuide7260000.
However,itisimportantthattherangealsocontainsenoughreserves.
Inlargeenvironments,inwhichyouexpectthatthedefault(200000)rangesizeisnotsufficient,set--range-sizetoahighervalue.
the--rid-baseoptionsetsthestartingnumberoftheRID,whichisthefar-rightnumberintheSID;thevaluerepresentstherangetoaddtothebaseIDtopreventconflictsthe--dom-sidoptionsetsthedomainSID,becausetherecanbemultipledomainsconfiguredfortrustsInthefollowingexample,thebaseIDis1,200,000andtheRIDis1,000.
TheresultingIDnumberisthen1,201,000.
[root@server~]$kinitadmin[root@server~]$ipaidrange-add--base-id=1200000--range-size=200000--rid-base=0--dom-sid=S-1-5-21-123-456-789trusted_dom_rangeIMPORTANTMakesurethatthemanuallydefinedIDrangedoesnotoverlapwiththeIDrangeusedbyIdM.
5.
3.
4.
5.
AdjustingDNAIDrangesmanuallyInsomecases,youmayneedtomanuallyadjustDistributedNumericAssignment(DNA)IDrangesforexistingreplicas,forexampletorecoveraDNAIDrangeassignedtoanon-functioningreplicaortoextendarangethathasrunoutofIDs.
WhenadjustingaDNAIDrangemanually,makesurethatthenewlyadjustedrangeisincludedintheIdMIDrange.
Youcancheckthisusingtheipaidrange-findcommand.
IfthenewlyadjustedrangeisnotincludedintheIdMIDrange,thecommandfails.
TorecoveraDNAIDrangefromanon-functioningreplica,usetheipa-replica-managednarange-showcommandtoseecurrentlyassignedDNAranges.
Toseethecurrentlyassignedon-deckDNAranges,usetheipa-replica-managednanextrange-showcommand.
IMPORTANTDonotcreateoverlappingIDranges.
IfanyoftheIDrangesyouassigntoserversorreplicasoverlap,itcouldresultintwodifferentserversassigningthesameIDvaluetodifferententries.
TodefinethecurrentDNAIDrangeforaspecifiedserver,usetheipa-replica-managednarange-setcommand:#ipa-replica-managednarange-setmasterA.
example.
com1250-1499TodefinethenextDNAIDrangeforaspecifiedserver,usetheipa-replica-managednanextrange-setcommand:#ipa-replica-managednanextrange-setmasterB.
example.
com1500-5000CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT735.
3.
4.
6.
KerberosFlagsforServicesandHostsAccessingservicesorhostsinatrusteddomaincanrequirespecialflagsfortheKerberosticket-grantingticket(TGT).
Forexample,ifyouwanttologinusingsinglesign-ontoanIdMclientwithanActiveDirectory(AD)accountfromanADclient,theKerberosTGTflagOK_AS_DELEGATEisrequired.
FormoreinformationandhowtosetKerberosflags,seeKerberosFlagsforServicesandHostsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
5.
3.
5.
SettingPACTypesforServicesOnIdMresources,ifanActiveDirectoryuserrequestsaticketforaservice,thenIdMforwardstherequesttoActiveDirectorytoretrievetheuserinformation.
Accessdata,associatedwiththeActiveDirectorygroupassignmentsfortheuser,issentbackbyActiveDirectoryandembeddedintheKerberosticket.
GroupinformationinActiveDirectoryisstoredinalistofidentifiersineachKerberosticketforActiveDirectoryusersinaspecialdatasetcalledprivilegedaccesscertificatesorMS-PAC.
ThegroupinformationinthePAChastobemappedtotheActiveDirectorygroupsandthentothecorrespondingIdMgroupstohelpdetermineaccess.
IdMservicescanbeconfiguredtogeneratePACsforeachauthenticationrequestwhenauserfirstattemptstoauthenticatetoadomainservice.
5.
3.
5.
1.
SettingDefaultPACTypesTheIdMserverconfigurationdefineswhichPACtypesaregeneratedbydefaultforaservice.
Theglobalsettingscanbeoverriddenbychangingthelocalsettingsonaspecificservice.
1.
OpentheIPAServertab.
2.
SelecttheConfigurationsubtab.
3.
ScrolltotheServiceOptionsarea.
Figure5.
7.
TheServiceOptionsArea4.
TousePAC,selecttheMS-PACcheckbox,whichaddsacertificatethatcanbeusedbyADservices.
Ifnocheckboxisselected,thennoPACisaddedtoKerberostickets.
Ifyouselectthenfs:NONEcheckbox,theMS-PACrecordwillnotbeaddedtotheserviceticketsissuedagainstNFSservers.
NOTEWindowsIntegrationGuide74NOTEYoucanignorethePADcheckbox.
ThisfunctionalityisnotyetavailableinIdM.
5.
ClicktheUpdatelinkatthetopofthepagetosavethechanges.
5.
3.
5.
2.
SettingPACTypesforaServiceTheglobalpolicysetswhatPACtypestouseforaserviceifnothingissetexplicitlyforthatservice.
However,theglobalsettingscanbeoverriddenonthelocalserviceconfiguration.
TochangethePACsettingfromthecommandline,usetheipaservice-modcommandwiththe--pac-typeoption.
Forinformationonhowtousethecommand,runitwiththe--helpoptionadded:$ipaservice-mod--helpUsage:ipa[global-options]service-modPRINCIPAL[options]ModifyanexistingIPAservice.
Options:-h,--helpshowthishelpmessageandexit.
.
.
TochangethePACsettinginthewebUI:1.
OpentheIdentitytab,andselecttheServicessubtab.
2.
Clickthenameoftheservicetoedit.
3.
IntheServiceSettingsarea,checktheOverrideinheritedsettingsoptionandthenselecttheMS-PACcheckboxtoaddacertificatethatcanbeusedbyADservices.
Figure5.
8.
TheServiceSettingsAreaIfnocheckboxisselected,thennoPACsareaddedtoKerberostickets.
NOTECHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT75NOTEYoucanignorethePADcheckbox.
ThisfunctionalityisnotyetavailableinIdM.
4.
ClicktheUpdatelinkatthetopofthepagetosavethechanges.
5.
3.
6.
UsingPOSIXAttributesDefinedinActiveDirectory5.
3.
6.
1.
DefiningUIDandGIDAttributesforActiveDirectoryUsersIftheWindowsadministratormanuallydefinesPOSIXUIDandGIDattributesforauser,createamatchinggroupontheIdMserverwiththesameGIDfortheuser.
Creatingthegroupensuresthattheuserisassociatedwithaprimaryusergroup.
Ifsuchgroupdoesnotexist,theIdMserverisunabletolookupallgroupstowhichtheuserbelongs.
5.
3.
6.
2.
TransferringLoginShellandHomeDirectoryAttributesIMPORTANTTheclientmustbeenrolledwithanIdMserverbasedonRedHatEnterpriseLinux7.
1orlatertobenefitfromthisfunctionality.
SSSDisabletoreadthefollowingattributevaluesfromanActiveDirectoryserverinatrustrelationshipwithIdM:theloginShellattribute,whichspecifiestheADuser'sshelltheunixHomeDirectoryattribute,whichspecifiestheADuser'shomedirectoryWhenacustomshellorhomedirectoryvalueisdefinedontheADserverusingtheseattributes,thecustomvalueisthendisplayedtotheIdMclientfortheADuser.
Therefore,thesameusershellisdisplayedfortheADuserbothontheADsideandontheIdMside.
NotethattodisplaytheADuser'shomedirectorytotheIdMclient,thesubdomain_homediroptioninthe[domain]sectionofthe/etc/sssd/sssd.
conffileontheIdMservermustbesetto%o.
The%ovaluerepresentsthehomedirectoryretrievedfromtheidentityprovider.
Forexample:[domain/example.
com]subdomain_homedir=%oIftheADadministratormodifiesloginShellorunixHomeDirectoryontheADside,thechangeisautomaticallyreflectedontheIdMsideaswell.
IftheattributesarenotdefinedontheADserver,SSSDusesatemplatedefaultvalue.
ThisdefaultvalueisthendisplayedtotheIdMclient.
5.
3.
7.
UsingSSHfromActiveDirectoryMachinesforIdMResourcesWhenatrustisconfigured,ActiveDirectoryuserscanaccessmachines,services,andfilesonIdMhostsusingSSHandtheirADcredentials.
5.
3.
7.
1.
CachingConsiderationsIdMclientsdonotconnecttoActiveDirectorydomaincontrollers(DC)directlytoretrieveuserWindowsIntegrationGuide76attributes.
Instead,aclientconnectstoanIdMserverwhocachesthisinformation.
Forthisreason,ifyoudisableauserinActiveDirectory,theusercanstillauthenticatetoIdMclientsusingSSHkeyauthenticationuntiltherecordoftheuserexpiresintheIdMdatabase.
IdMupdatesarecordofauserinthefollowingsituations:Theentryhasexpiredautomatically.
Youmanuallyexpiretheentryoftheuserinthecacheusingthesss_cacheutility:#sss_cache--useruser_nameTheuserauthenticatestoanIdMserverusingthekinitutilityorthewebUI.
5.
3.
7.
2.
UsingSSHWithoutPasswordsThelocalauthKerberosplug-inforlocalauthorizationensuresthatKerberosprincipalsareautomaticallymappedtolocalSSSDusernames.
Withlocalauth,WindowsusersfromatrustedADdomainarenotpromptedforapasswordwhenlogginginusingKerberosandcanthereforeuseSSHwithoutpasswords.
Theplug-inprovidesareliablemappingmechanismacrossmultiplerealmsandtrusts:whensssdconnectstotheKerberoslibrarytomaptheprincipaltoalocalPOSIXidentity,theSSSDplug-inmapsthemaccordingtothetrustagreementsdefinedinIdM.
Incertainsituations,usersuseanSSHbastionhosttoaccessotherRedHatEnterpriseLinuxmachines.
Bydefault,ifyouuseKerberostoauthenticatetoSSHonthebastionhost,theKerberosticketcannotbeforwardedtoauthenticateusingKerberostootherRedHatEnterpriseLinuxhosts.
Toenablesuchforwardauthentication,addtheOK_AS_DELEGATEKerberosflagtothebastionshostprincipal:#ipahost-modbastion_host.
idm.
example.
com--ok-as-delegate=trueKerberosAuthenticationforADUsersonRedHatEnterpriseLinux7.
1andnewerSystemsInRedHatEnterpriseLinux7.
1andnewersystems,SSSDautomaticallyconfiguresthelocalauthKerberosplug-in.
SSSDallowsusernamesintheformatuser@AD.
DOMAIN,ad.
domain\userandAD\user.
NOTEOnsystemswithlocalauth,itisnotrequiredtosettheauth_to_localoptioninthe/etc/krb5.
conffileorlistKerberosprincipalsinthe.
k5loginfile.
Thelocalauthplug-inmakesthispreviouslyusedconfigurationforloginswithoutpasswordsobsolete.
ManualConfigurationofKerberosAuthenticationforADUsersOnsystemswherethelocalauthplug-inisnotpresent,SSHpromptsforauserpasswordforActiveDirectorydomainuserseveniftheuserobtainsaproperKerberosticket.
ToenableActiveDirectoryuserstouseKerberosforauthenticationinthissituation,configuretheauth_to_localoptioninthe/etc/krb5.
conffileorlisttheuserKerberosprincipalsinthe.
k5loginfileinthehomedirectoryoftheuser.
Configuring/etc/krb5.
confThefollowingproceduredescribeshowtoconfigurerealmmappingintheKerberosconfiguration.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT771.
Openthe/etc/krb5.
conffile.
2.
Inthe[realms]section,identifytheIdMrealmbyname,andthenaddtwoauth_to_locallinestodefinetheKerberosprincipalnamemapping:Inonerule,includearuletomapdifferentActiveDirectoryusernameformatsandthespecificActiveDirectorydomain.
Intheotherrule,setthevalueofDEFAULT,forstandardUnixusernames.
Forexample:[realms]IDM={.
.
.
.
auth_to_local=RULE:[1:$1@$0](^.
*@ADDOMAIN$)s/@ADDOMAIN/@addomain/auth_to_local=DEFAULT}3.
RestarttheKDCservice.
[root@server~]#systemctlrestartkrb5kdc.
serviceNotethatifyouconfigureKerberosauthenticationusingtheauth_to_localoption,theusernameusedforSSHaccessmustmeetthefollowingcriteria:Theusernamemusthavetheformatad_user@ad_domain.
Thedomainnamemustbelowercase.
ThecaseoftheusernamemustmatchthecaseoftheusernameinActiveDirectory.
Forexample,userandUserareconsidereddifferentusersbecauseofthedifferentcases.
Formoreinformationaboutsettingauth_to_local,seethekrb5.
conf(5)manpage.
Configuring.
k5loginThefollowingprocedureconfiguresthesystemtofindtheKerberosprincipalnameforalocalusername.
1.
Createthe.
k5loginfileintheuser'shomedirectory.
2.
ListtheKerberosprincipalsusedbytheuserinthefile.
IftheauthenticatingusermatchestheprincipalinanexistingKerberosticket,theuserisallowedtologinusingtheticketandisnotpromptedforapassword.
NotethatifyouconfigureKerberosauthenticationusingthe.
k5loginconfiguration,theusernameusedforSSHaccessmusthavetheformatad_user@ad_domain.
Formoreinformationaboutconfiguringthe.
k5loginfile,seethe.
k5login(5)manpage.
EitheroneoftheseconfigurationproceduresresultsinADusersbeingabletologinusingKerberos.
5.
3.
8.
UsingaTrustwithKerberos-enabledWebApplicationsWindowsIntegrationGuide78AnyexistingwebapplicationcanbeconfiguredtouseKerberosauthentication,whichreferencesthetrustedActiveDirectoryandIdMKerberosrealms.
ForthefullKerberosconfigurationdirectives,seetheConfigurationpageforthemod_auth_kerbmodule.
NOTEAfterchangingtheApacheapplicationconfiguration,restarttheApacheservice:[root@ipaserver~]#systemctlrestarthttpd.
serviceForexample,foranApacheserver,thereareseveraloptionsthatdefinehowtheApacheserverconnectstotheIdMKerberosrealm:KrbAuthRealmsTheKrbAuthRealmsoptiongivestheapplicationlocationtothenameoftheIdMdomain.
Thisisrequired.
Krb5KeytabTheKrb5KeytaboptiongivesthelocationfortheIdMserverkeytab.
Thisisrequired.
KrbServiceNameTheKrbServiceNameoptionsetstheKerberosservicenameusedforthekeytab(HTTP).
Thisisrecommended.
KrbMethodK5PasswdandKrbMethodNegotiateTheKrbMethodK5PasswdKerberosmethodoptionenablespassword-basedauthenticationforvalidusers.
TheKrbMethodNegotiateoptionenablessinglesign-on(SSO)ifavalidKerberosticketisavailable.
Theseoptionsarerecommendedforeaseofuseformanyusers.
KrbLocalUserMappingTheKrbLocalUserMappingoptionenablesnormalweblogins(whichareusuallytheUIDorcommonnameoftheaccount)tobemappedtothefully-qualifiedusername(whichhasaformatofuser@REALM.
COM).
Thisoptionisstronglyrecommended.
Withoutthedomainname/loginnamemapping,thewebloginappearstobeadifferentuseraccountthanthedomainuser.
Thismeansthatuserscannotseetheirexpecteddata.
Forinformationonsupportedusernameformats,seeSection5.
2.
1.
9,"SupportedUserNameFormats".
Example5.
1.
KerberosConfigurationinanApacheWebApplicationAuthTypeKerberosAuthName"IPAKerberosauthentication"KrbMethodNegotiateonKrbMethodK5PasswdonCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT795.
3.
9.
ConfiguringanIdMserverasaKerberosDistributionCenterProxyforActiveDirectoryKerberoscommunicationIncertainsituations,networkrestrictionsorfirewallrulespreventIdentityManagement(IdM)clientsfromsendingKerberostraffictoport88onActiveDirectory(AD)domaincontrollers.
ThesolutionistosetupaKerberosproxy,forinstanceonanIdentityManagementserver,torelaytrafficfromIdMclientstoAD.
1.
OnIdMclients,addtheActiveDirectoryrealmtothe[realms]sectionofthe/etc/krb5.
conffile.
Setthekdcandkpasswd_serverparameterstopointtotheIdMserver'sfullyqualifieddomainnamefollowedby/KdcProxy':AD.
EXAMPLE.
COM={kdc=https://server.
idm.
example.
com/KdcProxykpasswd_server=https://server.
idm.
example.
com/KdcProxy}2.
OnIdMclients,disablethecreationof/var/lib/sss/pubconf/kdcinfo.
*fileswhichcouldoverridethe/etc/krb5.
confspecificationsfromthepreviousstep.
Editthe/etc/sssd/sssd.
conffile,settingthekrb5_use_kdcinfotoFalse:[domain/example.
com]krb5_use_kdcinfo=False3.
OnIdMservers,settheuse_dnsoptiontotrueinthe/etc/ipa/kdcproxy/kdcproxy.
conffiletoutilizeDNSservice(SRV)recordstofindADserverstocommunicatewith:use_dns=trueAlternatively,ifyoudonotwanttouseDNSSRVrecords,addexplicitADserverstothe[realms]sectionofthe/etc/krb5.
conffile:AD.
EXAMPLE.
COM={kdc=ad-server.
ad.
example.
comkpasswd_server=ad-server.
ad.
example.
com}NOTEYoucanperformsteps2and3oftheprocedurebyrunningascript,forexampleanAnsiblescript.
Thisisespeciallyusefulwhenmakingchangesonmultiplesystems.
KrbServiceNameHTTPKrbAuthRealmsIDM_DOMAINKrb5Keytab/etc/httpd/conf/ipa.
keytabKrbLocalUserMappingonKrbSaveCredentialsoffRequirevalid-userWindowsIntegrationGuide804.
OnIdMservers,restartIPAservices:#ipactlrestart5.
Toverifythattheprocedurehasbeensuccessful,runthefollowingonanIdMclient:#rm/var/lib/sss/pubconf/kdcinfo*#kinitad_user@AD.
EXAMPLE.
COMPasswordforad_user@AD.
EXAMPLE.
COM:#klistTicketcache:KEYRING:persistent:0:0Defaultprincipal:ad_user@AD.
EXAMPLE.
COMValidstartingExpiresServiceprincipal[.
.
.
outputtruncated.
.
.
]5.
4.
CHANGINGTHELDAPSEARCHBASEFORUSERSANDGROUPSINATRUSTEDACTIVEDIRECTORYDOMAINAsanadministrator,youcansetadifferentsearchbaseforusersandgroupsinthetrustedActiveDirectorydomain.
Forexample,thisenablesyoutofilteroutusersfrominactiveorganizationalunitssothatonlyactiveActiveDirectoryusersandgroupsarevisibletotheSSSDclientsystem.
5.
4.
1.
PrerequisitesToensurethatSSSDdoesnotresolveallgroupstheusersbelongsto,considerdisablingthesupportforthetokenGroupsattributeontheActiveDirectoryside.
WithtokenGroupsenabled,SSSDresolvesallgroupstheuserbelongstobecausetheattributecontainsaflatlistofSIDs.
SeeToken-GroupsattributeonMicrosoftDeveloperNetworkfordetailsabouttheattribute.
5.
4.
2.
ConfiguringtheLDAPSearchBasetoRestrictSearchesThisproceduredescribesrestrictingsearchesinSSSDtoaspecificsubtreebyeditingthe/etc/sssd/sssd.
conffile.
ConsiderationsIfyourSSSDclientsaredirectlyjoinedtoanActiveDirectorydomain,performthisprocedureonalltheclients.
IfyourSSSDclientsareinanIdentityManagementdomainthatisinatrustwithActiveDirectory,performthisprocedureonlyontheIdentityManagementserver.
Procedure1.
Makesurethetrusteddomainhasaseparate[domain]sectioninsssd.
conf.
Theheadingsoftrusteddomainsectionsfollowthistemplate:[domain/main_domain/trusted_domain]Forexample:CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT81[domain/idm.
example.
com/ad.
example.
com]2.
Editthesssd.
conffiletorestrictthesearchbasetoaspecificorganizationalunit(OU).
Forexample,theldap_search_baseoptionchangesthesearchbaseforalltypesofobjects.
[domain/idm.
example.
com/ad.
example.
com]ldap_search_base=ou=finance,dc=ad,dc=example,dc=comYoucanalsousetheldap_user_search_base,ldap_group_search_base,ldap_netgroup_search_base,andldap_service_search_baseoptions.
Formoredetailsontheseoptions,seethesssd-ldap(5)manpage.
3.
RestartSSSD.
#systemctlrestartsssd.
service4.
Toverify,resolveafewActiveDirectoryusersontheSSSDclient.
Forexample,totestachangetotheusersearchbaseandgroupsearchbase:#getentpasswdad_user@ad.
example.
com#getentgroupad_group@ad.
example.
comIfSSSDisconfiguredcorrectly,youareabletoresolveonlyobjectsfromtheconfiguredsearchbase.
Ifyouareabletoresolveusersfromothersearchdomains,troubleshoottheproblembyinspectingtheSSSDlogs:1.
ExpiretheSSSDcaches.
#sss_cache--everything2.
Inthegeneral[domain]sectionofsssd.
conf,setthedebug_leveloptionto9.
3.
Repeatthecommandforresolvingauser.
4.
IntheSSSDlogsat/var/log/sssd/,lookformessagesfromthesdap_get_generic_*functions.
Thefunctionslogthefilterandsearchbaseusedinusersearches.
AdditionalResourcesForalistofoptionsyoucanuseintrusteddomainsectionsofsssd.
conf,seeTRUSTEDDOMAINSECTIONinthesssd.
conf(5)manpage.
5.
5.
CHANGINGTHEFORMATOFUSERNAMESDISPLAYEDBYSSSDBydefault,SSSDusestheuser_name@domain_nameformatwhendisplayingusernames.
Beforeyouchangetheformat,seeSection5.
2.
1.
9,"SupportedUserNameFormats"tolearnaboutthereasonofthisdefaultvalue.
ToconfigurethatSSSDdisplaysonlytheusernamewithoutdomain:1.
Addthefollowingentrytothedomain'ssectioninthe/etc/sssd/sssd.
conffile:WindowsIntegrationGuide82full_name_format=%1$s2.
RestartSSSD:#systemctlrestartsssd5.
6.
RESTRICTINGIDENTITYMANAGEMENTORSSSDTOSELECTEDACTIVEDIRECTORYSERVERSORSITESINATRUSTEDACTIVEDIRECTORYDOMAINAsanadministrator,youcandisableautodiscoveryofActiveDirectoryserversandsitesinthetrustedActiveDirectorydomainandinsteadlistservers,sites,orbothmanually,sothatyoucanlimitthelistofActiveDirectoryserversthatSSSDcommunicateswith.
Forexample,thisenablesyoutoavoidcontactingsitesthatarenotaccessible.
5.
6.
1.
ConfiguringSSSDtoContactaSpecificActiveDirectoryServerThisproceduredescribesmanuallysettingActiveDirectoryserversthatSSSDconnectstobyeditingthe/etc/sssd/sssd.
conffile.
ConsiderationsIfyourSSSDclientsaredirectlyjoinedtoanActiveDirectorydomain,performthisprocedureonalltheclients.
Inthissetup,restrictingtheActiveDirectorydomaincontrollers(DCs)orsitesalsoconfigurestheSSSDclientstoconnecttoaparticularserverorsiteforauthentication.
IfyourSSSDclientsareinanIdentityManagementdomainthatisinatrustwithActiveDirectory,performthisprocedureonlyontheIdentityManagementserver.
Inthissetup,restrictingtheActiveDirectoryDCsorsitesdoesnotconfiguretheIdentityManagementclientstoconnecttoaparticularserverorsiteforauthentication.
AlthoughtrustedActiveDirectoryusersandgroupsareresolvedthroughIdentityManagementservers,authenticationisperformeddirectlyagainsttheActiveDirectoryDCs.
StartingwithRedHatEnterpriseLinux7.
6andsssd-1.
16.
2-5.
el7,youcanconfigureSSSDonIdMclientstouseaspecificADserverorsiteusingthead_serverandad_siteoptions.
InpriorversionsofRedHatEnterpriseLinux7,restrictauthenticationbydefiningtherequiredActiveDirectoryDCsinthe/etc/krb5.
conffileontheclients.
Procedure1.
Makesurethetrusteddomainhasaseparate[domain]sectioninsssd.
conf.
Theheadingsoftrusteddomainsectionsfollowthistemplate:[domain/main_domain/trusted_domain]Forexample:[domain/idm.
example.
com/ad.
example.
com]2.
Editthesssd.
conffiletolistthehostnamesoftheActiveDirectoryserversorsitestowhichyouwantSSSDtoconnect.
Usethead_serverand,optionally,ad_server_backupoptionsforActiveDirectoryservers.
UseCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT83Usethead_serverand,optionally,ad_server_backupoptionsforActiveDirectoryservers.
Usethead_siteoptionforActiveDirectorysites.
Formoredetailsontheseoptions,seethesssd-ad(5)manpage.
Forexample:[domain/idm.
example.
com/ad.
example.
com]ad_server=dc1.
ad.
example.
com3.
RestartSSSD.
#systemctlrestartsssd.
service4.
Toverify,ontheSSSDclient,resolveorauthenticateasanActiveDirectoryuserfromtheconfiguredserverorsite.
Forexample:#idad_user@ad.
example.
comIfyouareunabletoresolvetheuserorauthenticate,usethesestepstotroubleshoottheproblem:1.
Inthegeneral[domain]sectionofsssd.
conf,setthedebug_leveloptionto9.
2.
InspecttheSSSDlogsat/var/log/sssd/toseewhichserversSSSDcontacted.
AdditionalResourcesForalistofoptionsyoucanuseintrusteddomainsectionsofsssd.
conf,seeTRUSTEDDOMAINSECTIONinthesssd.
conf(5)manpage.
5.
7.
ACTIVEDIRECTORYTRUSTFORLEGACYLINUXCLIENTSLinuxclientsrunningRedHatEnterpriseLinuxwithSSSDversion1.
8orearlier(legacyclients)donotprovidenativesupportforIdMcross-foresttrustswithActiveDirectory.
Therefore,forADuserstobeabletoaccessservicesprovidedbytheIdMserver,thelegacyLinuxclientsandtheIdMserverhavetobeproperlyconfigured.
InsteadofusingSSSDversion1.
9orlatertocommunicatewiththeIdMservertoobtainLDAPinformation,legacyclientsuseotherutilitiesforthispurpose,forexamplenss_ldap,nss-pam-ldapd,orSSSDversion1.
8orearlier.
ClientsrunningthefollowingversionsofRedHatEnterpriseLinuxdonotuseSSSD1.
9andarethereforeconsideredtobelegacyclients:RedHatEnterpriseLinux5.
7orlaterRedHatEnterpriseLinux6.
0–6.
3IMPORTANTDonotusetheconfigurationdescribedinthissectionfornon-legacyclients,thatis,clientsrunningSSSDversion1.
9orlater.
SSSD1.
9orlaterprovidesnativesupportforIdMcross-foresttrustswithAD,meaningADuserscanproperlyaccessservicesonIdMclientswithoutanyadditionalconfiguration.
WhenalegacyclientjoinsthedomainofanIdMserverinatrustrelationshipwithAD,acompatLDAPWindowsIntegrationGuide84WhenalegacyclientjoinsthedomainofanIdMserverinatrustrelationshipwithAD,acompatLDAPtreeprovidestherequireduserandgroupdatatoADusers.
However,thecompattreeenablestheADuserstoaccessonlyalimitednumberofIdMservices.
Legacyclientsdonotprovideaccesstothefollowingservices:Kerberosauthenticationhost-basedaccesscontrol(HBAC)SELinuxusermappingsudorulesAccesstothefollowingservicesisprovidedevenincaseoflegacyclients:informationlook-uppasswordauthentication5.
7.
1.
Server-sideConfigurationforADTrustforLegacyClientsMakesuretheIdMservermeetsthefollowingconfigurationrequirements:Theipa-serverpackageforIdMandtheipa-server-trust-adpackagefortheIdMtrustadd-onhavebeeninstalled.
Theipa-server-installutilityhasbeenruntosetuptheIdMserver.
Theipa-adtrust-install--enable-compatcommandhasbeenrun,whichensuresthattheIdMserversupportstrustswithADdomainsandthatthecompatLDAPtreeisavailable.
Ifyouhavealreadyrunipa-adtrust-installwithoutthe--enable-compatoptioninthepast,runitagain,thistimeadding--enable-compat.
Theipatrust-addad.
example.
orgcommandhasbeenruntoestablishtheADtrust.
Ifthehost-basedaccesscontrol(HBAC)allow_allruleisdisabled,enablethesystem-authserviceontheIdMserver,whichallowsauthenticationoftheADusers.
Youcandeterminethecurrentstatusofallow_alldirectlyfromthecommandlineusingtheipahbacrule-showcommand.
Iftheruleisdisabled,Enabled:FALSEisdisplayedintheoutput:[user@server~]$kinitadmin[user@server~]$ipahbacrule-showallow_allRulename:allow_allUsercategory:allHostcategory:allServicecategory:allDescription:AllowalluserstoaccessanyhostfromanyhostEnabled:FALSENOTEForinformationondisablingandenablingHBACrules,seeConfiguringHost-BasedAccessControlintheLinuxDomainIdentity,Authentication,andPolicyGuide.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT85Toenablesystem-authontheIdMserver,createanHBACservicenamedsystem-authandaddanHBACruleusingthisservicetograntaccesstoIdMmasters.
AddingHBACservicesandrulesisdescribedintheLinuxDomainIdentity,Authentication,andPolicyGuide.
NotethatHBACservicesarePAMservicenames;ifyouaddanewPAMservice,makesuretocreateanHBACservicewiththesamenameandthengrantaccesstothisservicethroughHBACrules.
5.
7.
2.
Client-sideConfigurationUsingtheipa-adviseUtilityTheipa-adviseutilityprovidestheconfigurationinstructionstosetupalegacyclientforanADtrust.
Todisplaythecompletelistofscenariosforwhichipa-advisecanprovideconfigurationinstructions,runipa-advisewithoutanyoptions.
Runningipa-adviseprintsthenamesofallavailablesetsofconfigurationinstructionsalongwiththedescriptionsofwhateachsetdoesandwhenitisrecommendedtobeused.
[root@server~]#ipa-adviseconfig-redhat-nss-ldap:Instructionsforconfiguringasystemwithnss-ldapasaIPAclient.
Thissetofinstructionsistargetedforplatformsthatincludetheauthconfigutility,whichareallRedHatbasedplatforms.
config-redhat-nss-pam-ldapd:Instructionsforconfiguringasystem(.
.
.
)Todisplayasetofinstructions,runtheipa-adviseutilitywithaninstructionsetasaparameter:[root@server~]#ipa-adviseconfig-redhat-nss-ldap#!
/bin/sh#Instructionsforconfiguringasystemwithnss-ldapasaIPAclient.
#Thissetofinstructionsistargetedforplatformsthatincludethe#authconfigutility,whichareallRedHatbasedplatforms.
#SchemaCompatibilitypluginhasnotbeenconfiguredonthisserver.
To#configureit,run"ipa-adtrust-install--enable-compat"#Installrequiredpackagesviayumyuminstall-ywgetopensslnss_ldapauthconfig#NOTE:IPAcertificateusestheSHA-256hashfunction.
SHA-256was#introducedinRHEL5.
2.
Therefore,clientsolderthanRHEL5.
2willnot#beabletointeroperatewithIPAserver3.
x.
#Pleasenotethatthisscriptassumes/etc/openldap/cacertsasthe#defaultCAcertificatelocation.
Ifthisvalueisdifferentonyour#systemthescriptneedstobemodifiedaccordingly.
#DownloadtheCAcertificateoftheIPAservermkdir-p-m755/etc/openldap/cacertswgethttp://idm.
example.
com/ipa/config/ca.
crt-O/etc/openldap/cacerts/ca.
crt(.
.
.
)YoucanconfigureaLinuxclientusingtheipa-adviseutilitybyrunningthedisplayedinstructionsasashellscriptorbyexecutingtheinstructionsmanually.
Toruntheinstructionsasashellscript:WindowsIntegrationGuide861.
Createthescriptfile.
[root@server~]#ipa-adviseconfig-redhat-nss-ldap>setup_script.
sh2.
Addexecutepermissionstothefileusingthechmodutility.
[root@server~]#chmod+xsetup_script.
sh3.
Copythescripttotheclientusingthescputility.
[root@server~]#scpsetup_script.
shroot@client4.
Runthescriptontheclient.
[root@client~]#.
/setup_script.
shIMPORTANTAlwaysreadandreviewthescriptfilecarefullybeforeyourunitontheclient.
Toconfiguretheclientmanually,followandexecutetheinstructionsdisplayedbyipa-advisefromthecommandline.
5.
8.
TROUBLESHOOTINGCROSS-FORESTTRUSTSThissectionprovidesinformationaboutpossibleproblemsinancross-foresttrustenvironmentandwaystosolvethem.
5.
8.
1.
Troubleshootingtheipa-extdomPlug-inIdMclientsinanIdMdomainwithatrusttoActiveDirectory(AD)cannotreceiveinformationaboutusersandgroupsfromADdirectly.
Additionally,IdMdoesnotstoreinformationaboutADusersinDirectoryServerrunningonIdMmasters.
Instead,IdMserversusetheipa-extdomtoreceiveinformationaboutADusersandgroupsandforwardsthemtotherequestingclient.
SettingtheConfigTimeoutoftheipa-extdomPlug-inTheipa-extdomplug-insendsarequesttoSSSDforthedataaboutADusers.
However,notallrequesteddatamightbealreadyinthecacheofSSSD.
Inthiscase,SSSDrequeststhedatafromtheADdomaincontroller(DC).
Thiscanbetime-consumingforcertainoperations.
Theconfigtimeoutvaluedefinesthetimeinmillisecondsofhowlongtheipa-extdomplug-inwaitsforareplyofSSSDbeforetheplug-incancelstheconnectionandreturnsatimeouterrortothecaller.
Bydefault,theconfigtimeoutis10000milliseconds(10seconds).
Ifyousetatoosmallvalue,suchas500milliseconds,SSSDmightnothaveenoughtimetoreplyandrequestswillalwaysreturnatimeout.
Ifthevalueistoolarge,suchas30000milliseconds(30seconds),asinglerequestmightblocktheconnectiontoSSSDforthisamountoftime.
SinceonlyonethreadcanconnecttoSSSDatatime,allotherrequestsfromtheplug-inhavetowait.
IftherearemanyrequestssentbyIdMclients,theycanblockallavailableworkersconfiguredforCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT87IftherearemanyrequestssentbyIdMclients,theycanblockallavailableworkersconfiguredforDirectoryServerand,asaconsequence,theservermightnotbeabletoreplytoanykindofrequestforsometime.
Ifyousetatoosmallvalue,suchas500milliseconds,SSSDmightnothaveenoughtimetoreplyandrequestswillalwaysreturnatimeout.
Ifthevalueistoolarge,suchas30000milliseconds(30seconds),asinglerequestmightblocktheconnectiontoSSSDforthisamountoftime.
SinceonlyonethreadcanconnecttoSSSDatatime,allotherrequestsfromtheplug-inhavetowait.
IftherearemanyrequestssendbyIdMclients,theycanblockallavailableworkersconfiguredforDirectoryServerand,asaconsequence,theservermightnotbeabletoreplytoanykindofrequestforsometime.
Changetheconfigtimeoutinthefollowingsituations:IfIdMclientsfrequentlyreceivetimeouterrorsbeforetheirownsearchtimeoutisreachedwhenrequestinginformationaboutADusersandgroups,theconfigtimeoutvalueistoosmall.
IftheDirectoryServerontheIdMserverisoftenlockedandthepstackutilityreportsthatmanyorallworkerthreadsarehandlingipa-extdomrequestsatthistime,thevalueistoolarge.
Forexample,tosettheconfigvalueto20000milliseconds(20seconds),enter:#ldapmodify-D"cn=directorymanager"-Wdn:cn=ipa_extdom_extop,cn=plugins,cn=configchangetype:modifyreplace:ipaExtdomMaxNssTimeoutipaExtdomMaxNssTimeout:20000SettingtheMaximumSizeoftheipa-extdomPlug-inBufferUsedforNSSCallsTheipa-extdomplug-inusescallswhichusethesameAPIastypicalnameserviceswitch(NSS)callstorequestdatafromSSSD.
ThosecallsuseabufferwhereSSSDcanstoretherequesteddata.
Ifthebufferistoosmall,SSSDreturnsanERANGEerrorandtheplug-inretriestherequestwithalargerbuffer.
TheipaExtdomMaxNssBufSizeattributeinthecn=ipa_extdom_extop,cn=plugins,cn=configentryofDirectoryServerontheIdMmasterdefinesthemaximumsizeofthebufferinbytes.
Bydefault,thebufferis134217728bytes(128MB).
Onlyincreasethevalueif,forexample,agrouphassomanymembersthatallnamesdonotfitintothebufferandtheIPAclientcannotresolvethegroup.
Forexample,tosetthebufferto268435456bytes(256MB),enter:#ldapmodify-D"cn=directorymanager"-Wdn:cn=ipa_extdom_extop,cn=plugins,cn=configchangetype:modifyreplace:ipaExtdomMaxNssBufSizeipaExtdomMaxNssBufSize:268435456WindowsIntegrationGuide88PARTIII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:SYNCHRONIZATIONPARTIII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:SYNCHRONIZATION89CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERSThischapterdescribessynchronizationbetweenActiveDirectoryandRedHatEnterpriseLinuxIdentityManagement.
Synchronizationisoneofthetwomethodsforindirectintegrationofthetwoenvironments.
Fordetailsonthecross-foresttrust,whichistheother,recommendedmethod,seeChapter5,CreatingCross-forestTrustswithActiveDirectoryandIdentityManagement.
Ifyouareunsurewhichmethodtochooseforyourenvironment,readSection1.
3,"IndirectIntegration".
IdentityManagementusessynchronizationtocombinetheuserdatastoredinanActiveDirectorydomainandtheuserdatastoredintheIdMdomain.
Criticaluserattributes,includingpasswords,arecopiedandsynchronizedbetweentheservices.
Entrysynchronizationisperformedthroughaprocesssimilartoreplication,whichuseshookstoconnecttoandretrievedirectorydatafromtheWindowsserver.
PasswordsynchronizationisperformedthroughaWindowsservicewhichisinstalledontheWindowsserverandthencommunicatestotheIdentityManagementserver.
6.
1.
SUPPORTEDWINDOWSPLATFORMSSynchronizationissupportedwithActiveDirectoryforeststhatusethefollowingforestanddomainfunctionallevels:Forestfunctionallevelrange:WindowsServer2008-WindowsServer2012R2Domainfunctionallevelrange:WindowsServer2008-WindowsServer2012R2Thefollowingoperatingsystemsareexplicitlysupportedandtestedforsynchronizationusingthementionedfunctionallevels:WindowsServer2012R2WindowsServer2016PassSync1.
1.
5orlateriscompatiblewithallsupportedWindowsServerversions.
6.
2.
ABOUTACTIVEDIRECTORYANDIDENTITYMANAGEMENTWithintheIdMdomain,informationissharedamongserversandreplicasbycopyingthatinformation,reliablyandpredictably,betweendatamasters(serversandreplicas).
Thisprocessisreplication.
AsimilarprocesscanbeusedtosharedatabetweentheIdMdomainandaMicrosoftActiveDirectorydomain.
Thisissynchronization.
SynchronizationistheprocessofcopyinguserdatabackandforthbetweenActiveDirectoryandIdentityManagement.
WhenusersaresynchronizedbetweenActiveDirectoryandIdentityManagement,thedirectorysynchronization(DirSync)LDAPserverextensioncontrolisusedtosearchadirectoryforobjectsthathavechanged.
WindowsIntegrationGuide90Figure6.
1.
ActiveDirectoryandIdMSynchronizationSynchronizationisdefinedinanagreementbetweenanIdMserverandanActiveDirectorydomaincontroller.
Theagreementdefinesalloftheinformationrequiredtoidentifyuserentriesthatcanbesynchronized,suchasthesubtreetosynchronize,aswellasdefininghowaccountattributesarehandled.
Thesynchronizationagreementsarecreatedwithdefaultvalueswhichcanbetweakedtomeettheneedsofaspecificdomain.
Whentwoserversareinvolvedinsynchronization,theyarecalledpeers.
Table6.
1.
InformationinaSynchronizationAgreementWindowsInformationIdMInformationUsersubtree(cn=Users,$SUFFIX)ConnectioninformationActiveDirectoryadministratorusernameandpasswordPasswordSynchronizationServicepasswordCAcertificateUsersubtree(ou=People,$SUFFIX)Synchronizationismostcommonlybidirectional.
InformationissentbackandforthbetweentheIdMandtheWindowsdomaininaprocessthatisverysimilartohowIdMserversandreplicasshareinformationamongthemselves.
Anexceptionarenewuserentries,whichareonlyaddedfromtheWindowsdomaintotheIdMdomain.
Itispossibletoconfiguresynchronizationtoonlysynchronizeoneway.
Thatisunidirectionalsynchronization.
Topreventtheriskofdataconflicts,onlyonedirectoryshouldoriginateorremoveuserentries.
ThisistypicallytheWindowsdirectory,whichistheprimaryidentitystoreintheITenvironment,andthennewaccountsoraccountdeletionsaresynchronizedtotheIdentityManagementpeer.
Eitherdirectorycanmodifyentries.
Synchronization,then,isconfiguredbetweenoneIdentityManagementserverandoneActiveDirectorydomaincontroller.
TheIdentityManagementserverpropagatesthroughouttotheIdMdomain,whilethedomaincontrollerpropagateschangesthroughouttheWindowsdomain.
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS91Figure6.
2.
SynchronizationTopologyTherearesomekeyfeaturestoIdMsynchronization:Asynchronizationoperationrunseveryfiveminutes.
Tomodifythefrequency,setthewinSyncIntervalattributeintheActiveDirectorypeersDN:cn=meTowinserver.
ad.
example.
com,cn=replica,cn=dc\3Didm\,dc\3Dexample\,dc\3Dcom,cn=mappingtree,cn=configSynchronizationcanonlybeconfiguredwithoneActiveDirectorydomain.
SynchronizationcanonlybeconfiguredwithoneActiveDirectorydomaincontroller.
Onlyuserinformationissynchronized;groupinformationisnot.
Bothuserattributesandpasswordscanbesynchronized.
Whilemodificationsarebidirectional(goingbothfromActiveDirectorytoIdMandfromIdMtoActiveDirectory),creatingaccountsisonlyunidirectional,fromActiveDirectorytoIdentityManagement.
NewaccountscreatedinActiveDirectoryaresynchronizedovertoIdMautomatically.
However,useraccountscreatedinIdMmustalsobecreatedinActiveDirectorybeforetheywillbesynchronized.
Inthissituation,thesynchronizationprocesstriestofindamatchingaccountwiththesamevaluefortheuidattributeinIdMthanforthesAMAccountNameattributeinActiveDirectory.
Ifamatchisfound,theIdMntUserDomainIdattributeissettotheActiveDirectoryobjectGUIDvalue.
Theseattributesaregloballyuniqueandimmutable,andentriesstaysynchronized,eveniftheyaremovedorrenamed.
Accountlockinformationissynchronizedbydefault,soauseraccountwhichisdisabledinonedomainisdisabledintheother.
Passwordsynchronizationchangestakeeffectimmediately.
Ifauserpasswordisaddedorchangedononepeer,thatchangeisimmediatelypropagatedtotheotherpeerserver.
ThePasswordSynchronizationclientsynchronizesnewpasswordsorpasswordupdates.
Existingpasswords,whicharestoredinahashedforminbothIdMandActiveDirectory,cannotbedecryptedorsynchronizedwhenthePasswordSynchronizationclientisinstalled,soexistingWindowsIntegrationGuide92passwordsarenotsynchronized.
Userpasswordsmustbechangedtoinitiatesynchronizationbetweenthepeerservers.
Whiletherecanonlybeoneagreement,thePassSyncservicemustbeinstalledoneveryActiveDirectoryserver.
WhenActiveDirectoryusersaresynchronizedovertoIdM,certainattributes(includingKerberosandPOSIXattributes)willhaveIPAattributesautomaticallyaddedtotheuserentries.
TheseattributesareusedbyIdMwithinitsdomain.
TheyarenotsynchronizedbackoverthecorrespondingActiveDirectoryuserentry.
Someofthedatainsynchronizationcanbemodifiedaspartofthesynchronizationprocess.
Forexamples,certainattributescanbeautomaticallyaddedtoActiveDirectoryuseraccountswhentheyaresyncedovertotheIdMdomain.
TheseattributechangesaredefinedaspartofthesynchronizationagreementandaredescribedinSection6.
5.
2,"ChangingtheBehaviorforSynchronizingUserAccountAttributes".
6.
3.
ABOUTSYNCHRONIZEDATTRIBUTESIdentityManagementsynchronizesasubsetofuserattributesbetweenIdMandActiveDirectoryuserentries.
Anyotherattributespresentintheentry,eitherinIdentityManagementorinActiveDirectory,areignoredbysynchronization.
NOTEMostPOSIXattributesarenotsynchronized.
AlthoughtherearesignificantschemadifferencesbetweentheActiveDirectoryLDAPschemaandthe389DirectoryServerLDAPschemausedbyIdentityManagement,therearemanyattributesthatarethesame.
TheseattributesaresimplysynchronizedbetweentheActiveDirectoryandIdMuserentries,withnochangestotheattributenameorvalueformat.
UserSchemaThatAretheSameinIdentityManagementandWindowsServerscn[2]physicalDeliveryOfficeNamedescriptionpostOfficeBoxdestinationIndicatorpostalAddressfacsimileTelephoneNumberpostalCodegivennameregisteredAddresshomePhoneCHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS93snhomePostalAddressstinitialsstreetltelephoneNumbermailteletexTerminalIdentifiermobiletelexNumberotitleouuserCertificatepagerx121AddressSomeattributeshavedifferentnamesbutstillhavedirectparitybetweenIdM(whichuses389DirectoryServer)andActiveDirectory.
Theseattributesaremappedbythesynchronizationprocess.
Table6.
2.
UserSchemaMappedbetweenIdentityManagementandActiveDirectoryIdentityManagementActiveDirectorycn[a]namensAccountLockuserAccountControlntUserDomainIdsAMAccountNamentUserHomeDirhomeDirectoryntUserScriptPathscriptPathntUserLastLogonlastLogonWindowsIntegrationGuide94ntUserLastLogofflastLogoffntUserAcctExpiresaccountExpiresntUserCodePagecodePagentUserLogonHourslogonHoursntUserMaxStoragemaxStoragentUserProfileprofilePathntUserParmsuserParametersntUserWorkstationsuserWorkstations[a]Thecnismappeddirectly(cntocn)whensynchronizingfromIdentityManagementtoActiveDirectory.
WhensynchronizingfromActiveDirectorycnismappedfromthenameattributeinActiveDirectorytothecnattributeinIdentityManagement.
IdentityManagementActiveDirectory6.
3.
1.
UserSchemaDifferencesbetweenIdentityManagementandActiveDirectoryEventhoughattributesmaybesuccessfullysynchronizedbetweenActiveDirectoryandIdM,theremaystillbedifferencesinhowActiveDirectoryandIdentityManagementdefinetheunderlyingX.
500objectclasses.
ThiscouldleadtodifferencesinhowthedataarehandledinthedifferentLDAPservices.
ThissectiondescribesthedifferencesinhowActiveDirectoryandIdentityManagementhandlesomeoftheattributeswhichcanbesynchronizedbetweenthetwodomains.
6.
3.
1.
1.
ValuesforcnAttributesIn389DirectoryServer,thecnattributecanbemulti-valued,whileinActiveDirectorythisattributemusthaveonlyasinglevalue.
WhentheIdentityManagementcnattributeissynchronized,then,onlyonevalueissenttotheActiveDirectorypeer.
Whatthismeansforsynchronizationisthat,potentially,ifacnvalueisaddedtoanActiveDirectoryentryandthatvalueisnotoneofthevaluesforcninIdentityManagement,thenalloftheIdentityManagementcnvaluesareoverwrittenwiththesingleActiveDirectoryvalue.
OneotherimportantdifferenceisthatActiveDirectoryusesthecnattributeasitsnamingattribute,whereIdentityManagementusesuid.
Thismeansthatthereisthepotentialtorenametheentryentirely(andaccidentally)ifthecnattributeiseditedintheIdentityManagement.
6.
3.
1.
2.
ValuesforstreetandstreetAddressActiveDirectoryusestheattributestreetAddressforauser'spostaladdress;thisisthewaythat389DirectoryServerusesthestreetattribute.
TherearetwoimportantdifferencesinthewaythatActiveDirectoryandIdentityManagementusethestreetAddressandstreetattributes,respectively:CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS95In389DirectoryServer,streetAddressisanaliasforstreet.
ActiveDirectoryalsohasthestreetattribute,butitisaseparateattributethatcanholdanindependentvalue,notanaliasforstreetAddress.
ActiveDirectorydefinesbothstreetAddressandstreetassingle-valuedattributes,while389DirectoryServerdefinesstreetasamulti-valuedattribute,asspecifiedinRFC4519.
Becauseofthedifferentwaysthat389DirectoryServerandActiveDirectoryhandlestreetAddressandstreetattributes,therearetworulestofollowwhensettingaddressattributesinActiveDirectoryandIdentityManagement:ThesynchronizationprocessmapsstreetAddressintheActiveDirectoryentrytostreetinIdentityManagement.
Toavoidconflicts,thestreetattributeshouldnotbeusedinActiveDirectory.
OnlyoneIdentityManagementstreetattributevalueissynchronizedtoActiveDirectory.
IfthestreetAddressattributeischangedinActiveDirectoryandthenewvaluedoesnotalreadyexistinIdentityManagement,thenallstreetattributevaluesinIdentityManagementarereplacedwiththenew,singleActiveDirectoryvalue.
6.
3.
1.
3.
ConstraintsontheinitialsAttributeFortheinitialsattribute,ActiveDirectoryimposesamaximumlengthconstraintofsixcharacters,but389DirectoryServerdoesnothavealengthlimit.
IfaninitialsattributelongerthansixcharactersisaddedtoIdentityManagement,thevalueistrimmedwhenitissynchronizedwiththeActiveDirectoryentry.
6.
3.
1.
4.
Requiringthesurname(sn)AttributeActiveDirectoryallowspersonentriestobecreatedwithoutasurnameattribute.
However,RFC4519definesthepersonobjectclassasrequiringasurnameattribute,andthisisthedefinitionusedinDirectoryServer.
IfanActiveDirectorypersonentryiscreatedwithoutasurnameattribute,thatentrywillnotbesynchronizedovertoIdMsinceitfailswithanobjectclassviolation.
6.
3.
2.
ActiveDirectoryEntriesandPOSIXAttributesWhenaWindowsuseraccountcontainsvaluesfortheuidNumberandgidNumberattributes,WinSyncdoesnotsynchronizethesevaluesovertoIdentityManagement.
Instead,itcreatesnewUIDandGIDvaluesinIdentityManagement.
Asaresult,thevaluesforuidNumberandgidNumberaredifferentinActiveDirectoryandinIdentityManagement.
6.
4.
SETTINGUPACTIVEDIRECTORYFORSYNCHRONIZATIONSynchronizinguseraccountsisenabledwithinIdM.
Itisonlynecessarytosetupasynchronizationagreement(Section6.
5.
1,"CreatingSynchronizationAgreements").
However,theActiveDirectorydoesneedtobeconfiguredinawaythatallowstheIdentityManagementservertoconnecttoit.
6.
4.
1.
CreatinganActiveDirectoryUserforSynchronizationOntheWindowsserver,itisnecessarytocreatetheuserthattheIdMserverwillusetoconnecttotheActiveDirectorydomain.
WindowsIntegrationGuide96TheprocessforcreatingauserinActiveDirectoryiscoveredintheWindowsserverdocumentationathttp://technet.
microsoft.
com/en-us/library/cc732336.
aspx.
Thenewuseraccountmusthavetheproperpermissions:GrantthesynchronizationuseraccountReplicatingdirectorychangesrightstothesynchronizedActiveDirectorysubtree.
Replicatorrightsarerequiredforthesynchronizationusertoperformsynchronizationoperations.
Replicatorrightsaredescribedinhttp://support.
microsoft.
com/kb/303972.
AddthesynchronizationuserasamemberoftheAccountOperatorsandEnterpriseRead-onlyDomainControllersgroups.
ItisnotnecessaryfortheusertobelongtotheDomainAdminsgroup.
6.
4.
2.
SettingupanActiveDirectoryCertificateAuthorityTheIdentityManagementserverconnectstotheActiveDirectoryserverusingasecureconnection.
ThisrequiresthattheActiveDirectoryserverhaveanavailableCAcertificateorCAcertificatechainavailable,whichcanbeimportedintotheIdentityManagementsecuritydatabases,sothattheWindowsserverisatrustedpeer.
Whilethiscouldtechnicallybedonewithanexternal(toActiveDirectory)CA,mostdeploymentsshouldusetheCertificateServicesavailablewithActiveDirectory.
TheprocedureforsettingupandconfiguringcertificateservicesonActiveDirectoryiscoveredintheMicrosoftdocumentationathttp://technet.
microsoft.
com/en-us/library/cc772393(v=WS.
10).
aspx.
6.
5.
MANAGINGSYNCHRONIZATIONAGREEMENTS6.
5.
1.
CreatingSynchronizationAgreementsSynchronizationagreementsarecreatedontheIdMserverusingtheipa-replica-manageconnectcommandbecauseitcreatesaconnectiontotheActiveDirectorydomain.
ToestablishanencryptedconnectiontoActiveDirectory,IdMmusttotrusttheWindowsCAcertificate.
1.
Copytherootcertificateauthority(CA)certificatetotheIdMserver:a.
IfyourActiveDirectoryCAcertificateisself-signed:i.
ExporttheActiveDirectoryCAcertificateontheWindowsserver.
A.
PresstheSuperkey+RcombinationtoopentheRundialog.
B.
Entercertsrv.
mscandclickOK.
C.
Right-clickonthenameofthelocalCertificateAuthorityandchooseProperties.
D.
OntheGeneraltab,selectthecertificatetoexportintheCAcertificatesfieldandclickViewCertificate.
E.
OntheDetailstab,clickCopytoFiletostarttheCertificateExportWizard.
F.
ClickNext,andthenselectBase-64encodedX.
509(.
CER).
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS97G.
Specifyasuitabledirectoryandfilenamefortheexportedfile.
ClickNexttoexportthecertificate,andthenclickFinish.
H.
CopytheexportedcertificatetotheIdMservermachine.
b.
IfyourActiveDirectoryCAcertificateissignedbyanexternalCA:i.
TofindoutwhatcertificateistheCArootcertificate,displaythecertificatechain:#openssls_client-connectadserver.
example.
com:636CONNECTED(00000003)depth=1C=US,O=DemoCompany,OU=IT,CN=DemoCA-28verifyerror:num=20:unabletogetlocalissuercertificateverifyreturn:0---Certificatechain0s:/C=US/O=DemoCompany/OU=IT/CN=adserver.
example.
comi:/C=US/O=DemoCompany/OU=IT/CN=DemoCA-11s:/C=US/O=DemoCompany/OU=IT/CN=DemoCA-1i:/C=US/O=DemoCompany/OU=IT/CN=DemoRootCA2ThepreviousexampleshowsthattheActiveDirectoryserver'sCAcertificateissignedbyCN=DemoCA-1,whichissignedbyCN=DemoRootCA2.
ThismeansthatCN=DemoRootCA2istherootCA.
ii.
CopytheCAcertificatetotheIdMserver.
WindowsIntegrationGuide982.
RemoveanyexistingKerberoscredentialsontheIdMserver.
$kdestroy3.
Usetheipa-replica-managecommandtocreateaWindowssynchronizationagreement.
Thisrequiresthe--winsyncoption.
Ifpasswordswillbesynchronizedaswellasuseraccounts,thenalsousethe--passsyncoptionandsetapasswordtouseforPasswordSynchronization.
The--binddnand--bindpwoptionsgivetheusernameandpasswordofthesystemaccountontheActiveDirectoryserverthatIdMwillusetoconnecttotheActiveDirectoryserver.
$ipa-replica-manageconnect--winsync\--binddncn=administrator,cn=users,dc=example,dc=com\--bindpwWindows-secret\--passsyncsecretpwd\--cacert/etc/openldap/cacerts/windows.
cer\adserver.
example.
com-v--winsync:IdentifiesthisasaWindowssynchronizationagreement.
--binddn:IdMusesthisDNofanActiveDirectoryaccounttobindtotheremotedirectoryandsynchronizeattributes.
--bindpw:Passwordforthesynchronizationaccount.
--cacert:Fullpathandfilenametothe:ActiveDirectoryCAcertificate,iftheCAwasself-signed.
externalCAcertificate,iftheActiveDirectoryCAwassignedbyanexternalCA.
--win-subtree:DNoftheWindowsdirectorysubtreecontainingtheuserstosynchronize.
Thedefaultvalueiscn=Users,$SUFFIX.
AD_server_name:Fullyqualifieddomainname(FQDN)oftheActiveDirectorydomaincontroller.
4.
Whenprompted,entertheDirectoryManagerpassword.
5.
Optional.
ConfigurePasswordSynchronization,asinSection6.
6.
2,"SettingupPasswordSynchronization".
WithoutthePasswordSynchronizationclient,userattributesaresynchronizedbetweenthepeerservers,butpasswordsarenot.
NOTEThePasswordSynchronizationclientcapturespasswordchangesandthensynchronizesthembetweenActiveDirectoryandIdM.
Thismeansthatitsynchronizesnewpasswordsorpasswordupdates.
Existingpasswords,whicharestoredinahashedforminbothIdMandActiveDirectory,cannotbedecryptedorsynchronizedwhenthePasswordSynchronizationclientisinstalled,soexistingpasswordsarenotsynchronized.
Userpasswordsmustbechangedtoinitiatesynchronizationbetweenthepeerservers.
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS996.
5.
2.
ChangingtheBehaviorforSynchronizingUserAccountAttributesWhenthesynchronizationagreementiscreated,ithascertaindefaultbehaviorsdefinedforhowthesynchronizationprocesshandlestheuseraccountattributesduringsynchronization.
ThetypesofbehaviorsarethingslikehowtohandlelockoutattributesorhowtohandledifferentDNformats.
Thisbehaviorcanbechangedbyeditingthesynchronizationagreement.
Thesynchronizationagreementexistsasaspecialplug-inentryintheLDAPserverandeachattributebehaviorissetthroughanLDAPattribute.
Tochangethesynchronizationbehavior,usetheldapmodifycommandtomodifytheLDAPserverentrydirectly.
Forexample,accountlockoutattributesaresynchronizedbetweenIdMandActiveDirectorybydefault,butthiscanbedisabledbyeditingtheipaWinSyncAcctDisableattribute.
(ChangingthismeansthatifanaccountisdisabledinActiveDirectory,itisstillactiveinIdMandviceversa.
)[jsmith@ipaserver~]$ldapmodify-x-D"cn=directorymanager"-wpassworddn:cn=ipa-winsync,cn=plugins,cn=configchangetype:modifyreplace:ipaWinSyncAcctDisableipaWinSyncAcctDisable:nonemodifyingentry"cn=ipa-winsync,cn=plugins,cn=config"Thefollowingisanoverviewofsynchronizationsettingsattributes:GeneralUserAccountParametersipaWinSyncNewEntryFilter:Setsthesearchfiltertousetofindtheentrywhichcontainsthelistofobjectclassestoaddtonewuserentries.
Defaultvalue:(cn=ipaConfig)ipaWinSyncNewUserOCAttr:Setstheattributeintheconfigurationentrywhichactuallycontainsthelistofobjectclassestoaddtonewuserentries.
Defaultvalue:ipauserobjectclassesipaWinSyncHomeDirAttr:IdentifieswhichattributeintheentrycontainsthedefaultlocationofthePOSIXhomedirectory.
Defaultvalue:ipaHomesRootDiripaWinSyncUserAttr:SetsanadditionalattributewithaspecificvaluetoaddtoActiveDirectoryuserswhentheyaresynchronizedoverfromtheActiveDirectorydomain.
Iftheattributeismulti-valued,thenitcanbesetmultipletimes,andthesynchronizationprocessaddsallofthevaluestotheentry.
Example:ipaWinSyncUserAttr:attributeNameattributeValueNOTEThisonlysetstheattributevalueiftheentrydoesnotalreadyhavethatattributepresent.
Iftheattributeispresent,thentheentry'svalueisusedwhentheActiveDirectoryentryissynchronizedover.
WindowsIntegrationGuide100ipaWinSyncForceSync:SetswhetherexistingIdMusersthatmatchexistingADusersshouldbeforcedtobesynchronized.
Whensettotrue,suchIdMusersareautomaticallyeditedsothattheyaresynchronized.
Possiblevalues:true|falseIfanIdMuseraccounthasauidparameterwhichisidenticaltothesAMAccountNameinanexistingActiveDirectoryuser,thenthataccountisnotsynchronizedbydefault.
ThisattributetellsthesynchronizationservicetoaddthentUserandntUserDomainIdtotheIdMuserentriesautomatically,whichallowsthemtobesynchronized.
UserAccountLockParametersipaWinSyncAcctDisable:Setswhichwaytosynchronizeaccountlockoutattributes.
Itispossibletocontrolwhichaccountlockoutsettingsareineffect.
Forexample,to_admeansthatwhenaccountlockoutattributeissetinIdM,itsvalueissynchronizedovertoActiveDirectoryandoverridesthelocalActiveDirectoryvalue.
Bydefault,accountlockoutattributesaresynchronizedfrombothdomains.
Possiblevalues:both(default),to_ad,to_ds,noneipaWinSyncInactivatedFilter:SetsthesearchfiltertousetofindtheDNofthegroupusedtoholdinactivated(disabled)users.
Thisdoesnotneedtobechangedinmostdeployments.
Defaultvalue:(&(cn=inactivated)(objectclass=groupOfNames))GroupParametersipaWinSyncDefaultGroupAttr:Setstheattributeinthenewuseraccounttoreferencetoseewhatthedefaultgroupfortheuseris.
ThegroupnameintheentryisthenusedtofindthegidNumberfortheuseraccount.
Defaultvalue:ipaDefaultPrimaryGroupipaWinSyncDefaultGroupFilter:Setstheattributeinthenewuseraccounttoreferencetoseewhatthedefaultgroupfortheuseris.
ThegroupnameintheentryisthenusedtofindthegidNumberfortheuseraccount.
Defaultvalue:ipaDefaultPrimaryGroupRealmParametersipaWinSyncRealmAttr:Setstheattributewhichcontainstherealmnameintherealmentry.
Defaultvalue:cnipaWinSyncRealmFilter:SetsthesearchfiltertousetofindtheentrywhichcontainstheIdMrealmname.
Defaultvalue:(objectclass=krbRealmContainer)6.
5.
3.
ChangingtheSynchronizedWindowsSubtreeCreatingasynchronizationagreementautomaticallysetsthetwosubtreestouseasthesynchronizeduserdatabase.
InIdM,thedefaultiscn=users,cn=accounts,$SUFFIX,andforActiveDirectory,thedefaultisCN=Users,$SUFFIX.
ThevaluefortheActiveDirectorysubtreecanbesettoanon-defaultvaluewhenthesynchronizationCHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS101ThevaluefortheActiveDirectorysubtreecanbesettoanon-defaultvaluewhenthesynchronizationagreementiscreatedbyusingthe--win-subtreeoption.
Aftertheagreementiscreated,theActiveDirectorysubtreecanbechangedbyusingtheldapmodifycommandtoeditthensds7WindowsReplicaSubtreevalueinthesynchronizationagreemententry.
1.
Getthenameofthesynchronizationagreement,usingldapsearch.
Thissearchreturnsonlythevaluesforthednandnsds7WindowsReplicaSubtreeattributesinsteadoftheentireentry.
[jsmith@ipaserver~]$ldapsearch-xLLL-D"cn=directorymanager"-wpassword-p389-hipaserver.
example.
com-bcn=configobjectclass=nsdswindowsreplicationagreementdnnsds7WindowsReplicaSubtreedn:cn=meToWindowsBox.
example.
com,cn=replica,cn=dc\3Dexample\2Cdc\3Dcom,cn=mappingtree,cn=confignsds7WindowsReplicaSubtree:cn=users,dc=example,dc=com.
.
.
8dsquery*-scopebase-attrpwdPropertiespwdProperties1IfthevalueoftheattributepwdPropertiesissetto1,thepasswordcomplexitypolicyisenabledforthedomain.
NOTEIfyouareunsureifgrouppoliciesdefinedeviatingpasswordsettingsforOrganizationalUnits(ou),askyourgrouppolicyadministrator.
ToenabletheActiveDirectorypasswordcomplexitysettingforthewholedomain:1.
Rungpmc.
mscfromthecommandline.
2.
SelectGroupPolicyManagement.
3.
OpenForest:ad.
example.
com→Domains→ad.
example.
com.
4.
Right-clicktheDefaultDomainPolicyentryandselectEdit.
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS1055.
TheGroupPolicyManagementEditoropensautomatically.
6.
OpenComputerConfiguration→Policies→WindowsSettings→SecuritySettings→AccountPolicies→PasswordPolicy.
7.
EnablethePasswordmustmeetcomplexityrequirementsoptionandsave.
6.
6.
2.
SettingupPasswordSynchronizationInstallthePasswordSynchronizationServiceoneverydomaincontrollerintheActiveDirectorydomaininordertosynchronizeWindowspasswords.
1.
DownloadtheRedHat-PassSync-*.
msifiletotheActiveDirectorydomaincontroller:1.
LogintotheCustomerPortal.
2.
ClickDownloadsatthetopofthepage.
3.
SelectRedHatEnterpriseLinuxfromtheproductlist.
4.
SelectthemostrecentversionofRedHatEnterpriseLinux6orRedHatEnterpriseLinux7andarchitecture.
5.
DownloadWinSyncInstallerforthearchitectureoftheActiveDirectorydomaincontrollerbyclickingtheDownloadNowbutton.
2.
Double-clicktheMSIfiletoinstallit.
3.
ThePasswordSynchronrizationSetupwindowappears.
HitNexttobegininstalling.
WindowsIntegrationGuide1064.
FillintheinformationtoestablishtheconnectiontotheIdMserver.
TheIdMserverconnectioninformation,includingthehostnameandsecureportnumber.
TheusernameofthesystemuserwhichActiveDirectoryusestoconnecttotheIdMmachine.
ThisaccountisconfiguredautomaticallywhensynchronizationisconfiguredontheIdMserver.
Thedefaultaccountisuid=passsync,cn=sysaccounts,cn=etc,dc=example,dc=com.
Thepasswordsetinthe--passsyncoptionwhenthesynchronizationagreementwascreated.
ThesearchbaseforthepeoplesubtreeontheIdMserver.
TheActiveDirectoryserverconnectstotheIdMserversimilartoanldapsearchorreplicationoperation,soithastoknowwhereintheIdMsubtreetolookforuseraccounts.
Theusersubtreeiscn=users,cn=accounts,dc=example,dc=com.
Thecertificatetokenisnotusedatthistime,sothatfieldshouldbeleftblank.
HitNext,thenFinishtoinstallPasswordSynchronization.
5.
ImporttheIdMserver'sCAcertificateintothePassSynccertificatestore.
1.
DownloadtheIdMserver'sCAcertificatefromhttp://ipa.
example.
com/ipa/config/ca.
crt.
2.
CopytheIdMCAcertificatetotheActiveDirectoryserver.
3.
InstalltheIdMCAcertificateinthePasswordSynchronizationdatabase.
Forexample:CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS107cd"C:\ProgramFiles\RedHatDirectoryPasswordSynchronization"certutil.
exe-d.
-A-n"IPASERVER.
EXAMPLE.
COMIPACA"-tCT,,-a-iipaca.
crt6.
ReboottheWindowsmachinetostartPasswordSynchronization.
NOTETheWindowsmachinemustberebooted.
Withouttherebooting,PasswordHook.
dllisnotenabled,andpasswordsynchronizationwillnotfunction.
7.
Ifpasswordsforexistingaccountsshouldbesynchronized,resettheuserpasswords.
NOTEThePasswordSynchronizationclientcapturespasswordchangesandthensynchronizesthembetweenActiveDirectoryandIdM.
Thismeansthatitsynchronizesnewpasswordsorpasswordupdates.
Existingpasswords,whicharestoredinahashedforminbothIdMandActiveDirectory,cannotbedecryptedorsynchronizedwhenthePasswordSynchronizationclientisinstalled,soexistingpasswordsarenotsynchronized.
Userpasswordsmustbechangedtoinitiatesynchronizationbetweenthepeerservers.
Thefirstattempttosynchronizepasswords,whichhappenedwhenthePasswordSynchronizationapplicationisinstalled,willalwaysfailbecauseoftheSSLconnectionbetweentheDirectoryServerandActiveDirectorysynchronizationpeers.
Thetoolstocreatethecertificateandkeydatabasesisinstalledwiththe.
msi.
ThepasswordsynchronizationclientcannotsynchronizepasswordsformembersoftheIdMadmingroup.
Thisisanintendedbehaviortoprevent,forexample,passwordsynchronizationagentsorlowleveluseradministratorstochangepasswordsoftopleveladministrators.
NOTEPasswordsareonlyvalidatedonthesynchronizationsourcetomatchthepasswordpolicies.
ToverifyandenabletheActiveDirectorypasswordcomplexitypolicy,seeSection6.
6.
1,"SettinguptheWindowsServerforPasswordSynchronization".
[2]Thecnistreateddifferentlythanothersynchronizedattributes.
Itismappeddirectly(cntocn)whensynchronizingfromIdentityManagementtoActiveDirectory.
WhensynchronizingfromActiveDirectorytoIdentityManagement,however,cnismappedfromthenameattributeonWindowstothecnattributeinIdentityManagement.
WindowsIntegrationGuide108CHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUSTSynchronizationandtrustaretwopossibleapproachestoindirectintegration.
Synchronizationisgenerallydiscouraged,andRedHatrecommendstousetheapproachbasedonActiveDirectory(AD)trustinstead.
SeeSection1.
3,"IndirectIntegration"fordetails.
Thischapterdescribeshowtomigrateanexistingsynchronization-basedsetuptoADtrust.
ThefollowingmigratingoptionsareavailableinIdM:Section7.
1,"MigratefromSynchronizationtoTrustAutomaticallyUsingipa-winsync-migrate"Section7.
2,"MigratefromSynchronizationtoTrustManuallyUsingIDViews"7.
1.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTAUTOMATICALLYUSINGIPA-WINSYNC-MIGRATEIMPORTANTTheipa-winsync-migrateutilityisonlyavailableonsystemsrunningRedHatEnterpriseLinux7.
2orlater.
7.
1.
1.
HowMigrationUsingipa-winsync-migrateWorksTheipa-winsync-migrateutilitymigratesallsynchronizedusersfromanADforest,whilepreservingtheexistingconfigurationintheWinsyncenvironmentandtransferringitintotheADtrust.
ForeachADusercreatedbytheWinsyncagreement,ipa-winsync-migratecreatesanIDoverrideintheDefaultTrustView(seeSection8.
1,"ActiveDirectoryDefaultTrustView").
Afterthemigrationcompletes:TheIDoverridesfortheADusershavethefollowingattributescopiedfromtheoriginalentryinWinsync:Loginname(uid)UIDnumber(uidnumber)GIDnumber(gidnumber)Homedirectory(homedirectory)GECOSentry(gecos)TheuseraccountsintheADtrustkeeptheiroriginalconfigurationinIdM,whichincludes:POSIXattributesUsergroupsRole-basedaccesscontrolrulesHost-basedaccesscontrolrulesCHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUST109SELinuxmembershipsudorulesThenewADusersareaddedasmembersofanexternalIdMgroup.
TheoriginalWinsyncreplicationagreement,theoriginalsynchronizeduseraccounts,andalllocalcopiesoftheuseraccountsareremoved.
7.
1.
2.
HowtoMigrateUsingipa-winsync-migrateBeforeyoubegin:BackupyourIdMsetupusingtheipa-backuputility.
SeeBackingUpandRestoringIdentityManagementintheLinuxDomainIdentity,Authentication,andPolicyGuide.
Reason:ThemigrationaffectsasignificantpartoftheIdMconfigurationandmanyuseraccounts.
Creatingabackupenablesyoutorestoreyouroriginalsetupifnecessary.
Tomigrate:1.
Createatrustwiththesynchronizeddomain.
SeeChapter5,CreatingCross-forestTrustswithActiveDirectoryandIdentityManagement.
2.
Runipa-winsync-migrateandspecifytheADrealmandthehostnameoftheADdomaincontroller:#ipa-winsync-migrate--realmexample.
com--serverad.
example.
comIfaconflictoccursintheoverridescreatedbyipa-winsync-migrate,informationabouttheconflictisdisplayed,butthemigrationcontinues.
3.
UninstallthePasswordSyncservicefromtheADserver.
ThisremovesthesynchronizationagreementfromtheADdomaincontrollers.
Seetheipa-winsync-migrate(1)manpageformoredetailsabouttheutility.
7.
2.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTMANUALLYUSINGIDVIEWSYoucanuseIDviewstomanuallychangethePOSIXattributesthatADpreviouslygeneratedforADusers.
1.
Createabackupoftheoriginalsynchronizeduserorgroupentries.
2.
Createatrustwiththesynchronizeddomain.
Forinformationaboutcreatingtrusts,seeChapter5,CreatingCross-forestTrustswithActiveDirectoryandIdentityManagement.
3.
Foreverysynchronizeduserorgroup,preservetheUIDandGIDsgeneratedbyIdMbydoingoneofthefollowing:IndividuallycreateanIDviewappliedtothespecifichostandadduserIDoverridestotheview.
CreateuserIDoverridesintheDefaultTrustView.
WindowsIntegrationGuide110Fordetails,seeDefiningaDifferentAttributeValueforaUserAccountonDifferentHosts.
NOTEOnlyIdMuserscanmanageIDviews.
ADuserscannot.
4.
Deletetheoriginalsynchronizeduserorgroupentries.
ForgeneralinformationonusingIDviewsinActiveDirectoryenvironments,seeChapter8,UsingIDViewsinActiveDirectoryEnvironments.
CHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUST111CHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTSIDviewsenableyoutospecifynewvaluesforPOSIXuserorgroupattributes,aswellastodefineonwhichclienthostorhoststhenewvalueswillapply.
IntegrationsystemsotherthanIdentityManagement(IdM)sometimesgenerateUIDandGIDvaluesbasedonanalgorithmdifferentthanthealgorithmusedinIdM.
ByoverridingthepreviouslygeneratedvaluestomakethemcompliantwiththevaluesusedinIdM,aclientthatusedtobeamemberofanotherintegrationsystemcanbefullyintegratedwithIdM.
NOTEThischapteronlydescribesIDviewsfunctionalityrelatedtoActiveDirectory(AD).
ForgeneralinformationaboutIDviews,seetheLinuxDomainIdentity,Authentication,andPolicyGuide.
YoucanuseIDviewsinADenvironmentsforthefollowingpurposes:OverridingADUserAttributes,suchasPOSIXAttributesorSSHLoginDetailsSeeSection8.
3,"UsingIDViewstoDefineADUserAttributes"fordetails.
Migratingfromsynchronization-basedtotrust-basedintegrationSeeSection7.
2,"MigratefromSynchronizationtoTrustManuallyUsingIDViews"fordetails.
Performingper-hostgroupoverrideoftheIdMuserattributesSeeSection8.
4,"MigratingNISDomainstoIdM"fordetails.
8.
1.
ACTIVEDIRECTORYDEFAULTTRUSTVIEW8.
1.
1.
WhatIstheDefaultTrustViewTheDefaultTrustViewisthedefaultIDviewalwaysappliedtoADusersandgroupsintrust-basedsetups.
Itiscreatedautomaticallywhenyouestablishthetrustusingipa-adtrust-installandcannotbedeleted.
UsingtheDefaultTrustView,youcandefinecustomPOSIXattributesforADusersandgroups,thusoverridingthevaluesdefinedinAD.
Table8.
1.
ApplyingtheDefaultTrustViewValuesinADDefaultTrustViewResultLoginad_userad_user→ad_userUID111222→222GID111(novalue)→111NOTEWindowsIntegrationGuide112NOTETheDefaultTrustViewonlyacceptsoverridesforADusersandgroups,notforIdMusersandgroups.
ItisappliedontheIdMserverandclientsandthereforeonlyneedtoprovideoverridesforActiveDirectoryusersandgroups.
8.
1.
2.
OverridingtheDefaultTrustViewwithOtherIDViewsIfanotherIDviewappliedtothehostoverridestheattributevaluesintheDefaultTrustView,IdMappliesthevaluesfromthehost-specificIDviewontopoftheDefaultTrustView.
Ifanattributeisdefinedinthehost-specificIDview,IdMappliesthevaluefromthisview.
Ifanattributeisnotdefinedinthehost-specificIDview,IdMappliesthevaluefromtheDefaultTrustView.
TheDefaultTrustViewisalwaysappliedtoIdMserversandreplicasaswellastoADusersandgroups.
YoucannotassignadifferentIDviewtothem:theyalwaysapplythevaluesfromtheDefaultTrustView.
Table8.
2.
ApplyingaHost-SpecificIDViewonTopoftheDefaultTrustViewValuesinADDefaultTrustViewHost-SpecificViewResultLoginad_userad_user(novalue)→ad_userUID111222333→333GID111(novalue)333→3338.
1.
3.
IDOverridesonClientsBasedontheClientVersionTheIdMmastersalwaysapplyIDoverridesfromtheDefaultTrustView,regardlessofhowIdMclientsretrievethevalues:usingSSSDorusingSchemaCompatibilitytreerequests.
However,theavailabilityofIDoverridesfromhost-specificIDviewsislimited:Legacyclients:RHEL6.
3andearlier(SSSD1.
8andearlier)TheclientscanrequestaspecificIDviewtobeapplied.
Touseahost-specificIDviewonalegacyclient,changethebaseDNontheclientto:cn=id_view_name,cn=views,cn=compat,dc=example,dc=com.
RHEL6.
4to7.
0(SSSD1.
9to1.
11)Host-specificIDviewsontheclientsarenotsupported.
RHEL7.
1andlater(SSSD1.
12andlater)Fullsupport.
8.
2.
FIXINGIDCONFLICTSCHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS113IdMusesIDrangestoavoidcollisionsofPOSIXIDsfromdifferentdomains.
FordetailsonIDranges,seeIDRangesintheLinuxDomainIdentity,Authentication,andPolicyGuide.
POSIXIDsinIDviewsdonotuseaspecialrangetype,becauseIdMmustallowoverlapswithotherkindsofIDranges.
Forexample,ADuserscreatedthroughsynchronizationhavePOSIXIDsfromthesameIDrangeasIdMusers.
POSIXIDsaremanagedmanuallyinIDviewsontheIdMside.
Therefore,ifanIDcollisionoccurs,fixitbychangingtheconflictingIDs.
8.
3.
USINGIDVIEWSTODEFINEADUSERATTRIBUTESWithIDviews,youcanchangetheuserattributevaluesdefinedinAD.
Foracompletelistoftheattributes,seeAttributesanIDViewCanOverride.
Forexample:IfyouaremanagingamixedLinux-WindowsenvironmentandwanttomanuallydefinePOSIXattributesorSSHloginattributesforanADuser,buttheADpolicydoesnotallowit,youcanuseIDviewstooverridetheattributevalues.
WhentheADuserauthenticatestoclientsrunningSSSDorauthenticatesusingacompatLDAPtree,thenewvaluesareusedintheauthenticationprocess.
NOTEOnlyIdMuserscanmanageIDviews.
ADuserscannot.
Theprocessforoverridingtheattributevaluesfollowsthesesteps:1.
CreateanewIDview.
2.
AddauserIDoverrideintheIDview,andspecifytherequireattributevalue.
3.
ApplytheIDviewtoaspecifichost.
Fordetailsonhowtoperformthesesteps,seeDefiningaDifferentAttributeValueforaUserAccountonDifferentHostsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
8.
4.
MIGRATINGNISDOMAINSTOIDMIfyouaremanagingaLinuxenvironmentandwanttomigratedisparateNISdomainswithdifferentUIDsandGIDsintoamodernidentitymanagementsolution,youcanuseIDviewstosethostspecificUIDsandGIDsforexistinghoststopreventchangingthepermissionsonexistingfilesanddirectories.
Theprocessforthemigrationfollowsthesesteps:1.
CreatetheusersandgroupsintheIdMdomain.
Fordetails,seeAddingStageorActiveUsersAddingandRemovingUserGroups2.
UseIDviewsforexistinghoststooverridetheIDsIdMgeneratedduringtheusercreation:1.
CreateanindividualIDview.
2.
AddIDoverridesfortheusersandgroupstotheIDview.
WindowsIntegrationGuide1143.
AssigntheIDviewtothespecifichosts.
Fordetails,seeDefiningaDifferentAttributeValueforaUserAccountonDifferentHosts.
3.
InstallingandUninstallingIdentityManagementClientsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
4.
DecommissiontheNISdomains.
8.
5.
CONFIGURATIONOPTIONSFORUSINGSHORTNAMESTORESOLVEANDAUTHENTICATEUSERSANDGROUPSThissectiondescribesconfigurationoptionsenablingyoutouseshortuserorgroupnamesinsteadoftheuser_name@domainordomain\user_namefullyqualifiednamesformattoresolveandauthenticateusersandgroupsinanActiveDirectory(AD)environment.
Youcanconfigurethis:inIdentityManagement(IdM)thattrustsADonRedHatEnterpriseLinuxjoinedtoanADusingSSSD8.
5.
1.
HowDomainResolutionWorksYoucanusethedomainresolutionorderoptiontospecifytheorderinwhichalistofdomainsissearchedtoreturnamatchforagivenusername.
Youcansettheoption:ontheserver.
See:Section8.
5.
2.
1,"SettingtheDomainResolutionOrderGlobally"Section8.
5.
2.
2,"SettingtheDomainResolutionOrderforanIDview"ontheclient.
SeeSection8.
5.
3,"ConfiguringtheDomainResolutionOrderonanIdMClient"InenvironmentswithanActiveDirectorytrust,applyingoneorbothoftheserver-basedoptionsisrecommended.
Fromtheperspectiveofaparticularclient,thedomainresolutionorderoptioncanbesetinmorethanoneofthethreelocationsabove.
Theorderinwhichaclientconsultsthethreelocationsis:1.
thelocalsssd.
confconfiguration2.
theidviewconfiguration3.
theglobalIdMconfigurationOnlythedomainresolutionordersettingfoundfirstwillbeused.
InenvironmentsinwhichRedHatEnterpriseLinuxisdirectlyintegratedintoanAD,youcanonlysetthedomainresolutionorderontheclient.
NOTECHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS115NOTEYoumustusequalifiednamesif:AusernameexistsinmultipledomainsTheSSSDconfigurationincludesthedefault_domain_suffixoptionandyouwanttomakearequesttowardsadomainnotspecifiedwiththatoption8.
5.
2.
ConfiguringtheDomainResolutionOrderonanIdentityManagementServerSelecttheserver-basedconfigurationifalargenumberofclientsinadomainorsubdomainshoulduseanidenticaldomainresolutionorder.
8.
5.
2.
1.
SettingtheDomainResolutionOrderGloballySelectthisoptionforsettingthedomainresolutionordertoalltheclientsinthetrust.
Inordertodothis,usetheipaconfig-modcommand.
Forexample,inanIdMdomainthattrustsanADforestwithmultiplechilddomains:$ipaconfig-mod--domain-resolution-order='idm.
example.
com:ad.
example.
com:subdomain1.
ad.
example.
com:subdomain2.
ad.
example.
com'Maximumusernamelength:32Homedirectorybase:/home.
.
.
DomainResolutionOrder:idm.
example.
com:ad.
example.
com:subdomain1.
ad.
example.
com:subdomain2.
ad.
example.
com.
.
.
Withthedomainresolutionordersetinthisway,usersfromboththeIdMdomainandfromthetrustedADforestcanloginusingshortnamesonly.
8.
5.
2.
2.
SettingtheDomainResolutionOrderforanIDviewSelectthisoptiontoapplythesettingtotheclientsinaspecificdomain.
Forexample,onyoursubdomainserver,server.
idm.
example.
com,youobservemanymoreloginsfromthesubdomain2.
ad.
example.
comsubdomainthanfromsubdomain1.
ad.
example.
com.
Theglobalresolutionorderstates,however,thatthesubdomain1.
ad.
example.
comsubdomainuserdatabaseistriedoutbeforesubdomain2.
ad.
example.
comwhenresolvingusernames.
Tosetadifferentorderforcertainservers,setupadomainresolutionorderforaspecificview:1.
CreateanIDviewwiththedomainresolutionorderoptionset:$ipaidview-addexample_view--desc"IDviewforcustomshortnameresolutiononserver.
idm.
example.
com"--domain-resolution-ordersubdomain2.
ad.
example.
com:subdomain1.
ad.
example.
comAddedIDView"example_view"IDViewName:example_viewDescription:IDviewforcustomshortnameresolutiononserver.
idm.
example.
comDomainResolutionOrder:subdomain2.
ad.
example.
com:subdomain1.
ad.
example.
comWindowsIntegrationGuide1162.
Applytheviewontheclients.
Forexample:$ipaidview-applyexample_view--hostsserver.
idm.
example.
comAppliedIDView"example_view"hosts:server.
idm.
example.
comNumberofhoststheIDViewwasappliedto:1ForfurtherinformationonIDviews,seeChapter8,UsingIDViewsinActiveDirectoryEnvironments.
8.
5.
3.
ConfiguringtheDomainResolutionOrderonanIdMClientSetthedomainresolutionorderontheclientifyouwanttosetitonalownumberofclientsoriftheclientsaredirectlyconnectedtoAD.
Setthedomain_resolution_orderoption,inthe[sssd]section,inthe/etc/sssd/sssd.
conffile,forexample:domain_resolution_order=subdomain1.
ad.
example.
com,subdomain2.
ad.
example.
comForfurtherinformationonconfiguringthedomain_resolution_orderoption,seethesssd.
conf(5)manpage.
CHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS117APPENDIXA.
REVISIONHISTORYNotethatrevisionnumbersrelatetotheeditionofthismanual,nottoversionnumbersofRedHatEnterpriseLinux.
Revision7.
0-50WedMay272020FlorianDelehayeSeveralfixesandupdates.
Revision7.
0-49TueAug062019MarcMuehlfeldDocumentversionfor7.
7GApublication.
Revision7.
0-48WedJun052019MarcMuehlfeldUpdatedConfiguringTrustAgents,addedHowtheADProviderHandlesTrustedDomainsandChangingtheFormatofUserNamesDisplayedbySSSD.
Revision7.
0-47TueApr082019MarcMuehlfeldSeveralminorfixesandupdates.
Revision7.
0-46MonOct292018FilipHanzelkaPreparingdocumentfor7.
6GApublication.
Revision7.
0-45MonJun252018FilipHanzelkaAddedSwitchingBetweenSSSDandWinbindforSMBShareAccess.
Revision7.
0-44ThuApr52018FilipHanzelkaPreparingdocumentfor7.
5GApublication.
Revision7.
0-43WedFeb282018FilipHanzelkaUpdatedGPOSettingsSupportedbySSSD.
Revision7.
0-42MonFeb122018AnetateflováPetrováUpdatedCreatingaTwo-WayTrustwithaSharedSecret.
Revision7.
0-41MonJan292018AnetateflováPetrováMinorfixes.
Revision7.
0-40FriDec152017AnetateflováPetrováMinorfixes.
Revision7.
0-39MonDec62017AnetateflováPetrováUpdatedUsingSambaforActiveDirectoryIntegration.
Revision7.
0-38MonDec42017AnetateflováPetrováUpdatedDNSandRealmSettingsfortrusts.
Revision7.
0-37MonNov202017AnetateflováPetrováUpdatedCreatingaTwo-WayTrustwithaSharedSecret.
Revision7.
0-36MonNov62017AnetateflováPetrováMinorfixes.
Revision7.
0-35MonOct232017AnetateflováPetrováUpdatedActiveDirectoryEntriesandPOSIXAttributesandConfiguringanADDomainwithIDMappingasaProviderforSSSD.
Revision7.
0-34MonOct92017AnetateflováPetrováAddedConfigurationOptionsforUsingShortNames.
UpdatedTrustControllersandTrustAgents.
WindowsIntegrationGuide118Revision7.
0-33TueSep262017AnetateflováPetrováUpdatedtheautodiscoverysectionintheSSSDchapter.
Addedtwosectionsonconfiguringtrusteddomains.
Revision7.
0-32TueJul182017AnetateflováPetrováDocumentversionfor7.
4GApublication.
Revision7.
0-31TueMay232017AnetateflováPetrováAminorfixforAboutSecurityIDMapping.
Revision7.
0-30MonApr242017AnetateflováPetrováMinorfixesforDefiningWindowsIntegration.
Revision7.
0-29MonApr102017AnetateflováPetrováUpdatedDirectIntegration.
Revision7.
0-28MonMar272017AnetateflováPetrováMovedAllowingUserstoChangeOtherUsers'PasswordsCleanlytotheLinuxDomainIdentityguideasEnablingPasswordReset.
UpdatedSupportedWindowsPlatformsfortrusts.
Fixedbrokenlinks.
Otherminorupdates.
Revision7.
0-27MonFeb272017AnetateflováPetrováUpdatedportrequirementsfortrusts.
Minorrestructuringfortrustandsync.
Otherminorupdates.
Revision7.
0-26WedNov232016AnetateflováPetrováAddedipa-winsync-migrate.
Minorfixesforthetrust,SSSD,andsynchronizationchapters.
Revision7.
0-25TueOct182016AnetateflováPetrováVersionfor7.
3GApublication.
Revision7.
0-24ThuJul282016MarcMuehlfeldUpdateddiagrams,addedKerberosflagsforservicesandhosts,otherminorfixes.
Revision7.
0-23ThuJun092016MarcMuehlfeldUpdatedthesynchronizationchapter.
RemovedtheKerberoschapter.
Otherminorfixes.
Revision7.
0-22TueFeb092016AnetaPetrováUpdatedrealmd,removedindex,movedapartofIDviewstotheLinuxDomainIdentityguide,otherminorupdates.
Revision7.
0-21FriNov132015AnetaPetrováVersionfor7.
2GAreleasewithminorupdates.
Revision7.
0-20ThuNov122015AnetaPetrováVersionfor7.
2GArelease.
Revision7.
0-19FriSep182015TomáapekUpdatedthesplashpagesortorder.
Revision7.
0-18ThuSep102015AnetaPetrováUpdatedtheoutputformat.
Revision7.
0-17MonJul272015AnetaPetrováAddedGPO-basedaccesscontrol,anumberofotherminorchanges.
Revision7.
0-16ThuApr022015TomáapekAddedipa-advise,extendedCIFSsharewithSSSD,admonitionfortheIdentityManagementforUNIXextension.
Revision7.
0-15FriMar132015TomáapekAsyncupdatewithlast-minuteeditsfor7.
1.
APPENDIXA.
REVISIONHISTORY119Revision7.
0-13WedFeb252015TomáapekVersionfor7.
1GArelease.
Revision7.
0-11FriDec052014TomáapekRebuildtoupdatethesortorderonthesplashpage.
Revision7.
0-7MonSep152014TomáapekSection5.
3CreatingTruststemporarilyremovedforcontentupdates.
Revision7.
0-5June27,2014EllaDeonBallardImprovingSamba+Kerberos+Winbindchapters.
Revision7.
0-4June13,2014EllaDeonBallardAddingKerberosrealmchapter.
Revision7.
0-3June11,2014EllaDeonBallardInitialrelease.
WindowsIntegrationGuide120
comMarcMuehlfeldRedHatCustomerContentServicesFilipHanzelkaRedHatCustomerContentServicesLucieMaňáskováRedHatCustomerContentServicesAnetateflováPetrováRedHatCustomerContentServicesTomáapekRedHatCustomerContentServicesEllaDeonBallardRedHatCustomerContentServicesLegalNoticeCopyright2020RedHat,Inc.
ThisdocumentislicensedbyRedHatundertheCreativeCommonsAttribution-ShareAlike3.
0UnportedLicense.
Ifyoudistributethisdocument,oramodifiedversionofit,youmustprovideattributiontoRedHat,Inc.
andprovidealinktotheoriginal.
Ifthedocumentismodified,allRedHattrademarksmustberemoved.
RedHat,asthelicensorofthisdocument,waivestherighttoenforce,andagreesnottoassert,Section4dofCC-BY-SAtothefullestextentpermittedbyapplicablelaw.
RedHat,RedHatEnterpriseLinux,theShadowmanlogo,theRedHatlogo,JBoss,OpenShift,Fedora,theInfinitylogo,andRHCEaretrademarksofRedHat,Inc.
,registeredintheUnitedStatesandothercountries.
LinuxistheregisteredtrademarkofLinusTorvaldsintheUnitedStatesandothercountries.
JavaisaregisteredtrademarkofOracleand/oritsaffiliates.
XFSisatrademarkofSiliconGraphicsInternationalCorp.
oritssubsidiariesintheUnitedStatesand/orothercountries.
MySQLisaregisteredtrademarkofMySQLABintheUnitedStates,theEuropeanUnionandothercountries.
Node.
jsisanofficialtrademarkofJoyent.
RedHatisnotformallyrelatedtoorendorsedbytheofficialJoyentNode.
jsopensourceorcommercialproject.
TheOpenStackWordMarkandOpenStacklogoareeitherregisteredtrademarks/servicemarksortrademarks/servicemarksoftheOpenStackFoundation,intheUnitedStatesandothercountriesandareusedwiththeOpenStackFoundation'spermission.
Wearenotaffiliatedwith,endorsedorsponsoredbytheOpenStackFoundation,ortheOpenStackcommunity.
Allothertrademarksarethepropertyoftheirrespectiveowners.
AbstractHeterogeneousITenvironmentsoftencontainvariousdifferentdomainsandoperatingsystemsthatneedtobeabletoseamlesslycommunicate.
RedHatEnterpriseLinuxoffersmultiplewaystotightlyintegrateLinuxdomainswithActiveDirectory(AD)onMicrosoftWindows.
Theintegrationispossibleondifferentdomainobjectsthatincludeusers,groups,services,orsystems.
Thisguidealsocoversdifferentintegrationscenarios,rangingfromlightweightADpass-throughauthenticationtofull-fledgedKerberostrustedrealms.
Inadditiontothisguide,youcanfinddocumentationonotherfeaturesandservicesrelatedtoRedHatEnterpriseLinuxIdentityManagementinthefollowingguides:TheLinuxDomainIdentity,Authentication,andPolicyGuidedocumentsRedHatIdentityManagement,asolutionthatprovidesacentralizedandunifiedwaytomanageidentitystoresaswellasauthenticationandauthorizationpoliciesinaLinux-baseddomain.
TheSystem-LevelAuthenticationGuidedocumentsdifferentapplicationsandservicesavailabletoconfigureauthenticationonlocalsystems,includingtheauthconfigutility,theSystemSecurityServicesDaemon(SSSD)service,thePluggableAuthenticationModule(PAM)framework,Kerberos,thecertmongerutility,andsinglesign-on(SSO)forapplications.
TableofContentsCHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTS1.
1.
DEFININGWINDOWSINTEGRATION1.
2.
DIRECTINTEGRATION1.
3.
INDIRECTINTEGRATIONPARTI.
ADDINGASINGLELINUXSYSTEMTOANACTIVEDIRECTORYDOMAINCHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD2.
1.
HOWTHEADPROVIDERHANDLESTRUSTEDDOMAINS2.
2.
CONFIGURINGANADPROVIDERFORSSSD2.
3.
AUTOMATICKERBEROSHOSTKEYTABRENEWAL2.
4.
ENABLINGDYNAMICDNSUPDATES2.
5.
USINGRANGERETRIEVALSEARCHESWITHSSSD2.
6.
GROUPPOLICYOBJECTACCESSCONTROL2.
7.
CREATINGUSERPRIVATEGROUPSAUTOMATICALLYUSINGSSSD2.
8.
SSSDCLIENTSANDACTIVEDIRECTORYDNSSITEAUTODISCOVERY2.
9.
TROUBLESHOOTINGSSSDCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN3.
1.
SUPPORTEDDOMAINTYPESANDCLIENTS3.
2.
PREREQUISITESFORUSINGREALMD3.
3.
REALMDCOMMANDS3.
4.
DISCOVERINGANDJOININGIDENTITYDOMAINS3.
5.
REMOVINGASYSTEMFROMANIDENTITYDOMAIN3.
6.
LISTINGDOMAINS3.
7.
MANAGINGLOGINPERMISSIONSFORDOMAINUSERS3.
8.
CHANGINGDEFAULTUSERCONFIGURATION3.
9.
ADDITIONALCONFIGURATIONFORTHEACTIVEDIRECTORYDOMAINENTRYCHAPTER4.
USINGSAMBAFORACTIVEDIRECTORYINTEGRATION4.
1.
USINGWINBINDDTOAUTHENTICATEDOMAINUSERS4.
2.
USINGSMBSHARESWITHSSSDANDWINBIND4.
3.
ADDITIONALRESOURCESPARTII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:CROSS-FORESTTRUSTCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT5.
1.
INTRODUCTIONTOCROSS-FORESTTRUSTS5.
2.
CREATINGCROSS-FORESTTRUSTS5.
3.
MANAGINGANDCONFIGURINGACROSS-FORESTTRUSTENVIRONMENT5.
4.
CHANGINGTHELDAPSEARCHBASEFORUSERSANDGROUPSINATRUSTEDACTIVEDIRECTORYDOMAIN5.
5.
CHANGINGTHEFORMATOFUSERNAMESDISPLAYEDBYSSSD5.
6.
RESTRICTINGIDENTITYMANAGEMENTORSSSDTOSELECTEDACTIVEDIRECTORYSERVERSORSITESINATRUSTEDACTIVEDIRECTORYDOMAIN5.
7.
ACTIVEDIRECTORYTRUSTFORLEGACYLINUXCLIENTS5.
8.
TROUBLESHOOTINGCROSS-FORESTTRUSTSPARTIII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:SYNCHRONIZATIONCHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS6.
1.
SUPPORTEDWINDOWSPLATFORMS4457910101014141515171819202020202124252526272929293031323240638182838487899090TableofContents16.
2.
ABOUTACTIVEDIRECTORYANDIDENTITYMANAGEMENT6.
3.
ABOUTSYNCHRONIZEDATTRIBUTES6.
4.
SETTINGUPACTIVEDIRECTORYFORSYNCHRONIZATION6.
5.
MANAGINGSYNCHRONIZATIONAGREEMENTS6.
6.
MANAGINGPASSWORDSYNCHRONIZATIONCHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUST7.
1.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTAUTOMATICALLYUSINGIPA-WINSYNC-MIGRATE7.
2.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTMANUALLYUSINGIDVIEWSCHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS8.
1.
ACTIVEDIRECTORYDEFAULTTRUSTVIEW8.
2.
FIXINGIDCONFLICTS8.
3.
USINGIDVIEWSTODEFINEADUSERATTRIBUTES8.
4.
MIGRATINGNISDOMAINSTOIDM8.
5.
CONFIGURATIONOPTIONSFORUSINGSHORTNAMESTORESOLVEANDAUTHENTICATEUSERSANDGROUPSAPPENDIXA.
REVISIONHISTORY90939697104109109110112112113114114115118WindowsIntegrationGuide2TableofContents3CHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTSITenvironmentshaveastructure.
Thesystemsinthemarearrangedwithapurpose.
Integratingtwoseparateinfrastructuresrequiresanassessmentofthepurposeofeachofthoseenvironmentsandanunderstandingofhowandwheretheyinteract.
1.
1.
DEFININGWINDOWSINTEGRATIONWindowsintegrationcanmeanverydifferentthings,dependingontherequiredinteractionbetweentheLinuxenvironmentandtheWindowsenvironment.
ItcouldmeanthatindividualLinuxsystemsareenrolledintoaWindowsdomain,itcouldmeanthataLinuxdomainisconfiguredtobeapeertotheWindowsdomain,oritcouldsimplymeanthatinformationiscopiedbetweenenvironments.
ThereareseveralpointsofcontactbetweenaWindowsdomainandLinuxsystems.
Eachofthesepointsrevolvearoundidentifyingdifferentdomainobjects(users,groups,systems,services)andtheserviceswhichareusedinthatidentification.
UserIdentitiesandAuthenticationWhereareuseraccountslocated;inacentralauthenticationsystemrunningonWindows(ADdomain)orinacentralidentityandauthenticationserverrunningonLinuxHowareusersauthenticatedonaLinuxsystem;throughalocalLinuxauthenticationsystemoracentralauthenticationsystemrunningonWindowsHowisgroupmembershipconfiguredforusersHowisthatgroupmembershipdeterminedWillusersauthenticateusingausername/passwordpair,Kerberostickets,certificates,oracombinationofmethodsPOSIXattributesarerequiredtoaccessservicesonLinuxmachines.
Howaretheseattributesstored:aretheysetintheWindowsdomain,configuredlocallyontheLinuxsystem,ordynamicallymapped(forUID/GIDnumbersandWindowsSIDs)WhatuserswillbeaccessingwhatresourcesWillWindows-definedusersaccessLinuxresourcesWillLinux-definedusersaccessWindowsresourcesInmostenvironments,theActiveDirectorydomainisthecentralhubforuserinformation,whichmeansthatthereneedstobesomewayforLinuxsystemstoaccessthatuserinformationforauthenticationrequests.
Therealquestionthenishowtoobtainthatuserinformationandhowmuchofthatinformationisavailabletoexternalsystems.
TherealsoneedstobeabalancebetweeninformationrequiredforLinuxsystems(POSIXattributes)andLinuxusers(certainapplicationadministrators)andhowthatinformationismanaged.
HostandServicePrincipalsWhatresourceswillbeaccessedWhatauthenticationprotocolsarerequiredHowwillKerberosticketsbeobtainedHowwillSSLcertificatesberequestedorverifiedWillusersneedaccesstoasingledomainortobothLinuxandWindowsdomainsDNSDomains,Queries,andNameResolutionWindowsIntegrationGuide4WhatwillbetheDNSconfigurationIsthereasingleDNSdomainAretheresubdomainsHowwillsystemhostnamesberesolvedHowwillservicediscoverybeconfiguredSecurityPoliciesWhereareaccesscontrolinstructionssetWhichadministratorsareconfiguredforeachdomainChangeManagementHowfrequentlyaresystemsaddedtothedomainIftheunderlyingconfigurationforsomethingrelatedtoWindowsintegrationischanged,forexampletheDNSservice,howarethosechangespropagatedIsconfigurationmaintainedthroughdomain-relatedtoolsoraprovisioningsystemDoestheintegrationpathrequireadditionalapplicationsorconfigurationontheWindowsserverAsimportantaswhichelementsinthedomainsareintegrated,ishowthatintegrationismaintained.
Ifaparticularinstrumentofintegrationisheavilymanual,yettheenvironmenthasalargenumberofsystemswhicharefrequentlyupdated,thenthatoneinstrumentmaynotworkforthatenvironmentfromamaintenancestandpoint.
ThefollowingsectionsoutlinethemainscenariosforintegrationwithWindows.
Indirectintegration,LinuxsystemsareconnectedtoActiveDirectorywithoutanyadditionalintermediaries.
Indirectintegration,ontheotherhand,involvesanidentityserverthatcentrallymanagesLinuxsystemsandconnectsthewholeenvironmenttoActiveDirectoryoftheserver-to-serverlevel.
1.
2.
DIRECTINTEGRATIONYouneedtwocomponentstoconnectaLinuxsystemtoActiveDirectory(AD).
Onecomponentinteractswiththecentralidentityandauthenticationsource,whichisADinthiscase.
Theothercomponentdetectsavailabledomainsandconfiguresthefirstcomponenttoworkwiththerightidentitysource.
TherearedifferentoptionsthatcanbeusedtoretrieveinformationandperformauthenticationagainstAD.
Amongthemare:NativeLDAPandKerberosPAMandNSSmodulesAmongthesemodulesarenss_ldap,pam_ldap,andpam_krb5.
AsPAMandNSSmodulesareloadedintoeveryapplicationprocess,theydirectlyaffecttheexecutionenvironment.
Withnocaching,offlinesupport,orsufficientprotectionofaccesscredentials,useofthebasicLDAPandKerberosmodulesforNSSandPAMisdiscouragedduetotheirlimitedfunctionality.
SambaWinbindSambaWinbindhadbeenatraditionalwayofconnectingLinuxsystemstoAD.
WinbindemulatesaWindowsclientonaLinuxsystemandisabletocommunicatetoADservers.
Notethat:CHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTS5TheWinbindservicemustberunningifyouconfiguredSambaasadomainmember.
DirectintegrationwithWinbindinamulti-forestADsetuprequiresbidirectionaltrusts.
Remoteforestsmusttrustthelocalforesttoensurethattheidmap_adplug-inhandlesremoteforestuserscorrectly.
SystemSecurityServicesDaemon(SSSD)TheprimaryfunctionofSSSDistoaccessaremoteidentityandauthenticationresourcethroughacommonframeworkthatprovidescachingandofflinesupporttothesystem.
SSSDishighlyconfigurable;itprovidesPAMandNSSintegrationandadatabasetostorelocalusers,aswellascoreandextendeduserdataretrievedfromacentralserver.
SSSDistherecommendedcomponenttoconnectaLinuxsystemwithanidentityserverofyourchoice,beitActiveDirectory,IdentityManagement(IdM)inRedHatEnterpriseLinux,oranygenericLDAPorKerberosserver.
Notethat:DirectintegrationwithSSSDworksonlywithinasingleADforestbydefault.
Remoteforestsmusttrustthelocalforesttoensurethattheidmap_adplug-inhandlesremoteforestuserscorrectly.
ThemainreasontotransitionfromWinbindtoSSSDisthatSSSDcanbeusedforbothdirectandindirectintegrationandallowstoswitchfromoneintegrationapproachtoanotherwithoutsignificantmigrationcosts.
ThemostconvenientwaytoconfigureSSSDorWinbindinordertodirectlyintegrateaLinuxsystemwithADistousetherealmdservice.
Itallowscallerstoconfigurenetworkauthenticationanddomainmembershipinastandardway.
Therealmdserviceautomaticallydiscoversinformationaboutaccessibledomainsandrealmsanddoesnotrequireadvancedconfigurationtojoinadomainorrealm.
DirectintegrationisasimplewaytointroduceLinuxsystemstoADenvironment.
However,astheshareofLinuxsystemsgrows,thedeploymentsusuallyseetheneedforabettercentralizedmanagementoftheidentity-relatedpoliciessuchashost-basedaccesscontrol,sudo,orSELinuxusermappings.
Atfirst,theconfigurationoftheseaspectsoftheLinuxsystemscanbemaintainedinlocalconfigurationfiles.
Withagrowingnumberofsystemsthough,distributionandmanagementoftheconfigurationfilesiseasierwithaprovisioningsystemsuchasRedHatSatellite.
Thisapproachcreatesanoverheadofchangingtheconfigurationfilesandthendistributingthem.
Whendirectintegrationdoesnotscaleanymore,itismorebeneficialtoconsiderindirectintegrationdescribedinthenextsection.
1.
2.
1.
SupportedWindowsPlatformsfordirectintegrationYoucandirectlyintegrateyourLinuxmachinewithActiveDirectoryforeststhatusethefollowingforestanddomainfunctionallevels:Forestfunctionallevelrange:WindowsServer2008-WindowsServer2016[1]Domainfunctionallevelrange:WindowsServer2008-WindowsServer2016[1]Directintegrationhasbeentestedonthefollowingsupportedoperatingsystemsusingthementionedfunctionallevels:WindowsServer2019WindowsServer2016WindowsIntegrationGuide6WindowsServer2012R21.
3.
INDIRECTINTEGRATIONThemainadvantageoftheindirectintegrationistomanageLinuxsystemsandpoliciesrelatedtothosesystemscentrallywhileenablingusersfromActiveDirectory(AD)domainstotransparentlyaccessLinuxsystemsandservices.
Therearetwodifferentapproachestotheindirectintegration:Trust-basedsolutionTherecommendedapproachistoleverageIdentityManagement(IdM)inRedHatEnterpriseLinuxasthecentralservertocontrolLinuxsystemsandthenestablishcross-realmKerberostrustwithAD,enablingusersfromADtologontoandtousesinglesign-ontoaccessLinuxsystemsandresources.
ThissolutionusestheKerberoscapabilitytoestablishtrustsbetweendifferentidentitysources.
IdMpresentsitselftoADasaseparateforestandtakesadvantageoftheforest-leveltrustssupportedbyAD.
Incomplexenvironments,asingleIdMforestcanbeconnectedtomultipleADforests.
Thissetupenablesbetterseparationofdutiesfordifferentfunctionsintheorganization.
ADadministratorscanfocusonusersandpoliciesrelatedtouserswhileLinuxadministratorshavefullcontrolovertheLinuxinfrastructure.
Insuchacase,theLinuxrealmcontrolledbyIdMisanalogoustoanADresourcedomainorrealmbutwithLinuxsystemsinit.
NOTEInWindows,everydomainisaKerberosrealmandaDNSdomainatthesametime.
EverydomainmanagedbythedomaincontrollerneedstohaveitsowndedicatedDNSzone.
ThesameapplieswhenIdMistrustedbyADasaforest.
ADexpectsIdMtohaveitsownDNSdomain.
Forthetrustsetuptowork,theDNSdomainneedstobededicatedtotheLinuxenvironment.
Notethatintrustenvironments,IdMenablesyoutouseIDviewstoconfigurePOSIXattributesforADusersontheIdMserver.
Fordetails,see:Chapter8,UsingIDViewsinActiveDirectoryEnvironmentsSSSDClient-sideViewsintheSystem-LevelAuthenticationGuideSynchronization-basedsolutionAnalternativetoatrust-basedsolutionistoleverageusersynchronizationcapability,alsoavailableinIdMorRedHatDirectoryServer(RHDS),allowinguseraccounts(andwithRHDSalsogroupaccounts)tobesynchronizedfromADtoIdMorRHDS,butnotintheoppositedirection.
Usersynchronizationhascertainlimitations,including:duplicationofuserstheneedtosynchronizepasswords,whichrequiresaspecialcomponentonalldomaincontrollersinanADdomaintobeabletocapturepasswords,allusersmustfirstmanuallychangethemsynchronizationsupportsonlyasingledomainonlyonedomaincontrollerinADcanbeusedtosynchronizedatatooneinstanceofIdMorRHDSCHAPTER1.
WAYSTOINTEGRATEACTIVEDIRECTORYANDLINUXENVIRONMENTS7Insomeintegrationscenarios,theusersynchronizationmaybetheonlyavailableoption,butingeneral,useofthesynchronizationapproachisdiscouragedinfavorofthecross-realmtrust-basedintegration.
[1]WindowsServer2019doesnotintroduceanewfunctionallevel.
ThehighestfunctionallevelWindowsServer2019usesareWindowsServer2016.
WindowsIntegrationGuide8PARTI.
ADDINGASINGLELINUXSYSTEMTOANACTIVEDIRECTORYDOMAINPARTI.
ADDINGASINGLELINUXSYSTEMTOANACTIVEDIRECTORYDOMAIN9CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSDTheSystemSecurityServicesDaemon(SSSD)isasystemservicetoaccessremotedirectoriesandauthenticationmechanisms.
Itconnectsalocalsystem(anSSSDclient)toanexternalback-endsystem(adomain).
ThisprovidestheSSSDclientwithaccesstoidentityandauthenticationremoteservicesusinganSSSDprovider.
Forexample,theseremoteservicesinclude:anLDAPdirectory,anIdentityManagement(IdM)orActiveDirectory(AD)domain,oraKerberosrealm.
WhenusedasanidentitymanagementserviceforADintegration,SSSDisanalternativetoservicessuchasNISorWinbind.
ThischapterdescribeshowSSSDworkswithAD.
FormoredetailsonSSSD,seetheSystem-LevelAuthenticationGuide.
2.
1.
HOWTHEADPROVIDERHANDLESTRUSTEDDOMAINSThissectiondescribeshowSSSDhandlestrusteddomainsifyousetid_provider=adinthe/etc/sssd/sssd.
conffile.
SSSDonlysupportsdomainsinasingleActiveDirectoryforest.
IfSSSDrequiresaccesstomultipledomainsfrommultipleforests,considerusingIdMwithtrusts(preferred)orthewinbinddserviceinsteadofSSSD.
Bydefault,SSSDdiscoversalldomainsintheforestand,ifarequestforanobjectinatrusteddomainarrives,SSSDtriestoresolveit.
Ifthetrusteddomainsarenotreachableorgeographicallydistant,whichmakesthemslow,youcansetthead_enabled_domainsparameterin/etc/sssd/sssd.
conftolimitfromwhichtrusteddomainsSSSDresolvesobjects.
Bydefault,youmustusefully-qualifiedusernamestoresolveusersfromtrusteddomains.
2.
2.
CONFIGURINGANADPROVIDERFORSSSDTheADproviderenablesSSSDtousetheLDAPidentityproviderandtheKerberosauthenticationproviderwithoptimizationsforADenvironments.
2.
2.
1.
OverviewoftheIntegrationOptionsLinuxandWindowssystemsusedifferentidentifiersforusersandgroups:LinuxusesuserIDs(UID)andgroupIDs(GID).
SeeManagingUsersandGroupsintheSystemAdministrator'sGuide.
LinuxUIDsandGIDsarecompliantwiththePOSIXstandard.
WindowsusesecurityIDs(SID).
IMPORTANTDonotusethesameusernameinWindowsandActiveDirectory.
UsersauthenticatingtoaRedHatEnterpriseLinuxsystem,includingADusers,musthaveaUIDandGIDassigned.
Forthispurpose,SSSDprovidesthefollowingintegrationoptions:AutomaticallygeneratenewUIDsandGIDsforADusersSSSDcanusetheSIDofanADusertoalgorithmicallygeneratePOSIXIDsinaprocesscalledIDWindowsIntegrationGuide10SSSDcanusetheSIDofanADusertoalgorithmicallygeneratePOSIXIDsinaprocesscalledIDmapping.
IDmappingcreatesamapbetweenSIDsinADandIDsonLinux.
WhenSSSDdetectsanewADdomain,itassignsarangeofavailableIDstothenewdomain.
Therefore,eachADdomainhasthesameIDrangeoneverySSSDclientmachine.
WhenanADuserlogsintoanSSSDclientmachineforthefirsttime,SSSDcreatesanentryfortheuserintheSSSDcache,includingaUIDbasedontheuser'sSIDandtheIDrangeforthatdomain.
BecausetheIDsforanADuseraregeneratedinaconsistentwayfromthesameSID,theuserhasthesameUIDandGIDwhenloggingintoanyRedHatEnterpriseLinuxsystem.
SeeSection2.
2.
2,"ConfiguringanADDomainwithIDMappingasaProviderforSSSD".
NOTEWhenallclientsystemsuseSSSDtomapSIDstoLinuxIDs,themappingisconsistent.
Ifsomeclientsusedifferentsoftware,chooseoneofthefollowing:Ensurethatthesamemappingalgorithmisusedonallclients.
UseexplicitPOSIXattributes,asdescribedinUsePOSIXattributesdefinedinAD.
UsePOSIXattributesdefinedinADADcancreateandstorePOSIXattributes,suchasuidNumber,gidNumber,unixHomeDirectory,orloginShell.
WhenusingIDmappingdescribedinAutomaticallygeneratenewUIDsandGIDsforADusers,SSSDcreatesnewUIDsandGIDs,whichoverridesthevaluesdefinedinAD.
TokeeptheAD-definedvalues,youmustdisableIDmappinginSSSD.
SeeSection2.
2.
3,"ConfiguringSSSDtoUsePOSIXAttributesDefinedinAD".
2.
2.
2.
ConfiguringanADDomainwithIDMappingasaProviderforSSSDPrerequisitesMakesurethatboththeADsystemandtheLinuxsystemareproperlyconfigured:Verifytheconfigurationfornameresolution.
Inparticular,verifytheDNSSRVrecords.
Forexample,foradomainnamedad.
example.
com:ToverifytheDNSSRVLDAPrecords:#dig-tSRV_ldap.
_tcp.
ad.
example.
comToverifyADrecords:#dig-tSRV_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
comIfyoulaterconnectSSSDtoaparticularADdomaincontroller,itisnotnecessarytoverifytheDNSSRVrecords.
CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD11Verifythatsystemtimeonbothsystemsissynchronized.
ThisensuresthatKerberosisabletoworkproperly.
OpentherequiredportsonboththeLinuxsystemandallADdomaincontrollersinbothdirections:fromtheLinuxsystemtotheADdomaincontrollerandback.
Table2.
1.
PortsRequiredforDirectIntegrationofLinuxSystemsintoADUsingSSSDServicePortProtocolNotesDNS53UDPandTCPLDAP389UDPandTCPKerberos88UDPandTCPKerberos464UDPandTCPUsedbykadminforsettingandchangingapasswordLDAPGlobalCatalog3268TCPIftheid_provider=adoptionisbeingusedNTP123UDPOptionalConfiguretheLocalSystemRedHatrecommendsusingtherealmjoincommandtoconfigurethesystem.
SeeChapter3,UsingrealmdtoConnecttoanActiveDirectoryDomain.
Therealmdsuiteeditsallrequiredconfigurationfilesautomatically.
Forexample:#realmjoinad.
example.
comIfyoudonotwanttouserealmd,youcanconfigurethesystemmanually.
SeeManuallyConnectinganSSSDClienttoanActiveDirectoryDomainintheRedHatKnowledgebase.
Optional:ConfigureUserHomeDirectoriesandShellsThepam_oddjob_mkhomedir.
solibraryautomaticallycreateshomedirectorieswhenusersfirstlogintotheLinuxsystem.
Bydefault,SSSDretrievestheformatofthehomedirectoryfromtheADidentityprovider.
TocustomizethedirectoryformatonLinuxclients:1.
Openthe/etc/sssd/sssd.
conffile.
2.
Inthe[domain]section,useoneoftheseoptions:fallback_homedirsetsafallbackhomedirectoryformat,whichisusedonlyifahomedirectoryisnotdefinedinADoverride_homedirsetsahomedirectorytemplate,whichalwaysoverridesthehomedirectorydefinedinADForexample,toalwaysusetheformat/home/domain_name/user_name:WindowsIntegrationGuide12[domain/EXAMPLE][.
.
.
filetruncated.
.
.
]override_homedir=/home/%d/%uFordetails,seethesssd.
conf(5)manpage.
Bydefault,SSSDretrievesinformationaboutusershellsfromtheloginShellparameterconfiguredinAD.
TocustomizetheusershellsettingsonLinuxclients:1.
Openthe/etc/sssd/sssd.
conffile.
2.
Definetherequiredusershellsettingsusingtheseoptions:shell_fallbacksetsafallbackvalue,whichisusedonlyifnoshellsaredefinedinADoverride_shellsetsavaluethatalwaysoverridestheshelldefinedinADdefault_shellsetsadefaultshellvalueallowed_shellsandvetoed_shellssetlistsofallowedorblacklistedshellsFordetails,seethesssd.
conf(5)manpage.
LoadtheNewConfigurationRestartSSSDafterchangingtheconfigurationfile.
#systemctlrestartsssd.
serviceAdditionalResourcesSeethesssd-ldap(5)andsssd-krb5(5)manpagesforotherconfigurationoptionsforLDAPandKerberosproviders.
Seethesssd-ad(5)manpageforotherconfigurationoptionsforADproviders.
2.
2.
3.
ConfiguringSSSDtoUsePOSIXAttributesDefinedinADNOTEPreviously,theIdentityManagementforUNIXextensionwasavailabletoprovidePOSIXattributestouseraccounts.
Theextensionisnowdeprecated.
SeetheMicrosoftDeveloperNetworkfordetails.
IfyouhavebeenusingIdentityManagementforUNIX,seethisKnowledgebasearticleforanswerstofrequentlyaskedquestions.
ForoldproceduresthatreferenceIdentityManagementforUnixandtheServicesforUnixpackage,seetheseRedHatKnowledgebasearticles:ConfiguringanActiveDirectoryDomainwithPOSIXAttributesConfiguringActiveDirectoryasanLDAPDomainRecommendationsCHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD13Forbestperformance,publishthePOSIXattributestotheADglobalcatalog.
IfPOSIXattributesarenotpresentintheglobalcatalog,SSSDconnectstotheindividualdomaincontrollersdirectlyontheLDAPport.
JointheLinuxSystemtotheADDomainFollowthestepsinSection2.
2.
2,"ConfiguringanADDomainwithIDMappingasaProviderforSSSD".
DisableIDMappinginSSSD1.
Openthe/etc/sssd/sssd.
conffile.
2.
IntheADdomainsection,addtheldap_id_mapping=falsesetting.
NOTEIfyouusedtherealmutilitytojointhedomainandaddedthe--automatic-id-mapping=noswitch,therealmutilityalreadysetupSSSDwithldap_id_mapping=false.
3.
IfyoupreviouslyrequestedanyuserswiththedefaultIDmappingconfiguration,removetheSSSDcaches:rm-f/var/lib/sss/db/*SSSDwillnowusePOSIXattributesfromAD,insteadofcreatingthemlocally.
AdditionalResourcesForfurtherdetailsaboutIDmappingandtheldap_id_mappingparameter,seethesssd-ldap(8)manpage.
2.
3.
AUTOMATICKERBEROSHOSTKEYTABRENEWALSSSDautomaticallyrenewstheKerberoshostkeytabfileinanADenvironmentiftheadclipackageisinstalled.
Thedaemonchecksdailyifthemachineaccountpasswordisolderthantheconfiguredvalueandrenewsitifnecessary.
Thedefaultrenewalintervalis30days.
Tochangethedefault:1.
AddthefollowingparametertotheADproviderinyour/etc/sssd/sssd.
conffile:ad_maximum_machine_account_password_age=value_in_days2.
RestartSSSD:#systemctlrestartsssdTodisabletheautomaticKerberoshostkeytabrenewal,setad_maximum_machine_account_password_age=0.
2.
4.
ENABLINGDYNAMICDNSUPDATESADallowsitsclientstorefreshtheirDNSrecordsautomatically.
ADalsoactivelymaintainsDNSrecordsWindowsIntegrationGuide14ADallowsitsclientstorefreshtheirDNSrecordsautomatically.
ADalsoactivelymaintainsDNSrecordstomakesuretheyareupdated,includingtimingout(aging)andremoving(scavenging)inactiverecords.
DNSscavengingisnotenabledbydefaultontheADside.
SSSDallowstheLinuxsystemtoimitateaWindowsclientbyrefreshingitsDNSrecord,whichalsopreventsitsrecordfrombeingmarkedinactiveandremovedfromtheDNSrecord.
WhendynamicDNSupdatesareenabled,theclient'sDNSrecordisrefreshed:whentheidentityprovidercomesonline(always)whentheLinuxsystemreboots(always)ataspecifiedinterval(optionalconfiguration);bydefault,theADproviderupdatestheDNSrecordevery24hoursYoucansetthisbehaviortothesameintervalastheDHCPlease.
Inthiscase,theLinuxclientisrenewedaftertheleaseisrenewed.
DNSupdatesaresenttotheADserverusingKerberos/GSSAPIforDNS(GSS-TSIG).
Thismeansthatonlysecureconnectionsneedtobeenabled.
ThedynamicDNSconfigurationissetforeachdomain.
Forexample:[domain/ad.
example.
com]id_provider=adauth_provider=adchpass_provider=adaccess_provider=adldap_schema=addyndns_update=truedyndns_refresh_interval=43200dyndns_update_ptr=truedyndns_ttl=3600Fordetailsontheseoptions,seethesssd-ad(5)manpage.
2.
5.
USINGRANGERETRIEVALSEARCHESWITHSSSDSSSDsupportsAD'sSearchingUsingRangeRetrievalfeature.
Fordetailsonrangeretrievalsearches,seetheMicrosoftDeveloperNetwork.
IMPORTANTIfyousetcustomfiltersinthegrouporsearchbases,thefiltersmightnotworkwellwithverylargegroups.
2.
6.
GROUPPOLICYOBJECTACCESSCONTROLGroupPolicyisaMicrosoftWindowsfeaturethatenablesadministratorstocentrallymanagepoliciesforusersandcomputersinActiveDirectory(AD)environments.
Agrouppolicyobject(GPO)isacollectionofpolicysettingsthatarestoredonadomaincontroller(DC)andcanbeappliedtopolicytargets,suchascomputersandusers.
GPOpolicysettingsrelatedtoWindowslogonrightsarecommonlyusedtomanagecomputer-basedaccesscontrolinADenvironments.
CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD152.
6.
1.
HowSSSDWorkswithGPOAccessControlWhenyouconfigureSSSDtoapplyGPOaccesscontrol,SSSDretrievesGPOsapplicabletohostsystemsandADusers.
BasedontheretrievedGPOconfiguration,SSSDdeterminesifauserisallowedtologintoaparticularhost.
ThisenablestheadministratortodefineloginpolicieshonoredbybothLinuxandWindowsclientscentrallyontheADdomaincontroller.
IMPORTANTSecurityfilteringisafeaturethatenablesyoutofurtherlimitthescopeofGPOaccesscontroltospecificusers,groups,orhostsbylistingtheminthesecurityfilter.
However,SSSDonlysupportsusersandgroupsinthesecurityfilter.
SSSDignoreshostentriesinthesecurityfilter.
ToensurethatSSSDappliestheGPOaccesscontroltoaspecificsystem,createanewOUintheADdomain,movethesystemtotheOU,andthenlinktheGPOtothisOU.
2.
6.
2.
GPOSettingsSupportedbySSSDTable2.
2.
GPOaccesscontroloptionsretrievedbySSSDGPOoption[a]Correspondingsssd.
confoption[b]AllowlogonlocallyDenylogonlocallyad_gpo_map_interactiveAllowlogonthroughRemoteDesktopServicesDenylogonthroughRemoteDesktopServicesad_gpo_map_remote_interactiveAccessthiscomputerfromthenetworkDenyaccesstothiscomputerfromthenetworkad_gpo_map_networkAllowlogonasabatchjobDenylogonasabatchjobad_gpo_map_batchAllowlogonasaserviceDenylogonasaservicead_gpo_map_service[a]AsnamedintheGroupPolicyManagementEditoronWindows.
[b]Seethesssd-ad(5)manpagefordetailsabouttheseoptionsandforlistsofpluggableauthenticationmodule(PAM)servicestowhichtheGPOoptionsaremappedbydefault.
2.
6.
3.
ConfiguringGPO-basedAccessControlforSSSDGPO-basedaccesscontrolcanbeconfiguredinthe/etc/sssd/sssd.
conffile.
Thead_gpo_access_controloptionspecifiesthemodeinwhichtheGPO-basedaccesscontrolruns.
Itcanbesettothefollowingvalues:WindowsIntegrationGuide16ad_gpo_access_control=permissiveThepermissivevaluespecifiesthatGPO-basedaccesscontrolisevaluatedbutnotenforced;asyslogmessageisrecordedeverytimeaccesswouldbedenied.
Thisisthedefaultsetting.
ad_gpo_access_control=enforcingTheenforcingvaluespecifiesthatGPO-basedaccesscontrolisevaluatedandenforced.
ad_gpo_access_control=disabledThedisabledvaluespecifiesthatGPO-basedaccesscontrolisneitherevaluatednorenforced.
IMPORTANTBeforestartingtousetheGPO-basedaccesscontrolandsettingad_gpo_access_controltoenforcingmode,itisrecommendedtoensurethatad_gpo_access_controlissettopermissivemodeandexaminethelogs.
Byreviewingthesyslogmessages,youcantestandadjustthecurrentGPOsettingsasnecessarybeforefinallysettingtheenforcingmode.
ThefollowingparametersrelatedtotheGPO-basedaccesscontrolcanalsobespecifiedinthesssd.
conffile:Thead_gpo_map_*optionsandthead_gpo_default_rightoptionconfigurewhichPAMservicesaremappedtospecificWindowslogonrights.
ToaddaPAMservicetothedefaultlistofPAMservicesmappedtoaspecificGPOsetting,ortoremovetheservicefromthelist,usethead_gpo_map_*options.
Forexample,toremovethesuservicefromthelistofPAMservicesmappedtointeractivelogin(GPOsettingsAllowlogonlocallyandDenylogonlocally):ad_gpo_map_interactive=-suThead_gpo_cache_timeoutoptionspecifiestheintervalduringwhichsubsequentaccesscontrolrequestscanreusethefilesstoredinthecache,insteadofretrievingthemfromtheDCanew.
ForadetailedlistofavailableGPOparametersaswellastheirdescriptionsanddefaultvalues,seethesssd-ad(5)manpage.
2.
6.
4.
AdditionalResourcesFormoredetailsonconfiguringSSSDtoworkwithGPOs,seeConfigureSSSDtorespectActiveDirectorySSHorConsole/GUIGPOsinRedHatKnowledgebase.
2.
7.
CREATINGUSERPRIVATEGROUPSAUTOMATICALLYUSINGSSSDAnSSSDclientdirectlyintegratedintoADcanautomaticallycreateauserprivategroupforeveryADuserretrieved,ensuringthatitsGIDmatchestheuser'sUIDunlesstheGIDnumberisalreadytaken.
Toavoidconflicts,makesurethatnogroupswiththesameGIDsasuserUIDsexistontheserver.
TheGIDisnotstoredinAD.
ThisensuresthatADusersbenefitfromgroupfunctionality,whiletheLDAPCHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD17TheGIDisnotstoredinAD.
ThisensuresthatADusersbenefitfromgroupfunctionality,whiletheLDAPdatabasedoesnotcontainunnecessaryemptygroups.
2.
7.
1.
ActivatingtheAutomaticCreationofUserPrivateGroupsforADusersToactivatetheautomaticcreationofuserprivategroupsforADusers:1.
Editthe/etc/sssd/sssd.
conffile,addinginthe[domain/LDAP]section:auto_private_groups=true2.
Restartthesssdservice,removingthesssddatabase:#servicesssdstop;rm-rf/var/lib/sss/db/*;servicesssdstartAfterperformingthisprocedure,everyADuserhasaGIDwhichisidenticaltotheUID:#idad_user1uid=121298(ad_user1)gid=121298(ad_user1)groups=121298(ad_user1),10000(Group1)#idad_user2uid=121299(ad_user2)gid=121299(ad_user2)groups=121299(ad_user2),10000(Group1)2.
7.
2.
DeactivatingtheAutomaticCreationofUserPrivateGroupsforADusersTodeactivatetheautomaticcreationofuserprivategroupsforADusers:1.
Editthe/etc/sssd/sssd.
conffile,addinginthe[domain/LDAP]section:auto_private_groups=false2.
Restartthesssdservice,removingthesssddatabase:#servicesssdstop;rm-rf/var/lib/sss/db/*;servicesssdstartAfterperformingthisprocedure,allADusershaveanidentical,genericGID:#idad_user1uid=121298(ad_user1)gid=10000(group1)groups=10000(Group1)#idad_user2uid=121299(ad_user2)gid=10000(group1)groups=10000(Group1)2.
8.
SSSDCLIENTSANDACTIVEDIRECTORYDNSSITEAUTODISCOVERYActiveDirectoryforestscanbeverylarge,withnumerousdifferentdomaincontrollers,domainsandchilddomains,andphysicalsites.
ActiveDirectoryusestheconceptofsitestoidentifythephysicallocationforitsdomaincontrollers.
Thisenablesclientstoconnecttothedomaincontrollerthatisgeographicallyclosest,whichincreasesclientperformance.
Bydefault,SSSDclientsuseautodiscoverytofinditsADsiteandconnecttotheclosestdomaincontroller.
Theprocessconsistsofthesesteps:1.
SSSDqueriesSRVrecordsfromtheDNSserverintheADforest.
ThereturnedrecordscontainWindowsIntegrationGuide181.
SSSDqueriesSRVrecordsfromtheDNSserverintheADforest.
ThereturnedrecordscontainthenamesofDCsintheforest.
2.
SSSDsendsanLDAPpingtoeachoftheseDCs.
IfaDCdoesnotrespondwithinaconfiguredinterval,therequesttimesoutandSSSDsendstheLDAPpingtothenextone.
Iftheconnectionsucceeds,theresponsecontainsinformationabouttheADsitetheSSSDclientbelongsto.
3.
SSSDthenqueriesSRVrecordsfromtheDNSservertolocateDCswithinthesiteitbelongsto,andconnectstooneofthem.
NOTESSSDrememberstheADsiteitbelongstobydefault.
Inthisway,SSSDcansendtheLDAPpingdirectlytoaDCinthissiteduringtheautodiscoveryprocesstorefreshthesiteinformation.
Consequently,theprocedureofautodiscoveryisveryfastasnotimeoutsoccurnormally.
Ifthesitenolongerexistsortheclienthasmeanwhilebeenassignedtoadifferentsite,SSSDstartsqueryingforSRVrecordsintheforestandgoesthroughthewholeprocessagain.
Tooverridetheautodiscovery,specifytheADsitetowhichyouwanttheclienttoconnectbyusingthead_siteoptioninthe[domain]sectionofthe/etc/sssd/sssd.
conffile.
AdditionalResourcesSeethesssd-ad(5)manpagefordetailsonad_site.
ForenvironmentswithatrustbetweenIdentityManagementandActiveDirectory,seeSection5.
6,"RestrictingIdentityManagementorSSSDtoSelectedActiveDirectoryServersorSitesinaTrustedActiveDirectoryDomain".
2.
9.
TROUBLESHOOTINGSSSDFordetailsabouttroubleshootingSSSD,seetheTroubleshootingSSSDappendixintheSystem-LevelAuthenticationGuide.
CHAPTER2.
USINGACTIVEDIRECTORYASANIDENTITYPROVIDERFORSSSD19CHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAINTherealmdsystemprovidesaclearandsimplewaytodiscoverandjoinidentitydomainstoachievedirectdomainintegration.
ItconfiguresunderlyingLinuxsystemservices,suchasSSSDorWinbind,toconnecttothedomain.
Chapter2,UsingActiveDirectoryasanIdentityProviderforSSSDdescribeshowtousetheSystemSecurityServicesDaemon(SSSD)onalocalsystemandActiveDirectoryasaback-endidentityprovider.
Ensuringthatthesystemisproperlyconfiguredforthiscanbeacomplextask:thereareanumberofdifferentconfigurationparametersforeachpossibleidentityproviderandforSSSDitself.
Inaddition,alldomaininformationmustbeavailableinadvanceandthenproperlyformattedintheSSSDconfigurationforSSSDtointegratethelocalsystemwithAD.
Therealmdsystemsimplifiesthatconfiguration.
ItcanrunadiscoverysearchtoidentifyavailableADandIdentityManagementdomainsandthenjointhesystemtothedomain,aswellassetuptherequiredclientservicesusedtoconnecttothegivenidentitydomainandmanageuseraccess.
Additionally,becauseSSSDasanunderlyingservicesupportsmultipledomains,realmdcandiscoverandsupportmultipledomainsaswell.
3.
1.
SUPPORTEDDOMAINTYPESANDCLIENTSTherealmdsystemsupportsthefollowingdomaintypes:MicrosoftActiveDirectoryRedHatEnterpriseLinuxIdentityManagementThefollowingdomainclientsaresupportedbyrealmd:SSSDforbothRedHatEnterpriseLinuxIdentityManagementandMicrosoftActiveDirectoryWinbindforMicrosoftActiveDirectory3.
2.
PREREQUISITESFORUSINGREALMDTousetherealmdsystem,installtherealmdpackage.
#yuminstallrealmdInaddition,makesurethattheoddjob,oddjob-mkhomedir,sssd,andadclipackagesareinstalled.
Thesepackagesarerequiredtobeabletomanagethesystemusingrealmd.
NOTEAsmentionedinSection3.
4,"DiscoveringandJoiningIdentityDomains",youcansimplyuserealmdtofindoutwhichpackagestoinstall.
3.
3.
REALMDCOMMANDSTherealmdsystemhastwomajortaskareas:managingsystemenrollmentinadomainWindowsIntegrationGuide20settingwhichdomainusersareallowedtoaccessthelocalsystemresourcesThecentralutilityinrealmdiscalledrealm.
Mostrealmcommandsrequiretheusertospecifytheactionthattheutilityshouldperform,andtheentity,suchasadomainoruseraccount,forwhichtoperformtheaction:realmcommandargumentsForexample:realmjoinad.
example.
comrealmpermituser_nameTable3.
1.
realmdCommandsCommandDescriptionRealmCommandsdiscoverRunadiscoveryscanfordomainsonthenetwork.
joinAddthesystemtothespecifieddomain.
leaveRemovethesystemfromthespecifieddomain.
listListallconfigureddomainsforthesystemoralldiscoveredandconfigureddomains.
LoginCommandspermitEnableaccessforspecifiedusersorforalluserswithinaconfigureddomaintoaccessthelocalsystem.
denyRestrictaccessforspecifiedusersorforalluserswithinaconfigureddomaintoaccessthelocalsystem.
Formoreinformationabouttherealmcommands,seetherealm(8)manpage.
3.
4.
DISCOVERINGANDJOININGIDENTITYDOMAINSTherealmdiscovercommandreturnscompletedomainconfigurationandalistofpackagesthatmustbeinstalledforthesystemtobeenrolledinthedomain.
Therealmjoincommandthensetsupthelocalmachineforusewithaspecifieddomainbyconfiguringboththelocalsystemservicesandtheentriesintheidentitydomain.
Theprocessrunbyrealmjoinfollowsthesesteps:1.
Runningadiscoveryscanforthespecifieddomain.
2.
Automaticinstallationofthepackagesrequiredtojointhesystemtothedomain.
ThisincludesSSSDandthePAMhomedirectoryjobpackages.
NotethattheautomaticCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN21ThisincludesSSSDandthePAMhomedirectoryjobpackages.
NotethattheautomaticinstallationofpackagesrequiresthePackageKitsuitetoberunning.
NOTEIfPackageKitisdisabled,thesystempromptsyouforthemissingpackages,andyouwillberequiredtoinstallthemmanuallyusingtheyumutility.
3.
Joiningthedomainbycreatinganaccountentryforthesysteminthedirectory.
4.
Creatingthe/etc/krb5.
keytabhostkeytabfile.
5.
ConfiguringthedomaininSSSDandrestartingtheservice.
6.
EnablingdomainusersforthesystemservicesinPAMconfigurationandthe/etc/nsswitch.
conffile.
DiscoveringDomainsWhenrunwithoutanyoptions,therealmdiscovercommanddisplaysinformationaboutthedefaultDNSdomain,whichisthedomainassignedthroughtheDynamicHostConfigurationProtocol(DHCP):#realmdiscoverad.
example.
comtype:kerberosrealm-name:AD.
EXAMPLE.
COMdomain-name:ad.
example.
comconfigured:noserver-software:active-directoryclient-software:sssdrequired-package:oddjobrequired-package:oddjob-mkhomedirrequired-package:sssdrequired-package:adclirequired-package:samba-commonItisalsopossibletorunadiscoveryforaspecificdomain.
Todothis,runrealmdiscoverandaddthenameofthedomainyouwanttodiscover:#realmdiscoverad.
example.
comTherealmdsystemwillthenuseDNSSRVlookupstofindthedomaincontrollersinthisdomainautomatically.
NOTETherealmdiscovercommandrequiresNetworkManagertoberunning;inparticular,itdependsontheD-BusinterfaceofNetworkManager.
IfyoursystemdoesnotuseNetworkManager,alwaysspecifythedomainnameintherealmdiscovercommand.
TherealmdsystemcandiscoverbothActiveDirectoryandIdentityManagementdomains.
Ifbothdomainsexistinyourenvironment,youcanlimitthediscoveryresultstoaspecifictypeofserverusingthe--server-softwareoption.
Forexample:WindowsIntegrationGuide22#realmdiscover--server-software=active-directoryOneoftheattributesreturnedinthediscoverysearchislogin-policy,whichshowsifdomainusersareallowedtologinassoonasthejoiniscomplete.
Ifloginsarenotallowedbydefault,youcanallowthemmanuallybyusingtherealmpermitcommand.
Fordetails,seeSection3.
7,"ManagingLoginPermissionsforDomainUsers".
Formoreinformationabouttherealmdiscovercommand,seetherealm(8)manpage.
JoiningaDomainIMPORTANTNotethatActiveDirectorydomainsrequireuniquecomputernamestobeused.
BothNetBIOScomputernameanditsDNShostnameshouldbeuniquelydefinedandcorrespondtoeachother.
Tojointhesystemtoanidentitydomain,usetherealmjoincommandandspecifythedomainname:#realmjoinad.
example.
comrealm:Joinedad.
example.
comdomainBydefault,thejoinisperformedasthedomainadministrator.
ForAD,theadministratoraccountiscalledAdministrator;forIdM,itiscalledadmin.
Toconnectasadifferentuser,usethe-Uoption:#realmjoinad.
example.
com-UuserThecommandfirstattemptstoconnectwithoutcredentials,butitpromptsforapasswordifrequired.
IfKerberosisproperlyconfiguredonaLinuxsystem,joiningcanalsobeperformedwithaKerberosticketforauthentication.
ToselectaKerberosprincipal,usethe-Uoption.
#kinituser#realmjoinad.
example.
com-UuserTherealmjoincommandacceptsseveralotherconfigurationoptions.
Formoreinformationabouttherealmjoincommand,seetherealm(8)manpage.
Example3.
1.
ExampleProcedureforEnrollingaSystemintoaDomain1.
Runtherealmdiscovercommandtodisplayinformationaboutthedomain.
#realmdiscoverad.
example.
comad.
example.
comtype:kerberosrealm-name:AD.
EXAMPLE.
COMdomain-name:ad.
example.
comconfigured:noserver-software:active-directoryclient-software:sssd2.
Runtherealmjoincommandandpassthedomainnametothecommand.
Providetheadministratorpasswordifthesystempromptsforit.
CHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN23#realmjoinad.
example.
comPasswordforAdministrator:passwordNotethatwhendiscoveringorjoiningadomain,realmdchecksfortheDNSSRVrecord:_ldap.
_tcp.
domain.
example.
com.
forIdentityManagementrecords_ldap.
_tcp.
dc.
_msdcs.
domain.
example.
com.
forActiveDirectoryrecordsTherecordiscreatedbydefaultwhenADisconfigured,whichenablesittobefoundbytheservicediscovery.
TestingtheSystemConfigurationafterJoiningaDomainTotestwhetherthesystemwassuccessfullyenrolledintoadomain,verifythatyoucanloginasauserfromthedomainandthattheuserinformationisdisplayedcorrectly:1.
Runtheiduser@domain_namecommandtodisplayinformationaboutauserfromthedomain.
#iduser@ad.
example.
comuid=1348601103(user@ad.
example.
com)gid=1348600513(domaingroup@ad.
example.
com)groups=1348600513(domaingroup@ad.
example.
com)2.
Usingthesshutility,loginasthesameuser.
#ssh-luser@ad.
example.
comlinux-client.
ad.
example.
comuser@ad.
example.
com@linux-client.
ad.
example.
com'spassword:Creatinghomedirectoryforuser@ad.
example.
com.
3.
Verifythatthepwdutilityprintstheuser'shomedirectory.
$pwd/home/ad.
example.
com/user4.
Verifythattheidutilityprintsthesameinformationastheiduser@domain_namecommandfromthefirststep.
$iduid=1348601103(user@ad.
example.
com)gid=1348600513(domaingroup@ad.
example.
com)groups=1348600513(domaingroup@ad.
example.
com)context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.
c1023Thekinitutilityisalsousefulwhentestingwhetherthedomainjoinwassuccessful.
Notethattousetheutility,thekrb5-workstationpackagemustbeinstalled.
3.
5.
REMOVINGASYSTEMFROMANIDENTITYDOMAINToremoveasystemfromanidentitydomain,usetherealmleavecommand.
ThecommandremovesthedomainconfigurationfromSSSDandthelocalsystem.
#realmleavead.
example.
comWindowsIntegrationGuide24Bydefault,theremovalisperformedasthedefaultadministrator.
ForAD,theadministratoraccountiscalledAdministrator;forIdM,itiscalledadmin.
Ifadifferentuserwasusedtojointothedomain,itmightberequiredtoperformtheremovalasthatuser.
Tospecifyadifferentuser,usethe-Uoption:#realmleavead.
example.
com-U'AD.
EXAMPLE.
COM\user'Thecommandfirstattemptstoconnectwithoutcredentials,butitpromptsforapasswordifrequired.
Notethatwhenaclientleavesadomain,thecomputeraccountisnotdeletedfromthedirectory;thelocalclientconfigurationisonlyremoved.
Ifyouwanttodeletethecomputeraccount,runthecommandwiththe--removeoptionspecified.
Formoreinformationabouttherealmleavecommand,seetherealm(8)manpage.
3.
6.
LISTINGDOMAINSTherealmlistcommandlistseveryconfigureddomainforthesystem,aswellasthefulldetailsanddefaultconfigurationforthatdomain.
Thisisthesameinformationasisreturnedbytherealmdiscoverycommand,onlyforadomainthatisalreadyinthesystemconfiguration.
#realmlist--all--name-onlyad.
example.
comThemostnotableoptionsacceptedbyrealmlistare:--allThe--alloptionlistsalldiscovereddomains,bothconfiguredandunconfigured.
--name-onlyThe--name-onlyoptionlimitstheresultstothedomainnamesanddoesnotdisplaythedomainconfigurationdetails.
Formoreinformationabouttherealmlistcommand,seetherealm(8)manpage.
3.
7.
MANAGINGLOGINPERMISSIONSFORDOMAINUSERSBydefault,domain-sideaccesscontrolisapplied,whichmeansthatloginpoliciesfordomainusersaredefinedinthedomainitself.
Thisdefaultbehaviorcanbeoverriddensothatclient-sideaccesscontrolisused.
Withclient-sideaccesscontrol,loginpermissionaredefinedbylocalpoliciesonly.
Ifadomainappliesclient-sideaccesscontrol,youcanusetherealmdsystemtoconfigurebasicallowordenyaccessrulesforusersfromthatdomain.
Notethattheseaccessruleseitherallowordenyaccesstoallservicesonthesystem.
Morespecificaccessrulesmustbesetonaspecificsystemresourceorinthedomain.
Tosettheaccessrules,usethefollowingtwocommands:realmdenyTherealmdenycommandsimplydeniesaccesstoalluserswithinthedomain.
Usethiscommandwiththe--alloption.
realmpermitCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN25Therealmpermitcommandcanbeusedto:grantaccesstoallusersbyusingthe--alloption,forexample:$realmpermit--allgrantaccesstospecifiedusers,forexample:$realmpermituser@example.
com$realmpermit'AD.
EXAMPLE.
COM\user'denyaccesstospecifiedusersbyusingthe-xoption,forexample:$realmpermit-x'AD.
EXAMPLE.
COM\user'Notethatallowingaccesscurrentlyonlyworksforusersinprimarydomains,notforusersintrusteddomains.
Thisisbecausewhileuserloginsmustcontainthedomainname,SSSDcurrentlycannotproviderealmdwithinformationaboutavailablechilddomains.
IMPORTANTItissafertoonlyallowaccesstospecificallyselectedusersorgroupsthantodenyaccesstosome,whileenablingittoeveryoneelse.
Therefore,itisnotrecommendedtoallowaccesstoallbydefaultwhileonlydenyingittospecifieduserswithrealmpermit-x.
Instead,RedHatrecommendstomaintainadefaultnoaccesspolicyforallusersandonlygrantaccesstoselectedusersusingrealmpermit.
Formoreinformationabouttherealmdenyandrealmpermitcommands,seetherealm(8)manpage.
3.
8.
CHANGINGDEFAULTUSERCONFIGURATIONTherealmdsystemsupportsmodifyingthedefaultuserhomedirectoryandshellPOSIXattributes.
Forexample,thismightberequiredwhensomePOSIXattributesarenotsetintheWindowsuseraccountsorwhentheseattributesaredifferentfromPOSIXattributesofotherusersonthelocalsystem.
IMPORTANTChangingtheconfigurationasdescribedinthissectiononlyworksiftherealmjoincommandhasnotbeenrunyet.
Ifasystemisalreadyjoined,changethedefaulthomedirectoryandshellinthe/etc/sssd/sssd.
conffile,asdescribedinthesectioncalled"Optional:ConfigureUserHomeDirectoriesandShells".
TooverridethedefaulthomedirectoryandshellPOSIXattributes,specifythefollowingoptionsinthe[users]sectioninthe/etc/realmd.
conffile:default-homeThedefault-homeoptionsetsatemplateforcreatingahomedirectoryforaccountsthathavenohomedirectoryexplicitlyset.
Acommonformatis/home/%d/%u,where%disthedomainnameand%uistheusername.
WindowsIntegrationGuide26default-shellThedefault-shelloptiondefinesthedefaultusershell.
Itacceptsanysupportedsystemshell.
Forexample:[users]default-home=/home/%udefault-shell=/bin/bashFormoreinformationabouttheoptions,seetherealmd.
conf(5)manpage.
3.
9.
ADDITIONALCONFIGURATIONFORTHEACTIVEDIRECTORYDOMAINENTRYCustomsettingsforeachindividualdomaincanbedefinedinthe/etc/realmd.
conffile.
Eachdomaincanhaveitsownconfigurationsection;thenameofthesectionmustmatchthedomainname.
Forexample:[ad.
example.
com]attribute=valueattribute=valueIMPORTANTChangingtheconfigurationasdescribedinthissectiononlyworksiftherealmjoincommandhasnotbeenrunyet.
Ifasystemisalreadyjoined,changingthesesettingsdoesnothaveanyeffect.
Insuchsituations,youmustleavethedomain,asdescribedinSection3.
5,"RemovingaSystemfromanIdentityDomain",andthenjoinagain,asdescribedinthesectioncalled"JoiningaDomain".
Notethatjoiningrequiresthedomainadministrator'scredentials.
Tochangetheconfigurationforadomain,editthecorrespondingsectionin/etc/realmd.
conf.
ThefollowingexampledisablesIDmappingforthead.
example.
comdomain,setsthehostprincipal,andaddsthesystemtothespecifiedsubtree:[ad.
example.
com]computer-ou=ou=LinuxComputers,DC=domain,DC=example,DC=comuser-principal=host/linux-client@AD.
EXAMPLE.
COMautomatic-id-mapping=noNotethatthesameconfigurationcanalsobesetwhenoriginallyjoiningthesystemtothedomainusingtherealmjoincommand,describedinthesectioncalled"JoiningaDomain":#realmjoin--computer-ou="ou=LinuxComputers,dc=domain,dc=com"--automatic-id-mapping=no--user-principal=host/linux-client@AD.
EXAMPLE.
COMTable3.
2,"RealmConfigurationOptions"liststhemostnotableoptionsthatcanbesetinthedomaindefaultsectionin/etc/realmd.
conf.
Forcompleteinformationabouttheavailableconfigurationoptions,seetherealmd.
conf(5)manpage.
Table3.
2.
RealmConfigurationOptionsCHAPTER3.
USINGREALMDTOCONNECTTOANACTIVEDIRECTORYDOMAIN27OptionDescriptioncomputer-ouSetsthedirectorylocationforaddingcomputeraccountstothedomain.
ThiscanbethefullDNoranRDN,relativetotherootentry.
Thesubtreemustalreadyexist.
user-principalSetstheuserPrincipalNameattributevalueofthecomputeraccounttotheprovidedKerberosprincipal.
automatic-id-mappingSetswhethertoenabledynamicIDmappingordisablethemappingandusePOSIXattributesconfiguredinActiveDirectory.
WindowsIntegrationGuide28CHAPTER4.
USINGSAMBAFORACTIVEDIRECTORYINTEGRATIONSambaimplementstheServerMessageBlock(SMB)protocolinRedHatEnterpriseLinux.
TheSMBprotocolisusedtoaccessresourcesonaserver,suchasfilesharesandsharedprinters.
YoucanuseSambatoauthenticateActiveDirectory(AD)domainuserstoaDomainController(DC).
Additionally,youcanuseSambatoshareprintersandlocaldirectoriestootherSMBclientsinthenetwork.
4.
1.
USINGWINBINDDTOAUTHENTICATEDOMAINUSERSSamba'swinbinddserviceprovidesaninterfacefortheNameServiceSwitch(NSS)andenablesdomainuserstoauthenticatetoADwhenloggingintothelocalsystem.
Usingwinbinddprovidesthebenefitthatyoucanenhancetheconfigurationtosharedirectoriesandprinterswithoutinstallingadditionalsoftware.
Forfurtherdetail,seethesectionaboutSambaintheRedHatSystemAdministrator'sGuide.
4.
1.
1.
JoininganADDomainIfyouwanttojoinanADdomainandusetheWinbindservice,usetherealmjoin--client-software=winbinddomain_namecommand.
Therealmutilityautomaticallyupdatestheconfigurationfiles,suchasthoseforSamba,Kerberos,andPAM.
Forfurtherdetailsandexamples,seetheSettingupSambaasaDomainMembersectionintheRedHatSystemAdministrator'sGuide.
4.
2.
USINGSMBSHARESWITHSSSDANDWINBINDThissectiondescribeshowyoucanuseSSSDclientstoaccessandfullyusesharesbasedontheServerMessageBlock(SMB)protocol,alsoknownastheCommonInternetFileSystem(CIFS)protocol.
IMPORTANTUsingSSSDasaclientinIdMorActiveDirectorydomainshascertainlimitations,andRedHatdoesnotrecommendusingSSSDasIDmappingplug-inforWinbind.
Forfurtherdetails,seethe"WhatisthesupportstatusforSambafileserverrunningonIdMclientsordirectlyenrolledADclientswhereSSSDisusedastheclientdaemon"article.
SSSDdoesnotsupportalltheservicesthatWinbindprovides.
Forexample,SSSDdoesnotsupportauthenticationusingtheNTLANManager(NTLM)orNetBIOSnamelookup.
Ifyouneedtheseservices,useWinbind.
NotethatinIdentityManagementdomains,KerberosauthenticationandDNSnamelookupareavailableforthesamepurposes.
4.
2.
1.
HowSSSDWorkswithSMBTheSMBfile-sharingprotocoliswidelyusedonWindowsmachines.
InRedHatEnterpriseLinuxenvironmentswithatrustbetweenIdentityManagementandActiveDirectory,SSSDenablesseamlessuseofSMBasifitwasastandardLinuxfilesystem.
ToaccessaSMBshare,thesystemmustbeabletotranslateWindowsSIDstoLinuxPOSIXUIDsandGIDs.
SSSDclientsusetheSID-to-IDorSID-to-namealgorithm,whichenablesthisIDmapping.
CHAPTER4.
USINGSAMBAFORACTIVEDIRECTORYINTEGRATION294.
2.
2.
SwitchingBetweenSSSDandWinbindforSMBShareAccessThisproceduredescribeshowyoucanswitchbetweenSSSDandWinbindplug-insthatareusedforaccessingSMBsharesfromSSSDclients.
ForWinbindtobeabletoaccessSMBshares,youneedtohavethecifs-utilspackageinstalledonyourclient.
Tomakesurethatcifs-utilsisinstalledonyourmachine:$rpm-qcifs-utils1.
Optional.
FindoutwhetheryouarecurrentlyusingSSSDorWinbindtoaccessSMBsharesfromtheSSSDclient:#alternatives--displaycifs-idmap-plugincifs-idmap-plugin-statusisauto.
linkcurrentlypointsto/usr/lib/cifs-utils/cifs_idmap_sss.
so/usr/lib/cifs-utils/cifs_idmap_sss.
so-priority20/usr/lib/cifs-utils/idmapwb.
so-priority10Current`best'versionis/usr/lib/cifs-utils/cifs_idmap_sss.
so.
IftheSSSDplug-in(cifs_idmap_sss.
so)isinstalled,ithasahigherprioritythantheWinbindplug-in(idmapwb.
so)bydefault.
2.
BeforeswitchingtotheWinbindplug-in,makesureWinbindisrunningonthesystem:#systemctlis-activewinbind.
serviceactiveBeforeswitchingtotheSSSDplug-in,makesureSSSDisrunningonthesystem:#systemctlis-activesssd.
serviceactive3.
Toswitchtoadifferentplug-in,usethealternatives--setcifs-idmap-plugincommand,andspecifythepathtotherequiredplug-in.
Forexample,toswitchtoWinbind:#alternatives--setcifs-idmap-plugin/usr/lib/cifs-utils/idmapwb.
so4.
3.
ADDITIONALRESOURCESFordetailsaboutSamba,seethecorrespondingsectionintheRedHatSystemAdministrator'sGuide.
WindowsIntegrationGuide30PARTII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:CROSS-FORESTTRUSTPARTII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:CROSS-FORESTTRUST31CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENTThischapterdescribescreatingcross-foresttrustsbetweenActiveDirectoryandIdentityManagement.
Across-foresttrustistherecommendedoneofthetwomethodstointegrateIdentityManagementandActiveDirectory(AD)environmentsindirectly.
Theothermethodissynchronization.
Ifyouareunsurewhichmethodtochooseforyourenvironment,readSection1.
3,"IndirectIntegration".
Kerberosimplementsaconceptofatrust.
Inatrust,aprincipalfromoneKerberosrealmcanrequestatickettoaserviceinanotherKerberosrealm.
Usingthisticket,theprincipalcanauthenticateagainstresourcesonmachinesbelongingtotheotherrealm.
KerberosalsohastheabilitytocreatearelationshipbetweentwootherwiseseparateKerberosrealms:across-realmtrust.
Realmsthatarepartofatrustuseasharedpairofaticketandkey;amemberofonerealmthencountsasamemberofbothrealms.
RedHatIdentityManagementsupportsconfiguringacross-foresttrustbetweenanIdMdomainandanActiveDirectorydomain.
5.
1.
INTRODUCTIONTOCROSS-FORESTTRUSTSKerberosrealmonlyconcernsauthentication.
OtherservicesandprotocolsareinvolvedincomplementingidentityandauthorizationforresourcesrunningonthemachinesintheKerberosrealm.
Assuch,establishingKerberoscross-realmtrustisnotenoughtoallowusersfromonerealmtoaccessresourcesintheotherrealm;asupportisrequiredatotherlevelsofcommunicationaswell.
5.
1.
1.
TheArchitectureofaTrustRelationshipBothActiveDirectoryandIdentityManagementmanageavarietyofcoreservicessuchasKerberos,LDAP,DNS,orcertificateservices.
Totransparentlyintegratethesetwodiverseenvironments,allcoreservicesmustinteractseamlesslywithoneanother.
ActiveDirectoryTrusts,Forests,andCross-forestTrustsKerberoscross-realmtrustplaysanimportantroleinauthenticationbetweenActiveDirectoryenvironments.
AllactivitiestoresolveuserandgroupnamesinatrustedADdomainrequireauthentication,regardlessofhowaccessisperformed:usingLDAPprotocoloraspartoftheDistributedComputingEnvironment/RemoteProcedureCalls(DCE/RPC)ontopoftheServerMessageBlock(SMB)protocol.
BecausetherearemoreprotocolsinvolvedinorganizingaccessbetweentwodifferentActiveDirectorydomains,trustrelationshiphasamoregenericname,ActiveDirectorytrust.
MultipleADdomainscanbeorganizedtogetherintoanActiveDirectoryforest.
Arootdomainoftheforestisthefirstdomaincreatedintheforest.
IdentityManagementdomaincannotbepartofanexistingADforest,thusitisalwaysseenasaseparateforest.
Whentrustrelationshipisestablishedbetweentwoseparateforestrootdomains,allowingusersandservicesfromdifferentADforeststocommunicate,atrustiscalledActiveDirectorycross-foresttrust.
TrustFlowandOne-wayTrustsAtrustestablishesanaccessrelationshipbetweentwodomains.
ActiveDirectoryenvironmentscanbecomplexsotherearedifferentpossibletypesandarrangementsforActiveDirectorytrusts,betweenchilddomains,rootdomains,orforests.
Atrustisapathfromonedomaintoanother.
Thewaythatidentitiesandinformationmovebetweenthedomainsiscalledatrustflow.
Thetrusteddomaincontainsusers,andthetrustingdomainallowsaccesstoresources.
Inaone-wayWindowsIntegrationGuide32trust,trustflowsonlyinonedirection:userscanaccessthetrustingdomain'sresourcesbutusersinthetrustingdomaincannotaccessresourcesinthetrusteddomain.
InFigure5.
1,"One-wayTrust",DomainAistrustedbyDomainB,butDomainBisnottrustedbyDomainA.
Figure5.
1.
One-wayTrustIdMallowstheadministratortoconfigurebothone-wayandtwo-waytrusts.
Fordetails,seeSection5.
1.
4,"One-WayandTwo-WayTrusts".
TransitiveandNon-transitiveTrustsTrustscanbetransitivesothatadomaintrustsanotherdomainandanyotherdomaintrustedbythatseconddomain.
Figure5.
2.
TransitiveTrustsTrustscanalsobenon-transitivewhichmeansthetrustislimitedonlytotheexplicitlyincludeddomains.
Cross-forestTrustinActiveDirectoryandIdentityManagementWithinanActiveDirectoryforest,trustrelationshipsbetweendomainsarenormallytwo-wayandtransitivebydefault.
BecausetrustbetweentwoADforestsisatrustbetweentwoforestrootdomains,itcanalsobetwo-wayorone-way.
Thetransitivityofthecross-foresttrustisexplicit:anydomaintrustwithinanADforestthatleadstotherootdomainoftheforestistransitiveoverthecross-foresttrust.
However,separatecross-foresttrustsarenottransitive.
Anexplicitcross-foresttrustmustbeestablishedbetweeneachADforestrootdomaintoanotherADforestrootdomain.
FromtheperspectiveofAD,IdentityManagementrepresentsaseparateADforestwithasingleADCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT33FromtheperspectiveofAD,IdentityManagementrepresentsaseparateADforestwithasingleADdomain.
Whencross-foresttrustbetweenanADforestrootdomainandanIdMdomainisestablished,usersfromtheADforestdomainscaninteractwithLinuxmachinesandservicesfromtheIdMdomain.
Figure5.
3.
TrustDirection5.
1.
2.
ActiveDirectorySecurityObjectsandTrustActiveDirectoryGlobalCatalogTheglobalcatalogcontainsinformationaboutobjectsofanActiveDirectory.
Itstoresafullcopyofobjectswithinitsowndomain.
FromobjectsofotherdomainsintheActiveDirectoryforest,onlyapartialcopyofthecommonlymostsearchedattributesisstoredintheglobalcatalog.
Additionally,sometypesofgroupsareonlyvalidwithinaspecificscopeandmightnotbepartoftheglobalcatalog.
Notethatthecross-foresttrustcontextiswiderthanasingledomain.
Therefore,someoftheseserver-localordomain-localsecuritygroupmembershipsfromatrustedforestmightnotbevisibletoIdMservers.
GlobalCatalogandPOSIXAttributesActiveDirectorydoesnotreplicatePOSIXattributeswithitsdefaultsettings.
IfitisrequiredtousePOSIXattributesthataredefinedinADRedHatstronglyrecommendstoreplicatethemtotheglobalcatalogservice.
5.
1.
3.
TrustArchitectureinIdMOntheIdentityManagementside,theIdMserverhastobeabletorecognizeActiveDirectoryidentitiesandappropriatelyprocesstheirgroupmembershipforaccesscontrols.
TheMicrosoftPAC(MS-PAC,PrivilegeAccountCertificate)containstherequiredinformationabouttheuser;theirsecurityID,domainusername,andgroupmemberships.
IdentityManagementhastwocomponentstoanalyzedatainthePAContheKerberosticket:SSSD,toperformidentitylookupsonActiveDirectoryandtoretrieveuserandgroupsecurityidentifiers(SIDs)forauthorization.
SSSDalsocachesuser,group,andticketinformationforusersandmapsKerberosandDNSdomains,IdentityManagement(Linuxdomainmanagement),toassociatetheActiveDirectoryuserwithanIdMgroupforIdMpoliciesandaccess.
NOTEWindowsIntegrationGuide34NOTEAccesscontrolrulesandpoliciesforLinuxdomainadministration,suchasSELinux,sudo,andhost-basedaccesscontrols,aredefinedandappliedthroughIdentityManagement.
AnyaccesscontrolrulessetontheActiveDirectorysidearenotevaluatedorusedbyIdM;theonlyActiveDirectoryconfigurationwhichisrelevantisgroupmembership.
TrustswithDifferentActiveDirectoryForestsIdMcanalsobepartoftrustrelationshipswithdifferentADforests.
Onceatrustisestablished,additionaltrustswithotherforestscanbeaddedlater,followingthesamecommandsandprocedures.
IdMcantrustmultipleentirelyunrelatedforestsatthesametime,allowingusersfromsuchunrelatedADforestsaccesstoresourcesinthesamesharedIdMdomain.
5.
1.
3.
1.
ActiveDirectoryPACsandIdMTicketsGroupinformationinActiveDirectoryisstoredinalistofidentifiersinthePrivilegeAttributeCertificate(MS-PACorPAC)dataset.
ThePACcontainsvariousauthorizationinformation,suchasgroupmembershiporadditionalcredentialsinformation.
Italsoincludessecurityidentifiers(SIDs)ofusersandgroupsintheActiveDirectorydomain.
SIDsareidentifiersassignedtoActiveDirectoryusersandgroupswhentheyarecreated.
Intrustenvironments,groupmembersareidentifiedbySIDs,ratherthanbynamesorDNs.
APACisembeddedintheKerberosservicerequestticketforActiveDirectoryusersasawayofidentifyingtheentitytootherWindowsclientsandserversintheWindowsdomain.
IdMmapsthegroupinformationinthePACtotheActiveDirectorygroupsandthentothecorrespondingIdMgroupstodetermineaccess.
WhenanActiveDirectoryuserrequestsaticketforaserviceonIdMresources,theprocessgoesasfollows:1.
TherequestforaservicecontainsthePACoftheuser.
TheIdMKerberosDistributionCentre(KDC)analyzesthePACbycomparingthelistofActiveDirectorygroupstomembershipsinIdMgroups.
2.
ForSIDsoftheKerberosprincipaldefinedintheMS-PAC,theIdMKDCevaluatesexternalgroupmembershipsdefinedintheIdMLDAP.
IfadditionalmappingsareavailableforanSID,theMS-PACrecordisextendedwithotherSIDsoftheIdMgroupstowhichtheSIDbelongs.
TheresultingMS-PACissignedbytheIdMKDC.
3.
TheserviceticketisreturnedtotheuserwiththeupdatedPACsignedbytheIdMKDC.
UsersbelongingtoADgroupsknowntotheIdMdomaincannowberecognizedbySSSDrunningontheIdMclientsbasedontheMS-PACcontentoftheserviceticket.
ThisallowstoreduceidentitytraffictodiscovergroupmembershipsbytheIdMclients.
WhentheIdMclientevaluatestheserviceticket,theprocessincludesthefollowingsteps:1.
TheKerberosclientlibrariesusedintheevaluationprocesssendthePACdatatotheSSSDPACresponder.
2.
ThePACresponderverifiesthegroupSIDsinthePACandaddstheusertothecorrespondinggroupsintheSSSDcache.
SSSDstoresmultipleTGTsandticketsforeachuserasnewservicesareaccessed.
3.
UsersbelongingtotheverifiedgroupscannowaccesstherequiredservicesontheIdMside.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT355.
1.
3.
2.
ActiveDirectoryUsersandIdentityManagementGroupsWhenmanagingActiveDirectoryusersandgroups,youcanaddindividualADusersandwholeADgroupstoIdentityManagementgroups.
ForadescriptionofhowtoconfigureIdMgroupsforADusers,seeSection5.
3.
3,"CreatingIdMGroupsforActiveDirectoryUsers".
Non-POSIXExternalGroupsandSIDMappingGroupmembershipintheIdMLDAPisexpressedbyspecifyingadistinguishedname(DN)ofanLDAPobjectthatisamemberofagroup.
ADentriesarenotsynchronizedorcopiedovertoIdM,whichmeansthatADusersandgroupshavenoLDAPobjectsintheIdMLDAP.
Therefore,theycannotbedirectlyusedtoexpressgroupmembershipintheIdMLDAP.
Forthisreason,IdMcreatesnon-POSIXexternalgroups:proxyLDAPobjectsthatcontainreferencestoSIDsofADusersandgroupsasstrings.
Non-POSIXexternalgroupsarethenreferencedasnormalIdMLDAPobjectstosignifygroupmembershipforADusersandgroupsinIdM.
SIDsofnon-POSIXexternalgroupsareprocessedbySSSD;SSSDmapsSIDsofgroupstowhichanADuserbelongstoPOSIXgroupsinIdM.
TheSIDsontheADsideareassociatedwithusernames.
WhentheusernameisusedtoaccessIdMresources,SSSDinIdMresolvesthatusernametoitsSID,andthenlooksuptheinformationforthatSIDwithintheADdomain,asdescribedinSection5.
1.
3.
1,"ActiveDirectoryPACsandIdMTickets".
IDRangesWhenauseriscreatedinLinux,itisassignedauserIDnumber.
Inaddition,aprivategroupiscreatedfortheuser.
TheprivategroupIDnumberisthesameastheuserIDnumber.
InLinuxenvironment,thisdoesnotcreateaconflict.
OnWindows,however,thesecurityIDnumbermustbeuniqueforeveryobjectinthedomain.
TrustedADusersrequireaUIDandGIDnumberonaLinuxsystem.
ThisUIDandGIDnumbercanbegeneratedbyIdM,butiftheADentryalreadyhasUIDandGIDnumbersassigned,assigningdifferentnumberscreatesaconflict.
Toavoidsuchconflicts,itispossibletousetheAD-definedPOSIXattributes,includingtheUIDandGIDnumberandpreferredloginshell.
NOTEADstoresasubsetofinformationforallobjectswithintheforestinaglobalcatalog.
Theglobalcatalogincludeseveryentryforeverydomainintheforest.
IfyouwanttouseAD-definedPOSIXattributes,RedHatstronglyrecommendsthatyoufirstreplicatetheattributestotheglobalcatalog.
Whenatrustiscreated,IdMautomaticallydetectswhatkindofIDrangetouseandcreatesauniqueIDrangefortheADdomainaddedtothetrust.
Youcanalsochoosethismanuallybypassingoneofthefollowingoptionstotheipatrust-addcommand:ipa-ad-trustThisrangeoptionisusedforIDsalgorithmicallygeneratedbyIdMbasedontheSID.
IfIdMgeneratestheSIDsusingSID-to-POSIXIDmapping,theIDrangesforADandIdMusersandgroupsmusthaveunique,non-overlappingIDrangesavailable.
ipa-ad-trust-posixThisrangeoptionisusedforIDsdefinedinPOSIXattributesintheADentry.
WindowsIntegrationGuide36IdMobtainsthePOSIXattributes,includinguidNumberandgidNumber,fromtheglobalcataloginADorfromthedirectorycontroller.
IftheADdomainismanagedcorrectlyandwithoutIDconflicts,theIDnumbersgeneratedinthiswayareunique.
Inthiscase,noIDvalidationorIDrangeisrequired.
Forexample:[root@ipaserver~]#ipatrust-addname_of_the_trust--range-type=ipa-ad-trust-posixRecreatingatrustwiththeotherIDrangeIftheIDrangeofthecreatedtrustdoesnotsuityourdeployment,youcanre-createthetrustusingtheother--range-typeoption:1.
ViewalltheIDrangesthatarecurrentlyinuse:[root@ipaserver~]#ipaidrange-findInthelist,identifythenameoftheIDrangethatwascreatedbytheipatrust-addcommand.
ThefirstpartofthenameoftheIDrangeisthenameofthetrust:name_of_the_trust_id_range,forexamplead.
example.
com.
2.
(Optional)Ifyoudonotknowwhich--range-typeoption,ipa-ad-trustoripa-ad-trust-posix,wasusedwhenthetrustwascreated,identifytheoption:[root@ipaserver~]#ipaidrange-showname_of_the_trust_id_rangeMakenoteofthetypesothatyouchoosetheoppositetypeforthenewtrustinStep5.
3.
Removetherangethatwascreatedbytheipatrust-addcommand:[root@ipaserver~]#ipaidrange-delname_of_the_trust_id_range4.
Removethetrust:[root@ipaserver~]#ipatrust-delname_of_the_trust5.
Createanewtrustwiththecorrect--range-typeoption.
Forexample:[root@ipaserver~]#ipatrust-addname_of_the_trust--range-type=ipa-ad-trust5.
1.
3.
3.
ActiveDirectoryUsersandIdMPoliciesandConfigurationSeveralIdMpolicydefinitions,suchasSELinux,host-basedaccesscontrol,sudo,andnetgroups,relyonusergroupstoidentifyhowthepoliciesareapplied.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT37Figure5.
4.
ActiveDirectoryUsersandIdMGroupsandPoliciesActiveDirectoryusersareexternaltotheIdMdomain,buttheycanstillbeaddedasgroupmemberstoIdMgroups,aslongasthosegroupsareconfiguredasexternalgroupsdescribedinSection5.
1.
3.
2,"ActiveDirectoryUsersandIdentityManagementGroups".
Insuchcases,thesudo,host-basedaccesscontrols,andotherpoliciesareappliedtotheexternalPOSIXgroupand,ultimately,totheADuserwhenaccessingIdMdomainresources.
TheuserSIDinthePACintheticketisresolvedtotheADidentity.
ThismeansthatActiveDirectoryuserscanbeaddedasgroupmembersusingtheirfully-qualifiedusernameortheirSID.
5.
1.
4.
One-WayandTwo-WayTrustsIdMsupportstwotypesoftrustagreements,dependingonwhethertheentitiesthatcanestablishconnectiontoservicesinIdMarelimitedtoonlyADorcanincludeIdMentitiesaswell.
One-waytrustOne-waytrustenablesADusersandgroupstoaccessresourcesinIdM,butnottheotherwayaround.
TheIdMdomaintruststheADforest,buttheADforestdoesnottrusttheIdMdomain.
One-waytrustisthedefaultmodeforcreatingatrust.
Two-waytrustTwo-waytrustenablesADusersandgroupstoaccessresourcesinIdM.
However,thetwo-waytrustinIdMdoesnotgivetheusersanyadditionalrightscomparedtotheone-waytrustsolutioninAD.
Bothsolutionsareconsideredequallysecurebecauseofdefaultcross-foresttrustSIDfilteringsettings.
Formoregeneralinformationonone-wayandtwo-waytrusts,seeSection5.
1.
1,"TheArchitectureofaTrustRelationship".
Afteratrustisestablished,itisnotpossibletomodifyitstype.
Ifyourequireadifferenttypeoftrust,runtheipatrust-addcommandagain;bydoingthis,youcandeletetheexistingtrustandestablishanewone.
5.
1.
5.
ExternalTruststoActiveDirectoryAnexternaltrustisatrustrelationshipbetweendomainsthatareinadifferentforests.
WhileforestWindowsIntegrationGuide38Anexternaltrustisatrustrelationshipbetweendomainsthatareinadifferentforests.
WhileforesttrustsalwaysrequiretoestablishthetrustbetweentherootdomainsofActiveDirectoryforests,youcanestablishanexternaltrusttoanydomainwithintheforest.
Externaltrustsarenon-transitive.
Forthisreason,usersandgroupsfromotherActiveDirectorydomainshavenoaccesstoIdMresources.
Forfurtherinformation,seethesectioncalled"TransitiveandNon-transitiveTrusts".
5.
1.
6.
TrustControllersandTrustAgentsIdMprovidesthefollowingtypesofIdMserversthatsupporttrusttoActiveDirectory:TrustcontrollersIdMserversthatcancontrolthetrustandperformidentitylookupsagainstActiveDirectorydomaincontrollers(DC).
ActiveDirectorydomaincontrollerscontacttrustcontrollerswhenestablishingandverifyingthetrusttoActiveDirectory.
Thefirsttrustcontrolleriscreatedwhenyouconfigurethetrust.
FordetailsaboutconfiguringanIdMserverasatrustcontroller,seeSection5.
2.
2,"CreatingTrusts".
Trustcontrollersrunanincreasedamountofnetwork-facingservicescomparedtotrustagents,andthuspresentagreaterattacksurfaceforpotentialintruders.
TrustagentsIdMserversthatcanperformidentitylookupsagainstActiveDirectorydomaincontrollers.
FordetailsaboutconfiguringanIdMserverasatrustagent,seeSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
Inadditiontotrustcontrollersandagents,theIdMdomaincanalsoincludereplicaswithoutanyrole.
However,theseserversdonotcommunicatewithActiveDirectory.
Therefore,clientsthatcommunicatewiththeseserverscannotresolveActiveDirectoryusersandgroupsorauthenticateandauthorizeActiveDirectoryusers.
Table5.
1.
AcomparisonofthecapabilitiesprovidedbytrustcontrollersandtrustagentsCapabilityTrustcontrollersTrustagentsResolveActiveDirectoryusersandgroupsYesYesEnrollIdMclientsthatrunservicesaccessiblebyusersfromtrustedActiveDirectoryforestsYesYesManagethetrust(forexample,addtrustagreements)YesNoWhenplanningthedeploymentoftrustcontrollersandtrustagents,considertheseguidelines:ConfigureatleasttwotrustcontrollersperIdentityManagementdeployment.
Configureatleasttwotrustcontrollersineachdatacenter.
Ifyoueverwanttocreateadditionaltrustcontrollersorifanexistingtrustcontrollerfails,createanewCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT39Ifyoueverwanttocreateadditionaltrustcontrollersorifanexistingtrustcontrollerfails,createanewtrustcontrollerbypromotingatrustagentorareplica.
Todothis,usetheipa-adtrust-installutilityontheIdMserverasdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
IMPORTANTYoucannotdowngradeanexistingtrustcontrollertoatrustagent.
5.
2.
CREATINGCROSS-FORESTTRUSTS5.
2.
1.
EnvironmentandMachineRequirementsBeforeconfiguringatrustagreement,makesurethatboththeActiveDirectoryandIdentityManagementservers,machines,andenvironmentsmeettherequirementsandsettingsdescribedinthissection.
5.
2.
1.
1.
SupportedWindowsPlatformsYoucanestablishatrustrelationshipwithActiveDirectoryforeststhatusethefollowingforestanddomainfunctionallevels:Forestfunctionallevelrange:WindowsServer2008-WindowsServer2016Domainfunctionallevelrange:WindowsServer2008-WindowsServer2016Thefollowingoperatingsystemsaresupportedandtestedforestablishingatrustusingthementionedfunctionallevels:WindowsServer2012R2WindowsServer2016PreviousversionsofWindowsServerarenotsupportedforestablishingatrust.
5.
2.
1.
2.
DNSandRealmSettingsToestablishatrust,ActiveDirectoryandIdentityManagementrequirespecificDNSconfiguration:UniqueprimaryDNSdomainsEachsystemmusthaveitsownuniqueprimaryDNSdomainconfigured.
Forexample:ad.
example.
comforADandidm.
example.
comforIdMexample.
comforADandidm.
example.
comforIdMad.
example.
comforADandexample.
comforIdMIMPORTANTIftheIdMdomainistheparentdomainoftheADdomain,theIdMserversmustrunonRedHatEnterpriseLinux7.
5orlater.
ThemostconvenientmanagementsolutionisanenvironmentwhereeachDNSdomainismanagedWindowsIntegrationGuide40ThemostconvenientmanagementsolutionisanenvironmentwhereeachDNSdomainismanagedbyintegratedDNSservers,butitispossibletouseanyotherstandard-compliantDNSserveraswell.
ItisnotpossibleforADorIdMtosharetheprimaryDNSdomainwithanothersystemforidentitymanagement.
Formoreinformation,seedocumentationforhostnameandDNSconfigurationrequirementsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
Kerberosrealmnamesasupper-caseversionsofprimaryDNSdomainnamesKerberosrealmnamesmustbethesameastheprimaryDNSdomainnames,withalllettersuppercase.
Forexample,ifthedomainnamesaread.
example.
comforADandidm.
example.
comforIdM,theKerberosrealmnamesarerequiredtobeAD.
EXAMPLE.
COMandIDM.
EXAMPLE.
COM.
DNSrecordsresolvablefromallDNSdomainsinthetrustAllmachinesmustbeabletoresolveDNSrecordsfromallDNSdomainsinvolvedinthetrustrelationship:WhenconfiguringIdMDNS,followtheinstructionsdescribedinthesectiononconfiguringDNSserviceswithintheIdMdomainandsectiononmanagingDNSforwardingintheLinuxDomainIdentity,Authentication,andPolicyGuide.
IfyouareusingIdMwithoutintegratedDNS,followtheinstructionsdescribedinthesectiondescribingtheserverinstallationwithoutintegratedDNSintheLinuxDomainIdentity,Authentication,andPolicyGuide.
NooverlapbetweenIdMandADDNSdomainsMachinesjoinedtoIdMcanbedistributedovermultipleDNSdomains.
DNSdomainscontainingIdMclientsmustnotoverlapwithDNSdomainscontainingmachinesjoinedtoAD.
TheprimaryIdMDNSdomainmusthaveproperSRVrecordstosupportADtrusts.
YoucanacquirealistoftherequiredSRVrecordsspecifictoyoursystemsetupbyrunningthe$ipadns-update-system-records--dry-runcommand.
Thegeneratedlistcanlookforexamplelikethis:$ipadns-update-system-records--dry-runIPADNSrecords:_kerberos-master.
_tcp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos-master.
_udp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos.
_tcp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos.
_udp.
example.
com.
86400INSRV010088server.
example.
com.
_kerberos.
example.
com.
86400INTXT"EXAMPLE.
COM"_kpasswd.
_tcp.
example.
com.
86400INSRV0100464server.
example.
com.
_kpasswd.
_udp.
example.
com.
86400INSRV0100464server.
example.
com.
_ldap.
_tcp.
example.
com.
86400INSRV0100389server.
example.
com.
_ntp.
_udp.
example.
com.
86400INSRV0100123server.
example.
com.
ForotherDNSdomainsthatarepartofthesameIdMrealm,itisnotrequiredfortheSRVrecordstobeconfiguredwhenthetrusttoADisconfigured.
ThereasonisthatADdomaincontrollersdonotuseSRVrecordstodiscoverKDCsbutratherbasetheKDCdiscoveryonnamesuffixroutinginformationforthetrust.
VerifyingtheDNSConfigurationCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT41Beforeconfiguringtrust,verifythattheIdentityManagementandActiveDirectoryserverscanresolvethemselvesandalsoeachother.
Ifrunningthecommandsdescribedbelowdoesnotdisplaytheexpectedresults,inspecttheDNSconfigurationonthehostwherethecommandswereexecuted.
Ifthehostconfigurationseemscorrect,makesurethatDNSdelegationsfromtheparenttochilddomainsaresetupcorrectly.
NotethatADcachestheresultsofDNSlookups,andchangesyoumakeinDNSarethereforesometimesnotvisibleimmediately.
Youcandeletethecurrentcachebyrunningtheipconfig/flushdnscommand.
VerifythattheIdM-hostedservicesareresolvablefromtheIdMdomainserverusedforestablishingtrust1.
RunaDNSqueryfortheKerberosoverUDPandLDAPoverTCPservicerecords.
[root@ipaserver~]#dig+short-tSRV_kerberos.
_udp.
ipa.
example.
com.
010088ipamaster1.
ipa.
example.
com.
[root@ipaserver~]#dig+short-tSRV_ldap.
_tcp.
ipa.
example.
com.
0100389ipamaster1.
ipa.
example.
com.
ThecommandsareexpectedtolistallIdMservers.
2.
RunaDNSqueryfortheTXTrecordwiththeIdMKerberosrealmname.
TheobtainedvalueisexpectedtomatchtheKerberosrealmthatyouspecifiedwheninstallingIdM.
[root@ipaserver~]#dig+short-tTXT_kerberos.
ipa.
example.
com.
IPA.
EXAMPLE.
COM3.
Afteryouexecutetheipa-adtrust-installutility,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust",runaDNSqueryfortheMSDCKerberosoverUDPandLDAPoverTCPservicerecords.
[root@ipaserver~]#dig+short-tSRV_kerberos.
_udp.
dc.
_msdcs.
ipa.
example.
com.
010088ipamaster1.
ipa.
example.
com.
[root@ipaserver~]#dig+short-tSRV_ldap.
_tcp.
dc.
_msdcs.
ipa.
example.
com.
0100389ipamaster1.
ipa.
example.
com.
ThecommandsareexpectedtolistallIdMserversonwhichipa-adtrust-installhasbeenexecuted.
Notethattheoutputisemptyifipa-adtrust-installhasnotbeenexecutedonanyIdMserver,whichistypicallybeforeestablishingtheveryfirsttrustrelationship.
VerifythatIdMisabletoresolveservicerecordsforADRunaDNSqueryfortheKerberosoverUDPandLDAPoverTCPservicerecords.
[root@ipaserver~]#dig+short-tSRV_kerberos.
_udp.
dc.
_msdcs.
ad.
example.
com.
010088addc1.
ad.
example.
com.
[root@ipaserver~]#dig+short-tSRV_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
com.
0100389addc1.
ad.
example.
com.
ThesecommandsareexpectedtoreturnthenamesofADdomaincontrollers.
WindowsIntegrationGuide42VerifythattheIdM-hostedservicesareresolvablefromtheADserver1.
OntheADserver,setthenslookup.
exeutilitytolookupservicerecords.
C:\>nslookup.
exe>settype=SRV2.
EnterthedomainnamefortheKerberosoverUDPandLDAPoverTCPservicerecords.
>_kerberos.
_udp.
ipa.
example.
com.
_kerberos.
_udp.
ipa.
example.
com.
SRVservicelocation:priority=0weight=100port=88svrhostname=ipamaster1.
ipa.
example.
com>_ldap.
_tcp.
ipa.
example.
com_ldap.
_tcp.
ipa.
example.
comSRVservicelocation:priority=0weight=100port=389svrhostname=ipamaster1.
ipa.
example.
comTheexpectedoutputcontainsthesamesetofIdMserversasdisplayedinVerifythattheIdM-hostedservicesareresolvablefromtheIdMdomainserverusedforestablishingtrust.
3.
ChangetheservicetypetoTXTandrunaDNSqueryfortheTXTrecordwiththeIdMKerberosrealmname.
C:\>nslookup.
exe>settype=TXT>_kerberos.
ipa.
example.
com.
_kerberos.
ipa.
example.
com.
text="IPA.
EXAMPLE.
COM"TheoutputisexpectedtocontainthesamevalueasdisplayedinVerifythattheIdM-hostedservicesareresolvablefromtheIdMdomainserverusedforestablishingtrust.
4.
Afteryouexecutetheipa-adtrust-installutility,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust",runaDNSqueryfortheMSDCKerberosoverUDPandLDAPoverTCPservicerecords.
C:\>nslookup.
exe>settype=SRV>_kerberos.
_udp.
dc.
_msdcs.
ipa.
example.
com.
_kerberos.
_udp.
dc.
_msdcs.
ipa.
example.
com.
SRVservicelocation:priority=0weight=100port=88svrhostname=ipamaster1.
ipa.
example.
com>_ldap.
_tcp.
dc.
_msdcs.
ipa.
example.
com.
_ldap.
_tcp.
dc.
_msdcs.
ipa.
example.
com.
SRVservicelocation:priority=0CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT43weight=100port=389svrhostname=ipamaster1.
ipa.
example.
comThecommandisexpectedtolistallIdMserversonwhichtheipa-adtrust-installutilityhasbeenexecuted.
Notethattheoutputisemptyifipa-adtrust-installhasnotbeenexecutedonanyIdMserver,whichistypicallybeforeestablishingtheveryfirsttrustrelationship.
VerifythatADservicesareresolvablefromtheADserver1.
OntheADserver,setthenslookup.
exeutilitytolookupservicerecords.
C:\>nslookup.
exe>settype=SRV2.
EnterthedomainnamefortheKerberosoverUDPandLDAPoverTCPservicerecords.
>_kerberos.
_udp.
dc.
_msdcs.
ad.
example.
com.
_kerberos.
_udp.
dc.
_msdcs.
ad.
example.
com.
SRVservicelocation:priority=0weight=100port=88svrhostname=addc1.
ad.
example.
com>_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
com.
_ldap.
_tcp.
dc.
_msdcs.
ad.
example.
com.
SRVservicelocation:priority=0weight=100port=389svrhostname=addc1.
ad.
example.
comTheexpectedoutputcontainsthesamesetofADserversasdisplayedinVerifythatIdMisabletoresolveservicerecordsforAD.
5.
2.
1.
3.
NetBIOSNamesTheNetBIOSnameiscriticalforidentifyingtheActiveDirectory(AD)domainand,ifIdMhasatrustconfiguredwithAD,foridentifyingtheIdMdomainandservices.
Asaconsequence,youmustuseadifferentNetBIOSnamefortheIdMdomainthantheNetBIOSnamesusedintheADdomainstowhichyouwanttoestablishtheforesttrust.
TheNetBIOSnameofanActiveDirectoryorIdMdomainisusuallythefar-leftcomponentofthecorrespondingDNSdomain.
Forexample,iftheDNSdomainisad.
example.
com,theNetBIOSnameistypicallyAD.
NOTEThemaximumlengthofaNetBIOSnameis15characters.
5.
2.
1.
4.
FirewallsandPortsToenablecommunicationbetweenADdomaincontrollersandIdMservers,makesureyoumeetthefollowingportrequirements:WindowsIntegrationGuide44OpenportsrequiredforanADtrustandportsrequiredbyanIdMserverinanADtrustonIdMserversandallADdomaincontrollersinbothdirections:fromtheIdMserverstotheADdomaincontrollersandback.
OpentheportrequiredbyanIdMclientinanADtrustonallADdomaincontrollersofthetrustedADforest.
OntheIdMclients,makesuretheportisopenintheoutgoingdirection(seePrerequisitesforInstallingaClientintheLinuxDomainIdentity,Authentication,andPolicyGuide).
Table5.
2.
PortsRequiredforanADTrustServicePortProtocolEndpointresolutionportmapper135TCPNetBIOS-DGM138TCPandUDPNetBIOS-SSN139TCPandUDPMicrosoft-DS445TCPandUDPEndpointmapperlistenerrange1024-1300TCPADGlobalCatalog3268TCPLDAP389TCP[a]andUDP[a]TheTCPport389isnotrequiredtobeopenonIdMserversfortrust,butitisnecessaryforclientscommunicatingwiththeIdMserver.
Table5.
3.
PortsRequiredbyIdMServersinaTrustServicePortProtocolKerberosSeePortRequirementsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
LDAPDNSTable5.
4.
PortsRequiredbyIdMClientsinanADTrustServicePortProtocolNotesCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT45Kerberos88UDPandTCPThelibkrb5libraryusesUDPandfalls-backtotheTCPprotocolifthedatasentfromtheKerberosDistributionCenter(KDC)istoolarge.
ActiveDirectoryattachesaPrivilegeAttributeCertificate(PAC)totheKerberosticket,whichincreasesthesizeandrequiresinmostcasestousetheTCPprotocol.
Toavoidthefall-backandresendingtherequest,bydefault,SSSDinRedHatEnterpriseLinux7.
4andlaterusesTCPforuserauthentication.
Toconfigurethesizebeforelibkrb5usesTCP,settheudp_preference_limitinthe/etc/krb.
5.
conffile.
Fordetails,seethekrb5.
conf(5)manpage.
ServicePortProtocolNotesAdditionalResourcesForadviceonhowtoopentherequiredports,seePortRequirementsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
5.
2.
1.
5.
IPv6SettingsTheIdMsystemmusthavetheIPv6protocolenabledinthekernel.
IfIPv6isdisabled,thentheCLDAPplug-inusedbytheIdMservicesfailstoinitialize.
5.
2.
1.
6.
ClockSettingsBoththeActiveDirectoryserverandtheIdMservermusthavetheirclocksinsync.
5.
2.
1.
7.
CreatingaConditionalForwarderfortheIdMDomaininADPreparetheADDNSservertoforwardqueriesfortheIdMdomaintotheIdMDNSserver:1.
OnaWindowsADdomaincontroller,opentheActiveDirectory(AD)DNSconsole.
2.
Right-clickConditionalForwarders,selectNewConditionalForwarder.
3.
EntertheIdMDNSdomainnameandtheIPaddressoftheIdMDNSserver4.
SelectStorethisconditionalforwarderinActiveDirectory,andreplicateitasfollows,andselectthereplicationsettingthatmatchesyourenvironment.
5.
ClickOK.
WindowsIntegrationGuide466.
ToverifythattheADdomaincontroller(DC)canresolveDNSentriesfromtheIdMdomain,openacommandpromptandenter:C:\>nslookupserver.
idm.
example.
comIfthecommandreturnstheIPaddressoftheIdMserver,theconditionalforwarderisworkingcorrectly.
5.
2.
1.
8.
CreatingaForwardZonefortheADDomaininIdMPreparetheIdMDNSservertoforwardqueriesfortheADdomaintotheADDNSserver:1.
OntheIdMserver,createaforwardzoneentryfortheADDNSdomain.
ForfurtherdetailsaboutcreatingaDNSforwardzoneinIdMseetheConfiguringForwardZonessectionintheLinuxDomainIdentity,Authentication,andPolicyGuide.
2.
IftheADDNSserverdoesnotsupportDNSSEC,disableDNSSECvalidationontheIdMserver:a.
Editthe/etc/named.
conffileandsetthednssec-validationparametertono:dnssec-validationno;b.
Restartthenamed-pkcs11service:#systemctlrestartnamed-pkcs113.
ToverifythattheIdMservercanresolveDNSentriesfromtheADdomain,enter:CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT47#hostserver.
ad.
example.
comIfthecommandreturnstheIPaddressoftheADDC,theforwardzoneisworkingcorrectly.
5.
2.
1.
9.
SupportedUserNameFormatsIdMperformsusernamemappinginthelocalSSSDclient.
ThedefaultoutputusernameformatforusersfromtrusteddomainssupportedbySSSDisuser_name@domain.
ActiveDirectorysupportsseveraldifferentkindsofnameformats:user_name,user_name@DOMAIN_NAME,andDOMAIN_NAME\user_name.
Userscanuseeitheronlytheirusername(user_name)ortheirfully-qualifiedusername(user_name@domain_name),forexample,toauthenticatetothesystem.
WARNINGPreferably,usethefully-qualifiedusernametoavoidconflictsifthesameusernameexistsinmultipledomains.
Ifauserspecifiesonlytheusernamewithoutthedomain,SSSDsearchestheaccountinalldomainsconfiguredinthe/etc/sssd/sssd.
conffileandintrusteddomains.
IfyouconfiguredadomainresolutionorderasdescribedinSection8.
5.
3,"ConfiguringtheDomainResolutionOrderonanIdMClient",SSSDsearchesfortheuserinthedefinedorder.
Inanycase,SSSDusesthefirstentryfound.
Thiscanleadtoproblemsorconfusionifthesameusernameexistsinmultipledomainsandthefirstentryfoundisnottheexpectedone.
Bydefault,SSSDdisplaysusernamesalwaysinthefully-qualifiedformat.
Fordetailsaboutchangingtheformat,seeSection5.
5,"ChangingtheFormatofUserNamesDisplayedbySSSD".
Toidentifytheusernameandthedomaintowhichtheusernamebelongs,SSSDusesaregularexpressiondefinedinthere_expressionoption.
TheregularexpressionisusedforIdMbackendsorADbackendsandsupportsallthementionedformats:re_expression=(((PPPPP5.
2.
2.
CreatingTrustsThefollowingsectionsdescribecreatingtrustsinvariousconfigurationscenarios.
Section5.
2.
2.
1,"CreatingaTrustfromtheCommandLine"containsthefullprocedureforconfiguringatrustfromthecommandline.
Theothersectionsdescribethestepswhicharedifferentfromthisbasicconfigurationscenarioandreferencethebasicprocedureforallothersteps.
NOTEIfyousetupareplicainanexistingtrustenvironment,thereplicaisnotautomaticallyconfiguredasatrustcontroller.
Toconfigurethereplicaasanadditionaltrustcontroller,followtheproceduresinthissection.
WindowsIntegrationGuide48Aftercreatingatrust,seeSection5.
2.
3,"Post-installationConsiderationsforCross-forestTrusts".
5.
2.
2.
1.
CreatingaTrustfromtheCommandLineCreatingatrustrelationshipbetweentheIdMandActiveDirectoryKerberosrealmsinvolvesthefollowingsteps:1.
PreparingtheIdMserverforthetrust,describedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust"2.
Creatingatrustagreement,describedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement"3.
VerifyingtheKerberosconfiguration,describedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration"5.
2.
2.
1.
1.
PreparingtheIdMServerforTrustTosetuptheIdMserverforatrustrelationshipwithAD,followthesesteps:1.
InstalltherequiredIdM,trust,andSambapackages:[root@ipaserver]#yuminstallipa-serveripa-server-trust-adsamba-client2.
ConfiguretheIdMservertoenabletrustservices.
Youcanskipthisstepifyouinstalledtheserverwiththeipa-replica-install--setup-adtrustcommand.
a.
Runtheipa-adtrust-installutility:[root@ipaserver]#ipa-adtrust-installTheutilityaddsDNSservicerecordsrequiredforADtrusts.
TheserecordsarecreatedautomaticallyifIdMwasinstalledwithanintegratedDNSserver.
IfIdMwasinstalledwithoutanintegratedDNSserver,ipa-adtrust-installprintsalistofservicerecordsthatyoumustmanuallyaddtotheDNSbeforeyoucancontinue.
IMPORTANTRedHatstronglyrecommendstoverifytheDNSconfigurationasdescribedinthesectioncalled"VerifyingtheDNSConfiguration"everytimeafterrunningipa-adtrust-install,especiallyifIdMorADdonotuseintegratedDNSservers.
b.
Thescriptpromptstoconfiguretheslapi-nisplug-in,acompatibilityplug-inthatallowsolderLinuxclientstoworkwithtrustedusers.
DoyouwanttoenablesupportfortrusteddomainsinSchemaCompatibilitypluginThiswillallowclientsolderthanSSSD1.
9andnon-Linuxclientstoworkwithtrustedusers.
Enabletrusteddomainssupportinslapi-nis[no]:yc.
Atleastoneuser(theIdMadministrator)existswhenthedirectoryisfirstinstalled.
TheSIDCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT49c.
Atleastoneuser(theIdMadministrator)existswhenthedirectoryisfirstinstalled.
TheSIDgenerationtaskcancreateaSIDforanyexistinguserstosupportthetrustenvironment.
Thisisaresource-intensivetask;forahighnumberofusers,thiscanberunseparately.
Doyouwanttoruntheipa-sidgentask[no]:yes3.
MakesurethatDNSisproperlyconfigured,asdescribedinSection5.
2.
1.
2,"DNSandRealmSettings".
4.
Startthesmbservice:[root@ipaserver~]#systemctlstartsmb5.
Optionally,configurethatthesmbservicestartsautomaticallywhenthesystemboots:[root@ipaserver~]#systemctlenablesmb6.
Optionally,usethesmbclientutilitytoverifythatSambarespondstoKerberosauthenticationfromtheIdMside.
[root@ipaserver~]#smbclient-Lipaserver.
ipa.
example.
com-klp_load_ex:changingtoconfigbackendregistrySharenameTypeCommentIPC$IPCIPCService(Samba4.
9.
1)ReconnectingwithSMB1forworkgrouplisting.
ServerCommentWorkgroupMaster5.
2.
2.
1.
2.
CreatingaTrustAgreementCreateatrustagreementfortheActiveDirectorydomainandtheIdMdomainbyusingtheipatrust-addcommand:#ipatrust-add--type=typead_domain_name--adminad_admin_username--passwordTheipatrust-addcommandsetsupaone-waytrustbydefault.
Toestablishatwo-waytrust,passthe--two-way=trueoption.
SeeSection5.
1.
4,"One-WayandTwo-WayTrusts"fordetails.
Toestablishanexternaltrust,passthe--external=trueoptiontotheipatrust-addcommand.
SeeSection5.
1.
5,"ExternalTruststoActiveDirectory"fordetails.
NOTETheipatrust-addcommandconfigurestheserverasatrustcontrollerbydefault.
SeeSection5.
1.
6,"TrustControllersandTrustAgents"fordetails.
Thefollowingexampleestablishesatwo-waytrustbyusingthe--two-way=trueoption:WindowsIntegrationGuide50[root@ipaserver~]#ipatrust-add--type=adad.
example.
com--adminAdministrator--password--two-way=trueActiveDirectorydomainadministrator'spassword:AddedActiveDirectorytrustforrealm"ad.
example.
com"Realm-Name:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912SIDblacklistincoming:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18SIDblacklistoutgoing:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18Trustdirection:Two-waytrustTrusttype:ActiveDirectorydomainTruststatus:Establishedandverified5.
2.
2.
1.
3.
VerifyingtheKerberosConfigurationToverifytheKerberosconfiguration,testifitispossibletoobtainaticketforanIdMuserandiftheIdMusercanrequestservicetickets.
Toverifyatwo-waytrust:1.
RequestaticketforanIdMuser:[root@ipaserver~]#kinituser2.
RequestserviceticketsforaservicewithintheIdMdomain:[root@ipaserver~]#kvno-Shostipaserver.
example.
com3.
RequestserviceticketsforaservicewithintheADdomain:[root@ipaserver~]#kvno-Scifsadserver.
example.
comIftheADserviceticketissuccessfullygranted,thereisacross-realmticket-grantingticket(TGT)listedwithalloftheotherrequestedtickets.
TheTGTisnamedkrbtgt/AD.
DOMAIN@IPA.
DOMAIN.
[root@ipaserver]#klistTicketcache:FILE:/tmp/krb5cc_0Defaultprincipal:user@IPA.
DOMAINValidstartingExpiresServiceprincipal06/15/1212:13:0406/16/1212:12:55krbtgt/IPA.
DOMAIN@IPA.
DOMAIN06/15/1212:13:1306/16/1212:12:55host/ipaserver.
ipa.
example.
com@IPA.
DOMAIN06/15/1212:13:2306/16/1212:12:55krbtgt/AD.
DOMAIN@IPA.
DOMAIN06/15/1212:14:5806/15/1222:14:58cifs/adserver.
ad.
example.
com@AD.
DOMAINCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT51Toverifyaone-waytrustfromtheIdMside:1.
RequestaticketforanActiveDirectoryuser:[root@ipaserver~]#kinituser@AD.
DOMAIN2.
RequestserviceticketsforaservicewithintheIdMdomain:[root@ipaserver~]#kvno-Shostipaserver.
example.
comIftheADserviceticketissuccessfullygranted,thereisacross-realmticket-grantingticket(TGT)listedwithalloftheotherrequestedtickets.
TheTGTisnamedkrbtgt/IPA.
DOMAIN@AD.
DOMAIN.
[root@ipaserver]#klistTicketcache:KEYRING:persistent:0:krb_ccache_hRtox00Defaultprincipal:user@AD.
DOMAINValidstartingExpiresServiceprincipal03.
05.
201618:31:0604.
05.
201604:31:01host/ipaserver.
ipa.
example.
com@IPA.
DOMAINrenewuntil04.
05.
201618:31:0003.
05.
201618:31:0604.
05.
201604:31:01krbtgt/IPA.
DOMAIN@AD.
DOMAINrenewuntil04.
05.
201618:31:0003.
05.
201618:31:0104.
05.
201604:31:01krbtgt/AD.
DOMAIN@AD.
DOMAINrenewuntil04.
05.
201618:31:00Thelocalauthplug-inmapsKerberosprincipalstolocalSSSDusernames.
ThisallowsADuserstouseKerberosauthenticationandaccessLinuxservices,whichsupportGSSAPIauthenticationdirectly.
NOTEFormoreinformationabouttheplug-in,seeSection5.
3.
7.
2,"UsingSSHWithoutPasswords".
5.
2.
2.
2.
CreatingaTrustUsingaSharedSecretAsharedsecretisapasswordthatisknowntotrustedpeersandcanbeusedbyotherdomainstojointhetrust.
Thesharedsecretcanconfigurebothone-wayandtwo-waytrustswithinActiveDirectory(AD).
InAD,thesharedsecretisstoredasatrusteddomainobject(TDO)withinthetrustconfiguration.
IdMsupportscreatingaone-wayortwo-waytrustusingasharedsecretinsteadoftheADadministratorcredentials.
SettingupsuchatrustrequirestheadministratortocreatethesharedsecretinADandmanuallyvalidatethetrustontheADside.
5.
2.
2.
2.
1.
CreatingaTwo-WayTrustUsingaSharedSecretTocreateatwo-waytrustwithasharedsecretwithaMicrosoftWindowsServer2012,2012R2,or2016:1.
PreparetheIdMserverforthetrust,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
2.
IftheIdMandADhostsuseaDNSserverthatcannotresolvebothdomains,setupforwardingfortheDNSzones:WindowsIntegrationGuide52a.
PreparetheADDNSservertoforwardqueriesfortheIdMdomaintotheIdMDNSserver.
Fordetails,seeSection5.
2.
1.
7,"CreatingaConditionalForwarderfortheIdMDomaininAD".
b.
PreparetheIdMDNSservertoforwardqueriesfortheADdomaintotheADDNSserver.
Fordetails,seeSection5.
2.
1.
8,"CreatingaForwardZonefortheADDomaininIdM".
3.
ConfigureatrustintheActiveDirectoryDomainsandTrustsconsole.
Inparticular:Createanewtrust.
GivethetrusttheIdMdomainname,forexampleidm.
example.
com.
Specifythatthisisaforesttypeoftrust.
Specifythatthisisatwo-waytypeoftrust.
Specifythatthisisaforest-wideauthentication.
Setthetrustpassword.
NOTEThesamepasswordmustbeusedwhenconfiguringthetrustinIdM.
Whenaskedtoconfirmtheincomingtrust,selectNo.
4.
Createatrustagreement,asdescribedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement".
Whenrunningtheipatrust-addcommand,usethe--type,--trust-secretand--two-way=Trueoptions,andomitthe--adminoption.
Forexample:[root@ipaserver~]#ipatrust-add--type=adad.
example.
com--trust-secret--two-way=TrueSharedsecretforthetrust:AddedActiveDirectorytrustforrealm"ad.
example.
com"Realm-Name:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912SIDblacklistincoming:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18SIDblacklistoutgoing:S-1-5-20,S-1-5-3,S-1-5-2,S-1-5-1,S-1-5-7,S-1-5-6,S-1-5-5,S-1-5-4,S-1-5-9,S-1-5-8,S-1-5-17,S-1-5-16,S-1-5-15,S-1-5-14,S-1-5-13,S-1-5-12,S-1-5-11,S-1-5-10,S-1-3,S-1-2,S-1-1,S-1-0,S-1-5-19,S-1-5-18Trustdirection:TrustingforestTrusttype:ActiveDirectorydomainTruststatus:Waitingforconfirmationbyremoteside5.
Retrievethelistofdomains:[root@ipaserver~]#ipatrust-fetch-domainsad_domainCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT536.
OntheIdMserver,verifythatthetrustrelationshipisestablishedbyusingtheipatrust-showcommand.
[root@ipaserver~]#ipatrust-showad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912Trustdirection:TrustingforestTrusttype:ActiveDirectorydomain7.
Optionally,searchforthetrusteddomain:[root@ipaserver~]#ipatrustdomain-findad.
example.
comDomainname:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912Domainenabled:True8.
VerifytheKerberosconfiguration,asdescribedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration".
5.
2.
2.
2.
2.
CreatingaOne-WayTrustUsingaSharedSecretTocreateaone-waytrustusingasharedsecretwithaMicrosoftWindowsServer2012,2012R2or2016:1.
PreparetheIdMserverforthetrust,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
2.
IftheIdMandADhostsuseaDNSserverthatcannotresolvebothdomains,setupforwardingfortheDNSzones:a.
PreparetheADDNSservertoforwardqueriesfortheIdMdomaintotheIdMDNSserver.
Fordetails,seeSection5.
2.
1.
7,"CreatingaConditionalForwarderfortheIdMDomaininAD".
b.
PreparetheIdMDNSservertoforwardqueriesfortheADdomaintotheADDNSserver.
Fordetails,seeSection5.
2.
1.
8,"CreatingaForwardZonefortheADDomaininIdM".
3.
ConfigureatrustintheActiveDirectoryDomainsandTrustsconsole:a.
Rightclicktothedomainname,andselectProperties.
b.
OntheTruststab,clickNewTrust.
c.
EntertheIdMdomainname,andclickNext.
d.
SelectForesttrust,andclickNext.
e.
SelectOne-way:incoming,andclickNext.
f.
SelectThisdomainonly,andclickNext.
g.
Enterasharedsecret(trustpassword),andclickNext.
h.
Verifythesettings,andclickNext.
WindowsIntegrationGuide54i.
Whenthesystemasksifyouwanttoconfirmtheincomingtrust,selectNo,donotconfirmtheincomingtrust,andclickNext.
j.
ClickFinish.
4.
Createatrustagreement:[root@ipaserver~]#ipatrust-add--type=ad--trust-secretad.
example.
comSharedsecretforthetrust:passwordAddedActiveDirectorytrustforrealm"ad.
example.
com"Realmname:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-1762709870-351891212-3141221786Trustdirection:TrustingforestTrusttype:ActiveDirectorydomainTruststatus:WaitingforconfirmationbyremotesideEnterthesharedsecretyousetintheADDomainsandTrustsconsole.
5.
ValidatethetrustintheActiveDirectoryDomainsandTrustsconsole:a.
Rightclicktothedomainname,andselectProperties.
b.
OntheTruststab,selectthedomainintheDomainsthattrustthisdomain(incomingtrusts)pane,andclickProperties.
c.
ClicktheValidatebutton.
d.
SelectYes,validatetheincomingtrust,andenterthecredentialsoftheIdMadminuser.
6.
Updatethelistoftrusteddomains:[root@ipaserver~]#ipatrust-fetch-domainsad.
example.
comCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT55Listoftrustdomainssuccessfullyrefreshed.
Usetrustdomain-findcommandtolistthem.
Numberofentriesreturned07.
Listthetrusteddomains:[root@ipaserver~]#ipatrustdomain-findad.
example.
comDomainname:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-1762709870-351891212-3141221786Domainenabled:TrueNumberofentriesreturned18.
Optionally,verifythattheIdMservercanretrieveuserinformationfromADdomain:[root@ipaserver~]#getentpasswdadministrator@ad.
example.
comadministrator@ad.
example.
com:*:610600500:610600500:Administrator:/home/ad.
example.
com/administrator:5.
2.
2.
3.
VerifyingtheIDMappingToverifytheIDmapping:1.
RunthefollowingcommandonaWindowsActiveDirectorydomaincontroller(DC)tolistthehighestID:C:\>dcdiag/v/test:ridmanager/s:ad.
example.
com.
.
.
AvailableRIDPoolfortheDomainis1600to1073741823.
.
.
2.
ListtheIDrangesonanIdMserver:[root@ipaserver~]#ipaidrange-find1rangematchedRangename:AD.
EXAMPLE.
COM_id_rangeFirstPosixIDoftherange:610600000NumberofIDsintherange:200000FirstRIDofthecorrespondingRIDrange:0DomainSIDofthetrusteddomain:S-1-5-21-796215754-1239681026-23416912Rangetype:ActiveDirectorydomainrangeNumberofentriesreturned1YourequirethefirstPOSIXIDvalueinalaterstep.
WindowsIntegrationGuide563.
OntheActiveDirectoryDC,displaythesecurityidentifier(SID)orauser.
Forexample,todisplaytheSIDofadministrator:C:\>wmicuseraccountwherename="administrator"getsidS-1-5-21-796215754-1239681026-23416912-500ThelastpartoftheSIDistherelativeidentifier(RID).
Yourequiretheuser'sRIDinthenextstep.
NOTEIftheRIDishigherthanthedefaultIDrange(200000),usetheipaidrange-modcommandtoextendtherange.
Forexample:#ipaidrange-mod--range-size=1000000AD.
EXAMPLE.
COM_id_range4.
DisplaytheuserIDofthesameuserontheIdMserver:[root@ipaserver~]#idad\\administratoruid=610600500(administrator@ad.
example.
com).
.
.
5.
IfyouaddthefirstPOSIXIDvalue(610600000)totheRID(500),itmustmatchtheuserIDdisplayedontheIdMserver(610600500).
5.
2.
2.
4.
CreatingaTrustonanExistingIdMInstanceWhenconfiguringatrustforanexistingIdMinstance,certainsettingsfortheIdMserverandentrieswithinitsdomainarealreadyconfigured.
However,youmustsettheDNSconfigurationfortheActiveDirectorydomainandassignActiveDirectorySIDstoallexistingIdMusersandgroups.
1.
PreparetheIdMserverforthetrust,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
2.
Createatrustagreement,asdescribedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement".
3.
GenerateSIDsforeachIdMuser.
NOTEDonotperformthisstepiftheSIDsweregeneratedwhentheipa-adtrust-installutilitywasusedtoestablishthetrust.
a.
AddanewipaNTSecurityIdentifierattribute,containingaSID,automaticallyforeachentrybyrunningtheipa-sidgen-taskoperationontheback-endLDAPdirectory.
[root@ipaserver]#ldapmodify-x-Hldap://ipaserver.
ipa.
example.
com:389-D"cn=directorymanager"-wpassworddn:cn=sidgen,cn=ipa-sidgen-task,cn=tasks,cn=configchangetype:addobjectClass:topobjectClass:extensibleObjectCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT57cn:sidgennsslapd-basedn:dc=ipadomain,dc=comdelay:0addingnewentry"cn=sidgen,cn=ipa-sidgen-task,cn=tasks,cn=config"b.
Afterthetaskcompletessuccessfully,amessageisrecordedintheerrorlogsthattheSIDgenerationtask(Sidgentask)finishedwithastatusofzero(0).
[root@ipaserver]#grep"sidgen_task_thread"/var/log/dirsrv/slapd-IDM-EXAMPLE-COM/errors[20/Jul/2012:18:17:16+051800]sidgen_task_thread-[fileipa_sidgen_task.
c,line191]:Sidgentaskstarts.
.
.
[20/Jul/2012:18:17:16+051800]sidgen_task_thread-[fileipa_sidgen_task.
c,line196]:Sidgentaskfinished[0].
4.
VerifytheKerberosconfiguration,asdescribedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration".
5.
2.
2.
5.
AddingaSecondTrustWhenaddingatrustonanIdMserverthatalreadyhasoneormoretrustagreementsconfigured,certaingeneralIdMtrustsettings,suchasinstallingthetrust-relatedpackagesorconfiguringSIDs,isnolongerrequired.
Toaddanadditionaltrust,youonlymustconfigureDNSandestablishatrustagreement.
1.
MakesurethatDNSisproperlyconfigured,asdescribedinSection5.
2.
1.
2,"DNSandRealmSettings".
2.
Createatrustagreement,asdescribedinSection5.
2.
2.
1.
2,"CreatingaTrustAgreement".
5.
2.
2.
6.
CreatingaTrustintheWebUIBeforecreatingatrustinthewebUI,preparetheIdMserverforthetrust.
Thistrustconfigurationiseasiesttoperformfromthecommandline,asdescribedinSection5.
2.
2.
1.
1,"PreparingtheIdMServerforTrust".
Oncetheinitialconfigurationisset,atrustagreementcanbeaddedintheIdMwebUI:1.
OpentheIdMwebUI:https://ipaserver.
example.
com2.
OpentheIPAServermaintab,andselecttheTrustssubtab.
3.
IntheTrustssubtab,clickAddtoopenthenewtrustconfigurationwindow.
4.
Fillintherequiredinformationaboutthetrust:a.
ProvidetheADdomainnameintheDomainfield.
b.
Tosetupthetrustastwo-way,selecttheTwo-waytrustcheckbox.
Tosetupthetrustasone-way,leaveTwo-waytrustunselected.
Formoreinformationaboutone-wayandtwo-waytrusts,seeSection5.
1.
4,"One-WayandTwo-WayTrusts".
WindowsIntegrationGuide58c.
Toestablishanexternaltrusttoadomaininanotherforest,selecttheExternalTrustcheckbox.
Formoreinformation,seeSection5.
1.
5,"ExternalTruststoActiveDirectory".
d.
TheEstablishusingsectiondefineshowthetrustistobeestablished:ToestablishthetrustusingtheADadministrator'susernameandpassword,selectAdministrativeaccountandprovidetherequiredcredentials.
Alternatively,toestablishthetrustwithasharedpassword,selectPre-sharedpasswordandprovidethetrustpassword.
e.
DefinetheIDconfigurationforthetrust:TheRangetypeoptionallowsyoutochoosetheIDrangetype.
IfyouwantIdMtoautomaticallydetectwhatkindofIDrangetouse,selectDetect.
TodefinethestartingIDoftheIDrange,usetheBaseIDfield.
TodefinethesizeoftheIDrange,usetheRangesizefield.
IfyouwantIdMtousedefaultvaluesfortheIDrange,donotspecifytheseoptions.
FormoreinformationaboutIDranges,seethesectioncalled"IDRanges".
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT59Figure5.
5.
AddingaTrustintheWebUI5.
ClickAddtosavethenewtrust.
Afterthis,verifytheKerberosconfiguration,asdescribedinSection5.
2.
2.
1.
3,"VerifyingtheKerberosConfiguration".
5.
2.
3.
Post-installationConsiderationsforCross-forestTrusts5.
2.
3.
1.
PotentialBehaviorIssueswithActiveDirectoryTrust5.
2.
3.
1.
1.
ActiveDirectoryUsersandIdMAdministrationCurrently,ActiveDirectory(AD)usersandadministratorscanonlyseetheirself-servicepageafterloggingintotheIdMWebUI.
ADadministratorscannotaccesstheadministrator'sviewofIdMWebUI.
Fordetails,seethecorrespondingsectionoftheLinux_Domain_Identity_Authentication_and_Policy_Guide.
Additionally,ADuserscurrentlycannotmanagetheirownIDoverrides.
OnlyIdMuserscanaddandWindowsIntegrationGuide60Additionally,ADuserscurrentlycannotmanagetheirownIDoverrides.
OnlyIdMuserscanaddandmanageIDoverrides.
5.
2.
3.
1.
2.
AuthenticatingDeletedActiveDirectoryUsersBydefault,everyIdMclientusestheSSSDservicetocacheuseridentitiesandcredentials.
IftheIdMorADback-endprovideristemporarilyunavailable,SSSDenablesthelocalsystemtoreferenceidentitiesforuserswhohavealreadyloggedinsuccessfullyonce.
BecauseSSSDmaintainsalistofuserslocally,changesthataremadeonthebackendmightnotbeimmediatelyvisibletoclientsthatrunSSSDoffline.
Onsuchclients,userswhohavepreviouslyloggedintoIdMresourcesandwhosehashedpasswordsarestoredintheSSSDcacheareabletologinagaineveniftheiruseraccountshavebeendeletedinAD.
Iftheaboveconditionsaremet,theuseridentityiscachedinSSSD,andtheADuserisabletologintoIdMresourceseveniftheuseraccountisdeletedAD.
ThisproblemwillpersistuntilSSSDbecomesonlineandisabletoverifyADuserlogonagainstADdomaincontrollers.
IftheclientsystemrunsSSSDonline,thepasswordprovidedbytheuserisvalidatedbyanADdomaincontroller.
ThisensuresthatdeletedADusersarenotallowedtologin.
5.
2.
3.
1.
3.
CredentialCacheCollectionsandSelectingActiveDirectoryPrincipalsTheKerberoscredentialscacheattemptstomatchaclientprincipaltoaserverprincipalbasedonthefollowingidentifiersinthisorder:1.
servicename2.
hostname3.
realmnameWhentheclientandservermappingisbasedonthehostnameorrealnameandcredentialcachecollectionsareused,unexpectedbehaviorcanoccurinbindingasanADuser.
ThisisbecausetherealmnameoftheActiveDirectoryuserisdifferentthantherealmnameoftheIdMsystem.
IfanADuserobtainsaticketusingthekinitutilityandthenusesSSHtoconnecttoanIdMresource,theprincipalisnotselectedfortheresourceticket.
anIdMprincipalisusedbecausetheIdMprincipalmatchestherealmnameoftheresource.
Forexample,iftheADuserisAdministratorandthedomainisADEXAMPLE.
ADREALM,theprincipalisAdministrator@ADEXAMPLE.
ADREALM.
[root@server~]#kinitAdministrator@ADEXAMPLE.
ADREALMPasswordforAdministrator@ADEXAMPLE.
ADREALM:[root@server~]#klistTicketcache:KEYRING:persistent:0:0Defaultprincipal:Administrator@ADEXAMPLE.
ADREALMValidstartingExpiresServiceprincipal27.
11.
201511:25:2327.
11.
201521:25:23krbtgt/ADEXAMPLE.
ADREALM@ADEXAMPLE.
ADREALMrenewuntil28.
11.
201511:25:16ThisissetasthedefaultprincipalintheActiveDirectoryticketcache.
However,ifanyIdMuseralsohasaKerberosticket(suchasadmin),thenthereisaseparateIdMcredentialscache,withanIdMdefaultCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT61principal.
ThatIdMdefaultprincipalisselectedforahostticketiftheActiveDirectoryuserusesSSHtoconnecttoaresource.
[root@vm-197~]#ssh-lAdministrator@adexample.
adrealmipaclient.
example.
comAdministrator@adexample.
adrealm@ipaclient.
example.
com'spassword:[root@vm-197~]#klist-ATicketcache:KEYRING:persistent:0:0Defaultprincipal:Administrator@ADEXAMPLE.
ADREALMValidstartingExpiresServiceprincipal27.
11.
201511:25:2327.
11.
201521:25:23krbtgt/ADEXAMPLE.
ADREALM@ADEXAMPLE.
ADREALMrenewuntil28.
11.
201511:25:16Ticketcache:KEYRING:persistent:0:0Defaultprincipal:admin@EXAMPLE.
COM>>>>>IdMuserValidstartingExpiresServiceprincipal27.
11.
201511:25:1828.
11.
201511:25:16krbtgt/EXAMPLE.
COM@EXAMPLE.
COM27.
11.
201511:25:4828.
11.
201511:25:16host/ipaclient.
example.
com@EXAMPLE.
COM>>>>>hostprincipalThisisbecausetherealmnameoftheIdMprincipalmatchestherealmoftheIdMresource.
5.
2.
3.
1.
4.
ResolvingGroupSIDsLosingKerberosTicketsRunningacommandtoobtainaSIDfromtheSambaservice,suchasnetgetlocalsidornetgetdomainsid,removesanyexistingadminticketfromtheKerberoscache.
NOTEYouarenotrequiredtoruncommandssuchasnetgetlocalsidornetgetdomainsidinordertouseActiveDirectorytrusts.
CannotVerifyGroupMembershipforUsersItisnotpossibletoverifythataspecifictrusteduserisassociatedwithaspecificIdMgroup,externalorPOSIX.
CannotDisplayRemoteActiveDirectoryGroupMembershipsforanActiveDirectoryUserIMPORTANTNotethatthisproblemnolongeroccursiftheIdMserverandclientrunonRedHatEnterpriseLinux7.
1orlater.
TheidutilitycanbeusedtodisplaylocalgroupassociationsforLinuxsystemusers.
However,iddoesnotdisplayActiveDirectorygroupmembershipsforActiveDirectoryusers,eventhoughSambatoolsdodisplaythem.
Toworkaroundthis,youcanusethesshutilitytologintoanIdMclientmachineasthegivenADuser.
WindowsIntegrationGuide62Toworkaroundthis,youcanusethesshutilitytologintoanIdMclientmachineasthegivenADuser.
AftertheADuserlogsinsuccessfullyforthefirsttime,theidsearchdetectsanddisplaystheADgroupmemberships:[root@ipaserver~]#idADDOMAIN\useruid=1921801107(user@ad.
example.
com)gid=1921801107(user@ad.
example.
com)groups=1921801107(user@ad.
example.
com),129600004(ad_users),1921800513(domainusers@ad.
example.
com)5.
2.
3.
2.
ConfiguringTrustAgentsAfteryousetupanewreplicainatrustenvironment,thereplicadoesnotautomaticallyhavetheADtrustagentroleinstalled.
Toconfigurethereplicaasatrustagent:1.
Onanexistingtrustcontroller,runtheipa-adtrust-install--add-agentscommand:[root@existing_trust_controller]#ipa-adtrust-install--add-agentsThecommandstartsaninteractiveconfigurationsessionandpromptsyoufortheinformationrequiredtosetuptheagent.
Forfurtherinformationaboutthe--add-agentsoption,seetheipa-adtrust-install(1)manpage.
2.
Onthenewreplica:a.
RestarttheIdMservice:[root@new_trust_controller]#ipactlrestartb.
RemoveallentriesfromtheSSSDcache:[root@new_trust_controller]#sssctlcache-removeNOTETousethesssctlcommand,thesssd-toolspackagemustbeinstalled.
c.
Optionally,verifythatthereplicahastheADtrustagentroleinstalled:[root@new_trust_controller]#ipaserver-shownew_replica.
idm.
example.
com.
.
.
Enabledserverroles:CAserver,NTPserver,ADtrustagent5.
3.
MANAGINGANDCONFIGURINGACROSS-FORESTTRUSTENVIRONMENT5.
3.
1.
UserPrincipalNamesinaTrustedDomainsEnvironmentIdMsupportsthelogginginusinguserprincipalnames(UPN).
AUPNisanalternativetotheusernametoauthenticatewith,andhastheformatusername@KERBEROS-REALM.
InanActiveDirectoryforestitispossibletoconfigureadditionalUPNsuffixes.
TheseenterpriseprincipalnamesareusedtoprovideCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT63alternativeloginstothedefaultUPN.
Forexample,ifacompanyusestheKerberosrealmAD.
EXAMPLE.
COM,thedefaultUPNforauserisuser@ad.
example.
com.
Howeveroftenacompanywantinsteadtheiruserstobeabletologinusingtheiremailaddresses,likeuser@example.
com.
InthiscasetheadministratoraddsanadditionalUPNsuffixexample.
comtotheActiveDirectoryforestandsetsthenewsuffixintheuser'saccountproperties.
WhenyouaddorremoveUPNsuffixesinatrustedADforest,youhavetorefreshtheinformationforthetrustedforestontheIdMmaster:[root@ipaserver~]#ipatrust-fetch-domainsRealm-Name:ad.
example.
comNonewtrustdomainswerefoundNumberofentriesreturned0VerifythatthealternativeUPNwasfetched,byrunning:[root@ipaserver~]#ipatrust-showRealm-Name:ad.
example.
comRealm-Name:ad.
example.
comDomainNetBIOSname:ADDomainSecurityIdentifier:S-1-5-21-796215754-1239681026-23416912Trustdirection:Two-waytrustTrusttype:ActiveDirectorydomainUPNsuffixes:example.
comTheUPNsuffixesforadomainarestoredinthemulti-valueattributeipaNTAdditionalSuffixesinthecn=trusted_domain_name,cn=ad,cn=trusts,dc=idm,dc=example,dc=comsubtree.
5.
3.
2.
IdMClientsinanActiveDirectoryDNSDomainInsomeenvironmentswithtrustsbetweenIdMandActiveDirectory,youcanconfigureuserstoaccessanIdMclientusingahostnamefromtheActiveDirectoryDNSdomain,whiletheclientitselfisjoinedtoIdMtobenefitfromitsLinux-focusedfeatures.
IMPORTANTThisisnotarecommendedconfigurationandhassomelimitations.
RedHatrecommendstoalwaysdeployIdMclientsinaDNSzonedifferentfromtheonesownedbyActiveDirectoryandaccessIdMclientsthroughtheirIdMhostnames.
5.
3.
2.
1.
KerberosSingleSign-ontotheIdMClientisnotRequiredForIdMclientssetupintheActiveDirectoryDNSdomain,onlypasswordauthenticationisavailabletoaccessresourcesonthisIdMhost.
Toconfiguretheclientforthisscenario:1.
ToensurethattheSystemSecurityServiceDaemon(SSSD)ontheclientcancommunicatewiththeIdMservers,installtheIdMclientwiththe--domain=IPA_DNS_Domainoption:WindowsIntegrationGuide64[root@idm-client.
ad.
example.
com~]#ipa-client-install--domain=idm.
example.
comThisoptiondisablestheSRVrecordauto-detectionfortheActiveDirectoryDNSdomain.
2.
LocatetheexistingmappingfortheActiveDirectorydomaininthe[domain_realm]sectionofthe/etc/krb5.
confconfigurationfile:.
ad.
example.
com=IDM.
EXAMPLE.
COMad.
example.
com=IDM.
EXAMPLE.
COMReplacebothlineswithamappingentryfortheLinuxclientsfullyqualifieddomainname(FQDN)intheActiveDirectoryDNSzonetotheIdMrealm:idm-client.
ad.
example.
com=IDM.
EXAMPLE.
COMReplacingthedefaultmappingpreventsKerberosfromsendingitsrequestsfortheActiveDirectorydomaintotheIdMKerberosDistributionCenter(KDC).
InsteadKerberosusesauto-discoverythroughSRVDNSrecordstolocatetheKDC.
Onlyfortheaddedhostidm-client.
ad.
example.
comtheIdMKDCisset.
NOTEAuthenticatingtoresourcesonclientsthatarenotwithinanIdM-ownedDNSzoneisonlypossiblebyusingusernameandpassword.
HandlingofSSLcertificatesSSL-basedservicesrequireacertificatewithdNSNameextensionrecordsthatcoverallsystemhostnames,becausebothoriginal(A/AAAA)andCNAMErecordsmustbeinthecertificate.
Currently,IdMonlyissuescertificatestohostobjectsintheIdMdatabase.
Inthedescribedsetupwithoutsinglesign-onavailable,IdMalreadyhasahostobjectfortheFQDNinthedatabase,andcertmongercanrequestacertificateforthisname:[root@idm-client.
ad.
example.
com~]#ipa-getcertrequest-r\-f/etc/httpd/alias/server.
crt\-k/etc/httpd/alias/server.
key\-NCN=ipa-client.
ad.
example.
com\-Dipa-client.
ad.
example.
com\-Khost/idm-client.
ad.
example.
com@IDM.
EXAMPLE.
COM\-Uid-kp-serverAuthThecertmongerserviceusesthedefaulthostkeystoredinthe/etc/krb5.
keytabfiletoauthenticatetotheIdMCertificateAuthority(CA).
5.
3.
2.
2.
KerberosSingleSign-ontotheIdMClientisRequiredIfyourequireKerberossinglesign-ontoaccessresourcesontheIdMclient,theclientmustbewithintheIdMDNSdomain,forexampleidm-client.
idm.
example.
com.
YoumustcreateaCNAMErecordidm-client.
ad.
example.
comintheActiveDirectoryDNSdomainpointingtotheA/AAAArecordoftheIdMclient.
ForKerberos-basedapplicationservers,MITKerberossupportsamethodtoallowtheacceptanceofanyhost-basedprincipalavailableintheapplication'skeytab.
TodisablethestrictchecksonwhatCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT65KerberosprincipalwasusedtotargettheKerberosserver,setthefollowingoptioninthe[libdefaults]sectionofthe/etc/krb5.
confconfigurationfile:ignore_acceptor_hostname=trueHandlingofSSLcertificatesSSL-basedservicesrequireacertificatewithdNSNameextensionrecordsthatcoverallsystemhostnames,becausebothoriginal(A/AAAA)andCNAMErecordsmustbeinthecertificate.
Currently,IdMonlyissuescertificatestohostobjectsintheIdMdatabase.
Inthedescribedsetupwithoutsinglesign-onavailable,IdMalreadyhasahostobjectfortheFQDNinthedatabase,andcertmongercanrequestacertificateforthisname:1.
Createanewhostobject:[root@idm-server.
idm.
example.
com~]#ipahost-addidm-client.
ad.
example.
com--forceUsethe--forceoption,becausethehostnameisaCNAMEandnotanA/AAAArecord.
2.
AllowtheIdMDNShostnametomanagetheActiveDirectoryhostentryintheIdMdatabase:[root@idm-server.
idm.
example.
com~]#ipahost-add-managedbyidm-client.
ad.
example.
com\--hosts=idm-client.
idm.
example.
comWiththissetup,theIdMclientcanrequestanSSLcertificatewithdNSNameextensionrecordforitshostnamewithintheActiveDirectoryDNSdomain:[root@idm-client.
idm.
example.
com~]#ipa-getcertrequest-r\-f/etc/httpd/alias/server.
crt\-k/etc/httpd/alias/server.
key\-NCN=`hostname--fqdn`\-D`hostname--fqdn`\-Didm-client.
ad.
example.
com\-Khost/idm-client.
idm.
example.
com@IDM.
EXAMPLE.
COM\-Uid-kp-serverAuth5.
3.
3.
CreatingIdMGroupsforActiveDirectoryUsersUsergroupsarerequiredtosetaccesspermissions,host-basedaccesscontrol,sudorules,andothercontrolsonIdMusers.
ThesegroupsarewhatgrantaccesstoIdMdomainresources,aswellasrestrictingaccess.
BothADusersandADgroupscanbeaddeddirectlytoIdMusergroups.
Todothat,firstaddtheADusersorgroupstoanon-POSIXIdMexternalgroupandthentoalocalIdMPOSIXgroup.
ThePOSIXgroupcanthenbeusedforuserandrolemanagementoftheADusers.
Theprinciplesofhandlingnon-POSIXgroupsinIdMaredescribedinSection5.
1.
3.
2,"ActiveDirectoryUsersandIdentityManagementGroups".
NOTEWindowsIntegrationGuide66NOTEItisalsopossibletoaddADusergroupsasmemberstoIdMexternalgroups.
ThismightmakeiteasiertodefinepoliciesforWindowsusers,bykeepingtheuserandgroupmanagementwithinthesingleADrealm.
1.
Optional.
CreateorselectthegroupintheADdomaintousetomanageADusersintheIdMrealm.
MultiplegroupscanbeusedandaddedtodifferentgroupsontheIdMside.
2.
CreateanexternalgroupintheIdMdomainfortheActiveDirectoryusersbyaddingthe--externaloptiontotheipagroup-addcommand.
The--externaloptionindicatesthatthisgroupisintendedtocontainmembersfromoutsidetheIdMdomain.
Forexample:[root@ipaserver~]#ipagroup-add--desc='ADusersexternalmap'ad_users_external--externalAddedgroup"ad_users_external"Groupname:ad_users_externalDescription:ADusersexternalmapNOTETheexternalgroupmustbelinkedtoaadditionalgroupofauserandnottotheuser'sprimarygroup.
ActiveDirectorystoresgroupmembersinmemberattributesofagroup,andIdMusesthisattributetoresolvethemembers.
However,ActiveDirectorystorestheprimarygroupofusersintheprimaryGroupIDattributeintheuser'sentry,whichisnotresolved.
3.
CreateanewIdMPOSIXgrouporselectanexistingoneforadministeringtheIdMpolicies.
Forexample,tocreateanewgroup:[root@ipaserver~]#ipagroup-add--desc='ADusers'ad_usersAddedgroup"ad_users"Groupname:ad_usersDescription:ADusersGID:1296000044.
AddtheADusersorgroupstotheIdMexternalgroupasanexternalmember.
TheADmemberisidentifiedbyitsfully-qualifiedname,suchasDOMAIN\group_nameorDOMAIN\username.
TheADidentityisthenmappedtotheActiveDirectorySIDfortheuserorgroup.
Forexample,foranADgroup:[root@ipaserver~]#ipagroup-add-memberad_users_external--external"AD\DomainUsers"[memberuser]:[membergroup]:Groupname:ad_users_externalDescription:ADusersexternalmapExternalmember:S-1-5-21-3655990580-1375374850-1633065477-513CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT67SID_DOM_GROUP(2)Numberofmembersadded15.
AddtheexternalIdMgrouptothePOSIXIdMgroupasamember.
Forexample:[root@ipaserver~]#ipagroup-add-memberad_users--groupsad_users_externalGroupname:ad_usersDescription:ADusersGID:129600004Membergroups:ad_users_externalNumberofmembersadded15.
3.
4.
MaintainingTrustsTrustmanagementinvolvesseveralareas,suchasglobaltrustconfiguration,Kerberostrustconfiguration,DNSrealmconfiguration,orIDrangesassignmenttoActiveDirectoryusers.
5.
3.
4.
1.
EditingtheGlobalTrustConfigurationTheipa-adtrust-installutilityautomaticallyautomaticallyconfiguresbackgroundinformationfortheIdMdomainwhichisrequiredtocreateatrustwiththeActiveDirectorydomain.
Theglobaltrustconfigurationcontainsfiveattributes:AWindows-stylesecurityID(SID);thisattributeisautogeneratedandcannotbemodifiedAdomainGUID;thisattributeisautogeneratedandcannotbemodifiedAKerberosdomainname;thisattributecomesfromtheIdMconfigurationandcannotbemodifiedThedefaultgrouptowhichtoaddIdMusers;thisattributecanbemodifiedTheNetBIOSname;itisnotrecommendedtomodifythisattributeThetrustconfigurationisstoredinthecn=domain,cn=ad,cn=etc,dc=example,dc=comsubtree.
5.
3.
4.
1.
1.
ChangingtheNetBIOSNameIMPORTANTChangingtheNetBIOSnameinmostcasesrequirestore-establishallexistingtrusts.
Therefore,RedHatrecommendsnottochangetheattribute.
ANetBIOSnamecompatiblewithinanActiveDirectorytopologyisconfiguredfortheIdMserverwhenrunningtheipa-adtrust-installutility.
Tochangeitlater,runipa-adtrust-installagainandspecifythenewNetBIOSnameusingthe--netbios-nameoption:[root@ipaserver]#ipa-adtrust-install--netbios-name=NEWBIOSNAMEWindowsIntegrationGuide685.
3.
4.
1.
2.
ChangingtheDefaultGroupforWindowsUsersWhenIdentityManagementisconfiguredtotrustanActiveDirectoryforest,anMS-PACrecordisaddedtotheKerberosticketsofIdMusers.
AnMS-PACrecordcontainssecurityidentifiers(SIDs)ofthegroupstowhichanIdMuserbelongs.
IftheprimarygroupoftheIdMuserhasnoSIDassigned,thevalueofthesecurityidentifierdefinedfortheDefaultSMBGroupwillbeused.
ThesamelogicisappliedbytheSambasuitewhentheADdomaincontrollerrequestsuserinformationfromtheIdMtrustcontroller.
TheDefaultSMBGroupisafallbackgroupcreatedautomaticallybytheipa-adtrust-installutility.
Thedefaultgroupcannotbedeleted,butyoucanusetheglobaltrustconfigurationtospecifyanotherIdMgrouptobeusedasafallbackfortheprimarygroupoftheIdMusers.
Tosetthedefaultgroupfromthecommandline,usetheipatrustconfig-modcommand:[root@server~]#kinitadmin[root@server~]#ipatrustconfig-mod--fallback-primary-group="ExampleWindowsGroup"TosetthedefaultgroupfromtheIdMwebUI:1.
OpentheIdMwebUI.
https://ipaserver.
example.
com2.
UndertheIPAServermaintab,selecttheTrustssubtab,andthenopentheGlobalConfigurationsection.
3.
SelectanewgroupfromalloftheIdMgroupsintheFallbackprimarygroupdrop-downlist.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT69Figure5.
6.
ConfiguringtheDefaultGroupforWindowsUsers4.
ClickSavetosavethenewconfiguration.
5.
3.
4.
2.
Discovering,Enabling,andDisablingTrustDomainsAtransitivetrustmeansthatthetrustpathcanfollowachainofdomains.
ItisdescribedinmoredetailinSection5.
1.
1,"TheArchitectureofaTrustRelationship".
IdMhasatrustwiththerootdomaininaforestand,duetotransitivity,allofitschilddomainsandotherdomainsfromthesameforestareimplicitlyincludedinthattrust.
IdMfollowsthattopologyasWindowsusersfromanywhereintheforestattempttoaccessIdMresources.
EachdomainandchilddomainisatrustdomainintheIdMtrustconfiguration.
Eachdomainisstoredinitsownentry,cn=subdomain,cn=trust_name,cn=ad,cn=trusts,dc=example,dc=cominthetrustssubtree.
IdMattemptstodiscoverandmapthefullActiveDirectorytopologywhenthetrustisfirstconfigured,althoughinsomecasesitisrequiredorbeneficialtoretrievethattopologymanually.
Thatisdonewiththetrust-fetch-domainscommand:[root@ipaserver~]#kinitadmin[root@ipaserver~]#ipatrust-fetch-domainsad.
example.
comListoftrustdomainssuccessfullyrefreshedRealmname:test.
ad.
example.
comDomainNetBIOSname:TESTDomainSecurityIdentifier:S-1-5-21-87535643-5658642561-5780864324WindowsIntegrationGuide70Realmname:users.
ad.
example.
comDomainNetBIOSname:USERSDomainSecurityIdentifier:S-1-5-21-91314187-2404433721-1858927112Realmname:prod.
ad.
example.
comDomainNetBIOSname:PRODDomainSecurityIdentifier:S-1-5-21-46580863-3346886432-4578854233Numberofentriesreturned3NOTEWhenaddingatrustwithasharedsecret,youneedtomanuallyretrievetopologyoftheADforest.
Afterrunningtheipatrust-addad.
domain--trust-secretcommand,validateincomingtrustatADsideusingforesttrustpropertiesintheADDomainsandTruststool.
Then,runtheipatrust-fetch-domainsad.
domaincommand.
IdMwillreceiveinformationaboutthetrust,whichwillthenbeusable.
Oncethetopologyisretrieved(throughautomaticormanualdiscovery),individualdomainsandchilddomainsinthattopologycanbeenabled,disabled,orremovedentirelywithintheIdMtrustconfiguration.
Forexample,todisallowusersfromaspecificchilddomainfromusingIdMresources,disablethattrustdomain:[root@ipaserver~]#kinitadmin[root@ipaserver~]#ipatrustdomain-disabletest.
ad.
example.
comDisabledtrustdomain"test.
ad.
example.
com"Thattrustdomaincanbere-enabledusingthetrustdomain-enablecommand.
Ifadomainshouldbepermanentlyremovedfromthetopology,thanitcanbedeletedfromtheIdMtrustconfiguration.
[root@ipaserver~]#kinitadmin[root@ipaserver~]#ipatrustdomain-delprod.
ad.
example.
comRemovedinformationaboutthetrusteddomain""prod.
ad.
example.
com"5.
3.
4.
3.
ViewingandmanagingdomainsassociatedwithIdMKerberosrealmDomainsthatareassociatedwiththeIdMKerberosrealmarestoredinthecn=RealmDomains,cn=ipa,cn=etc,dc=example,dc=comsubtreeintheIdMdirectory.
ThelistofdomainsisusedbyIdMwhenitestablishesatrustwithActiveDirectory.
KnowingthefulllistofdomainsmanagedbyIdMallowstheADdomaincontrollertoknowwhichauthenticationrequeststoroutetotheIdMKDC.
ThelistofconfigureddomainsassociatedwithIdMrealmcanbedisplayedusingtherealmdomains-showcommand:CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT71[root@ipaserver~]#kinitadmin[root@ipaserver~]#iparealmdomains-showDomain:ipa.
example.
org,ipa.
example.
com,example.
comInanIdMsetupwithintegratedDNS:AdomainisautomaticallyaddedtothedomainslistafteranewDNSzoneisaddedtoIdMusingtheipadnszone-addcommand.
Runningiparealmdomains-showshowsthenewdomaininthelistofdomainscontrolledbytheIdMKDC:#kinitadmin#ipadnszone-addipa2.
example.
com#iparealmdomains-showDomain:ipa.
example.
org,ipa.
example.
com,example.
com,ipa2.
example.
comDeletionandothertypesofmodificationofdomainsassociatedwiththeIdMKerberosrealmarealsotakencareofautomatically.
InanIdMsetupwithoutintegratedDNS:IfaDNSzonehasbeenaddedthatispartoftheIdMKerberosrealm,thenewdomainhastobeaddedmanuallytotheIdMlistofdomainsunderthecontroloftheIdMKDC.
Addthenewdomainusingtheiparealmdomains-modcommandwiththe--add-domainoption:[root@ipaserver~]#kinitadmin[root@ipaserver~]#iparealmdomains-mod--add-domain=ipa2.
example.
comDomain:ipa.
example.
org,ipa.
example.
com,example.
com,ipa2.
example.
comIfaDNSzonehasbeendeleted,youneedtodeletethedomainassociatedwiththeIdMKerberosrealmmanually,too:[root@ipaserver~]#kinitadmin[root@ipaserver~]#iparealmdomains-mod--del-domain=ipa2.
example.
comDomain:ipa.
example.
org,ipa.
example.
com,example.
comIftherearemultiplechangestobemadetothelistofdomains,thelistitselfcanbemodifiedandreplacedusingthe--domainoption.
[root@ipaserver~]#iparealmdomains-mod--domain={ipa.
example.
org,ipa2.
example.
com}5.
3.
4.
4.
AddingRangesforUIDandGIDNumbersinaTransitiveTrustCreatingIDrangesatthetimewhenatrustisoriginallyconfiguredisdescribedinthesectioncalled"IDRanges".
ToaddanIDrangelater,usetheipaidrange-addcommandwiththefollowingoptions:the--base-idoptionsetsthebaseIDforthePOSIXrange,whichisthestartingnumberThe--range-sizeoptionsetsthesizeofthePOSIXIDrangeIdMuses.
IdMmapstheRIDofusersandgroupsinatrustedADdomaintoPOSIXIDs.
The--range-sizeoptiondefinesthemaximumnumberofIDsIdMcreates.
ADusesanewRIDforeachuserandgroupyoucreate.
Ifyoudeleteauserorgroup,ADwillnotre-usetheRIDforfutureADentries.
Therefore,therangemustbelargeenoughforIdMtoassignanIDtoeachexistingADuserandgroupaswellastheonesyoucreateinthefuture.
Forexample,ifanadministratordeletes20000of50000ADusersandwill,duringthetime,create10000newaccounts,therangemustbeatleastsettoWindowsIntegrationGuide7260000.
However,itisimportantthattherangealsocontainsenoughreserves.
Inlargeenvironments,inwhichyouexpectthatthedefault(200000)rangesizeisnotsufficient,set--range-sizetoahighervalue.
the--rid-baseoptionsetsthestartingnumberoftheRID,whichisthefar-rightnumberintheSID;thevaluerepresentstherangetoaddtothebaseIDtopreventconflictsthe--dom-sidoptionsetsthedomainSID,becausetherecanbemultipledomainsconfiguredfortrustsInthefollowingexample,thebaseIDis1,200,000andtheRIDis1,000.
TheresultingIDnumberisthen1,201,000.
[root@server~]$kinitadmin[root@server~]$ipaidrange-add--base-id=1200000--range-size=200000--rid-base=0--dom-sid=S-1-5-21-123-456-789trusted_dom_rangeIMPORTANTMakesurethatthemanuallydefinedIDrangedoesnotoverlapwiththeIDrangeusedbyIdM.
5.
3.
4.
5.
AdjustingDNAIDrangesmanuallyInsomecases,youmayneedtomanuallyadjustDistributedNumericAssignment(DNA)IDrangesforexistingreplicas,forexampletorecoveraDNAIDrangeassignedtoanon-functioningreplicaortoextendarangethathasrunoutofIDs.
WhenadjustingaDNAIDrangemanually,makesurethatthenewlyadjustedrangeisincludedintheIdMIDrange.
Youcancheckthisusingtheipaidrange-findcommand.
IfthenewlyadjustedrangeisnotincludedintheIdMIDrange,thecommandfails.
TorecoveraDNAIDrangefromanon-functioningreplica,usetheipa-replica-managednarange-showcommandtoseecurrentlyassignedDNAranges.
Toseethecurrentlyassignedon-deckDNAranges,usetheipa-replica-managednanextrange-showcommand.
IMPORTANTDonotcreateoverlappingIDranges.
IfanyoftheIDrangesyouassigntoserversorreplicasoverlap,itcouldresultintwodifferentserversassigningthesameIDvaluetodifferententries.
TodefinethecurrentDNAIDrangeforaspecifiedserver,usetheipa-replica-managednarange-setcommand:#ipa-replica-managednarange-setmasterA.
example.
com1250-1499TodefinethenextDNAIDrangeforaspecifiedserver,usetheipa-replica-managednanextrange-setcommand:#ipa-replica-managednanextrange-setmasterB.
example.
com1500-5000CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT735.
3.
4.
6.
KerberosFlagsforServicesandHostsAccessingservicesorhostsinatrusteddomaincanrequirespecialflagsfortheKerberosticket-grantingticket(TGT).
Forexample,ifyouwanttologinusingsinglesign-ontoanIdMclientwithanActiveDirectory(AD)accountfromanADclient,theKerberosTGTflagOK_AS_DELEGATEisrequired.
FormoreinformationandhowtosetKerberosflags,seeKerberosFlagsforServicesandHostsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
5.
3.
5.
SettingPACTypesforServicesOnIdMresources,ifanActiveDirectoryuserrequestsaticketforaservice,thenIdMforwardstherequesttoActiveDirectorytoretrievetheuserinformation.
Accessdata,associatedwiththeActiveDirectorygroupassignmentsfortheuser,issentbackbyActiveDirectoryandembeddedintheKerberosticket.
GroupinformationinActiveDirectoryisstoredinalistofidentifiersineachKerberosticketforActiveDirectoryusersinaspecialdatasetcalledprivilegedaccesscertificatesorMS-PAC.
ThegroupinformationinthePAChastobemappedtotheActiveDirectorygroupsandthentothecorrespondingIdMgroupstohelpdetermineaccess.
IdMservicescanbeconfiguredtogeneratePACsforeachauthenticationrequestwhenauserfirstattemptstoauthenticatetoadomainservice.
5.
3.
5.
1.
SettingDefaultPACTypesTheIdMserverconfigurationdefineswhichPACtypesaregeneratedbydefaultforaservice.
Theglobalsettingscanbeoverriddenbychangingthelocalsettingsonaspecificservice.
1.
OpentheIPAServertab.
2.
SelecttheConfigurationsubtab.
3.
ScrolltotheServiceOptionsarea.
Figure5.
7.
TheServiceOptionsArea4.
TousePAC,selecttheMS-PACcheckbox,whichaddsacertificatethatcanbeusedbyADservices.
Ifnocheckboxisselected,thennoPACisaddedtoKerberostickets.
Ifyouselectthenfs:NONEcheckbox,theMS-PACrecordwillnotbeaddedtotheserviceticketsissuedagainstNFSservers.
NOTEWindowsIntegrationGuide74NOTEYoucanignorethePADcheckbox.
ThisfunctionalityisnotyetavailableinIdM.
5.
ClicktheUpdatelinkatthetopofthepagetosavethechanges.
5.
3.
5.
2.
SettingPACTypesforaServiceTheglobalpolicysetswhatPACtypestouseforaserviceifnothingissetexplicitlyforthatservice.
However,theglobalsettingscanbeoverriddenonthelocalserviceconfiguration.
TochangethePACsettingfromthecommandline,usetheipaservice-modcommandwiththe--pac-typeoption.
Forinformationonhowtousethecommand,runitwiththe--helpoptionadded:$ipaservice-mod--helpUsage:ipa[global-options]service-modPRINCIPAL[options]ModifyanexistingIPAservice.
Options:-h,--helpshowthishelpmessageandexit.
.
.
TochangethePACsettinginthewebUI:1.
OpentheIdentitytab,andselecttheServicessubtab.
2.
Clickthenameoftheservicetoedit.
3.
IntheServiceSettingsarea,checktheOverrideinheritedsettingsoptionandthenselecttheMS-PACcheckboxtoaddacertificatethatcanbeusedbyADservices.
Figure5.
8.
TheServiceSettingsAreaIfnocheckboxisselected,thennoPACsareaddedtoKerberostickets.
NOTECHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT75NOTEYoucanignorethePADcheckbox.
ThisfunctionalityisnotyetavailableinIdM.
4.
ClicktheUpdatelinkatthetopofthepagetosavethechanges.
5.
3.
6.
UsingPOSIXAttributesDefinedinActiveDirectory5.
3.
6.
1.
DefiningUIDandGIDAttributesforActiveDirectoryUsersIftheWindowsadministratormanuallydefinesPOSIXUIDandGIDattributesforauser,createamatchinggroupontheIdMserverwiththesameGIDfortheuser.
Creatingthegroupensuresthattheuserisassociatedwithaprimaryusergroup.
Ifsuchgroupdoesnotexist,theIdMserverisunabletolookupallgroupstowhichtheuserbelongs.
5.
3.
6.
2.
TransferringLoginShellandHomeDirectoryAttributesIMPORTANTTheclientmustbeenrolledwithanIdMserverbasedonRedHatEnterpriseLinux7.
1orlatertobenefitfromthisfunctionality.
SSSDisabletoreadthefollowingattributevaluesfromanActiveDirectoryserverinatrustrelationshipwithIdM:theloginShellattribute,whichspecifiestheADuser'sshelltheunixHomeDirectoryattribute,whichspecifiestheADuser'shomedirectoryWhenacustomshellorhomedirectoryvalueisdefinedontheADserverusingtheseattributes,thecustomvalueisthendisplayedtotheIdMclientfortheADuser.
Therefore,thesameusershellisdisplayedfortheADuserbothontheADsideandontheIdMside.
NotethattodisplaytheADuser'shomedirectorytotheIdMclient,thesubdomain_homediroptioninthe[domain]sectionofthe/etc/sssd/sssd.
conffileontheIdMservermustbesetto%o.
The%ovaluerepresentsthehomedirectoryretrievedfromtheidentityprovider.
Forexample:[domain/example.
com]subdomain_homedir=%oIftheADadministratormodifiesloginShellorunixHomeDirectoryontheADside,thechangeisautomaticallyreflectedontheIdMsideaswell.
IftheattributesarenotdefinedontheADserver,SSSDusesatemplatedefaultvalue.
ThisdefaultvalueisthendisplayedtotheIdMclient.
5.
3.
7.
UsingSSHfromActiveDirectoryMachinesforIdMResourcesWhenatrustisconfigured,ActiveDirectoryuserscanaccessmachines,services,andfilesonIdMhostsusingSSHandtheirADcredentials.
5.
3.
7.
1.
CachingConsiderationsIdMclientsdonotconnecttoActiveDirectorydomaincontrollers(DC)directlytoretrieveuserWindowsIntegrationGuide76attributes.
Instead,aclientconnectstoanIdMserverwhocachesthisinformation.
Forthisreason,ifyoudisableauserinActiveDirectory,theusercanstillauthenticatetoIdMclientsusingSSHkeyauthenticationuntiltherecordoftheuserexpiresintheIdMdatabase.
IdMupdatesarecordofauserinthefollowingsituations:Theentryhasexpiredautomatically.
Youmanuallyexpiretheentryoftheuserinthecacheusingthesss_cacheutility:#sss_cache--useruser_nameTheuserauthenticatestoanIdMserverusingthekinitutilityorthewebUI.
5.
3.
7.
2.
UsingSSHWithoutPasswordsThelocalauthKerberosplug-inforlocalauthorizationensuresthatKerberosprincipalsareautomaticallymappedtolocalSSSDusernames.
Withlocalauth,WindowsusersfromatrustedADdomainarenotpromptedforapasswordwhenlogginginusingKerberosandcanthereforeuseSSHwithoutpasswords.
Theplug-inprovidesareliablemappingmechanismacrossmultiplerealmsandtrusts:whensssdconnectstotheKerberoslibrarytomaptheprincipaltoalocalPOSIXidentity,theSSSDplug-inmapsthemaccordingtothetrustagreementsdefinedinIdM.
Incertainsituations,usersuseanSSHbastionhosttoaccessotherRedHatEnterpriseLinuxmachines.
Bydefault,ifyouuseKerberostoauthenticatetoSSHonthebastionhost,theKerberosticketcannotbeforwardedtoauthenticateusingKerberostootherRedHatEnterpriseLinuxhosts.
Toenablesuchforwardauthentication,addtheOK_AS_DELEGATEKerberosflagtothebastionshostprincipal:#ipahost-modbastion_host.
idm.
example.
com--ok-as-delegate=trueKerberosAuthenticationforADUsersonRedHatEnterpriseLinux7.
1andnewerSystemsInRedHatEnterpriseLinux7.
1andnewersystems,SSSDautomaticallyconfiguresthelocalauthKerberosplug-in.
SSSDallowsusernamesintheformatuser@AD.
DOMAIN,ad.
domain\userandAD\user.
NOTEOnsystemswithlocalauth,itisnotrequiredtosettheauth_to_localoptioninthe/etc/krb5.
conffileorlistKerberosprincipalsinthe.
k5loginfile.
Thelocalauthplug-inmakesthispreviouslyusedconfigurationforloginswithoutpasswordsobsolete.
ManualConfigurationofKerberosAuthenticationforADUsersOnsystemswherethelocalauthplug-inisnotpresent,SSHpromptsforauserpasswordforActiveDirectorydomainuserseveniftheuserobtainsaproperKerberosticket.
ToenableActiveDirectoryuserstouseKerberosforauthenticationinthissituation,configuretheauth_to_localoptioninthe/etc/krb5.
conffileorlisttheuserKerberosprincipalsinthe.
k5loginfileinthehomedirectoryoftheuser.
Configuring/etc/krb5.
confThefollowingproceduredescribeshowtoconfigurerealmmappingintheKerberosconfiguration.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT771.
Openthe/etc/krb5.
conffile.
2.
Inthe[realms]section,identifytheIdMrealmbyname,andthenaddtwoauth_to_locallinestodefinetheKerberosprincipalnamemapping:Inonerule,includearuletomapdifferentActiveDirectoryusernameformatsandthespecificActiveDirectorydomain.
Intheotherrule,setthevalueofDEFAULT,forstandardUnixusernames.
Forexample:[realms]IDM={.
.
.
.
auth_to_local=RULE:[1:$1@$0](^.
*@ADDOMAIN$)s/@ADDOMAIN/@addomain/auth_to_local=DEFAULT}3.
RestarttheKDCservice.
[root@server~]#systemctlrestartkrb5kdc.
serviceNotethatifyouconfigureKerberosauthenticationusingtheauth_to_localoption,theusernameusedforSSHaccessmustmeetthefollowingcriteria:Theusernamemusthavetheformatad_user@ad_domain.
Thedomainnamemustbelowercase.
ThecaseoftheusernamemustmatchthecaseoftheusernameinActiveDirectory.
Forexample,userandUserareconsidereddifferentusersbecauseofthedifferentcases.
Formoreinformationaboutsettingauth_to_local,seethekrb5.
conf(5)manpage.
Configuring.
k5loginThefollowingprocedureconfiguresthesystemtofindtheKerberosprincipalnameforalocalusername.
1.
Createthe.
k5loginfileintheuser'shomedirectory.
2.
ListtheKerberosprincipalsusedbytheuserinthefile.
IftheauthenticatingusermatchestheprincipalinanexistingKerberosticket,theuserisallowedtologinusingtheticketandisnotpromptedforapassword.
NotethatifyouconfigureKerberosauthenticationusingthe.
k5loginconfiguration,theusernameusedforSSHaccessmusthavetheformatad_user@ad_domain.
Formoreinformationaboutconfiguringthe.
k5loginfile,seethe.
k5login(5)manpage.
EitheroneoftheseconfigurationproceduresresultsinADusersbeingabletologinusingKerberos.
5.
3.
8.
UsingaTrustwithKerberos-enabledWebApplicationsWindowsIntegrationGuide78AnyexistingwebapplicationcanbeconfiguredtouseKerberosauthentication,whichreferencesthetrustedActiveDirectoryandIdMKerberosrealms.
ForthefullKerberosconfigurationdirectives,seetheConfigurationpageforthemod_auth_kerbmodule.
NOTEAfterchangingtheApacheapplicationconfiguration,restarttheApacheservice:[root@ipaserver~]#systemctlrestarthttpd.
serviceForexample,foranApacheserver,thereareseveraloptionsthatdefinehowtheApacheserverconnectstotheIdMKerberosrealm:KrbAuthRealmsTheKrbAuthRealmsoptiongivestheapplicationlocationtothenameoftheIdMdomain.
Thisisrequired.
Krb5KeytabTheKrb5KeytaboptiongivesthelocationfortheIdMserverkeytab.
Thisisrequired.
KrbServiceNameTheKrbServiceNameoptionsetstheKerberosservicenameusedforthekeytab(HTTP).
Thisisrecommended.
KrbMethodK5PasswdandKrbMethodNegotiateTheKrbMethodK5PasswdKerberosmethodoptionenablespassword-basedauthenticationforvalidusers.
TheKrbMethodNegotiateoptionenablessinglesign-on(SSO)ifavalidKerberosticketisavailable.
Theseoptionsarerecommendedforeaseofuseformanyusers.
KrbLocalUserMappingTheKrbLocalUserMappingoptionenablesnormalweblogins(whichareusuallytheUIDorcommonnameoftheaccount)tobemappedtothefully-qualifiedusername(whichhasaformatofuser@REALM.
COM).
Thisoptionisstronglyrecommended.
Withoutthedomainname/loginnamemapping,thewebloginappearstobeadifferentuseraccountthanthedomainuser.
Thismeansthatuserscannotseetheirexpecteddata.
Forinformationonsupportedusernameformats,seeSection5.
2.
1.
9,"SupportedUserNameFormats".
Example5.
1.
KerberosConfigurationinanApacheWebApplicationAuthTypeKerberosAuthName"IPAKerberosauthentication"KrbMethodNegotiateonKrbMethodK5PasswdonCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT795.
3.
9.
ConfiguringanIdMserverasaKerberosDistributionCenterProxyforActiveDirectoryKerberoscommunicationIncertainsituations,networkrestrictionsorfirewallrulespreventIdentityManagement(IdM)clientsfromsendingKerberostraffictoport88onActiveDirectory(AD)domaincontrollers.
ThesolutionistosetupaKerberosproxy,forinstanceonanIdentityManagementserver,torelaytrafficfromIdMclientstoAD.
1.
OnIdMclients,addtheActiveDirectoryrealmtothe[realms]sectionofthe/etc/krb5.
conffile.
Setthekdcandkpasswd_serverparameterstopointtotheIdMserver'sfullyqualifieddomainnamefollowedby/KdcProxy':AD.
EXAMPLE.
COM={kdc=https://server.
idm.
example.
com/KdcProxykpasswd_server=https://server.
idm.
example.
com/KdcProxy}2.
OnIdMclients,disablethecreationof/var/lib/sss/pubconf/kdcinfo.
*fileswhichcouldoverridethe/etc/krb5.
confspecificationsfromthepreviousstep.
Editthe/etc/sssd/sssd.
conffile,settingthekrb5_use_kdcinfotoFalse:[domain/example.
com]krb5_use_kdcinfo=False3.
OnIdMservers,settheuse_dnsoptiontotrueinthe/etc/ipa/kdcproxy/kdcproxy.
conffiletoutilizeDNSservice(SRV)recordstofindADserverstocommunicatewith:use_dns=trueAlternatively,ifyoudonotwanttouseDNSSRVrecords,addexplicitADserverstothe[realms]sectionofthe/etc/krb5.
conffile:AD.
EXAMPLE.
COM={kdc=ad-server.
ad.
example.
comkpasswd_server=ad-server.
ad.
example.
com}NOTEYoucanperformsteps2and3oftheprocedurebyrunningascript,forexampleanAnsiblescript.
Thisisespeciallyusefulwhenmakingchangesonmultiplesystems.
KrbServiceNameHTTPKrbAuthRealmsIDM_DOMAINKrb5Keytab/etc/httpd/conf/ipa.
keytabKrbLocalUserMappingonKrbSaveCredentialsoffRequirevalid-userWindowsIntegrationGuide804.
OnIdMservers,restartIPAservices:#ipactlrestart5.
Toverifythattheprocedurehasbeensuccessful,runthefollowingonanIdMclient:#rm/var/lib/sss/pubconf/kdcinfo*#kinitad_user@AD.
EXAMPLE.
COMPasswordforad_user@AD.
EXAMPLE.
COM:#klistTicketcache:KEYRING:persistent:0:0Defaultprincipal:ad_user@AD.
EXAMPLE.
COMValidstartingExpiresServiceprincipal[.
.
.
outputtruncated.
.
.
]5.
4.
CHANGINGTHELDAPSEARCHBASEFORUSERSANDGROUPSINATRUSTEDACTIVEDIRECTORYDOMAINAsanadministrator,youcansetadifferentsearchbaseforusersandgroupsinthetrustedActiveDirectorydomain.
Forexample,thisenablesyoutofilteroutusersfrominactiveorganizationalunitssothatonlyactiveActiveDirectoryusersandgroupsarevisibletotheSSSDclientsystem.
5.
4.
1.
PrerequisitesToensurethatSSSDdoesnotresolveallgroupstheusersbelongsto,considerdisablingthesupportforthetokenGroupsattributeontheActiveDirectoryside.
WithtokenGroupsenabled,SSSDresolvesallgroupstheuserbelongstobecausetheattributecontainsaflatlistofSIDs.
SeeToken-GroupsattributeonMicrosoftDeveloperNetworkfordetailsabouttheattribute.
5.
4.
2.
ConfiguringtheLDAPSearchBasetoRestrictSearchesThisproceduredescribesrestrictingsearchesinSSSDtoaspecificsubtreebyeditingthe/etc/sssd/sssd.
conffile.
ConsiderationsIfyourSSSDclientsaredirectlyjoinedtoanActiveDirectorydomain,performthisprocedureonalltheclients.
IfyourSSSDclientsareinanIdentityManagementdomainthatisinatrustwithActiveDirectory,performthisprocedureonlyontheIdentityManagementserver.
Procedure1.
Makesurethetrusteddomainhasaseparate[domain]sectioninsssd.
conf.
Theheadingsoftrusteddomainsectionsfollowthistemplate:[domain/main_domain/trusted_domain]Forexample:CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT81[domain/idm.
example.
com/ad.
example.
com]2.
Editthesssd.
conffiletorestrictthesearchbasetoaspecificorganizationalunit(OU).
Forexample,theldap_search_baseoptionchangesthesearchbaseforalltypesofobjects.
[domain/idm.
example.
com/ad.
example.
com]ldap_search_base=ou=finance,dc=ad,dc=example,dc=comYoucanalsousetheldap_user_search_base,ldap_group_search_base,ldap_netgroup_search_base,andldap_service_search_baseoptions.
Formoredetailsontheseoptions,seethesssd-ldap(5)manpage.
3.
RestartSSSD.
#systemctlrestartsssd.
service4.
Toverify,resolveafewActiveDirectoryusersontheSSSDclient.
Forexample,totestachangetotheusersearchbaseandgroupsearchbase:#getentpasswdad_user@ad.
example.
com#getentgroupad_group@ad.
example.
comIfSSSDisconfiguredcorrectly,youareabletoresolveonlyobjectsfromtheconfiguredsearchbase.
Ifyouareabletoresolveusersfromothersearchdomains,troubleshoottheproblembyinspectingtheSSSDlogs:1.
ExpiretheSSSDcaches.
#sss_cache--everything2.
Inthegeneral[domain]sectionofsssd.
conf,setthedebug_leveloptionto9.
3.
Repeatthecommandforresolvingauser.
4.
IntheSSSDlogsat/var/log/sssd/,lookformessagesfromthesdap_get_generic_*functions.
Thefunctionslogthefilterandsearchbaseusedinusersearches.
AdditionalResourcesForalistofoptionsyoucanuseintrusteddomainsectionsofsssd.
conf,seeTRUSTEDDOMAINSECTIONinthesssd.
conf(5)manpage.
5.
5.
CHANGINGTHEFORMATOFUSERNAMESDISPLAYEDBYSSSDBydefault,SSSDusestheuser_name@domain_nameformatwhendisplayingusernames.
Beforeyouchangetheformat,seeSection5.
2.
1.
9,"SupportedUserNameFormats"tolearnaboutthereasonofthisdefaultvalue.
ToconfigurethatSSSDdisplaysonlytheusernamewithoutdomain:1.
Addthefollowingentrytothedomain'ssectioninthe/etc/sssd/sssd.
conffile:WindowsIntegrationGuide82full_name_format=%1$s2.
RestartSSSD:#systemctlrestartsssd5.
6.
RESTRICTINGIDENTITYMANAGEMENTORSSSDTOSELECTEDACTIVEDIRECTORYSERVERSORSITESINATRUSTEDACTIVEDIRECTORYDOMAINAsanadministrator,youcandisableautodiscoveryofActiveDirectoryserversandsitesinthetrustedActiveDirectorydomainandinsteadlistservers,sites,orbothmanually,sothatyoucanlimitthelistofActiveDirectoryserversthatSSSDcommunicateswith.
Forexample,thisenablesyoutoavoidcontactingsitesthatarenotaccessible.
5.
6.
1.
ConfiguringSSSDtoContactaSpecificActiveDirectoryServerThisproceduredescribesmanuallysettingActiveDirectoryserversthatSSSDconnectstobyeditingthe/etc/sssd/sssd.
conffile.
ConsiderationsIfyourSSSDclientsaredirectlyjoinedtoanActiveDirectorydomain,performthisprocedureonalltheclients.
Inthissetup,restrictingtheActiveDirectorydomaincontrollers(DCs)orsitesalsoconfigurestheSSSDclientstoconnecttoaparticularserverorsiteforauthentication.
IfyourSSSDclientsareinanIdentityManagementdomainthatisinatrustwithActiveDirectory,performthisprocedureonlyontheIdentityManagementserver.
Inthissetup,restrictingtheActiveDirectoryDCsorsitesdoesnotconfiguretheIdentityManagementclientstoconnecttoaparticularserverorsiteforauthentication.
AlthoughtrustedActiveDirectoryusersandgroupsareresolvedthroughIdentityManagementservers,authenticationisperformeddirectlyagainsttheActiveDirectoryDCs.
StartingwithRedHatEnterpriseLinux7.
6andsssd-1.
16.
2-5.
el7,youcanconfigureSSSDonIdMclientstouseaspecificADserverorsiteusingthead_serverandad_siteoptions.
InpriorversionsofRedHatEnterpriseLinux7,restrictauthenticationbydefiningtherequiredActiveDirectoryDCsinthe/etc/krb5.
conffileontheclients.
Procedure1.
Makesurethetrusteddomainhasaseparate[domain]sectioninsssd.
conf.
Theheadingsoftrusteddomainsectionsfollowthistemplate:[domain/main_domain/trusted_domain]Forexample:[domain/idm.
example.
com/ad.
example.
com]2.
Editthesssd.
conffiletolistthehostnamesoftheActiveDirectoryserversorsitestowhichyouwantSSSDtoconnect.
Usethead_serverand,optionally,ad_server_backupoptionsforActiveDirectoryservers.
UseCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT83Usethead_serverand,optionally,ad_server_backupoptionsforActiveDirectoryservers.
Usethead_siteoptionforActiveDirectorysites.
Formoredetailsontheseoptions,seethesssd-ad(5)manpage.
Forexample:[domain/idm.
example.
com/ad.
example.
com]ad_server=dc1.
ad.
example.
com3.
RestartSSSD.
#systemctlrestartsssd.
service4.
Toverify,ontheSSSDclient,resolveorauthenticateasanActiveDirectoryuserfromtheconfiguredserverorsite.
Forexample:#idad_user@ad.
example.
comIfyouareunabletoresolvetheuserorauthenticate,usethesestepstotroubleshoottheproblem:1.
Inthegeneral[domain]sectionofsssd.
conf,setthedebug_leveloptionto9.
2.
InspecttheSSSDlogsat/var/log/sssd/toseewhichserversSSSDcontacted.
AdditionalResourcesForalistofoptionsyoucanuseintrusteddomainsectionsofsssd.
conf,seeTRUSTEDDOMAINSECTIONinthesssd.
conf(5)manpage.
5.
7.
ACTIVEDIRECTORYTRUSTFORLEGACYLINUXCLIENTSLinuxclientsrunningRedHatEnterpriseLinuxwithSSSDversion1.
8orearlier(legacyclients)donotprovidenativesupportforIdMcross-foresttrustswithActiveDirectory.
Therefore,forADuserstobeabletoaccessservicesprovidedbytheIdMserver,thelegacyLinuxclientsandtheIdMserverhavetobeproperlyconfigured.
InsteadofusingSSSDversion1.
9orlatertocommunicatewiththeIdMservertoobtainLDAPinformation,legacyclientsuseotherutilitiesforthispurpose,forexamplenss_ldap,nss-pam-ldapd,orSSSDversion1.
8orearlier.
ClientsrunningthefollowingversionsofRedHatEnterpriseLinuxdonotuseSSSD1.
9andarethereforeconsideredtobelegacyclients:RedHatEnterpriseLinux5.
7orlaterRedHatEnterpriseLinux6.
0–6.
3IMPORTANTDonotusetheconfigurationdescribedinthissectionfornon-legacyclients,thatis,clientsrunningSSSDversion1.
9orlater.
SSSD1.
9orlaterprovidesnativesupportforIdMcross-foresttrustswithAD,meaningADuserscanproperlyaccessservicesonIdMclientswithoutanyadditionalconfiguration.
WhenalegacyclientjoinsthedomainofanIdMserverinatrustrelationshipwithAD,acompatLDAPWindowsIntegrationGuide84WhenalegacyclientjoinsthedomainofanIdMserverinatrustrelationshipwithAD,acompatLDAPtreeprovidestherequireduserandgroupdatatoADusers.
However,thecompattreeenablestheADuserstoaccessonlyalimitednumberofIdMservices.
Legacyclientsdonotprovideaccesstothefollowingservices:Kerberosauthenticationhost-basedaccesscontrol(HBAC)SELinuxusermappingsudorulesAccesstothefollowingservicesisprovidedevenincaseoflegacyclients:informationlook-uppasswordauthentication5.
7.
1.
Server-sideConfigurationforADTrustforLegacyClientsMakesuretheIdMservermeetsthefollowingconfigurationrequirements:Theipa-serverpackageforIdMandtheipa-server-trust-adpackagefortheIdMtrustadd-onhavebeeninstalled.
Theipa-server-installutilityhasbeenruntosetuptheIdMserver.
Theipa-adtrust-install--enable-compatcommandhasbeenrun,whichensuresthattheIdMserversupportstrustswithADdomainsandthatthecompatLDAPtreeisavailable.
Ifyouhavealreadyrunipa-adtrust-installwithoutthe--enable-compatoptioninthepast,runitagain,thistimeadding--enable-compat.
Theipatrust-addad.
example.
orgcommandhasbeenruntoestablishtheADtrust.
Ifthehost-basedaccesscontrol(HBAC)allow_allruleisdisabled,enablethesystem-authserviceontheIdMserver,whichallowsauthenticationoftheADusers.
Youcandeterminethecurrentstatusofallow_alldirectlyfromthecommandlineusingtheipahbacrule-showcommand.
Iftheruleisdisabled,Enabled:FALSEisdisplayedintheoutput:[user@server~]$kinitadmin[user@server~]$ipahbacrule-showallow_allRulename:allow_allUsercategory:allHostcategory:allServicecategory:allDescription:AllowalluserstoaccessanyhostfromanyhostEnabled:FALSENOTEForinformationondisablingandenablingHBACrules,seeConfiguringHost-BasedAccessControlintheLinuxDomainIdentity,Authentication,andPolicyGuide.
CHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT85Toenablesystem-authontheIdMserver,createanHBACservicenamedsystem-authandaddanHBACruleusingthisservicetograntaccesstoIdMmasters.
AddingHBACservicesandrulesisdescribedintheLinuxDomainIdentity,Authentication,andPolicyGuide.
NotethatHBACservicesarePAMservicenames;ifyouaddanewPAMservice,makesuretocreateanHBACservicewiththesamenameandthengrantaccesstothisservicethroughHBACrules.
5.
7.
2.
Client-sideConfigurationUsingtheipa-adviseUtilityTheipa-adviseutilityprovidestheconfigurationinstructionstosetupalegacyclientforanADtrust.
Todisplaythecompletelistofscenariosforwhichipa-advisecanprovideconfigurationinstructions,runipa-advisewithoutanyoptions.
Runningipa-adviseprintsthenamesofallavailablesetsofconfigurationinstructionsalongwiththedescriptionsofwhateachsetdoesandwhenitisrecommendedtobeused.
[root@server~]#ipa-adviseconfig-redhat-nss-ldap:Instructionsforconfiguringasystemwithnss-ldapasaIPAclient.
Thissetofinstructionsistargetedforplatformsthatincludetheauthconfigutility,whichareallRedHatbasedplatforms.
config-redhat-nss-pam-ldapd:Instructionsforconfiguringasystem(.
.
.
)Todisplayasetofinstructions,runtheipa-adviseutilitywithaninstructionsetasaparameter:[root@server~]#ipa-adviseconfig-redhat-nss-ldap#!
/bin/sh#Instructionsforconfiguringasystemwithnss-ldapasaIPAclient.
#Thissetofinstructionsistargetedforplatformsthatincludethe#authconfigutility,whichareallRedHatbasedplatforms.
#SchemaCompatibilitypluginhasnotbeenconfiguredonthisserver.
To#configureit,run"ipa-adtrust-install--enable-compat"#Installrequiredpackagesviayumyuminstall-ywgetopensslnss_ldapauthconfig#NOTE:IPAcertificateusestheSHA-256hashfunction.
SHA-256was#introducedinRHEL5.
2.
Therefore,clientsolderthanRHEL5.
2willnot#beabletointeroperatewithIPAserver3.
x.
#Pleasenotethatthisscriptassumes/etc/openldap/cacertsasthe#defaultCAcertificatelocation.
Ifthisvalueisdifferentonyour#systemthescriptneedstobemodifiedaccordingly.
#DownloadtheCAcertificateoftheIPAservermkdir-p-m755/etc/openldap/cacertswgethttp://idm.
example.
com/ipa/config/ca.
crt-O/etc/openldap/cacerts/ca.
crt(.
.
.
)YoucanconfigureaLinuxclientusingtheipa-adviseutilitybyrunningthedisplayedinstructionsasashellscriptorbyexecutingtheinstructionsmanually.
Toruntheinstructionsasashellscript:WindowsIntegrationGuide861.
Createthescriptfile.
[root@server~]#ipa-adviseconfig-redhat-nss-ldap>setup_script.
sh2.
Addexecutepermissionstothefileusingthechmodutility.
[root@server~]#chmod+xsetup_script.
sh3.
Copythescripttotheclientusingthescputility.
[root@server~]#scpsetup_script.
shroot@client4.
Runthescriptontheclient.
[root@client~]#.
/setup_script.
shIMPORTANTAlwaysreadandreviewthescriptfilecarefullybeforeyourunitontheclient.
Toconfiguretheclientmanually,followandexecutetheinstructionsdisplayedbyipa-advisefromthecommandline.
5.
8.
TROUBLESHOOTINGCROSS-FORESTTRUSTSThissectionprovidesinformationaboutpossibleproblemsinancross-foresttrustenvironmentandwaystosolvethem.
5.
8.
1.
Troubleshootingtheipa-extdomPlug-inIdMclientsinanIdMdomainwithatrusttoActiveDirectory(AD)cannotreceiveinformationaboutusersandgroupsfromADdirectly.
Additionally,IdMdoesnotstoreinformationaboutADusersinDirectoryServerrunningonIdMmasters.
Instead,IdMserversusetheipa-extdomtoreceiveinformationaboutADusersandgroupsandforwardsthemtotherequestingclient.
SettingtheConfigTimeoutoftheipa-extdomPlug-inTheipa-extdomplug-insendsarequesttoSSSDforthedataaboutADusers.
However,notallrequesteddatamightbealreadyinthecacheofSSSD.
Inthiscase,SSSDrequeststhedatafromtheADdomaincontroller(DC).
Thiscanbetime-consumingforcertainoperations.
Theconfigtimeoutvaluedefinesthetimeinmillisecondsofhowlongtheipa-extdomplug-inwaitsforareplyofSSSDbeforetheplug-incancelstheconnectionandreturnsatimeouterrortothecaller.
Bydefault,theconfigtimeoutis10000milliseconds(10seconds).
Ifyousetatoosmallvalue,suchas500milliseconds,SSSDmightnothaveenoughtimetoreplyandrequestswillalwaysreturnatimeout.
Ifthevalueistoolarge,suchas30000milliseconds(30seconds),asinglerequestmightblocktheconnectiontoSSSDforthisamountoftime.
SinceonlyonethreadcanconnecttoSSSDatatime,allotherrequestsfromtheplug-inhavetowait.
IftherearemanyrequestssentbyIdMclients,theycanblockallavailableworkersconfiguredforCHAPTER5.
CREATINGCROSS-FORESTTRUSTSWITHACTIVEDIRECTORYANDIDENTITYMANAGEMENT87IftherearemanyrequestssentbyIdMclients,theycanblockallavailableworkersconfiguredforDirectoryServerand,asaconsequence,theservermightnotbeabletoreplytoanykindofrequestforsometime.
Ifyousetatoosmallvalue,suchas500milliseconds,SSSDmightnothaveenoughtimetoreplyandrequestswillalwaysreturnatimeout.
Ifthevalueistoolarge,suchas30000milliseconds(30seconds),asinglerequestmightblocktheconnectiontoSSSDforthisamountoftime.
SinceonlyonethreadcanconnecttoSSSDatatime,allotherrequestsfromtheplug-inhavetowait.
IftherearemanyrequestssendbyIdMclients,theycanblockallavailableworkersconfiguredforDirectoryServerand,asaconsequence,theservermightnotbeabletoreplytoanykindofrequestforsometime.
Changetheconfigtimeoutinthefollowingsituations:IfIdMclientsfrequentlyreceivetimeouterrorsbeforetheirownsearchtimeoutisreachedwhenrequestinginformationaboutADusersandgroups,theconfigtimeoutvalueistoosmall.
IftheDirectoryServerontheIdMserverisoftenlockedandthepstackutilityreportsthatmanyorallworkerthreadsarehandlingipa-extdomrequestsatthistime,thevalueistoolarge.
Forexample,tosettheconfigvalueto20000milliseconds(20seconds),enter:#ldapmodify-D"cn=directorymanager"-Wdn:cn=ipa_extdom_extop,cn=plugins,cn=configchangetype:modifyreplace:ipaExtdomMaxNssTimeoutipaExtdomMaxNssTimeout:20000SettingtheMaximumSizeoftheipa-extdomPlug-inBufferUsedforNSSCallsTheipa-extdomplug-inusescallswhichusethesameAPIastypicalnameserviceswitch(NSS)callstorequestdatafromSSSD.
ThosecallsuseabufferwhereSSSDcanstoretherequesteddata.
Ifthebufferistoosmall,SSSDreturnsanERANGEerrorandtheplug-inretriestherequestwithalargerbuffer.
TheipaExtdomMaxNssBufSizeattributeinthecn=ipa_extdom_extop,cn=plugins,cn=configentryofDirectoryServerontheIdMmasterdefinesthemaximumsizeofthebufferinbytes.
Bydefault,thebufferis134217728bytes(128MB).
Onlyincreasethevalueif,forexample,agrouphassomanymembersthatallnamesdonotfitintothebufferandtheIPAclientcannotresolvethegroup.
Forexample,tosetthebufferto268435456bytes(256MB),enter:#ldapmodify-D"cn=directorymanager"-Wdn:cn=ipa_extdom_extop,cn=plugins,cn=configchangetype:modifyreplace:ipaExtdomMaxNssBufSizeipaExtdomMaxNssBufSize:268435456WindowsIntegrationGuide88PARTIII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:SYNCHRONIZATIONPARTIII.
INTEGRATINGALINUXDOMAINWITHANACTIVEDIRECTORYDOMAIN:SYNCHRONIZATION89CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERSThischapterdescribessynchronizationbetweenActiveDirectoryandRedHatEnterpriseLinuxIdentityManagement.
Synchronizationisoneofthetwomethodsforindirectintegrationofthetwoenvironments.
Fordetailsonthecross-foresttrust,whichistheother,recommendedmethod,seeChapter5,CreatingCross-forestTrustswithActiveDirectoryandIdentityManagement.
Ifyouareunsurewhichmethodtochooseforyourenvironment,readSection1.
3,"IndirectIntegration".
IdentityManagementusessynchronizationtocombinetheuserdatastoredinanActiveDirectorydomainandtheuserdatastoredintheIdMdomain.
Criticaluserattributes,includingpasswords,arecopiedandsynchronizedbetweentheservices.
Entrysynchronizationisperformedthroughaprocesssimilartoreplication,whichuseshookstoconnecttoandretrievedirectorydatafromtheWindowsserver.
PasswordsynchronizationisperformedthroughaWindowsservicewhichisinstalledontheWindowsserverandthencommunicatestotheIdentityManagementserver.
6.
1.
SUPPORTEDWINDOWSPLATFORMSSynchronizationissupportedwithActiveDirectoryforeststhatusethefollowingforestanddomainfunctionallevels:Forestfunctionallevelrange:WindowsServer2008-WindowsServer2012R2Domainfunctionallevelrange:WindowsServer2008-WindowsServer2012R2Thefollowingoperatingsystemsareexplicitlysupportedandtestedforsynchronizationusingthementionedfunctionallevels:WindowsServer2012R2WindowsServer2016PassSync1.
1.
5orlateriscompatiblewithallsupportedWindowsServerversions.
6.
2.
ABOUTACTIVEDIRECTORYANDIDENTITYMANAGEMENTWithintheIdMdomain,informationissharedamongserversandreplicasbycopyingthatinformation,reliablyandpredictably,betweendatamasters(serversandreplicas).
Thisprocessisreplication.
AsimilarprocesscanbeusedtosharedatabetweentheIdMdomainandaMicrosoftActiveDirectorydomain.
Thisissynchronization.
SynchronizationistheprocessofcopyinguserdatabackandforthbetweenActiveDirectoryandIdentityManagement.
WhenusersaresynchronizedbetweenActiveDirectoryandIdentityManagement,thedirectorysynchronization(DirSync)LDAPserverextensioncontrolisusedtosearchadirectoryforobjectsthathavechanged.
WindowsIntegrationGuide90Figure6.
1.
ActiveDirectoryandIdMSynchronizationSynchronizationisdefinedinanagreementbetweenanIdMserverandanActiveDirectorydomaincontroller.
Theagreementdefinesalloftheinformationrequiredtoidentifyuserentriesthatcanbesynchronized,suchasthesubtreetosynchronize,aswellasdefininghowaccountattributesarehandled.
Thesynchronizationagreementsarecreatedwithdefaultvalueswhichcanbetweakedtomeettheneedsofaspecificdomain.
Whentwoserversareinvolvedinsynchronization,theyarecalledpeers.
Table6.
1.
InformationinaSynchronizationAgreementWindowsInformationIdMInformationUsersubtree(cn=Users,$SUFFIX)ConnectioninformationActiveDirectoryadministratorusernameandpasswordPasswordSynchronizationServicepasswordCAcertificateUsersubtree(ou=People,$SUFFIX)Synchronizationismostcommonlybidirectional.
InformationissentbackandforthbetweentheIdMandtheWindowsdomaininaprocessthatisverysimilartohowIdMserversandreplicasshareinformationamongthemselves.
Anexceptionarenewuserentries,whichareonlyaddedfromtheWindowsdomaintotheIdMdomain.
Itispossibletoconfiguresynchronizationtoonlysynchronizeoneway.
Thatisunidirectionalsynchronization.
Topreventtheriskofdataconflicts,onlyonedirectoryshouldoriginateorremoveuserentries.
ThisistypicallytheWindowsdirectory,whichistheprimaryidentitystoreintheITenvironment,andthennewaccountsoraccountdeletionsaresynchronizedtotheIdentityManagementpeer.
Eitherdirectorycanmodifyentries.
Synchronization,then,isconfiguredbetweenoneIdentityManagementserverandoneActiveDirectorydomaincontroller.
TheIdentityManagementserverpropagatesthroughouttotheIdMdomain,whilethedomaincontrollerpropagateschangesthroughouttheWindowsdomain.
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS91Figure6.
2.
SynchronizationTopologyTherearesomekeyfeaturestoIdMsynchronization:Asynchronizationoperationrunseveryfiveminutes.
Tomodifythefrequency,setthewinSyncIntervalattributeintheActiveDirectorypeersDN:cn=meTowinserver.
ad.
example.
com,cn=replica,cn=dc\3Didm\,dc\3Dexample\,dc\3Dcom,cn=mappingtree,cn=configSynchronizationcanonlybeconfiguredwithoneActiveDirectorydomain.
SynchronizationcanonlybeconfiguredwithoneActiveDirectorydomaincontroller.
Onlyuserinformationissynchronized;groupinformationisnot.
Bothuserattributesandpasswordscanbesynchronized.
Whilemodificationsarebidirectional(goingbothfromActiveDirectorytoIdMandfromIdMtoActiveDirectory),creatingaccountsisonlyunidirectional,fromActiveDirectorytoIdentityManagement.
NewaccountscreatedinActiveDirectoryaresynchronizedovertoIdMautomatically.
However,useraccountscreatedinIdMmustalsobecreatedinActiveDirectorybeforetheywillbesynchronized.
Inthissituation,thesynchronizationprocesstriestofindamatchingaccountwiththesamevaluefortheuidattributeinIdMthanforthesAMAccountNameattributeinActiveDirectory.
Ifamatchisfound,theIdMntUserDomainIdattributeissettotheActiveDirectoryobjectGUIDvalue.
Theseattributesaregloballyuniqueandimmutable,andentriesstaysynchronized,eveniftheyaremovedorrenamed.
Accountlockinformationissynchronizedbydefault,soauseraccountwhichisdisabledinonedomainisdisabledintheother.
Passwordsynchronizationchangestakeeffectimmediately.
Ifauserpasswordisaddedorchangedononepeer,thatchangeisimmediatelypropagatedtotheotherpeerserver.
ThePasswordSynchronizationclientsynchronizesnewpasswordsorpasswordupdates.
Existingpasswords,whicharestoredinahashedforminbothIdMandActiveDirectory,cannotbedecryptedorsynchronizedwhenthePasswordSynchronizationclientisinstalled,soexistingWindowsIntegrationGuide92passwordsarenotsynchronized.
Userpasswordsmustbechangedtoinitiatesynchronizationbetweenthepeerservers.
Whiletherecanonlybeoneagreement,thePassSyncservicemustbeinstalledoneveryActiveDirectoryserver.
WhenActiveDirectoryusersaresynchronizedovertoIdM,certainattributes(includingKerberosandPOSIXattributes)willhaveIPAattributesautomaticallyaddedtotheuserentries.
TheseattributesareusedbyIdMwithinitsdomain.
TheyarenotsynchronizedbackoverthecorrespondingActiveDirectoryuserentry.
Someofthedatainsynchronizationcanbemodifiedaspartofthesynchronizationprocess.
Forexamples,certainattributescanbeautomaticallyaddedtoActiveDirectoryuseraccountswhentheyaresyncedovertotheIdMdomain.
TheseattributechangesaredefinedaspartofthesynchronizationagreementandaredescribedinSection6.
5.
2,"ChangingtheBehaviorforSynchronizingUserAccountAttributes".
6.
3.
ABOUTSYNCHRONIZEDATTRIBUTESIdentityManagementsynchronizesasubsetofuserattributesbetweenIdMandActiveDirectoryuserentries.
Anyotherattributespresentintheentry,eitherinIdentityManagementorinActiveDirectory,areignoredbysynchronization.
NOTEMostPOSIXattributesarenotsynchronized.
AlthoughtherearesignificantschemadifferencesbetweentheActiveDirectoryLDAPschemaandthe389DirectoryServerLDAPschemausedbyIdentityManagement,therearemanyattributesthatarethesame.
TheseattributesaresimplysynchronizedbetweentheActiveDirectoryandIdMuserentries,withnochangestotheattributenameorvalueformat.
UserSchemaThatAretheSameinIdentityManagementandWindowsServerscn[2]physicalDeliveryOfficeNamedescriptionpostOfficeBoxdestinationIndicatorpostalAddressfacsimileTelephoneNumberpostalCodegivennameregisteredAddresshomePhoneCHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS93snhomePostalAddressstinitialsstreetltelephoneNumbermailteletexTerminalIdentifiermobiletelexNumberotitleouuserCertificatepagerx121AddressSomeattributeshavedifferentnamesbutstillhavedirectparitybetweenIdM(whichuses389DirectoryServer)andActiveDirectory.
Theseattributesaremappedbythesynchronizationprocess.
Table6.
2.
UserSchemaMappedbetweenIdentityManagementandActiveDirectoryIdentityManagementActiveDirectorycn[a]namensAccountLockuserAccountControlntUserDomainIdsAMAccountNamentUserHomeDirhomeDirectoryntUserScriptPathscriptPathntUserLastLogonlastLogonWindowsIntegrationGuide94ntUserLastLogofflastLogoffntUserAcctExpiresaccountExpiresntUserCodePagecodePagentUserLogonHourslogonHoursntUserMaxStoragemaxStoragentUserProfileprofilePathntUserParmsuserParametersntUserWorkstationsuserWorkstations[a]Thecnismappeddirectly(cntocn)whensynchronizingfromIdentityManagementtoActiveDirectory.
WhensynchronizingfromActiveDirectorycnismappedfromthenameattributeinActiveDirectorytothecnattributeinIdentityManagement.
IdentityManagementActiveDirectory6.
3.
1.
UserSchemaDifferencesbetweenIdentityManagementandActiveDirectoryEventhoughattributesmaybesuccessfullysynchronizedbetweenActiveDirectoryandIdM,theremaystillbedifferencesinhowActiveDirectoryandIdentityManagementdefinetheunderlyingX.
500objectclasses.
ThiscouldleadtodifferencesinhowthedataarehandledinthedifferentLDAPservices.
ThissectiondescribesthedifferencesinhowActiveDirectoryandIdentityManagementhandlesomeoftheattributeswhichcanbesynchronizedbetweenthetwodomains.
6.
3.
1.
1.
ValuesforcnAttributesIn389DirectoryServer,thecnattributecanbemulti-valued,whileinActiveDirectorythisattributemusthaveonlyasinglevalue.
WhentheIdentityManagementcnattributeissynchronized,then,onlyonevalueissenttotheActiveDirectorypeer.
Whatthismeansforsynchronizationisthat,potentially,ifacnvalueisaddedtoanActiveDirectoryentryandthatvalueisnotoneofthevaluesforcninIdentityManagement,thenalloftheIdentityManagementcnvaluesareoverwrittenwiththesingleActiveDirectoryvalue.
OneotherimportantdifferenceisthatActiveDirectoryusesthecnattributeasitsnamingattribute,whereIdentityManagementusesuid.
Thismeansthatthereisthepotentialtorenametheentryentirely(andaccidentally)ifthecnattributeiseditedintheIdentityManagement.
6.
3.
1.
2.
ValuesforstreetandstreetAddressActiveDirectoryusestheattributestreetAddressforauser'spostaladdress;thisisthewaythat389DirectoryServerusesthestreetattribute.
TherearetwoimportantdifferencesinthewaythatActiveDirectoryandIdentityManagementusethestreetAddressandstreetattributes,respectively:CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS95In389DirectoryServer,streetAddressisanaliasforstreet.
ActiveDirectoryalsohasthestreetattribute,butitisaseparateattributethatcanholdanindependentvalue,notanaliasforstreetAddress.
ActiveDirectorydefinesbothstreetAddressandstreetassingle-valuedattributes,while389DirectoryServerdefinesstreetasamulti-valuedattribute,asspecifiedinRFC4519.
Becauseofthedifferentwaysthat389DirectoryServerandActiveDirectoryhandlestreetAddressandstreetattributes,therearetworulestofollowwhensettingaddressattributesinActiveDirectoryandIdentityManagement:ThesynchronizationprocessmapsstreetAddressintheActiveDirectoryentrytostreetinIdentityManagement.
Toavoidconflicts,thestreetattributeshouldnotbeusedinActiveDirectory.
OnlyoneIdentityManagementstreetattributevalueissynchronizedtoActiveDirectory.
IfthestreetAddressattributeischangedinActiveDirectoryandthenewvaluedoesnotalreadyexistinIdentityManagement,thenallstreetattributevaluesinIdentityManagementarereplacedwiththenew,singleActiveDirectoryvalue.
6.
3.
1.
3.
ConstraintsontheinitialsAttributeFortheinitialsattribute,ActiveDirectoryimposesamaximumlengthconstraintofsixcharacters,but389DirectoryServerdoesnothavealengthlimit.
IfaninitialsattributelongerthansixcharactersisaddedtoIdentityManagement,thevalueistrimmedwhenitissynchronizedwiththeActiveDirectoryentry.
6.
3.
1.
4.
Requiringthesurname(sn)AttributeActiveDirectoryallowspersonentriestobecreatedwithoutasurnameattribute.
However,RFC4519definesthepersonobjectclassasrequiringasurnameattribute,andthisisthedefinitionusedinDirectoryServer.
IfanActiveDirectorypersonentryiscreatedwithoutasurnameattribute,thatentrywillnotbesynchronizedovertoIdMsinceitfailswithanobjectclassviolation.
6.
3.
2.
ActiveDirectoryEntriesandPOSIXAttributesWhenaWindowsuseraccountcontainsvaluesfortheuidNumberandgidNumberattributes,WinSyncdoesnotsynchronizethesevaluesovertoIdentityManagement.
Instead,itcreatesnewUIDandGIDvaluesinIdentityManagement.
Asaresult,thevaluesforuidNumberandgidNumberaredifferentinActiveDirectoryandinIdentityManagement.
6.
4.
SETTINGUPACTIVEDIRECTORYFORSYNCHRONIZATIONSynchronizinguseraccountsisenabledwithinIdM.
Itisonlynecessarytosetupasynchronizationagreement(Section6.
5.
1,"CreatingSynchronizationAgreements").
However,theActiveDirectorydoesneedtobeconfiguredinawaythatallowstheIdentityManagementservertoconnecttoit.
6.
4.
1.
CreatinganActiveDirectoryUserforSynchronizationOntheWindowsserver,itisnecessarytocreatetheuserthattheIdMserverwillusetoconnecttotheActiveDirectorydomain.
WindowsIntegrationGuide96TheprocessforcreatingauserinActiveDirectoryiscoveredintheWindowsserverdocumentationathttp://technet.
microsoft.
com/en-us/library/cc732336.
aspx.
Thenewuseraccountmusthavetheproperpermissions:GrantthesynchronizationuseraccountReplicatingdirectorychangesrightstothesynchronizedActiveDirectorysubtree.
Replicatorrightsarerequiredforthesynchronizationusertoperformsynchronizationoperations.
Replicatorrightsaredescribedinhttp://support.
microsoft.
com/kb/303972.
AddthesynchronizationuserasamemberoftheAccountOperatorsandEnterpriseRead-onlyDomainControllersgroups.
ItisnotnecessaryfortheusertobelongtotheDomainAdminsgroup.
6.
4.
2.
SettingupanActiveDirectoryCertificateAuthorityTheIdentityManagementserverconnectstotheActiveDirectoryserverusingasecureconnection.
ThisrequiresthattheActiveDirectoryserverhaveanavailableCAcertificateorCAcertificatechainavailable,whichcanbeimportedintotheIdentityManagementsecuritydatabases,sothattheWindowsserverisatrustedpeer.
Whilethiscouldtechnicallybedonewithanexternal(toActiveDirectory)CA,mostdeploymentsshouldusetheCertificateServicesavailablewithActiveDirectory.
TheprocedureforsettingupandconfiguringcertificateservicesonActiveDirectoryiscoveredintheMicrosoftdocumentationathttp://technet.
microsoft.
com/en-us/library/cc772393(v=WS.
10).
aspx.
6.
5.
MANAGINGSYNCHRONIZATIONAGREEMENTS6.
5.
1.
CreatingSynchronizationAgreementsSynchronizationagreementsarecreatedontheIdMserverusingtheipa-replica-manageconnectcommandbecauseitcreatesaconnectiontotheActiveDirectorydomain.
ToestablishanencryptedconnectiontoActiveDirectory,IdMmusttotrusttheWindowsCAcertificate.
1.
Copytherootcertificateauthority(CA)certificatetotheIdMserver:a.
IfyourActiveDirectoryCAcertificateisself-signed:i.
ExporttheActiveDirectoryCAcertificateontheWindowsserver.
A.
PresstheSuperkey+RcombinationtoopentheRundialog.
B.
Entercertsrv.
mscandclickOK.
C.
Right-clickonthenameofthelocalCertificateAuthorityandchooseProperties.
D.
OntheGeneraltab,selectthecertificatetoexportintheCAcertificatesfieldandclickViewCertificate.
E.
OntheDetailstab,clickCopytoFiletostarttheCertificateExportWizard.
F.
ClickNext,andthenselectBase-64encodedX.
509(.
CER).
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS97G.
Specifyasuitabledirectoryandfilenamefortheexportedfile.
ClickNexttoexportthecertificate,andthenclickFinish.
H.
CopytheexportedcertificatetotheIdMservermachine.
b.
IfyourActiveDirectoryCAcertificateissignedbyanexternalCA:i.
TofindoutwhatcertificateistheCArootcertificate,displaythecertificatechain:#openssls_client-connectadserver.
example.
com:636CONNECTED(00000003)depth=1C=US,O=DemoCompany,OU=IT,CN=DemoCA-28verifyerror:num=20:unabletogetlocalissuercertificateverifyreturn:0---Certificatechain0s:/C=US/O=DemoCompany/OU=IT/CN=adserver.
example.
comi:/C=US/O=DemoCompany/OU=IT/CN=DemoCA-11s:/C=US/O=DemoCompany/OU=IT/CN=DemoCA-1i:/C=US/O=DemoCompany/OU=IT/CN=DemoRootCA2ThepreviousexampleshowsthattheActiveDirectoryserver'sCAcertificateissignedbyCN=DemoCA-1,whichissignedbyCN=DemoRootCA2.
ThismeansthatCN=DemoRootCA2istherootCA.
ii.
CopytheCAcertificatetotheIdMserver.
WindowsIntegrationGuide982.
RemoveanyexistingKerberoscredentialsontheIdMserver.
$kdestroy3.
Usetheipa-replica-managecommandtocreateaWindowssynchronizationagreement.
Thisrequiresthe--winsyncoption.
Ifpasswordswillbesynchronizedaswellasuseraccounts,thenalsousethe--passsyncoptionandsetapasswordtouseforPasswordSynchronization.
The--binddnand--bindpwoptionsgivetheusernameandpasswordofthesystemaccountontheActiveDirectoryserverthatIdMwillusetoconnecttotheActiveDirectoryserver.
$ipa-replica-manageconnect--winsync\--binddncn=administrator,cn=users,dc=example,dc=com\--bindpwWindows-secret\--passsyncsecretpwd\--cacert/etc/openldap/cacerts/windows.
cer\adserver.
example.
com-v--winsync:IdentifiesthisasaWindowssynchronizationagreement.
--binddn:IdMusesthisDNofanActiveDirectoryaccounttobindtotheremotedirectoryandsynchronizeattributes.
--bindpw:Passwordforthesynchronizationaccount.
--cacert:Fullpathandfilenametothe:ActiveDirectoryCAcertificate,iftheCAwasself-signed.
externalCAcertificate,iftheActiveDirectoryCAwassignedbyanexternalCA.
--win-subtree:DNoftheWindowsdirectorysubtreecontainingtheuserstosynchronize.
Thedefaultvalueiscn=Users,$SUFFIX.
AD_server_name:Fullyqualifieddomainname(FQDN)oftheActiveDirectorydomaincontroller.
4.
Whenprompted,entertheDirectoryManagerpassword.
5.
Optional.
ConfigurePasswordSynchronization,asinSection6.
6.
2,"SettingupPasswordSynchronization".
WithoutthePasswordSynchronizationclient,userattributesaresynchronizedbetweenthepeerservers,butpasswordsarenot.
NOTEThePasswordSynchronizationclientcapturespasswordchangesandthensynchronizesthembetweenActiveDirectoryandIdM.
Thismeansthatitsynchronizesnewpasswordsorpasswordupdates.
Existingpasswords,whicharestoredinahashedforminbothIdMandActiveDirectory,cannotbedecryptedorsynchronizedwhenthePasswordSynchronizationclientisinstalled,soexistingpasswordsarenotsynchronized.
Userpasswordsmustbechangedtoinitiatesynchronizationbetweenthepeerservers.
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS996.
5.
2.
ChangingtheBehaviorforSynchronizingUserAccountAttributesWhenthesynchronizationagreementiscreated,ithascertaindefaultbehaviorsdefinedforhowthesynchronizationprocesshandlestheuseraccountattributesduringsynchronization.
ThetypesofbehaviorsarethingslikehowtohandlelockoutattributesorhowtohandledifferentDNformats.
Thisbehaviorcanbechangedbyeditingthesynchronizationagreement.
Thesynchronizationagreementexistsasaspecialplug-inentryintheLDAPserverandeachattributebehaviorissetthroughanLDAPattribute.
Tochangethesynchronizationbehavior,usetheldapmodifycommandtomodifytheLDAPserverentrydirectly.
Forexample,accountlockoutattributesaresynchronizedbetweenIdMandActiveDirectorybydefault,butthiscanbedisabledbyeditingtheipaWinSyncAcctDisableattribute.
(ChangingthismeansthatifanaccountisdisabledinActiveDirectory,itisstillactiveinIdMandviceversa.
)[jsmith@ipaserver~]$ldapmodify-x-D"cn=directorymanager"-wpassworddn:cn=ipa-winsync,cn=plugins,cn=configchangetype:modifyreplace:ipaWinSyncAcctDisableipaWinSyncAcctDisable:nonemodifyingentry"cn=ipa-winsync,cn=plugins,cn=config"Thefollowingisanoverviewofsynchronizationsettingsattributes:GeneralUserAccountParametersipaWinSyncNewEntryFilter:Setsthesearchfiltertousetofindtheentrywhichcontainsthelistofobjectclassestoaddtonewuserentries.
Defaultvalue:(cn=ipaConfig)ipaWinSyncNewUserOCAttr:Setstheattributeintheconfigurationentrywhichactuallycontainsthelistofobjectclassestoaddtonewuserentries.
Defaultvalue:ipauserobjectclassesipaWinSyncHomeDirAttr:IdentifieswhichattributeintheentrycontainsthedefaultlocationofthePOSIXhomedirectory.
Defaultvalue:ipaHomesRootDiripaWinSyncUserAttr:SetsanadditionalattributewithaspecificvaluetoaddtoActiveDirectoryuserswhentheyaresynchronizedoverfromtheActiveDirectorydomain.
Iftheattributeismulti-valued,thenitcanbesetmultipletimes,andthesynchronizationprocessaddsallofthevaluestotheentry.
Example:ipaWinSyncUserAttr:attributeNameattributeValueNOTEThisonlysetstheattributevalueiftheentrydoesnotalreadyhavethatattributepresent.
Iftheattributeispresent,thentheentry'svalueisusedwhentheActiveDirectoryentryissynchronizedover.
WindowsIntegrationGuide100ipaWinSyncForceSync:SetswhetherexistingIdMusersthatmatchexistingADusersshouldbeforcedtobesynchronized.
Whensettotrue,suchIdMusersareautomaticallyeditedsothattheyaresynchronized.
Possiblevalues:true|falseIfanIdMuseraccounthasauidparameterwhichisidenticaltothesAMAccountNameinanexistingActiveDirectoryuser,thenthataccountisnotsynchronizedbydefault.
ThisattributetellsthesynchronizationservicetoaddthentUserandntUserDomainIdtotheIdMuserentriesautomatically,whichallowsthemtobesynchronized.
UserAccountLockParametersipaWinSyncAcctDisable:Setswhichwaytosynchronizeaccountlockoutattributes.
Itispossibletocontrolwhichaccountlockoutsettingsareineffect.
Forexample,to_admeansthatwhenaccountlockoutattributeissetinIdM,itsvalueissynchronizedovertoActiveDirectoryandoverridesthelocalActiveDirectoryvalue.
Bydefault,accountlockoutattributesaresynchronizedfrombothdomains.
Possiblevalues:both(default),to_ad,to_ds,noneipaWinSyncInactivatedFilter:SetsthesearchfiltertousetofindtheDNofthegroupusedtoholdinactivated(disabled)users.
Thisdoesnotneedtobechangedinmostdeployments.
Defaultvalue:(&(cn=inactivated)(objectclass=groupOfNames))GroupParametersipaWinSyncDefaultGroupAttr:Setstheattributeinthenewuseraccounttoreferencetoseewhatthedefaultgroupfortheuseris.
ThegroupnameintheentryisthenusedtofindthegidNumberfortheuseraccount.
Defaultvalue:ipaDefaultPrimaryGroupipaWinSyncDefaultGroupFilter:Setstheattributeinthenewuseraccounttoreferencetoseewhatthedefaultgroupfortheuseris.
ThegroupnameintheentryisthenusedtofindthegidNumberfortheuseraccount.
Defaultvalue:ipaDefaultPrimaryGroupRealmParametersipaWinSyncRealmAttr:Setstheattributewhichcontainstherealmnameintherealmentry.
Defaultvalue:cnipaWinSyncRealmFilter:SetsthesearchfiltertousetofindtheentrywhichcontainstheIdMrealmname.
Defaultvalue:(objectclass=krbRealmContainer)6.
5.
3.
ChangingtheSynchronizedWindowsSubtreeCreatingasynchronizationagreementautomaticallysetsthetwosubtreestouseasthesynchronizeduserdatabase.
InIdM,thedefaultiscn=users,cn=accounts,$SUFFIX,andforActiveDirectory,thedefaultisCN=Users,$SUFFIX.
ThevaluefortheActiveDirectorysubtreecanbesettoanon-defaultvaluewhenthesynchronizationCHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS101ThevaluefortheActiveDirectorysubtreecanbesettoanon-defaultvaluewhenthesynchronizationagreementiscreatedbyusingthe--win-subtreeoption.
Aftertheagreementiscreated,theActiveDirectorysubtreecanbechangedbyusingtheldapmodifycommandtoeditthensds7WindowsReplicaSubtreevalueinthesynchronizationagreemententry.
1.
Getthenameofthesynchronizationagreement,usingldapsearch.
Thissearchreturnsonlythevaluesforthednandnsds7WindowsReplicaSubtreeattributesinsteadoftheentireentry.
[jsmith@ipaserver~]$ldapsearch-xLLL-D"cn=directorymanager"-wpassword-p389-hipaserver.
example.
com-bcn=configobjectclass=nsdswindowsreplicationagreementdnnsds7WindowsReplicaSubtreedn:cn=meToWindowsBox.
example.
com,cn=replica,cn=dc\3Dexample\2Cdc\3Dcom,cn=mappingtree,cn=confignsds7WindowsReplicaSubtree:cn=users,dc=example,dc=com.
.
.
8dsquery*-scopebase-attrpwdPropertiespwdProperties1IfthevalueoftheattributepwdPropertiesissetto1,thepasswordcomplexitypolicyisenabledforthedomain.
NOTEIfyouareunsureifgrouppoliciesdefinedeviatingpasswordsettingsforOrganizationalUnits(ou),askyourgrouppolicyadministrator.
ToenabletheActiveDirectorypasswordcomplexitysettingforthewholedomain:1.
Rungpmc.
mscfromthecommandline.
2.
SelectGroupPolicyManagement.
3.
OpenForest:ad.
example.
com→Domains→ad.
example.
com.
4.
Right-clicktheDefaultDomainPolicyentryandselectEdit.
CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS1055.
TheGroupPolicyManagementEditoropensautomatically.
6.
OpenComputerConfiguration→Policies→WindowsSettings→SecuritySettings→AccountPolicies→PasswordPolicy.
7.
EnablethePasswordmustmeetcomplexityrequirementsoptionandsave.
6.
6.
2.
SettingupPasswordSynchronizationInstallthePasswordSynchronizationServiceoneverydomaincontrollerintheActiveDirectorydomaininordertosynchronizeWindowspasswords.
1.
DownloadtheRedHat-PassSync-*.
msifiletotheActiveDirectorydomaincontroller:1.
LogintotheCustomerPortal.
2.
ClickDownloadsatthetopofthepage.
3.
SelectRedHatEnterpriseLinuxfromtheproductlist.
4.
SelectthemostrecentversionofRedHatEnterpriseLinux6orRedHatEnterpriseLinux7andarchitecture.
5.
DownloadWinSyncInstallerforthearchitectureoftheActiveDirectorydomaincontrollerbyclickingtheDownloadNowbutton.
2.
Double-clicktheMSIfiletoinstallit.
3.
ThePasswordSynchronrizationSetupwindowappears.
HitNexttobegininstalling.
WindowsIntegrationGuide1064.
FillintheinformationtoestablishtheconnectiontotheIdMserver.
TheIdMserverconnectioninformation,includingthehostnameandsecureportnumber.
TheusernameofthesystemuserwhichActiveDirectoryusestoconnecttotheIdMmachine.
ThisaccountisconfiguredautomaticallywhensynchronizationisconfiguredontheIdMserver.
Thedefaultaccountisuid=passsync,cn=sysaccounts,cn=etc,dc=example,dc=com.
Thepasswordsetinthe--passsyncoptionwhenthesynchronizationagreementwascreated.
ThesearchbaseforthepeoplesubtreeontheIdMserver.
TheActiveDirectoryserverconnectstotheIdMserversimilartoanldapsearchorreplicationoperation,soithastoknowwhereintheIdMsubtreetolookforuseraccounts.
Theusersubtreeiscn=users,cn=accounts,dc=example,dc=com.
Thecertificatetokenisnotusedatthistime,sothatfieldshouldbeleftblank.
HitNext,thenFinishtoinstallPasswordSynchronization.
5.
ImporttheIdMserver'sCAcertificateintothePassSynccertificatestore.
1.
DownloadtheIdMserver'sCAcertificatefromhttp://ipa.
example.
com/ipa/config/ca.
crt.
2.
CopytheIdMCAcertificatetotheActiveDirectoryserver.
3.
InstalltheIdMCAcertificateinthePasswordSynchronizationdatabase.
Forexample:CHAPTER6.
SYNCHRONIZINGACTIVEDIRECTORYANDIDENTITYMANAGEMENTUSERS107cd"C:\ProgramFiles\RedHatDirectoryPasswordSynchronization"certutil.
exe-d.
-A-n"IPASERVER.
EXAMPLE.
COMIPACA"-tCT,,-a-iipaca.
crt6.
ReboottheWindowsmachinetostartPasswordSynchronization.
NOTETheWindowsmachinemustberebooted.
Withouttherebooting,PasswordHook.
dllisnotenabled,andpasswordsynchronizationwillnotfunction.
7.
Ifpasswordsforexistingaccountsshouldbesynchronized,resettheuserpasswords.
NOTEThePasswordSynchronizationclientcapturespasswordchangesandthensynchronizesthembetweenActiveDirectoryandIdM.
Thismeansthatitsynchronizesnewpasswordsorpasswordupdates.
Existingpasswords,whicharestoredinahashedforminbothIdMandActiveDirectory,cannotbedecryptedorsynchronizedwhenthePasswordSynchronizationclientisinstalled,soexistingpasswordsarenotsynchronized.
Userpasswordsmustbechangedtoinitiatesynchronizationbetweenthepeerservers.
Thefirstattempttosynchronizepasswords,whichhappenedwhenthePasswordSynchronizationapplicationisinstalled,willalwaysfailbecauseoftheSSLconnectionbetweentheDirectoryServerandActiveDirectorysynchronizationpeers.
Thetoolstocreatethecertificateandkeydatabasesisinstalledwiththe.
msi.
ThepasswordsynchronizationclientcannotsynchronizepasswordsformembersoftheIdMadmingroup.
Thisisanintendedbehaviortoprevent,forexample,passwordsynchronizationagentsorlowleveluseradministratorstochangepasswordsoftopleveladministrators.
NOTEPasswordsareonlyvalidatedonthesynchronizationsourcetomatchthepasswordpolicies.
ToverifyandenabletheActiveDirectorypasswordcomplexitypolicy,seeSection6.
6.
1,"SettinguptheWindowsServerforPasswordSynchronization".
[2]Thecnistreateddifferentlythanothersynchronizedattributes.
Itismappeddirectly(cntocn)whensynchronizingfromIdentityManagementtoActiveDirectory.
WhensynchronizingfromActiveDirectorytoIdentityManagement,however,cnismappedfromthenameattributeonWindowstothecnattributeinIdentityManagement.
WindowsIntegrationGuide108CHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUSTSynchronizationandtrustaretwopossibleapproachestoindirectintegration.
Synchronizationisgenerallydiscouraged,andRedHatrecommendstousetheapproachbasedonActiveDirectory(AD)trustinstead.
SeeSection1.
3,"IndirectIntegration"fordetails.
Thischapterdescribeshowtomigrateanexistingsynchronization-basedsetuptoADtrust.
ThefollowingmigratingoptionsareavailableinIdM:Section7.
1,"MigratefromSynchronizationtoTrustAutomaticallyUsingipa-winsync-migrate"Section7.
2,"MigratefromSynchronizationtoTrustManuallyUsingIDViews"7.
1.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTAUTOMATICALLYUSINGIPA-WINSYNC-MIGRATEIMPORTANTTheipa-winsync-migrateutilityisonlyavailableonsystemsrunningRedHatEnterpriseLinux7.
2orlater.
7.
1.
1.
HowMigrationUsingipa-winsync-migrateWorksTheipa-winsync-migrateutilitymigratesallsynchronizedusersfromanADforest,whilepreservingtheexistingconfigurationintheWinsyncenvironmentandtransferringitintotheADtrust.
ForeachADusercreatedbytheWinsyncagreement,ipa-winsync-migratecreatesanIDoverrideintheDefaultTrustView(seeSection8.
1,"ActiveDirectoryDefaultTrustView").
Afterthemigrationcompletes:TheIDoverridesfortheADusershavethefollowingattributescopiedfromtheoriginalentryinWinsync:Loginname(uid)UIDnumber(uidnumber)GIDnumber(gidnumber)Homedirectory(homedirectory)GECOSentry(gecos)TheuseraccountsintheADtrustkeeptheiroriginalconfigurationinIdM,whichincludes:POSIXattributesUsergroupsRole-basedaccesscontrolrulesHost-basedaccesscontrolrulesCHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUST109SELinuxmembershipsudorulesThenewADusersareaddedasmembersofanexternalIdMgroup.
TheoriginalWinsyncreplicationagreement,theoriginalsynchronizeduseraccounts,andalllocalcopiesoftheuseraccountsareremoved.
7.
1.
2.
HowtoMigrateUsingipa-winsync-migrateBeforeyoubegin:BackupyourIdMsetupusingtheipa-backuputility.
SeeBackingUpandRestoringIdentityManagementintheLinuxDomainIdentity,Authentication,andPolicyGuide.
Reason:ThemigrationaffectsasignificantpartoftheIdMconfigurationandmanyuseraccounts.
Creatingabackupenablesyoutorestoreyouroriginalsetupifnecessary.
Tomigrate:1.
Createatrustwiththesynchronizeddomain.
SeeChapter5,CreatingCross-forestTrustswithActiveDirectoryandIdentityManagement.
2.
Runipa-winsync-migrateandspecifytheADrealmandthehostnameoftheADdomaincontroller:#ipa-winsync-migrate--realmexample.
com--serverad.
example.
comIfaconflictoccursintheoverridescreatedbyipa-winsync-migrate,informationabouttheconflictisdisplayed,butthemigrationcontinues.
3.
UninstallthePasswordSyncservicefromtheADserver.
ThisremovesthesynchronizationagreementfromtheADdomaincontrollers.
Seetheipa-winsync-migrate(1)manpageformoredetailsabouttheutility.
7.
2.
MIGRATEFROMSYNCHRONIZATIONTOTRUSTMANUALLYUSINGIDVIEWSYoucanuseIDviewstomanuallychangethePOSIXattributesthatADpreviouslygeneratedforADusers.
1.
Createabackupoftheoriginalsynchronizeduserorgroupentries.
2.
Createatrustwiththesynchronizeddomain.
Forinformationaboutcreatingtrusts,seeChapter5,CreatingCross-forestTrustswithActiveDirectoryandIdentityManagement.
3.
Foreverysynchronizeduserorgroup,preservetheUIDandGIDsgeneratedbyIdMbydoingoneofthefollowing:IndividuallycreateanIDviewappliedtothespecifichostandadduserIDoverridestotheview.
CreateuserIDoverridesintheDefaultTrustView.
WindowsIntegrationGuide110Fordetails,seeDefiningaDifferentAttributeValueforaUserAccountonDifferentHosts.
NOTEOnlyIdMuserscanmanageIDviews.
ADuserscannot.
4.
Deletetheoriginalsynchronizeduserorgroupentries.
ForgeneralinformationonusingIDviewsinActiveDirectoryenvironments,seeChapter8,UsingIDViewsinActiveDirectoryEnvironments.
CHAPTER7.
MIGRATINGEXISTINGENVIRONMENTSFROMSYNCHRONIZATIONTOTRUST111CHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTSIDviewsenableyoutospecifynewvaluesforPOSIXuserorgroupattributes,aswellastodefineonwhichclienthostorhoststhenewvalueswillapply.
IntegrationsystemsotherthanIdentityManagement(IdM)sometimesgenerateUIDandGIDvaluesbasedonanalgorithmdifferentthanthealgorithmusedinIdM.
ByoverridingthepreviouslygeneratedvaluestomakethemcompliantwiththevaluesusedinIdM,aclientthatusedtobeamemberofanotherintegrationsystemcanbefullyintegratedwithIdM.
NOTEThischapteronlydescribesIDviewsfunctionalityrelatedtoActiveDirectory(AD).
ForgeneralinformationaboutIDviews,seetheLinuxDomainIdentity,Authentication,andPolicyGuide.
YoucanuseIDviewsinADenvironmentsforthefollowingpurposes:OverridingADUserAttributes,suchasPOSIXAttributesorSSHLoginDetailsSeeSection8.
3,"UsingIDViewstoDefineADUserAttributes"fordetails.
Migratingfromsynchronization-basedtotrust-basedintegrationSeeSection7.
2,"MigratefromSynchronizationtoTrustManuallyUsingIDViews"fordetails.
Performingper-hostgroupoverrideoftheIdMuserattributesSeeSection8.
4,"MigratingNISDomainstoIdM"fordetails.
8.
1.
ACTIVEDIRECTORYDEFAULTTRUSTVIEW8.
1.
1.
WhatIstheDefaultTrustViewTheDefaultTrustViewisthedefaultIDviewalwaysappliedtoADusersandgroupsintrust-basedsetups.
Itiscreatedautomaticallywhenyouestablishthetrustusingipa-adtrust-installandcannotbedeleted.
UsingtheDefaultTrustView,youcandefinecustomPOSIXattributesforADusersandgroups,thusoverridingthevaluesdefinedinAD.
Table8.
1.
ApplyingtheDefaultTrustViewValuesinADDefaultTrustViewResultLoginad_userad_user→ad_userUID111222→222GID111(novalue)→111NOTEWindowsIntegrationGuide112NOTETheDefaultTrustViewonlyacceptsoverridesforADusersandgroups,notforIdMusersandgroups.
ItisappliedontheIdMserverandclientsandthereforeonlyneedtoprovideoverridesforActiveDirectoryusersandgroups.
8.
1.
2.
OverridingtheDefaultTrustViewwithOtherIDViewsIfanotherIDviewappliedtothehostoverridestheattributevaluesintheDefaultTrustView,IdMappliesthevaluesfromthehost-specificIDviewontopoftheDefaultTrustView.
Ifanattributeisdefinedinthehost-specificIDview,IdMappliesthevaluefromthisview.
Ifanattributeisnotdefinedinthehost-specificIDview,IdMappliesthevaluefromtheDefaultTrustView.
TheDefaultTrustViewisalwaysappliedtoIdMserversandreplicasaswellastoADusersandgroups.
YoucannotassignadifferentIDviewtothem:theyalwaysapplythevaluesfromtheDefaultTrustView.
Table8.
2.
ApplyingaHost-SpecificIDViewonTopoftheDefaultTrustViewValuesinADDefaultTrustViewHost-SpecificViewResultLoginad_userad_user(novalue)→ad_userUID111222333→333GID111(novalue)333→3338.
1.
3.
IDOverridesonClientsBasedontheClientVersionTheIdMmastersalwaysapplyIDoverridesfromtheDefaultTrustView,regardlessofhowIdMclientsretrievethevalues:usingSSSDorusingSchemaCompatibilitytreerequests.
However,theavailabilityofIDoverridesfromhost-specificIDviewsislimited:Legacyclients:RHEL6.
3andearlier(SSSD1.
8andearlier)TheclientscanrequestaspecificIDviewtobeapplied.
Touseahost-specificIDviewonalegacyclient,changethebaseDNontheclientto:cn=id_view_name,cn=views,cn=compat,dc=example,dc=com.
RHEL6.
4to7.
0(SSSD1.
9to1.
11)Host-specificIDviewsontheclientsarenotsupported.
RHEL7.
1andlater(SSSD1.
12andlater)Fullsupport.
8.
2.
FIXINGIDCONFLICTSCHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS113IdMusesIDrangestoavoidcollisionsofPOSIXIDsfromdifferentdomains.
FordetailsonIDranges,seeIDRangesintheLinuxDomainIdentity,Authentication,andPolicyGuide.
POSIXIDsinIDviewsdonotuseaspecialrangetype,becauseIdMmustallowoverlapswithotherkindsofIDranges.
Forexample,ADuserscreatedthroughsynchronizationhavePOSIXIDsfromthesameIDrangeasIdMusers.
POSIXIDsaremanagedmanuallyinIDviewsontheIdMside.
Therefore,ifanIDcollisionoccurs,fixitbychangingtheconflictingIDs.
8.
3.
USINGIDVIEWSTODEFINEADUSERATTRIBUTESWithIDviews,youcanchangetheuserattributevaluesdefinedinAD.
Foracompletelistoftheattributes,seeAttributesanIDViewCanOverride.
Forexample:IfyouaremanagingamixedLinux-WindowsenvironmentandwanttomanuallydefinePOSIXattributesorSSHloginattributesforanADuser,buttheADpolicydoesnotallowit,youcanuseIDviewstooverridetheattributevalues.
WhentheADuserauthenticatestoclientsrunningSSSDorauthenticatesusingacompatLDAPtree,thenewvaluesareusedintheauthenticationprocess.
NOTEOnlyIdMuserscanmanageIDviews.
ADuserscannot.
Theprocessforoverridingtheattributevaluesfollowsthesesteps:1.
CreateanewIDview.
2.
AddauserIDoverrideintheIDview,andspecifytherequireattributevalue.
3.
ApplytheIDviewtoaspecifichost.
Fordetailsonhowtoperformthesesteps,seeDefiningaDifferentAttributeValueforaUserAccountonDifferentHostsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
8.
4.
MIGRATINGNISDOMAINSTOIDMIfyouaremanagingaLinuxenvironmentandwanttomigratedisparateNISdomainswithdifferentUIDsandGIDsintoamodernidentitymanagementsolution,youcanuseIDviewstosethostspecificUIDsandGIDsforexistinghoststopreventchangingthepermissionsonexistingfilesanddirectories.
Theprocessforthemigrationfollowsthesesteps:1.
CreatetheusersandgroupsintheIdMdomain.
Fordetails,seeAddingStageorActiveUsersAddingandRemovingUserGroups2.
UseIDviewsforexistinghoststooverridetheIDsIdMgeneratedduringtheusercreation:1.
CreateanindividualIDview.
2.
AddIDoverridesfortheusersandgroupstotheIDview.
WindowsIntegrationGuide1143.
AssigntheIDviewtothespecifichosts.
Fordetails,seeDefiningaDifferentAttributeValueforaUserAccountonDifferentHosts.
3.
InstallingandUninstallingIdentityManagementClientsintheLinuxDomainIdentity,Authentication,andPolicyGuide.
4.
DecommissiontheNISdomains.
8.
5.
CONFIGURATIONOPTIONSFORUSINGSHORTNAMESTORESOLVEANDAUTHENTICATEUSERSANDGROUPSThissectiondescribesconfigurationoptionsenablingyoutouseshortuserorgroupnamesinsteadoftheuser_name@domainordomain\user_namefullyqualifiednamesformattoresolveandauthenticateusersandgroupsinanActiveDirectory(AD)environment.
Youcanconfigurethis:inIdentityManagement(IdM)thattrustsADonRedHatEnterpriseLinuxjoinedtoanADusingSSSD8.
5.
1.
HowDomainResolutionWorksYoucanusethedomainresolutionorderoptiontospecifytheorderinwhichalistofdomainsissearchedtoreturnamatchforagivenusername.
Youcansettheoption:ontheserver.
See:Section8.
5.
2.
1,"SettingtheDomainResolutionOrderGlobally"Section8.
5.
2.
2,"SettingtheDomainResolutionOrderforanIDview"ontheclient.
SeeSection8.
5.
3,"ConfiguringtheDomainResolutionOrderonanIdMClient"InenvironmentswithanActiveDirectorytrust,applyingoneorbothoftheserver-basedoptionsisrecommended.
Fromtheperspectiveofaparticularclient,thedomainresolutionorderoptioncanbesetinmorethanoneofthethreelocationsabove.
Theorderinwhichaclientconsultsthethreelocationsis:1.
thelocalsssd.
confconfiguration2.
theidviewconfiguration3.
theglobalIdMconfigurationOnlythedomainresolutionordersettingfoundfirstwillbeused.
InenvironmentsinwhichRedHatEnterpriseLinuxisdirectlyintegratedintoanAD,youcanonlysetthedomainresolutionorderontheclient.
NOTECHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS115NOTEYoumustusequalifiednamesif:AusernameexistsinmultipledomainsTheSSSDconfigurationincludesthedefault_domain_suffixoptionandyouwanttomakearequesttowardsadomainnotspecifiedwiththatoption8.
5.
2.
ConfiguringtheDomainResolutionOrderonanIdentityManagementServerSelecttheserver-basedconfigurationifalargenumberofclientsinadomainorsubdomainshoulduseanidenticaldomainresolutionorder.
8.
5.
2.
1.
SettingtheDomainResolutionOrderGloballySelectthisoptionforsettingthedomainresolutionordertoalltheclientsinthetrust.
Inordertodothis,usetheipaconfig-modcommand.
Forexample,inanIdMdomainthattrustsanADforestwithmultiplechilddomains:$ipaconfig-mod--domain-resolution-order='idm.
example.
com:ad.
example.
com:subdomain1.
ad.
example.
com:subdomain2.
ad.
example.
com'Maximumusernamelength:32Homedirectorybase:/home.
.
.
DomainResolutionOrder:idm.
example.
com:ad.
example.
com:subdomain1.
ad.
example.
com:subdomain2.
ad.
example.
com.
.
.
Withthedomainresolutionordersetinthisway,usersfromboththeIdMdomainandfromthetrustedADforestcanloginusingshortnamesonly.
8.
5.
2.
2.
SettingtheDomainResolutionOrderforanIDviewSelectthisoptiontoapplythesettingtotheclientsinaspecificdomain.
Forexample,onyoursubdomainserver,server.
idm.
example.
com,youobservemanymoreloginsfromthesubdomain2.
ad.
example.
comsubdomainthanfromsubdomain1.
ad.
example.
com.
Theglobalresolutionorderstates,however,thatthesubdomain1.
ad.
example.
comsubdomainuserdatabaseistriedoutbeforesubdomain2.
ad.
example.
comwhenresolvingusernames.
Tosetadifferentorderforcertainservers,setupadomainresolutionorderforaspecificview:1.
CreateanIDviewwiththedomainresolutionorderoptionset:$ipaidview-addexample_view--desc"IDviewforcustomshortnameresolutiononserver.
idm.
example.
com"--domain-resolution-ordersubdomain2.
ad.
example.
com:subdomain1.
ad.
example.
comAddedIDView"example_view"IDViewName:example_viewDescription:IDviewforcustomshortnameresolutiononserver.
idm.
example.
comDomainResolutionOrder:subdomain2.
ad.
example.
com:subdomain1.
ad.
example.
comWindowsIntegrationGuide1162.
Applytheviewontheclients.
Forexample:$ipaidview-applyexample_view--hostsserver.
idm.
example.
comAppliedIDView"example_view"hosts:server.
idm.
example.
comNumberofhoststheIDViewwasappliedto:1ForfurtherinformationonIDviews,seeChapter8,UsingIDViewsinActiveDirectoryEnvironments.
8.
5.
3.
ConfiguringtheDomainResolutionOrderonanIdMClientSetthedomainresolutionorderontheclientifyouwanttosetitonalownumberofclientsoriftheclientsaredirectlyconnectedtoAD.
Setthedomain_resolution_orderoption,inthe[sssd]section,inthe/etc/sssd/sssd.
conffile,forexample:domain_resolution_order=subdomain1.
ad.
example.
com,subdomain2.
ad.
example.
comForfurtherinformationonconfiguringthedomain_resolution_orderoption,seethesssd.
conf(5)manpage.
CHAPTER8.
USINGIDVIEWSINACTIVEDIRECTORYENVIRONMENTS117APPENDIXA.
REVISIONHISTORYNotethatrevisionnumbersrelatetotheeditionofthismanual,nottoversionnumbersofRedHatEnterpriseLinux.
Revision7.
0-50WedMay272020FlorianDelehayeSeveralfixesandupdates.
Revision7.
0-49TueAug062019MarcMuehlfeldDocumentversionfor7.
7GApublication.
Revision7.
0-48WedJun052019MarcMuehlfeldUpdatedConfiguringTrustAgents,addedHowtheADProviderHandlesTrustedDomainsandChangingtheFormatofUserNamesDisplayedbySSSD.
Revision7.
0-47TueApr082019MarcMuehlfeldSeveralminorfixesandupdates.
Revision7.
0-46MonOct292018FilipHanzelkaPreparingdocumentfor7.
6GApublication.
Revision7.
0-45MonJun252018FilipHanzelkaAddedSwitchingBetweenSSSDandWinbindforSMBShareAccess.
Revision7.
0-44ThuApr52018FilipHanzelkaPreparingdocumentfor7.
5GApublication.
Revision7.
0-43WedFeb282018FilipHanzelkaUpdatedGPOSettingsSupportedbySSSD.
Revision7.
0-42MonFeb122018AnetateflováPetrováUpdatedCreatingaTwo-WayTrustwithaSharedSecret.
Revision7.
0-41MonJan292018AnetateflováPetrováMinorfixes.
Revision7.
0-40FriDec152017AnetateflováPetrováMinorfixes.
Revision7.
0-39MonDec62017AnetateflováPetrováUpdatedUsingSambaforActiveDirectoryIntegration.
Revision7.
0-38MonDec42017AnetateflováPetrováUpdatedDNSandRealmSettingsfortrusts.
Revision7.
0-37MonNov202017AnetateflováPetrováUpdatedCreatingaTwo-WayTrustwithaSharedSecret.
Revision7.
0-36MonNov62017AnetateflováPetrováMinorfixes.
Revision7.
0-35MonOct232017AnetateflováPetrováUpdatedActiveDirectoryEntriesandPOSIXAttributesandConfiguringanADDomainwithIDMappingasaProviderforSSSD.
Revision7.
0-34MonOct92017AnetateflováPetrováAddedConfigurationOptionsforUsingShortNames.
UpdatedTrustControllersandTrustAgents.
WindowsIntegrationGuide118Revision7.
0-33TueSep262017AnetateflováPetrováUpdatedtheautodiscoverysectionintheSSSDchapter.
Addedtwosectionsonconfiguringtrusteddomains.
Revision7.
0-32TueJul182017AnetateflováPetrováDocumentversionfor7.
4GApublication.
Revision7.
0-31TueMay232017AnetateflováPetrováAminorfixforAboutSecurityIDMapping.
Revision7.
0-30MonApr242017AnetateflováPetrováMinorfixesforDefiningWindowsIntegration.
Revision7.
0-29MonApr102017AnetateflováPetrováUpdatedDirectIntegration.
Revision7.
0-28MonMar272017AnetateflováPetrováMovedAllowingUserstoChangeOtherUsers'PasswordsCleanlytotheLinuxDomainIdentityguideasEnablingPasswordReset.
UpdatedSupportedWindowsPlatformsfortrusts.
Fixedbrokenlinks.
Otherminorupdates.
Revision7.
0-27MonFeb272017AnetateflováPetrováUpdatedportrequirementsfortrusts.
Minorrestructuringfortrustandsync.
Otherminorupdates.
Revision7.
0-26WedNov232016AnetateflováPetrováAddedipa-winsync-migrate.
Minorfixesforthetrust,SSSD,andsynchronizationchapters.
Revision7.
0-25TueOct182016AnetateflováPetrováVersionfor7.
3GApublication.
Revision7.
0-24ThuJul282016MarcMuehlfeldUpdateddiagrams,addedKerberosflagsforservicesandhosts,otherminorfixes.
Revision7.
0-23ThuJun092016MarcMuehlfeldUpdatedthesynchronizationchapter.
RemovedtheKerberoschapter.
Otherminorfixes.
Revision7.
0-22TueFeb092016AnetaPetrováUpdatedrealmd,removedindex,movedapartofIDviewstotheLinuxDomainIdentityguide,otherminorupdates.
Revision7.
0-21FriNov132015AnetaPetrováVersionfor7.
2GAreleasewithminorupdates.
Revision7.
0-20ThuNov122015AnetaPetrováVersionfor7.
2GArelease.
Revision7.
0-19FriSep182015TomáapekUpdatedthesplashpagesortorder.
Revision7.
0-18ThuSep102015AnetaPetrováUpdatedtheoutputformat.
Revision7.
0-17MonJul272015AnetaPetrováAddedGPO-basedaccesscontrol,anumberofotherminorchanges.
Revision7.
0-16ThuApr022015TomáapekAddedipa-advise,extendedCIFSsharewithSSSD,admonitionfortheIdentityManagementforUNIXextension.
Revision7.
0-15FriMar132015TomáapekAsyncupdatewithlast-minuteeditsfor7.
1.
APPENDIXA.
REVISIONHISTORY119Revision7.
0-13WedFeb252015TomáapekVersionfor7.
1GArelease.
Revision7.
0-11FriDec052014TomáapekRebuildtoupdatethesortorderonthesplashpage.
Revision7.
0-7MonSep152014TomáapekSection5.
3CreatingTruststemporarilyremovedforcontentupdates.
Revision7.
0-5June27,2014EllaDeonBallardImprovingSamba+Kerberos+Winbindchapters.
Revision7.
0-4June13,2014EllaDeonBallardAddingKerberosrealmchapter.
Revision7.
0-3June11,2014EllaDeonBallardInitialrelease.
WindowsIntegrationGuide120
- ssstrustview相关文档
- 978-1-4799-6065-1/15/$31.00
- simplertrustview
- Cordestrustview
- ,"网络安全扫描"
- 解析trustview
- verifytrustview
819云(240元)香港CN2 日本CN2 物理机 E5 16G 1T 20M 3IP
819云是我们的老熟人了,服务器一直都是稳定为主,老板人也很好,这次给大家带来了新活动,十分给力 香港CN2 日本CN2 物理机 E5 16G 1T 20M 3IP 240元0官方网站:https://www.819yun.com/ 特惠专员Q:442379204套餐介绍套餐CPU内存硬盘带宽IP价格香港CN2 (特价)E5 随机分配16G1T 机械20M3IP240元/月日本CN2 (...
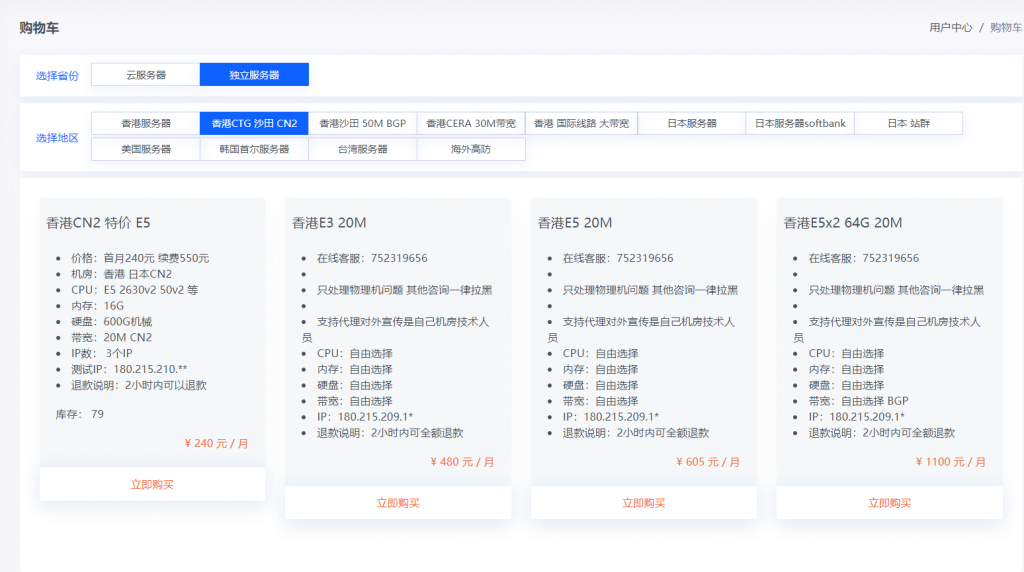
BuyVM新设立的迈阿密机房速度怎么样?简单的测评速度性能
BuyVM商家算是一家比较老牌的海外主机商,公司设立在加拿大,曾经是低价便宜VPS主机的代表,目前为止有提供纽约、拉斯维加斯、卢森堡机房,以及新增加的美国迈阿密机房。如果我们有需要选择BuyVM商家的机器需要注意的是注册信息的时候一定要规范,否则很容易出现欺诈订单,甚至你开通后都有可能被禁止账户,也是这个原因,曾经被很多人吐槽的。这里我们简单的对于BuyVM商家新增加的迈阿密机房进行简单的测评。如...
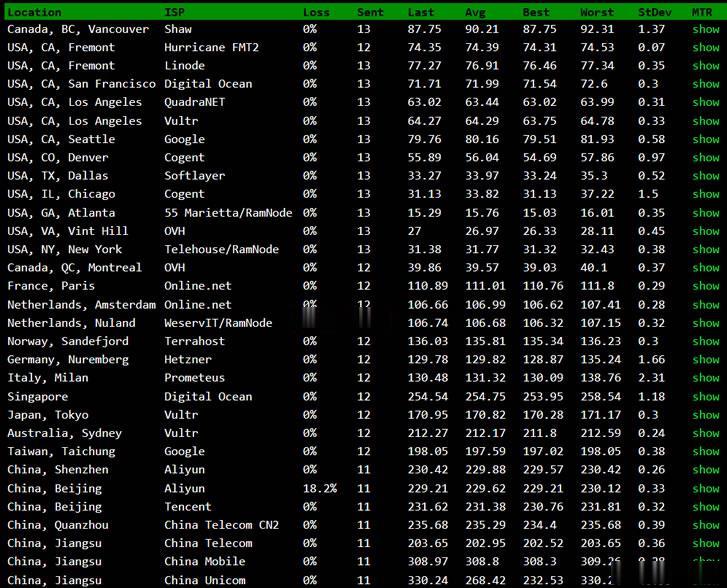
恒创新客(317元)香港云服务器 2M带宽 三网CN2线路直连
恒创科技也有暑期的活动,其中香港服务器也有一定折扣,当然是针对新用户的,如果我们还没有注册过或者可以有办法注册到新用户的,可以买他们家的香港服务器活动价格,2M带宽香港云服务器317元。对于一般用途还是够用的。 活动链接:恒创暑期活动爆款活动均是针对新用户的。1、云服务器仅限首次购买恒创科技产品的新用户。1 核 1G 实例规格,单个账户限购 1台;其他活动机型,单个账户限购 3 台(必须在一个订单...
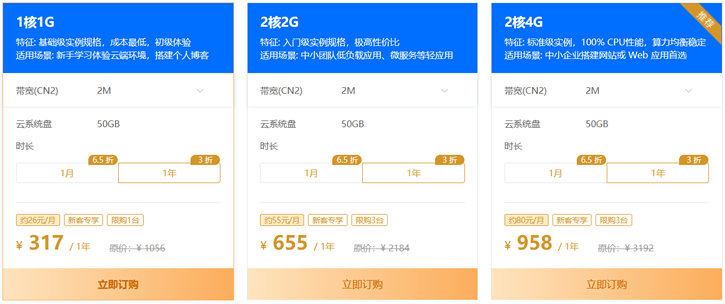
trustview为你推荐
-
百度空间首页如何上百度空间首页麒麟990和骁龙865哪个好高通865处理器怎么样?值得入手吗?迈腾和帕萨特哪个好新帕萨特怎么样 迈腾和帕萨特哪个好浮动利率和固定利率哪个好房贷利率是固定的还是浮动的好?ps软件哪个好什么PS软件好海克斯皮肤哪个好诺手二周年皮肤好不好,和海克斯那个比哪个好,二周年属于稀有吗电信10000宽带测速电信宽带速度东莞电信宽带东莞电信宽带资费问题。急!东莞电信网上营业厅怎样联系申请东莞中国电信固话360云盘360云盘有多大?